cryptography专题
Python密码学:cryptography库
在数字时代,确保数据的安全性和隐私至关重要。Python中的cryptography库是一个全面的包,为Python开发者提供了密码学原语和配方。它支持高级配方和常见密码学算法的低级接口。 cryptography库概述 cryptography库旨在易于使用且默认安全。它包括各种密码学操作的高级和低级API,如: 对称加密非对称加密哈希函数消息认证码(MAC)数字签名密钥管理 crypt
调用微信退款接口时出现System.Security.Cryptography.CryptographicException: 出现了内部错误 解决办法
我总结了一下出现证书无法加载的原因有以下三个 1.证书密码不正确,微信证书密码就是商户号 解决办法:请检查证书密码是不是和商户号一致 2.IIS设置错误,未加载用户配置文件 解决办法:找到网站使用的应用程序池-->右击-->高级设置-->打开如下图-->在加载用户配置文件选择true 3.如果以上两个方案都不能解决问题,就有可能是加载证书时没有给定证书存储标识
113 - Power of Cryptography
题目:113 - Power of Cryptography 题目大意:求k,k^n = p; 解题思路:k = p ^ (1/n);并且double的上限是1.7E+308,p的范围是1.0E + 101. #include<stdio.h>#include<math.h>int main() {double p, n;while (scanf("%lf%lf", &n,
Theory of Cryptography (TCC 2020)
分类文章编号格和加密1-8区块链9-15隐私保护、密钥交换和群组协议16-22简明论证23-29零知识30-36安全计算37-49最有影响力论文50量子和采样51-57信息论密码学和理想模型58-64秘密分享和编码65-71 LWE and Encryption 1. Lossiness and Entropic Hardness for Ring-LWE Zvika Brakerski,
Java加密体系结构参考指南-Java Cryptography Architecture
本文是从英文的官网摘了翻译的,用作自己的整理和记录。水平有限,欢迎指正。版本是:22 原文地址:https://docs.oracle.com/en/java/javase/22/security/java-cryptography-architecture-jca-reference-guide.html#GUID-815542FE-CF3D-407A-9673-CAE9840F6231
[amanhardikar] - Cryptography v1.1
From: http://www.amanhardikar.com/mindmaps/Cryptography.png
POJ2109_ Power of Cryptography
题目大意: 给你两个数,n,p ,求一个数K 使行 K^n == p. 题目测试样例与数据范围: 2 163 277 4357186184021382204544 431234 其中 4^2 == 16,3^3==27,1234*7==4357184021382204544 注意 1<=n<=200,1<=p<10^101. 题目保证有解且 1<=k
(python)cryptography-安全的加密
前言 cryptography 是一个广泛使用的 Python 加密库,提供了各种加密、哈希和签名算法的实现。它支持多种加密算法,如 AES、RSA、ECC 等,以及哈希函数(如 SHA-256、SHA-384 等)和数字签名算法(如 DSA、ECDSA 等). 目录 常见用途 密码学函数 主要功能 优点 缺点 总结 常见用途 数据加密 使用对
python安装cryptography 报错: error adding symbols: Bad value
python安装cryptography 报错: error adding symbols: Bad value 在安装python 的paramiko 模块时,paramiko 模块 依赖于cryptography, 会先安装cryptography $ pip install paramiko 报错: 一开始以为没有安装openssl, libssl-dev, pytho
POJ 2109 Power of Cryptography 数论
题意:求 k,令 k 的 n 次方和 p 相等。 题解:偷了下懒。 不过高精度还得再熟悉下,有空就系统补做一下吧。不过c++中类型的有效范围还是得记着: 类型 长度 有效数字 绝对值范围 float 32 6~7 10^(-37) ~ 10^38 double
Introduction to Cryptography with Java Applets
版权声明:原创作品,允许转载,转载时请务必以超链接形式标明文章原始出版、作者信息和本声明。否则将追究法律责任。 http://blog.csdn.net/topmvp - topmvp This book covers the mathematical basis of cryptography and cryptanalysis, like linear diophantine equati
Java Cryptography
版权声明:原创作品,允许转载,转载时请务必以超链接形式标明文章原始出版、作者信息和本声明。否则将追究法律责任。 http://blog.csdn.net/topmvp - topmvp Cryptography isn't all there is to security. But rendering information unintelligible to those without
Cryptography for Dummies
版权声明:原创作品,允许转载,转载时请务必以超链接形式标明文章原始出版、作者信息和本声明。否则将追究法律责任。 http://blog.csdn.net/topmvp - topmvp *Cryptography is the most effective way to achieve data security and is essential to e-commerce activitie
Networked RFID Systems and Lightweight Cryptography: Raising Barriers to Product Counterfeiting
版权声明:原创作品,允许转载,转载时请务必以超链接形式标明文章原始出版、作者信息和本声明。否则将追究法律责任。 http://blog.csdn.net/topmvp - topmvp The book consists of a collection of works on utilising the automatic identification technology provided
貪心::poj1328 radar installation poj2109 Power of Cryptography poj2586 Y2K Accounting Bug
貪心,就是步步為贏。 這是ACM知識表里基礎算法中的貪心部分,屬於水題範疇。 1. poj1328 radar installation 題目:照抄了。 Assume the coasting is an infinite straight line. Land is in one side of coasting, sea in the other. Each small island
(20191030已解决)Linux安装ccxt后ImportError: No module named cryptography.hazmat
crytography 网上的方法试了一通,都不成功。 后来发现Python版本是2.7 先将Python升级为3,然后用pip3安装所需要的各种包 ,就很顺利的运行下去了。不再出现如题问题。 《CentOS7.x安装Python3》
cryptography,一个神奇的 Python 库!
更多资料获取 📚 个人网站:ipengtao.com 大家好,今天为大家分享一个神奇的 Python 库 - cryptography。 Github地址:https://github.com/pyca/cryptography 在当今数字化时代,信息安全越来越受到重视。数据加密是保护数据安全的重要手段之一,而Python的cryptography库提供了丰富的功能来支持各种
解决cryptography库报错【DLL load failed while importing _rust】
解决 DLL load failed while importing _rust python使用库cryptography问题分析解决办法 python使用库cryptography 当 from cryptography.hazmat.bindings._rust import exceptions as rust_exceptions 时,会报错: ImportError
【Jasypt】you have not installed the Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction
在用Jasypt解密的时候遇到的问题, 报错:you have not installed the Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy 详细错误: 翻译之后可以看到缺少JCE,于是面向Google编程之后下载了JCE: 在这个网站 因为我是JDk8,这个网站没有JDK8版本对应的JDC,
UVa 113 / POJ 2109 Power of Cryptography (使用double处理大整数泰勒公式与误差分析)
113 - Power of Cryptography Time limit: 3.000 seconds http://uva.onlinejudge.org/index.php?option=com_onlinejudge&Itemid=8&category=99&page=show_problem&problem=49 http://poj.org/problem?id=2109
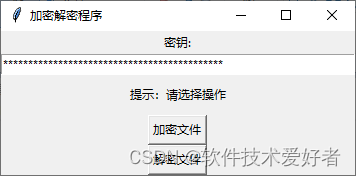
用Python和 Cryptography库给你的文件加密解密
用Python和 Cryptography库给你的文件加密解密 用Python和 Cryptography库给你的文件加把安全锁。 先介绍与加密解密有关的几个基本概念。 加密(Encryption):加密是将明文转换为密文的过程,使得未经授权的人无法读懂。 解密(Decryption):解密是将密文转换为明文的过程,使得原始信息可以被正确的人阅读。 密钥(Key):密钥是加密和解密过程中
Python的cryptography库介绍
Python的cryptography是密码库,源码地址为:https://github.com/pyca/cryptography,最新发布版本为41.0.7,license为Apache 2.0/BSD 3,它支持在Windows、Linux、macOS上使用。如果通过源码编译,需要依赖OpenSSL。Python版本需要为3.7+. 通过pip安装,执行: pip
Gregor and Cryptography
题目: 题目链接: 题解: 质数一定是奇数,所以选择 p − 1 p-1 p−1 和 p / 2 p/2 p/2 #include <bits/stdc++.h>using namespace std;int main(){int t;cin>>t;while(t--){long long n;cin>>n;cout<<n/2<<" "<<n-1<<endl;}return 0;
pip离线安装wheel包 python2 python3离线安装mysqldb cryptography mysql-python第三方库
python27版本离线安装python-mysql版本 一:下载可执行文件 二:点击直接安装 三:或者https://www.lfd.uci.edu/~gohlke/pythonlibs/#mysql-python该目录下mysqlclient‑1.4.6‑cp27‑cp27m‑win32.whl安装包 然后执行 pip install --no-index --find-links="."
pip离线安装wheel包 python2 python3离线安装mysqldb cryptography mysql-python第三方库
python27版本离线安装python-mysql版本 一:下载可执行文件 二:点击直接安装 三:或者https://www.lfd.uci.edu/~gohlke/pythonlibs/#mysql-python该目录下mysqlclient‑1.4.6‑cp27‑cp27m‑win32.whl安装包 然后执行 pip install --no-index --find-links="."
poj 2109 Power of Cryptography 贪心 暑假第四题
看了这道题的discuss,就想笑了,说是专坑不看评论的老手们,许多人打了二分+高精度,wr了,但最后一句话ac了。。。 这题怎么能分到贪心,我也是醉了。 1<=n<= 200, 1<=p<10101,1<=k<=109 我个人认为最保险的思路应该是log: k^n=p; ln(k)=ln(p)/n; k=exp( ln(p)/n ); 代码如下:



![[amanhardikar] - Cryptography v1.1](https://img-blog.csdn.net/20150719124748007)