本文主要是介绍ENSP PRO LAB笔记:配置SRv6(Part3),希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
八、SRv6 TE Flow Group测试
8.1 测试拓扑
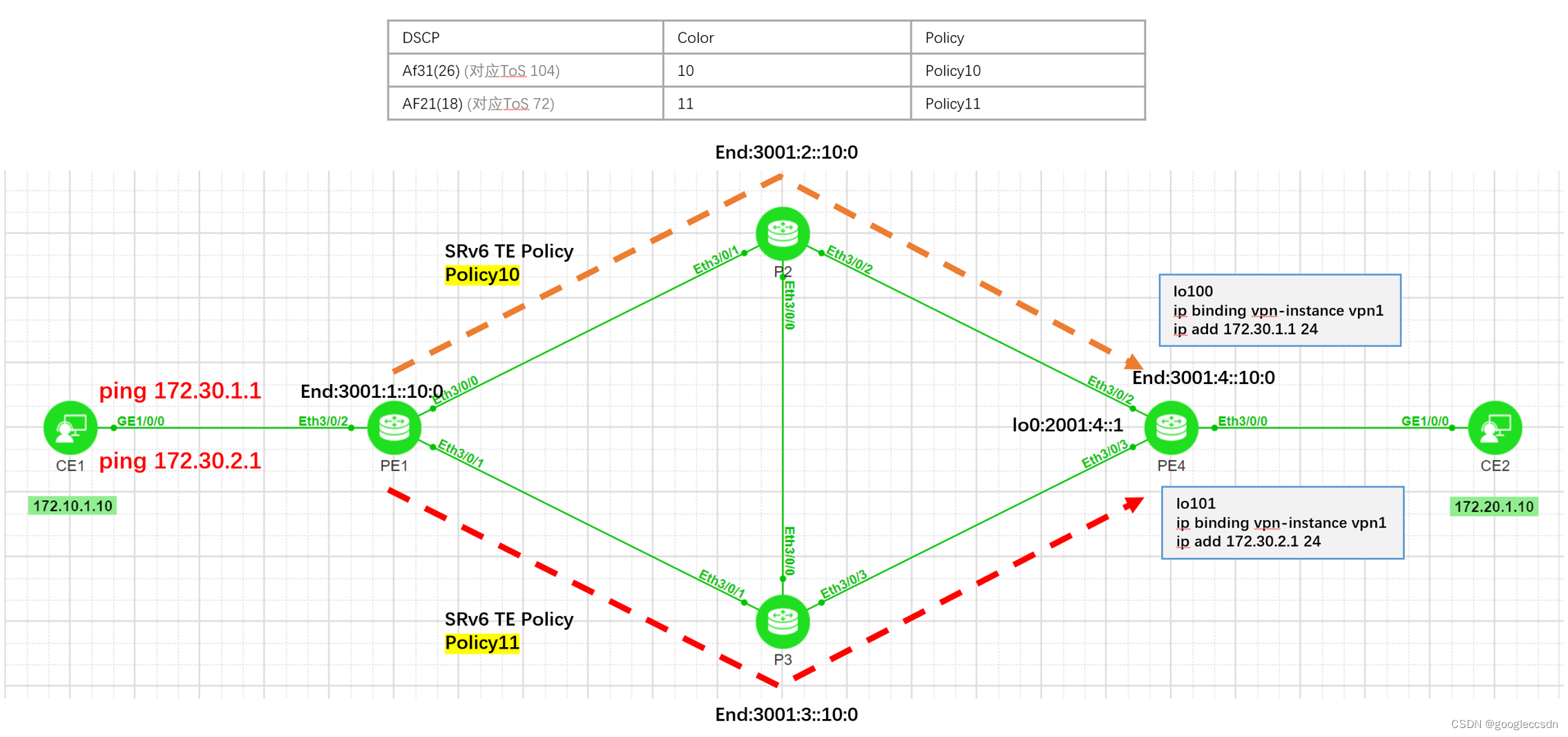
8.2 测试说明
- PE1配置2条SRv6 TE Policy,命名为policy10(color10)、policy11(color11)
- PE4 vpn1配置测试loopback100、loopback101,用于ping测试
- PE4发布vpn路由172.30.0.0/16
- PE1配置Mapping policy,用于DSCP引流
- PE1接收EVPN路由172.30.0.0/16时对此路由进行染色,通过DSCP引流的方式,将业务流量引入动态创建的SRv6 TE Flow Group
- 由于目前模拟路由器不支持DSCP标记,在CE1 ping 测试时,设置相应DSCP(支持linux ping)
- CE1 ping相同网段(172.30.0.0/16)的不同地址,PE1根据DSCP,选择不同的SRv6 TE Policy进行传输
8.3 测试步骤
8.3.1 配置SRv6 TE Policy
PE1配置:
segment-routing ipv6
segment-list list10
index 5 sid ipv6 3001:2::10:0
index 10 sid ipv6 3001:4::10:0
segment-list list11
index 5 sid ipv6 3001:3::10:0
index 10 sid ipv6 3001:4::10:0
srv6-te policy policy10 endpoint 2001:4::1 color 10
binding-sid 3001:1::90:0
candidate-path preference 100
segment-list list10
srv6-te policy policy11 endpoint 2001:4::1 color 11
binding-sid 3001:1::91:0
candidate-path preference 100
segment-list list11
#
8.3.2 查看SRv6 TE Policy信息
[PE1]dis srv6-te policy
PolicyName : policy10
Color : 10 Endpoint : 2001:4::1
TunnelId : 1 Binding SID : 3001:1::90:0(Insert)
TunnelType : SRv6-TE Policy DelayTimerRemain : -
Policy State : Up State Change Time : 2023-09-27 04:56:39
Admin State : Up Traffic Statistics : Disable
Backup Hot-Standby : Disable BFD : Disable
Interface Index : - Interface Name : -
Interface State : - Encapsulation Mode : Insert
Candidate-path Count : 1 Candidate-path Preference : 100Path State : Active Path Type : PrimaryProtocol-Origin : Configuration(30) Originator : 0, 0.0.0.0Discriminator : 100 Binding SID : 3001:1::90:0GroupId : 1 Policy Name : policy10Template ID : 0 Path Verification : EnableDelayTimerRemain : - Network Slice ID : -Segment-List Count : 1Segment-List : list10Segment-List ID : 1 XcIndex : 2 List State : Up DelayTimerRemain : -Verification State : Up SuppressTimeRemain : -PMTU : 9600 Active PMTU : 9600Weight : 1 BFD State : -Network Slice ID : - Binding SID : -Reverse Binding SID : - SID :3001:2::10:0 3001:4::10:0 PolicyName : policy11
Color : 11 Endpoint : 2001:4::1
TunnelId : 2 Binding SID : 3001:1::91:0(Insert)
TunnelType : SRv6-TE Policy DelayTimerRemain : -
Policy State : Up State Change Time : 2023-09-27 04:54:41
Admin State : Up Traffic Statistics : Disable
Backup Hot-Standby : Disable BFD : Disable
Interface Index : - Interface Name : -
Interface State : - Encapsulation Mode : Insert
Candidate-path Count : 1 Candidate-path Preference : 100Path State : Active Path Type : PrimaryProtocol-Origin : Configuration(30) Originator : 0, 0.0.0.0Discriminator : 100 Binding SID : 3001:1::91:0GroupId : 2 Policy Name : policy11Template ID : 0 Path Verification : EnableDelayTimerRemain : - Network Slice ID : -Segment-List Count : 1Segment-List : list11Segment-List ID : 2 XcIndex : 1 List State : Up DelayTimerRemain : -Verification State : Up SuppressTimeRemain : -PMTU : 9600 Active PMTU : 9600Weight : 1 BFD State : -Network Slice ID : - Binding SID : -Reverse Binding SID : - SID :3001:3::10:0 3001:4::10:0 8.3.3 配置测试Loopback地址
PE4创建两个loopback地址,分别配置测试网段172.30.1.0/24, 172.30.2.0/24,但对外只发布172.30.0.0/16的路由。
PE4:
#
interface LoopBack100
ip binding vpn-instance vpn1
ip address 172.30.1.1 255.255.255.0
#
interface LoopBack101
ip binding vpn-instance vpn1
ip address 172.30.2.1 255.255.255.0
#
8.3.4 发布VPN路由
PE4上,bgp ipv4 vpn实例vpn1在引入直连路由时,不引入loopback100/loopback101直连路由,通过引入静态路由方式,引入172.30.0.0/16,并发给PE1,这样做的目的是:PE1的vpn1都通过172.30.0.0/16访问172.30.1.1和172.30.2.1,并通过dscp对应不同的小color,迭代到不同的policy转发路径。
PE4配置
#
bgp 100
#
ipv4-family vpn-instance vpn1
import-route direct route-policy p1
import-route static
#
route-policy p1 permit node 10
if-match interface Ethernet3/0/0 (只允许局域端口的直连路由)
#
ip route-static vpn-instance vpn1 172.30.0.0 255.255.0.0 NULL0
#
执行完以上步骤后,在PE1用以下命令查看,172.30.0.0/16未染色之前,走SRv6 BE路径:
[PE1]dis ip routing-table vpn-instance vpn1
8.3.5 配置SRv6 Mapping Policy
8.3.5.1 功能说明
通过配置SRv6 Mapping Policy,设备利用业务路由(即VPN路由或私网路由)Color属性去匹配相同Color的SRv6 Mapping Policy,如果SRv6 Mapping Policy存在,则设备动态生成一个SRv6 TE Flow Group,供业务转发使用。该SRv6 TE Flow Group里存在多个Color属性不同,但EndPoint相同的SRv6 TE Policy。
8.3.5.2 DSCP说明
| 源IP地址 | 目的IP地址 | 模拟数据流 | DSCP设置 | Color |
| 172.10.1.10 | 172.30.1.1 | 数据流1 | AF31(DSCP:26,011010) | 10 |
| 172.10.1.10 | 172.30.2.1 | 数据流2 | AF21(DSCP:18,010010) | 11 |
8.3.5.3 配置Mapping policy
PE1配置:
#
segment-routing ipv6
mapping-policy p1 color 1000
match-type dscp
index 100 dscp ipv4 26 match srv6-te-policy color 10
index 200 dscp ipv4 18 match srv6-te-policy color 11
#
8.3.6 配置DSCP引流
#
route-policy p1 permit node 10
if-match ip-prefix 1
apply extcommunity color 0:101
#
route-policy p1 permit node 20
if-match ip-prefix 2
apply extcommunity color 0:1000
#
route-policy p1 permit node 30
#
ip ip-prefix 1 index 10 permit 172.20.1.0 24
ip ip-prefix 2 index 10 permit 172.30.0.0 16
#
#
tunnel-policy tnl-1
tunnel select-seq ipv6 srv6-te-policy load-balance-number 1
#
tunnel-policy tnl-2
tunnel select-seq ipv6 srv6-te-flow-group srv6-te-policy load-balance-number 1 unmix
#
#
ip vpn-instance vpn1
ipv4-family
tnl-policy tnl-2 evpn
#
8.3.7 查看SRv6 TE Flow Group信息
[PE1]dis srv6-te flow-groupSRv6-TE Flow Group Information
----------------------------------------------------------------------------------------------
Group Name :
Color : 1000 Endpoint : 2001:4::1
Group Tunnel ID : 4 Group Tunnel Type : SRv6-TE Flow Group
Group Tunnel State : Up State Change Time : 2023-09-27 04:54:43
Interface Index : - Interface Name : -
Interface State : -
Delay Timer Remain : - UP/ALL Num : 2/2Index : 100 AfType : IPv4DSCP : 26Match Tunnel : SRv6-TE Policy State : UpColor : 10 Tunnel Id : 1Index : 200 AfType : IPv4DSCP : 18Match Tunnel : SRv6-TE Policy State : UpColor : 11 Tunnel Id : 2
[PE1]8.3.8 查看VPN实例vpn1的路由
查看VPN实例IPv4路由表信息,可以看到私网路由已经成功迭代到SRv6 TE Flow Group。
[PE1]dis ip routing-table vpn-instance vpn1
Route Flags: R - relay, D - download to fib, T - to vpn-instance, B - black hole route
------------------------------------------------------------------------------
Routing Table : vpn1Destinations : 7 Routes : 7 Destination/Mask Proto Pre Cost Flags NextHop Interface127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0172.10.1.0/24 Direct 0 0 D 172.10.1.1 Ethernet3/0/2172.10.1.1/32 Direct 0 0 D 127.0.0.1 Ethernet3/0/2172.10.1.255/32 Direct 0 0 D 127.0.0.1 Ethernet3/0/2172.20.1.0/24 IBGP 255 0 RD 2001:4::1 policy1172.30.0.0/16 IBGP 255 0 RD 2001:4::1 SRv6-TE Flow Group
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
[PE1]8.3.9 Ping测试
8.3.9.1 测试说明
由于目前ENSP Pro的NE路由器版本不支持QoS,所以在PC侧设置DSCP值。
ping -Q 104 (设置DSCP为26,即AF31)
ping -Q 72 (设置DSCP为18(010010),即AF21, 计算方式:IP ToS为1个字节,共8个bit, 7到2bit位为:010010,补充1-0bit位:00,01001000换算10进制为72)
8.3.9.2 查看DSCP是否正确设置
CE1 ping测试时,在PE1-Eth3/0/2抓包,查看DSCP是否正确设置。
ping -Q 104 172.30.1.1 (设置DSCP为26(AF31)),抓包结果符合预期:
Frame 1: 98 bytes on wire (784 bits), 98 bytes captured (784 bits)
Ethernet II, Src: b2:e0:61:ae:0e:be (b2:e0:61:ae:0e:be), Dst: 38:03:00:11:03:02 (38:03:00:11:03:02)
Internet Protocol Version 4, Src: 172.10.1.10, Dst: 172.30.1.10100 .... = Version: 4.... 0101 = Header Length: 20 bytes (5)Differentiated Services Field: 0x68 (DSCP: AF31, ECN: Not-ECT)0110 10.. = Differentiated Services Codepoint: Assured Forwarding 31 (26).... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)Total Length: 84Identification: 0xe123 (57635)010. .... = Flags: 0x2, Don't fragment...0 0000 0000 0000 = Fragment Offset: 0Time to Live: 64Protocol: ICMP (1)Header Checksum: 0xfee9 [validation disabled][Header checksum status: Unverified]Source Address: 172.10.1.10Destination Address: 172.30.1.1
Internet Control Message Protocol
ping -Q 72 172.30.2.1 (设置DSCP为18(AF21)),抓包结果符合预期:
Frame 1: 98 bytes on wire (784 bits), 98 bytes captured (784 bits)
Ethernet II, Src: b2:e0:61:ae:0e:be (b2:e0:61:ae:0e:be), Dst: 38:03:00:11:03:02 (38:03:00:11:03:02)
Internet Protocol Version 4, Src: 172.10.1.10, Dst: 172.30.2.10100 .... = Version: 4.... 0101 = Header Length: 20 bytes (5)Differentiated Services Field: 0x48 (DSCP: AF21, ECN: Not-ECT)0100 10.. = Differentiated Services Codepoint: Assured Forwarding 21 (18).... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)Total Length: 84Identification: 0x21f7 (8695)010. .... = Flags: 0x2, Don't fragment...0 0000 0000 0000 = Fragment Offset: 0Time to Live: 64Protocol: ICMP (1)Header Checksum: 0xbd36 [validation disabled][Header checksum status: Unverified]Source Address: 172.10.1.10Destination Address: 172.30.2.1
Internet Control Message Protocol
8.3.9.3 CE1 ping -Q 104 172.30.1.1
在PE1-3/0/0和3/0/1同时抓包,结果能正常ping通,3/0/0能抓到发出的包,3/0/1没有抓到发出的包。经过抓包分析,此数据流通过SRv6 TE Policy policy10传输,符合预期:
Frame 2: 194 bytes on wire (1552 bits), 194 bytes captured (1552 bits)
Ethernet II, Src: 38:03:00:11:03:00 (38:03:00:11:03:00), Dst: 38:06:00:11:03:01 (38:06:00:11:03:01)
Internet Protocol Version 6, Src: ::, Dst: 3001:2::10:00110 .... = Version: 6.... 1111 1111 .... .... .... .... .... = Traffic Class: 0xff (DSCP: Unknown, ECN: CE).... 1111 11.. .... .... .... .... .... = Differentiated Services Codepoint: Unknown (63).... .... ..11 .... .... .... .... .... = Explicit Congestion Notification: Congestion Experienced (3).... 0000 0000 0000 0000 0001 = Flow Label: 0x00001Payload Length: 140Next Header: Routing Header for IPv6 (43)Hop Limit: 63Source Address: ::Destination Address: 3001:2::10:0Routing Header for IPv6 (Segment Routing)Next Header: IPIP (4)Length: 6[Length: 56 bytes]Type: Segment Routing (4)Segments Left: 2Last Entry: 2Flags: 0x00Tag: 0000Address[0]: 3001:4::4001:0Address[1]: 3001:4::10:0Address[2]: 3001:2::10:0
Internet Protocol Version 4, Src: 172.10.1.10, Dst: 172.30.1.10100 .... = Version: 4.... 0101 = Header Length: 20 bytes (5)Differentiated Services Field: 0x68 (DSCP: AF31, ECN: Not-ECT)0110 10.. = Differentiated Services Codepoint: Assured Forwarding 31 (26).... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)Total Length: 84Identification: 0xac39 (44089)010. .... = Flags: 0x2, Don't fragment...0 0000 0000 0000 = Fragment Offset: 0Time to Live: 63Protocol: ICMP (1)Header Checksum: 0x34d4 [validation disabled][Header checksum status: Unverified]Source Address: 172.10.1.10Destination Address: 172.30.1.1
Internet Control Message Protocol
8.3.9.4 CE1 ping -Q 72 172.30.2.1
在PE1-3/0/0和3/0/1同时抓包,结果能正常ping通,3/0/1能抓到发出的包,3/0/0没有抓到发出的包。经过抓包分析,此数据流通过SRv6 TE Policy policy11传输,符合预期:
Frame 2: 194 bytes on wire (1552 bits), 194 bytes captured (1552 bits)
Ethernet II, Src: 38:03:00:11:03:01 (38:03:00:11:03:01), Dst: 38:02:00:11:03:01 (38:02:00:11:03:01)Destination: 38:02:00:11:03:01 (38:02:00:11:03:01)Source: 38:03:00:11:03:01 (38:03:00:11:03:01)Type: IPv6 (0x86dd)
Internet Protocol Version 6, Src: ::, Dst: 3001:3::10:00110 .... = Version: 6.... 1111 1111 .... .... .... .... .... = Traffic Class: 0xff (DSCP: Unknown, ECN: CE).... 1111 11.. .... .... .... .... .... = Differentiated Services Codepoint: Unknown (63).... .... ..11 .... .... .... .... .... = Explicit Congestion Notification: Congestion Experienced (3).... 0000 0000 0000 0000 0001 = Flow Label: 0x00001Payload Length: 140Next Header: Routing Header for IPv6 (43)Hop Limit: 63Source Address: ::Destination Address: 3001:3::10:0Routing Header for IPv6 (Segment Routing)Next Header: IPIP (4)Length: 6[Length: 56 bytes]Type: Segment Routing (4)Segments Left: 2Last Entry: 2Flags: 0x00Tag: 0000Address[0]: 3001:4::4001:0Address[1]: 3001:4::10:0Address[2]: 3001:3::10:0
Internet Protocol Version 4, Src: 172.10.1.10, Dst: 172.30.2.10100 .... = Version: 4.... 0101 = Header Length: 20 bytes (5)Differentiated Services Field: 0x48 (DSCP: AF21, ECN: Not-ECT)0100 10.. = Differentiated Services Codepoint: Assured Forwarding 21 (18).... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)Total Length: 84Identification: 0x3819 (14361)010. .... = Flags: 0x2, Don't fragment...0 0000 0000 0000 = Fragment Offset: 0Time to Live: 63Protocol: ICMP (1)Header Checksum: 0xa814 [validation disabled][Header checksum status: Unverified]Source Address: 172.10.1.10Destination Address: 172.30.2.1
Internet Control Message Protocol
这篇关于ENSP PRO LAB笔记:配置SRv6(Part3)的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!






