本文主要是介绍一次PKIX异常问题排查记录,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
文章目录
- 事件说明
- PKIX异常堆栈信息
- 问题分析
- 原因一 证书不被信任
- JDK版本太古老,不支持ssl新版的实现
- 外部插件补充新版ssl协议支持
- 访问的目标网站需要登陆才能访问
事件说明
起因于对接外部第三方服务,使用https请求,浏览器访问目标地址成功,但是在程序中通过http调用直接就报异常了,具体异常堆栈信息后面有带上。当前项目运行环境为 jdk1.6,已经可以算是古老版本了。
PKIX异常堆栈信息
javax.net.ssl.SSLHandshakeException:
sun.security.validator.ValidatorException: PKIX path building failed:
sun.security.provider.certpath.SunCertPathBuilderException: unable to
find valid certification path to requested target at
com.sun.net.ssl.internal.ssl.Alerts.getSSLException(Alerts.java:174)
at
com.sun.net.ssl.internal.ssl.SSLSocketImpl.fatal(SSLSocketImpl.java:1747)
at
com.sun.net.ssl.internal.ssl.Handshaker.fatalSE(Handshaker.java:241)
at
com.sun.net.ssl.internal.ssl.Handshaker.fatalSE(Handshaker.java:235)
at
com.sun.net.ssl.internal.ssl.ClientHandshaker.serverCertificate(ClientHandshaker.java:1209)
at
com.sun.net.ssl.internal.ssl.ClientHandshaker.processMessage(ClientHandshaker.java:135)
at
com.sun.net.ssl.internal.ssl.Handshaker.processLoop(Handshaker.java:593)
at
com.sun.net.ssl.internal.ssl.Handshaker.process_record(Handshaker.java:529)
at
com.sun.net.ssl.internal.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:943)
at
com.sun.net.ssl.internal.ssl.SSLSocketImpl.performInitialHandshake(SSLSocketImpl.java:1188)
at
com.sun.net.ssl.internal.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1215)
at
com.sun.net.ssl.internal.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1199)
at
org.apache.http.conn.ssl.SSLConnectionSocketFactory.createLayeredSocket(SSLConnectionSocketFactory.java:275)
at
org.apache.http.conn.ssl.SSLConnectionSocketFactory.connectSocket(SSLConnectionSocketFactory.java:254)
at
org.apache.http.impl.conn.HttpClientConnectionOperator.connect(HttpClientConnectionOperator.java:123)
at
org.apache.http.impl.conn.PoolingHttpClientConnectionManager.connect(PoolingHttpClientConnectionManager.java:318)
at
org.apache.http.impl.execchain.MainClientExec.establishRoute(MainClientExec.java:363)
at
org.apache.http.impl.execchain.MainClientExec.execute(MainClientExec.java:219)
at
org.apache.http.impl.execchain.ProtocolExec.execute(ProtocolExec.java:195)
at org.apache.http.impl.execchain.RetryExec.execute(RetryExec.java:86)
at
org.apache.http.impl.execchain.RedirectExec.execute(RedirectExec.java:108)
at
org.apache.http.impl.client.InternalHttpClient.doExecute(InternalHttpClient.java:184)
at
org.apache.http.impl.client.CloseableHttpClient.execute(CloseableHttpClient.java:82)
at
org.apache.http.impl.client.CloseableHttpClient.execute(CloseableHttpClient.java:106)
at com.zengame.util.HttpUtil.doPost(HttpUtil.java:204) at
com.zengame.util.HttpUtil.doPost(HttpUtil.java:72) at
com.zengame.games.Singleton.SynchonizedSingleton T e a S h o p P r o d u c t T i m e r . r u n ( S y n c h o n i z e d S i n g l e t o n . j a v a : 94 ) a t j a v a . u t i l . c o n c u r r e n t . E x e c u t o r s TeaShopProductTimer.run(SynchonizedSingleton.java:94) at java.util.concurrent.Executors TeaShopProductTimer.run(SynchonizedSingleton.java:94)atjava.util.concurrent.ExecutorsRunnableAdapter.call(Executors.java:439)
at
java.util.concurrent.FutureTask S y n c . i n n e r R u n A n d R e s e t ( F u t u r e T a s k . j a v a : 317 ) a t j a v a . u t i l . c o n c u r r e n t . F u t u r e T a s k . r u n A n d R e s e t ( F u t u r e T a s k . j a v a : 150 ) a t j a v a . u t i l . c o n c u r r e n t . S c h e d u l e d T h r e a d P o o l E x e c u t o r Sync.innerRunAndReset(FutureTask.java:317) at java.util.concurrent.FutureTask.runAndReset(FutureTask.java:150) at java.util.concurrent.ScheduledThreadPoolExecutor Sync.innerRunAndReset(FutureTask.java:317)atjava.util.concurrent.FutureTask.runAndReset(FutureTask.java:150)atjava.util.concurrent.ScheduledThreadPoolExecutorScheduledFutureTask.access 101 ( S c h e d u l e d T h r e a d P o o l E x e c u t o r . j a v a : 98 ) a t j a v a . u t i l . c o n c u r r e n t . S c h e d u l e d T h r e a d P o o l E x e c u t o r 101(ScheduledThreadPoolExecutor.java:98) at java.util.concurrent.ScheduledThreadPoolExecutor 101(ScheduledThreadPoolExecutor.java:98)atjava.util.concurrent.ScheduledThreadPoolExecutorScheduledFutureTask.runPeriodic(ScheduledThreadPoolExecutor.java:180)
at
java.util.concurrent.ScheduledThreadPoolExecutor S c h e d u l e d F u t u r e T a s k . r u n ( S c h e d u l e d T h r e a d P o o l E x e c u t o r . j a v a : 204 ) a t j a v a . u t i l . c o n c u r r e n t . T h r e a d P o o l E x e c u t o r ScheduledFutureTask.run(ScheduledThreadPoolExecutor.java:204) at java.util.concurrent.ThreadPoolExecutor ScheduledFutureTask.run(ScheduledThreadPoolExecutor.java:204)atjava.util.concurrent.ThreadPoolExecutorWorker.runTask(ThreadPoolExecutor.java:895)
at
java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:918)
at java.lang.Thread.run(Thread.java:662) Caused by:
sun.security.validator.ValidatorException: PKIX path building failed:
sun.security.provider.certpath.SunCertPathBuilderException: unable to
find valid certification path to requested target at
sun.security.validator.PKIXValidator.doBuild(PKIXValidator.java:323)
at
sun.security.validator.PKIXValidator.engineValidate(PKIXValidator.java:217)
at sun.security.validator.Validator.validate(Validator.java:218) at
com.sun.net.ssl.internal.ssl.X509TrustManagerImpl.validate(X509TrustManagerImpl.java:126)
at
com.sun.net.ssl.internal.ssl.X509TrustManagerImpl.checkServerTrusted(X509TrustManagerImpl.java:209)
at
com.sun.net.ssl.internal.ssl.X509TrustManagerImpl.checkServerTrusted(X509TrustManagerImpl.java:249)
at
com.sun.net.ssl.internal.ssl.ClientHandshaker.serverCertificate(ClientHandshaker.java:1188)
… 31 more Caused by:
sun.security.provider.certpath.SunCertPathBuilderException: unable to
find valid certification path to requested target at
sun.security.provider.certpath.SunCertPathBuilder.engineBuild(SunCertPathBuilder.java:174)
at java.security.cert.CertPathBuilder.build(CertPathBuilder.java:238)
at
sun.security.validator.PKIXValidator.doBuild(PKIXValidator.java:318)
… 37 more
问题分析
原因一 证书不被信任
PKIX异常最常见的原因就是访问的目标网站,请求发送方不信任目标网站,因此,我先是通过Google Chrome 访问了一下,是可以成功访问的,因此尝试通过浏览器导出证书到本地,然后进入到jdk环境中。导入证书到项目中步骤如下:
1、从浏览器访问目标网站,以访问csdn为例,访问成功之后,点击浏览器地址栏前的这个按钮,https链接一般都会有这个锁的标识。
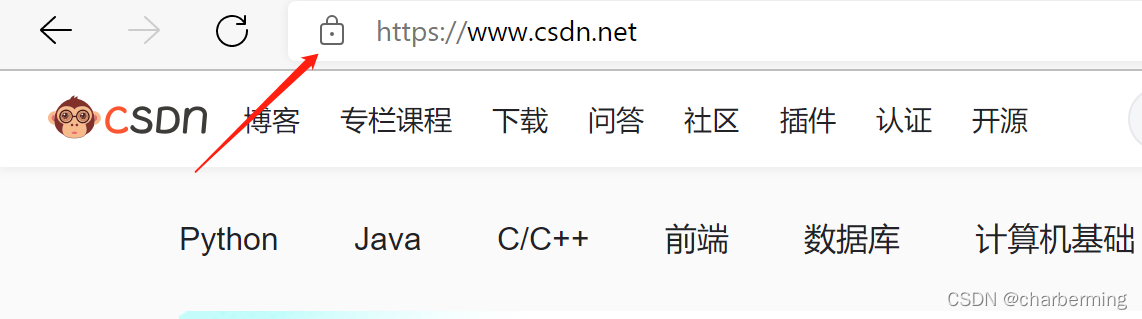
2、点击锁标识之后,会弹出下面的列表,选择第一个 安全连接
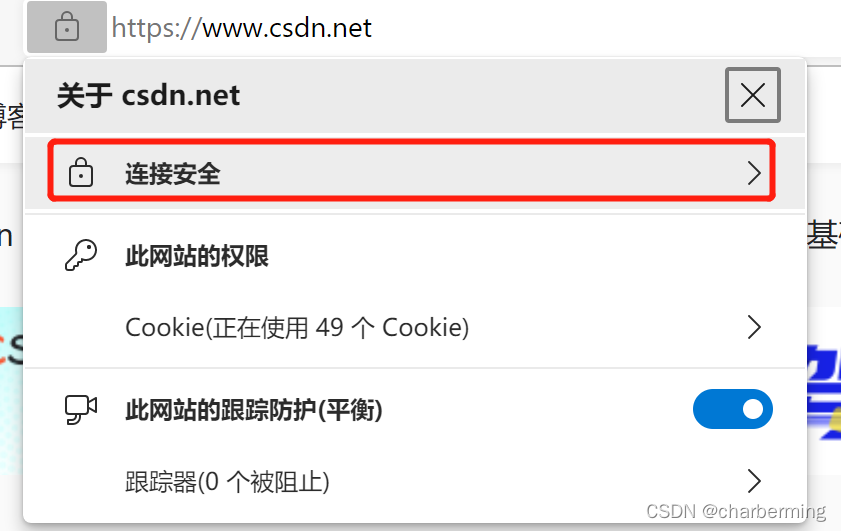
3、点击连接安全进入如下框框,点击认证证书的那个按钮。
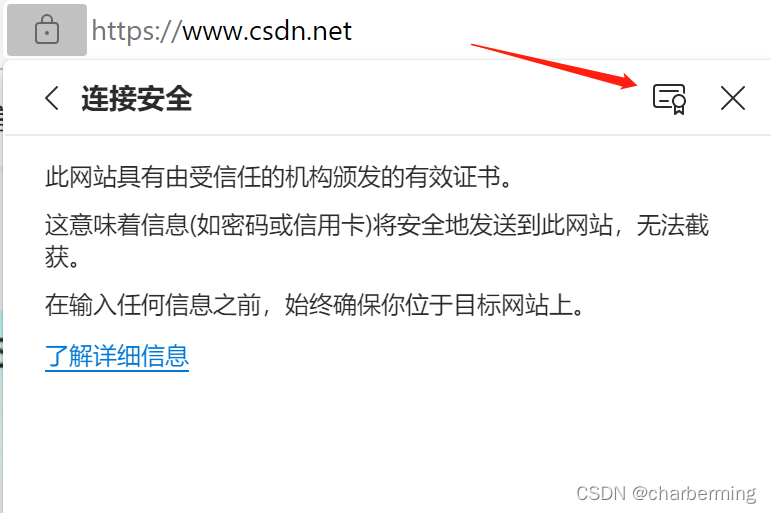
4、下一步会弹出证书相关的信息窗口,可以看到这个网站证书相关的信息,我们到处证书要选择第二个页签:详细信息,然后点击 复制到文件。
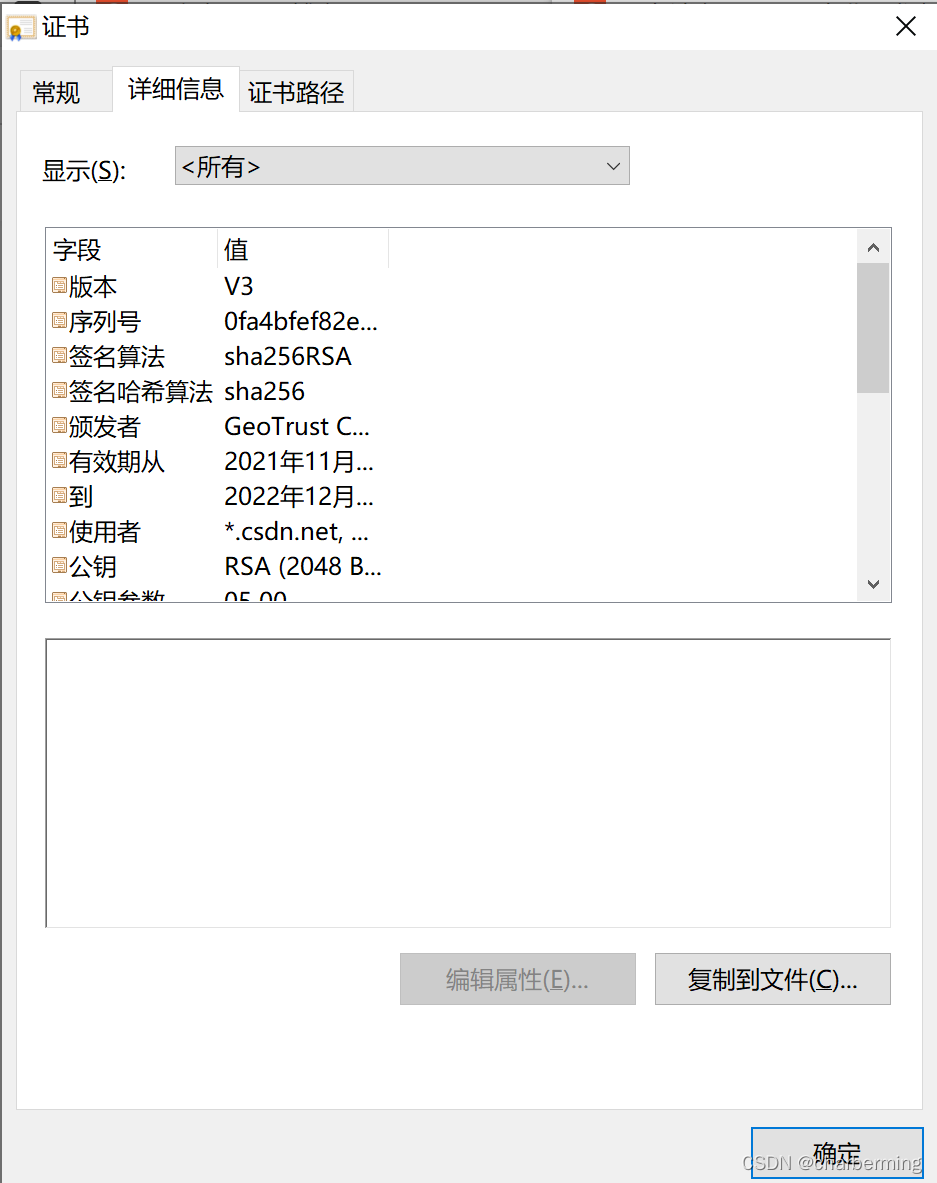
5、选择复制文件,弹出下一步操作的弹框,点击下一步进入到证书导出向导,这里选择Base64编码X.509。
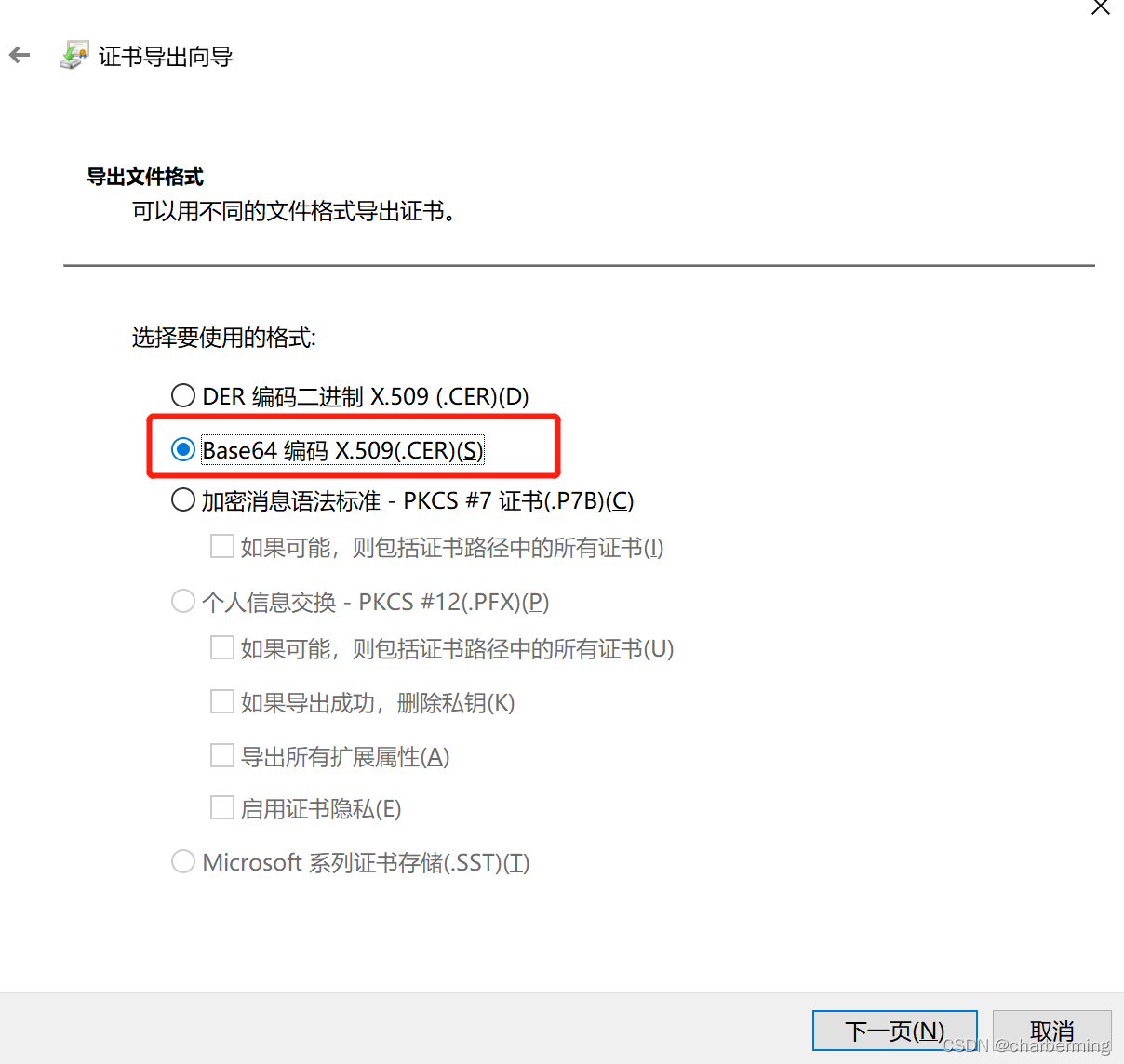
6、点击下一步,然后将导出的证书文件保存在本地目录,文件名后缀为 .cer
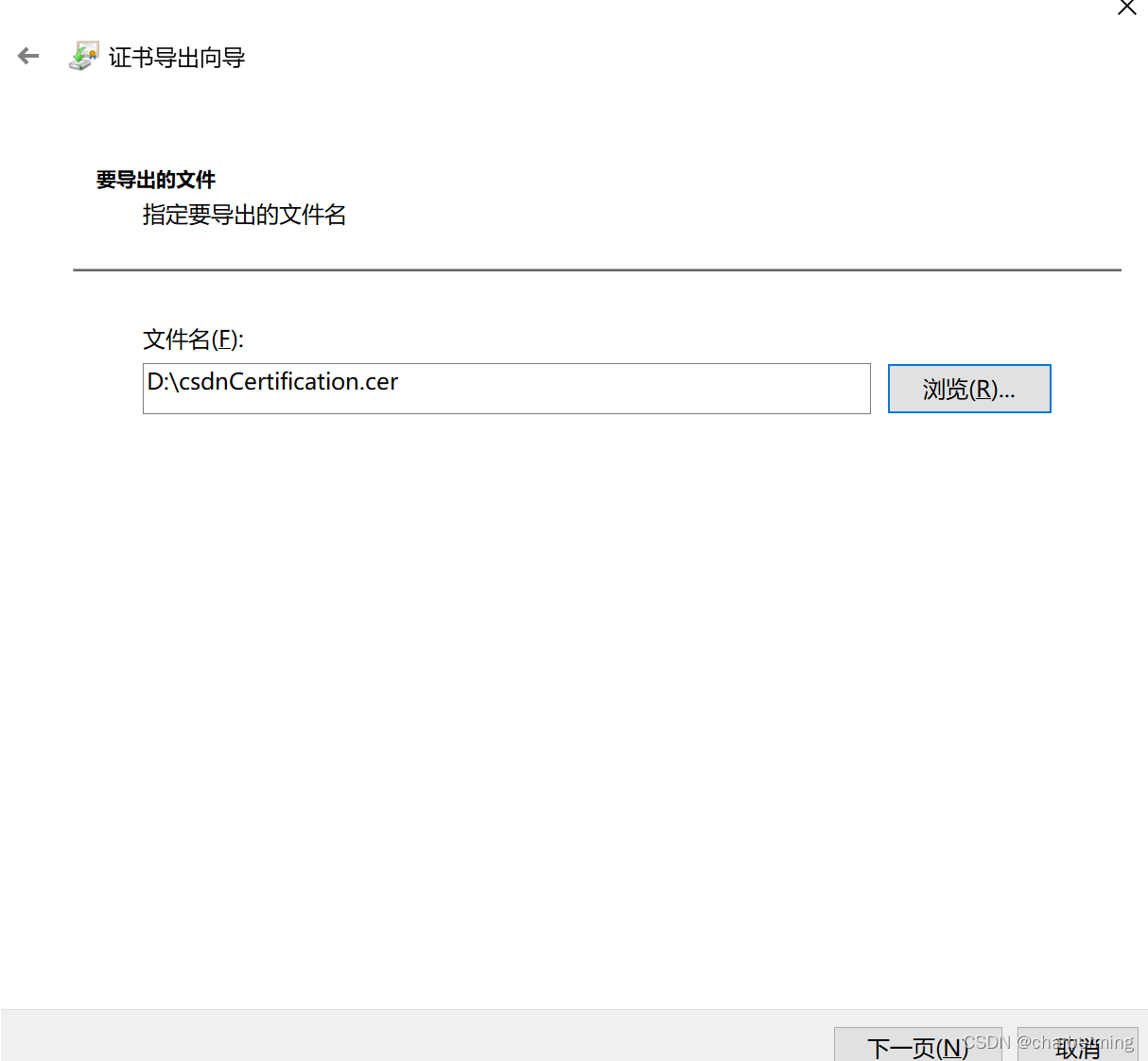
最后CMD执行
keytool -import -alias cacerts -keystore cacerts -file D:\csdnCertification.cer -trustcacerts
然后将生成的证书文件放到jdk安装目录下的jre/lib/security目录下
对于这个方法,网上大多数人能成功,但是这里还是么有用,出现了其他的异常,这里后面继续找其他方案尝试。
JDK版本太古老,不支持ssl新版的实现
由于我们的jdk目前是1.6,尝试升级成1.8,之后,问题得到解决,但是升级显然不是说升就升得了的,毕竟影响到整个项目架构。
外部插件补充新版ssl协议支持
上面说到jdk不支持,那么我们通过 Bouncy Castle来做一下扩展,BouncyCastle就是一个提供了很多哈希算法和加密算法的第三方库。它提供了Java标准库没有的一些算法。使用这个需要下载她的jar包,具体可以搜索一下它的使用方式,这里就写了。
访问的目标网站需要登陆才能访问
这里我是找第三方的服务提供商要了个测试账号,登陆之后再请求访问,没有出现PKIX异常,那就是需要登陆之后才给你授权访问了,至此尝试结束。
以上总结用于记录自己遇到PKIX异常的时候,问题排查解决的方式,分享出来,希能对各位看官有所帮助吧。
这篇关于一次PKIX异常问题排查记录的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!








