本文主要是介绍DeepID face recognition,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
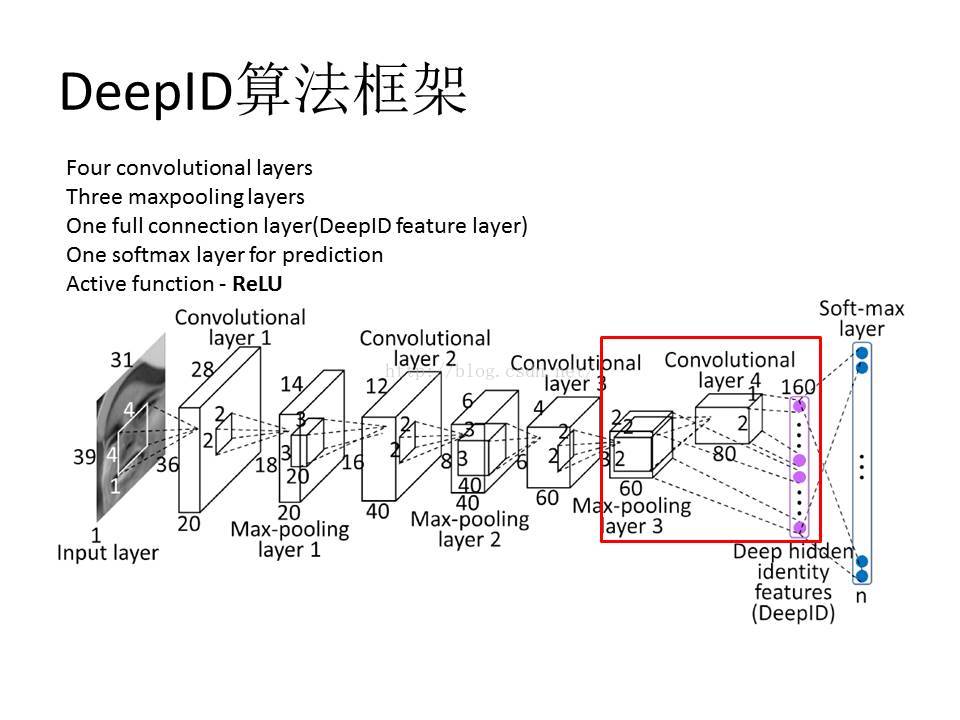

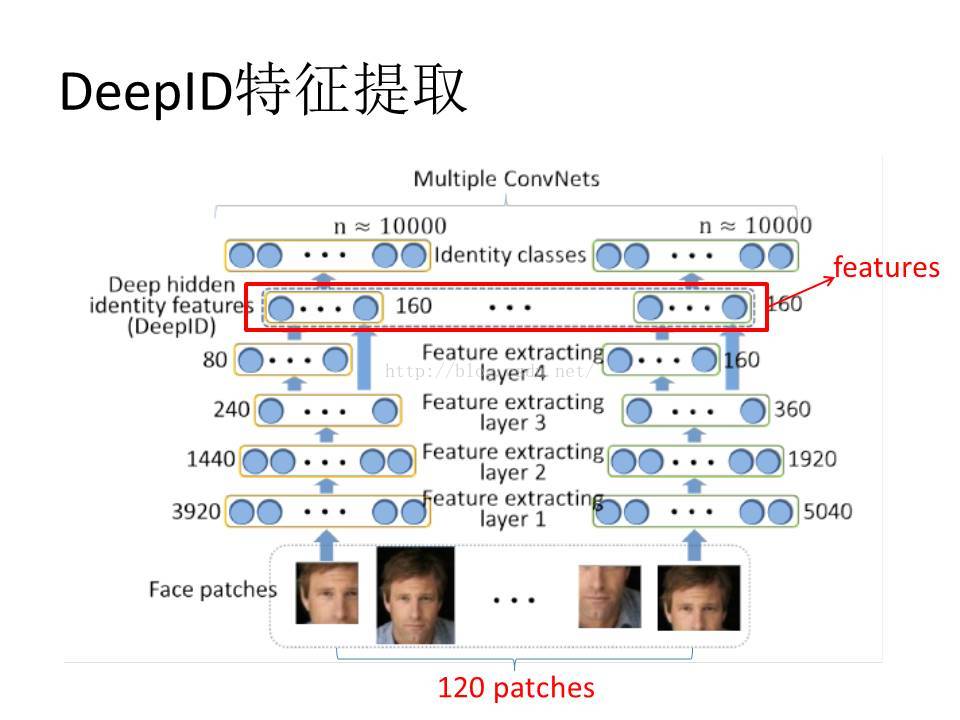
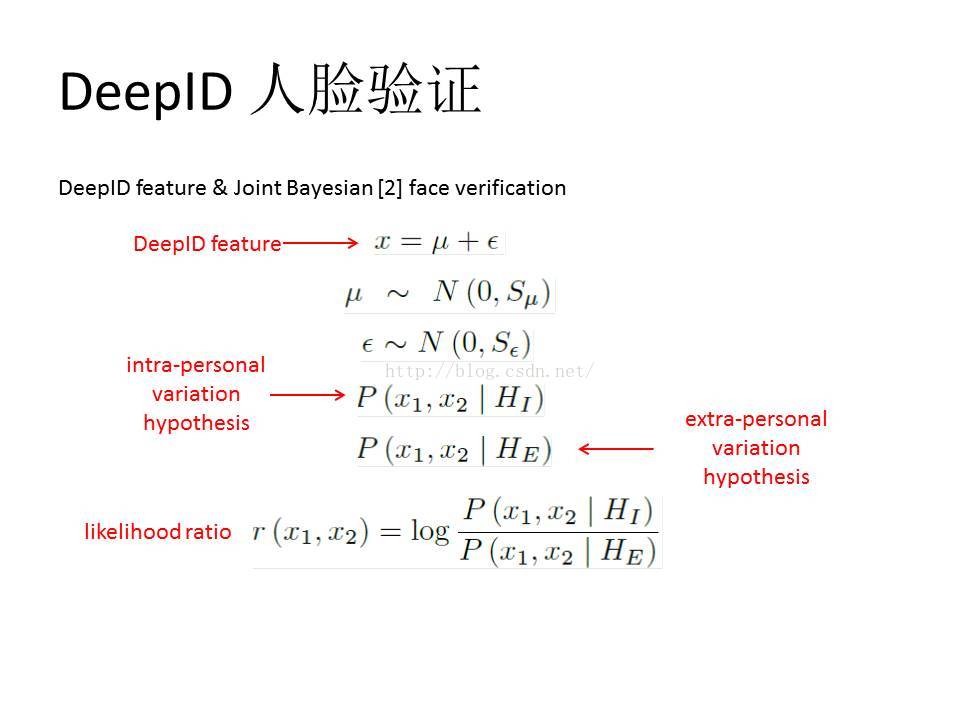
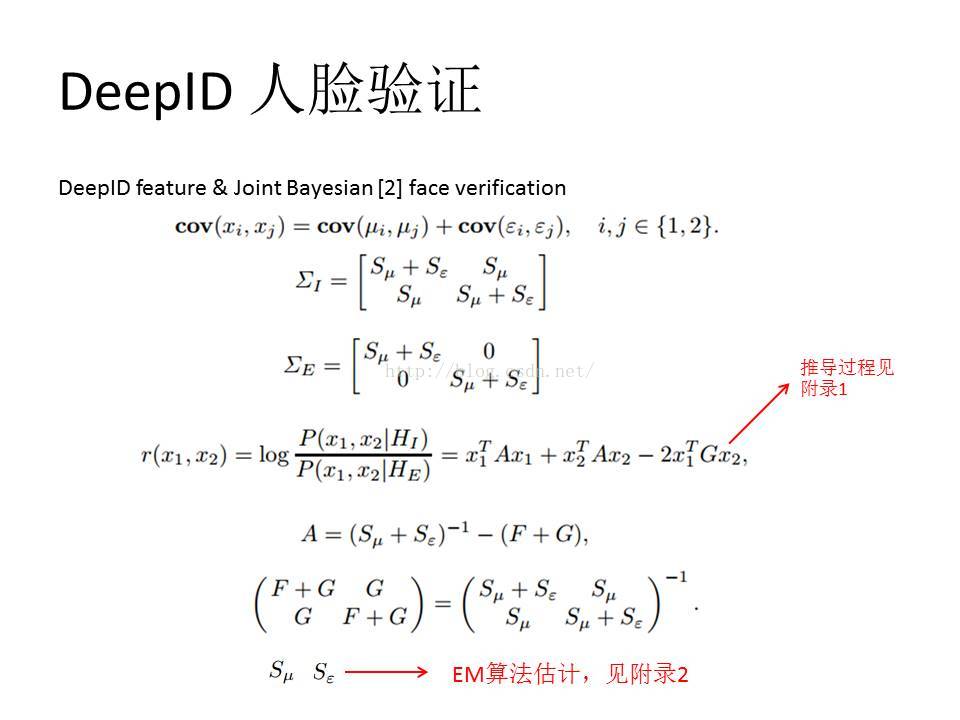

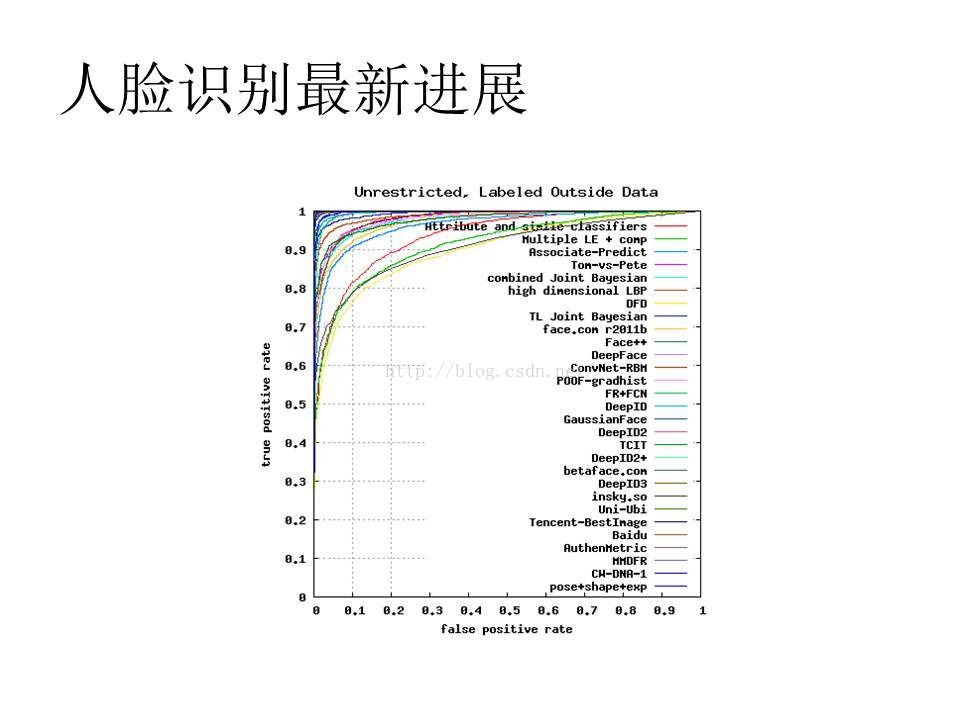
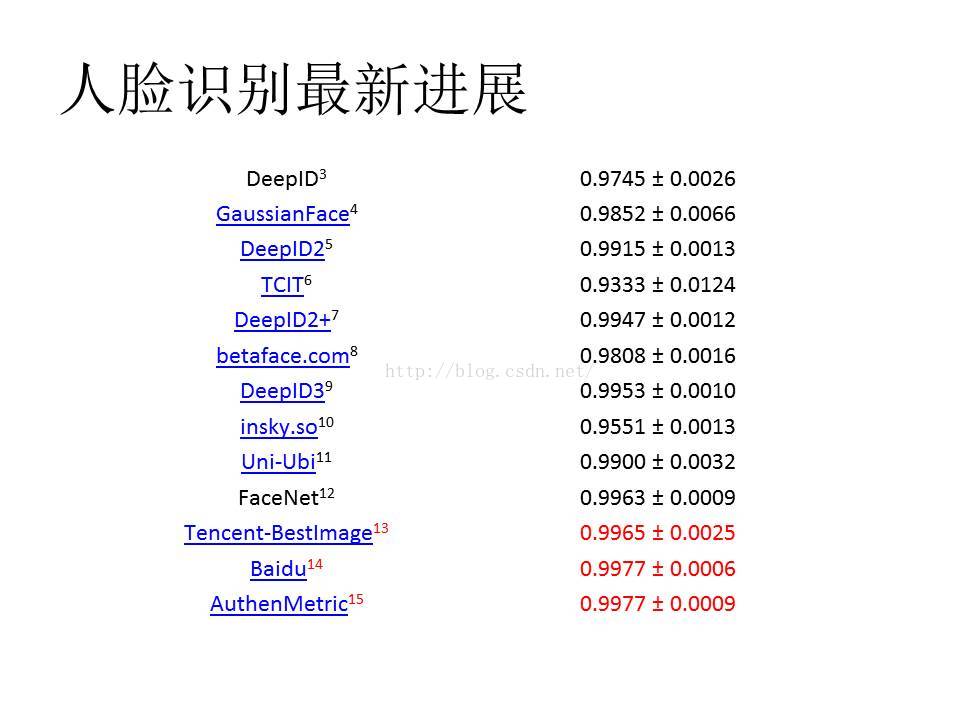




[1] Y. Sun, X. Wang, and X. Tang. Deepconvolutional networkcascadeforfacialpoint detection. In Proc. CVPR, 2013.
[2] D. Chen, X. Cao, L. Wang, F. Wen, and J.Sun. Bayesianfacerevisited: Ajoint formulation. In Proc. ECCV, 2012.
[3] Yi Sun, Xiaogang Wang, and XiaoouTang.DeepLearningFace Representation from Predicting 10,000 Classes.
Computer Vision and Pattern Recognition(CVPR), 2014.
[4] Chaochao Lu and Xiaoou Tang.Surpassing Human-LevelFace Verification Performance on LFW withGaussianFace.
[5] Yi Sun, Xiaogang Wang, and XiaoouTang.DeepLearningFace Representation by Joint Identification-Verification.
[6] Taiwan Colour & ImagingTechnology (TCIT) Brief method description:TCITcalculates the average position of thefacial area and judges the identical person or other person by face recognitionusing the facial area. Face Feature Positioning is applied to get the face datatemplate which is used to verify different faces.
[7] Yi Sun, Xiaogang Wang, and XiaoouTang. Deeply Learned Face Representations are Sparse, Selective, and Robust.arXiv:1412.1265, 2014, 2014.
[8] betaface.com Brief methoddescription:Wehaveused original LFW images, converted to greyscale, auto-aligned with ouralignment system and followed unrestricted protocol with labeled outside data:unrestricted protocol, labeled outside data results, LFW was not used fortraining or fine-tuning.
[9] Yi Sun, Ding Liang, Xiaogang Wang,and Xiaoou Tang. DeepID3: Face Recognition with Very Deep Neural Networks.arXiv:1502.00873, 2014.
[10] insky.so Brief methoddescription:Weusedoriginal LFW images to run the test procedure. Our system choose the rightimages according to the requirement auto and output the facial recognitionresults. And then, using the standard method to get the ROC curve. We have notdo training process using LFW images.
[11] Uni-Ubi Brief method description:Intest,we have used original LFW images, converted to greyscale, auto-aligned with ourface detector and alignment system and followed unrestricted protocol withlabeled outside data results, LFW was not used for training or fine-tuning.
[12] Florian Schroff, DmitryKalenichenko, and James Philbin. FaceNet: A Unified Embedding for Face Recognition and Clustering. Computer Visionand Pattern Recognition (CVPR), 2015.
[13] Tencent-BestImage Brief methoddescription: Wefollowedthe Unrestricted, Labeled Outside Data protocol and build our system combiningour alignment system, deep CNN network with 12 convolution layers and JointBayesian. The whole system is trained on BestImage Celebrities Face (BCF)dataset, which contains about 20,000 individuals and 1 million face images. TheBCF dataset has no intersection with LFW. We divide BCF into two subdataset-BCF training set and BCF validation set. We train out deep CNN networkon BCF training set with 20 different face patches and combine features of eachpatch with PCA and Joint Bayesian learned on BCF validation set.
[14] Jingtuo Liu, Yafeng Deng, Tao Bai,Zhengping Wei, and Chang Huang; Baidu Targeting Ultimate Accuracy: FaceRecognition via Deep Embedding.
[15] AuthenMetric Brief methoddescription:
The system consists of a workflow of facedetection, face alignment, face feature extraction, and face matching, allusing our own algorithms. 25 face feature extraction models were trained usinga deep network with a training set of 500,000 face images of 10,000 individuals(no LFW subjects are included in the training set), each on a different facepatch. The face matching (similarity of two faces) module was trained using adeep metric learning network, where a face is represented as the concatenationof the 25 feature vectors. The training and test follow the Unrestricted,Labeled Outside Data protocol.
[16] X. Cao, D. Wipf, F. Wen, G. Duan, and J.Sun. A practicaltransferlearningalgorithmfor face verification. In Proc. ICCV, 2013.
[17]https://www.microsoft.com/en-us/research/wp-content/uploads/2012/01/JointBayesian_Suppl.pdf
这篇关于DeepID face recognition的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!









