本文主要是介绍单机 取证,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
一.环境准备
1.镜像文件

2.任务说明
镜像文件取证

3.工具
Autopsy 4.21.0

二.开始取证
1.将镜像导入到Autopsy中
打开





稍等一会
都选择默认

导入镜像


(1)evidence1

1.保存到桌面

2.stegsolve

50 4b 03 04压缩包文件头

3.010 Editor
用010 Editor打开随便一个压缩包,将里面的十六进制Ctrl+Shift+v复制粘贴到左边并保存压缩包

解压并打开得到Evidence1

4.转化为MD5值
certutil -hashfile D:\文件路径\eg2kX.jpg md5

(2)evidence2
1.导出文件并把、并保存到桌面

2.010 Editor
用010 Editor打开是zip压缩文件,修改后缀名,将.jpg修改为.zip


3.解压

4.转化为MD5值
certutil -hashfile D:文件路径\ZQOo2.jpg md5

(3)evidence3
1.导出并保存到桌面


2.png高宽一把梭工具(高度隐写)
用工具对图片进行高度隐写的解密


3.转化为MD5值
certutil -hashfile D:文件路径\p3qQ4.jpg md5

(4)evidence4
1.打开并保存到桌面

2.转化为MD5值
certutil -hashfile D:文件路径\nsOh2.png md5

(5)evidence5
1.打开并保存到桌面

2.010 Editor
看到文件头是png,修改压缩包后缀改为.png,得到一张图片

3.foremost
foremost 文件名 ,分离得到两张图片

4.010 Editor
用010 Editor打开导出的压缩包,Ctrl+f搜索 49 45 4E 44
发现有一串base32的编码

5.随波逐流
用随波逐流工具进行base32解码
6.转化为MD5值
certutil -hashfile D:文件路径\RVlYt.zip md5

(6)evidence6
1.导出并保存到桌面

2.file
file 显示文件类型

修改后缀名
3.Audacity
用Audacity打开音频文件,是莫斯电码
4.摩斯电码解密
莫斯电码在线网站:CTF在线工具-在线莫尔斯电码编码|在线莫尔斯电码解码|莫尔斯电码算法|Morse

5.转化为MD5值
certutil -hashfile D:文件路径\mkjRv.zip md5
(7)evidence7
1.导出并保存到桌面

2.010 Editor

修改后缀名

3.StegSolve
用StegSolve工具进行分析

4.转化为MD5值
certutil -hashfile D:文件路径\OR8iq.xml md5
(8)evidence8
1.导出并保存到桌面

2.010 Editor
用010 Editor打开是.png文件,修改后缀名

再用010 Editor打开,看到最后有一堆二进制

3.Python脚本
二进制转十进制,十进制转ASCII码,ASCII码进行base解密
import base64
def binary_to_decimal(binary_str):decimal_list = []for i in range(0,len(binary_str),8):binary = binary_str[i:i+8]decimal = int(binary,2)decimal_list.append(decimal)return decimal_list
binary_str = "01001011010010010101100101010101010101010101010100110010010100110100100101010110010101110100011101000011010101010011001101001101010010110101101001001000010001100100100101010110010000110100101101001001010101100100101101000110010010110100111001001011010011000100101101011010010000110101011101001001010101000101001101001110010001110100001001001010010001010101100101010110010000110101011101001111010000100100110001010110010001010100110101000010010100010101000001000110010010100100010101001011010011110100101101010000010010110100011001010111010001110100100101010011010000110101011001001011010100100100101001000101010010110101010100110010010101100100011101010110010100010101011001001101010101100100110001000101010010100101101001000111010101110101100101010101010100110100110101001011010100100101011001011000010000010101011001001011010100110100011101000110010000110101100001010101010101010101001101000110010011100101001001001110010001100100111100110011010000110101011101001010010110100100101001000110010010010101001101010011010001100100101101010110010010110101010001001011010100110011001001010111010001110100001001010011010001100100011101010110010100110100011001001011010010100100010101000110010010010101011001010100010100010100101101011010010010100100010001000001010011010100010001011010010010110100100101011001010001100100110101010100001100100101001101001001010101100100101001000101010100010101011001001011010101110100111101000010010000110101011001000111010101100101010001001101010010100100111001001100010001110101011101011010010000110101001101001010010101100101011001010110010001010101001001000011010101010100111001001110010010100100010101010001010101010101001001010010010010100100101001001010010101100100010101010010010011000100110101001010010110100100110001010111010110010101011001010011010011110100101101001110010010110100010101010101010100100100101101010011010010110101010100110010010101010100011101010110001100110100110001001101010100100100110001000101001100100011001000110010010100110100101001000010010010110100011001001101010100110101001101011000010010110100100101011001010001010100101100110110010010110101001101001001010110100100100001000101001101000101010001001010010100010100101101010101001101100101000100111101001111010011110100111101"
res=binary_to_decimal(binary_str)
data = ''
for i in res:data += chr(i)data=base64.b32decode(data).decode('utf-8')
data=base64.b64decode(data).decode('utf-8')
data=base64.b32decode(data).decode('utf-8')
data=bytes.fromhex(data).decode('utf-8')
data=base64.b32decode(data).decode('utf-8')
data=base64.b64decode(data).decode('utf-8')
data=base64.b32decode(data).decode('utf-8')
print(data)

4.转化为MD5值
certutil -hashfile D:文件路径\8cFQj.py md5

(9)evidence9
1.导出并保存到桌面

2.010 Editor
用010 Editor打开文件,是png,修改后缀名为.png文件


并解压

3.WPS
用WPS打开,发现什么都没有,右键填充为黑色

4.转化为MD5值
certutil -hashfile D:文件路径\jMH7w.js md5

(10)evidence10
1.导出并保存到桌面

2.010 Editor
用010 Editor打开,是png修改后缀名为.png


3.StegSolve
用StegSolve打开

4.转化为MD5值
certutil -hashfile D:文件路径\01d98.gif md5

三.取证结果
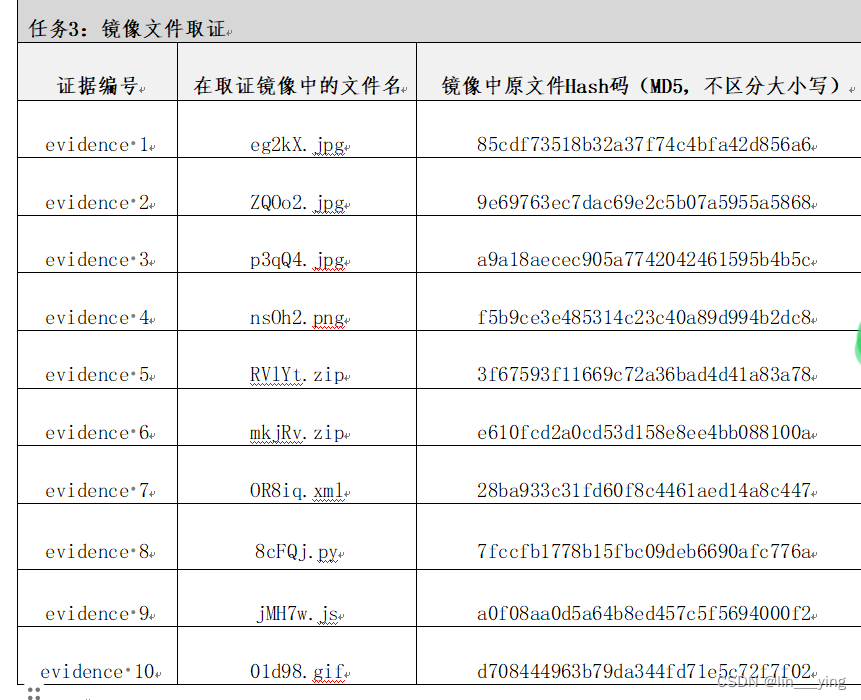
这篇关于单机 取证的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!