本文主要是介绍HCIA--ACL和远程登陆实验,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
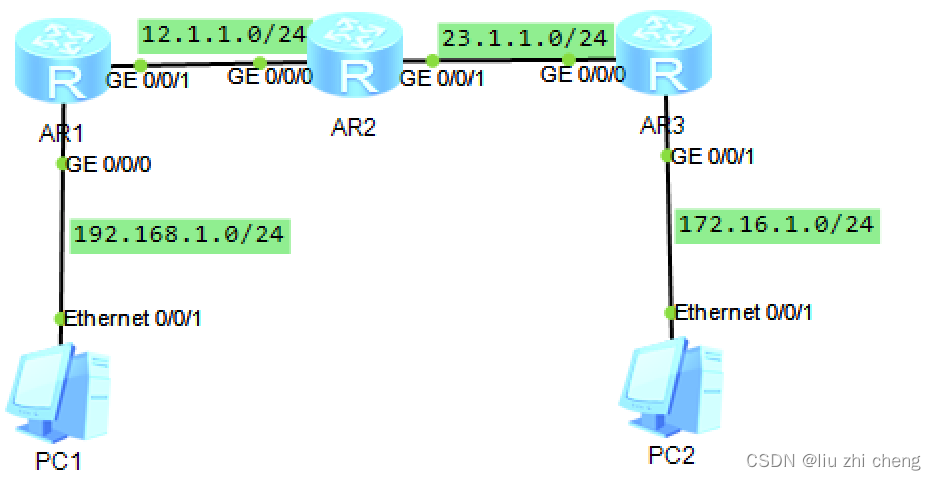
1.划分网段,配IP地址,启用OSPF协议:
AR1配置:
[Huawei]sys R1
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]ip add 192.168.1.1 24
[R1-GigabitEthernet0/0/0]int g0/0/1
[R1-GigabitEthernet0/0/1]ip add 12.1.1.1 24
[R1-GigabitEthernet0/0/1]qu
[R1]ospf 100 router-id 1.1.1.1
[R1-ospf-100]area 0
[R1-ospf-100-area-0.0.0.0]network 0.0.0.0 255.255.255.255AR2配置:
[Huawei]sys R2
[R2]int g0/0/0
[R2-GigabitEthernet0/0/0]ip add 12.1.1.2 24
[R2-GigabitEthernet0/0/0]int g0/0/1
[R2-GigabitEthernet0/0/1]ip add 23.1.1.1 24
[R2-GigabitEthernet0/0/1]qu
[R2]ospf 100 router-id 2.2.2.2
[R2-ospf-100]area 0
[R2-ospf-100-area-0.0.0.0]network 0.0.0.0 255.255.255.255
AR3配置:
[Huawei]sys R3
[R3]int g0/0/0
[R3-GigabitEthernet0/0/0]ip add 23.1.1.2 24
[R3-GigabitEthernet0/0/0]int g0/0/1
[R3-GigabitEthernet0/0/1]ip add 172.16.1.1 24
[R3-GigabitEthernet0/0/1]qu
[R3]ospf 100 router-id 3.3.3.3
[R3-ospf-100]ar 0
[R3-ospf-100-area-0.0.0.0]network 0.0.0.0 255.255.255.255
[R3]acl 2000 #acl配置
[R3-acl-basic-2000]rule deny source 192.168.1.2 0.0.0.0
[R3-acl-basic-2000]qu
[R3]int g0/0/1 #acl调用
[R3-GigabitEthernet0/0/1]traffic-filter outbound acl 2000
[R3-GigabitEthernet0/0/1]qu
[R3]dis acl all #查看acl
2. 基本ACL配置:
AR2:
[R2]acl 2000
[R2-acl-basic-2000]rule deny source 12.1.1.1 0.0.0.0
[R2-acl-basic-2000]qu
[R2]int g0/0/1
[R2-GigabitEthernet0/0/1]traffic-filter outbound acl 2000
[R2-GigabitEthernet0/0/1]undo traffic-filter outbound
AR3:
[R3]acl 2000
[R3-acl-basic-2000]rule deny source 192.168.1.2 0.0.0.0
[R3-acl-basic-2000]qu
[R3]int g0/0/0
[R3-GigabitEthernet0/0/0]traffic-filter outbound acl 2000
[R3-GigabitEthernet0/0/0]undo traffic-filter outbound
[R3-GigabitEthernet0/0/0]qu
[R3]int g0/0/1
[R3-GigabitEthernet0/0/1]traffic-filter outbound acl 2000
[R3-GigabitEthernet0/0/1]qu
[R3]dis acl allTotal quantity of nonempty ACL number is 1 Basic ACL 2000, 1 rule
Acl's step is 5rule 5 deny source 192.168.1.2 0 [R3]undo acl 2000
[R3]q
<R3>terminal debugging
Info: Current terminal debugging is on.
<R3>debugging ip icmp
3. 高级ACL配置,使用位置:靠近源的接口
AR1:
[R1]acl 3000
[R1-acl-adv-3000]rule deny ip source 192.168.1.2 0.0.0.0 destination 172.16.1.2
0.0.0.0
[R1-acl-adv-3000]qu
[R1]int g0/0/0 #调用acl
[R1-GigabitEthernet0/0/0]traffic-filter inbound acl 3000
AR2:
[R2]acl 3000
[R2-acl-adv-3000]rule deny icmp source 12.1.1.1 0.0.0.0 destination 23.1.1.2
0.0.0.0 #不让12.1.1.1,23.1.1.2互相访问
[R2-acl-adv-3000]q
[R2]int g0/0/1 #调用
[R2-GigabitEthernet0/0/1]traffic-filter outbound acl 3000
[R2-GigabitEthernet0/0/1]q
[R2]undo acl 3000[R2]acl 3000
[R2-acl-adv-3000]rule 5 deny icmp source 23.1.1.2 0.0.0.0 destination 12.1.1.1
0.0.0.0 #流量可以从R1到R3,但不能回去
[R2-acl-adv-3000]qu
[R2]int g0/0/1
[R2-GigabitEthernet0/0/1]traffic-filter inbound acl 3000
AR3:
<R3>terminal debugging #打开debugging
Info: Current terminal debugging is on.
<R3>debugging ip icmp
4. 远程登陆配置:
AR1:
[R1]int l0
[R1-LoopBack0]ip add 1.1.1.1 32[R1]qu
<R1>telnet 23.1.1.2 #远程登陆R3Press CTRL_] to quit telnet modeTrying 23.1.1.2 ...Connected to 23.1.1.2 ...Login authenticationPassword:
<R3>AR3:
[R3]user-interface vty 0 4 #配置远程登陆
[R3-ui-vty0-4]authentication-mode password
Please configure the login password (maximum length 16):123
[R3-ui-vty0-4]user privilege level 15 #开启最高权限
或者使用用户名、密码远程登陆:
AR3:
[R3]aaa
[R3-aaa]local-user xx privilege level 15 password cipher yy
Info: Add a new user.
[R3-aaa]qu
[R3]user-interface vty 0 4 #调用
[R3-ui-vty0-4]authentication-mode aaa
在AR1上登陆AR3:
<R1>telnet 23.1.1.2Press CTRL_] to quit telnet modeTrying 23.1.1.2 ...Connected to 23.1.1.2 ...Login authenticationUsername:xx
Password:<R3>5. 干掉远程登陆,AR2:
[R2]acl 3000 #干掉远程登陆
[R2-acl-adv-3000]rule deny tcp source 12.1.1.1 0.0.0.0 destination 23.1.1.2 0.0.
0.0 destination-port eq telnet
[R2]int g0/0/0 #调用
[R2-GigabitEthernet0/0/0]traffic-filter inbound acl 3000AR1测试结果:
<R1>telnet 23.1.1.2Press CTRL_] to quit telnet modeTrying 23.1.1.2 ...6. PC1 无法ping通PC2,但PC2可以pingPC1:
AR1:
[R1]acl 3000
[R1-acl-adv-3000]rule deny icmp source 192.168.1.2 0.0.0.0 destination 172.16.1.
2 0.0.0.0 icmp-type echo
[R1-acl-adv-3000]qu
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]traffic-filter inbound acl 3000
PC1可以ping通PC2,但PC2不能pingPC1:
AR1:
[R1]acl 3000
[R1-acl-adv-3000]rule deny icmp source 192.168.1.2 0.0.0.0 destination 172.16.1.
2 0.0.0.0 icmp-type echo-reply
[R1-acl-adv-3000]qu
[R1-GigabitEthernet0/0/1]int g0/0/0
[R1-GigabitEthernet0/0/0]traffic-filter inbound acl 3000
Error: A simplified ACL has been applied in this view.
7. ACL的命名写法:
AR1:
[R1]acl name xx
[R1-acl-adv-xx]rule deny icmp source 1.1.1.1 0.0.0.0 destination 23.1.1.1 0.0.0
.0
[R1-acl-adv-xx]int g0/0/0 #调用
[R1-GigabitEthernet0/0/0]traffic-filter inbound acl name xx
这篇关于HCIA--ACL和远程登陆实验的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!









