本文主要是介绍分布式搭载博客网站,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
一.运行环境:
| IP | 主机名 | 系统 | 服务 |
| 192.168.118.128 | Server-Web | Linux | Web |
| 192.168.118.131 | Server-NFS-DNS | Linux | NFS/DNS |
二.基础配置
[root@server ~]# hostnamectl set-hostname Server-Web
[root@server ~]# hostname
Server-Web[root@server ~]#vim /etc/hosts127.0.0.1 Server-Web
192.168.118.128 Server-Web
192.168.118.131 Server-NFS-DNS[root@server ~]# reboot
[root@node ~]# hostnamectl set-hostname Server-NFS-DNS
[root@node ~]# hostname
Server-NFS-DNS
[root@node ~]# reboot[root@Server-NFS-DNS ~]# vim /etc/hosts127.0.0.1 Server-NFS-DNS192.168.118.128 Server-Web
192.168.118.131 Server-NFS-DNS
相同操作:[root@Server-NFS-DNS ~]# systemctl start firewalld
[root@Server-NFS-DNS ~]# systemctl enable firewalld
相同操作:vim /etc/chrony.confserver ntp.aliyun.com iburstsystemctl restart chronydchronyc sources -vtimedatectl status

[root@Server-Web ~]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Created directory '/root/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa
Your public key has been saved in /root/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:kNDhoYpfc4CEb5NVN+WC39+sPbE2FausptyEzk5qs0s root@Server-Web
The key's randomart image is:
+---[RSA 3072]----+
| .. .o+.o.. |
|.. ..+.= o |
| ..oo = . . |
| .=. . o o . |
|....o . S . o|
| . . o .. o...|
| . E o .o ++ |
| .o* o. == |
| .+=*ooo..o |
+----[SHA256]-----+
[root@Server-Web ~]# ssh-copy-id 192.168.118.131
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
The authenticity of host '192.168.118.131 (192.168.118.131)' can't be established.
ED25519 key fingerprint is SHA256:OXWoro2/b049fk8uPMIfR4b5nj0v8M3PoMq+75B1jaM.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keysAuthorized users only. All activities may be monitored and reported.
root@192.168.118.131's password:Number of key(s) added: 1
Now try logging into the machine, with: "ssh '192.168.118.131'"
and check to make sure that only the key(s) you wanted were added.[root@Server-Web ~]# ssh 192.168.118.131
Authorized users only. All activities may be monitored and reported.
Authorized users only. All activities may be monitored and reported.
Last login: Wed Apr 17 11:39:31 2024 from 192.168.118.1
Welcome to 5.10.0-182.0.0.95.oe2203sp3.x86_64System information as of time: 2024年 04月 17日 星期三 11:44:11 CST
System load: 0.00
Processes: 193
Memory used: 10.4%
Swap used: 0%
Usage On: 12%
IP address: 192.168.118.131
Users online: 2
[root@Server-NFS-DNS ~]# exit
注销
Connection to 192.168.118.131 closed.
[root@Server-Web ~]#
Server-NFS-DNS:
[root@Server-NFS-DNS ~]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa
Your public key has been saved in /root/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:gwX4W59iAtyPksBTA6D0gKYuPvi2LDgkTbeysPG1pzU root@Server-NFS-DNS
The key's randomart image is:
+---[RSA 3072]----+
|o+.. .. |
|+.o + . |
|+. + + . |
|. = + oo. |
|.o + +.=S. . |
|=oo = + +.o |
|B= + oEo . |
|*++ .... |
| ==..o |
+----[SHA256]-----+
[root@Server-NFS-DNS ~]# ssh-copy-id 192.168.118.128
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keysAuthorized users only. All activities may be monitored and reported.
root@192.168.118.128's password:Number of key(s) added: 1
Now try logging into the machine, with: "ssh '192.168.118.128'"
and check to make sure that only the key(s) you wanted were added.[root@Server-NFS-DNS ~]# ssh 192.168.118.128
Authorized users only. All activities may be monitored and reported.
Authorized users only. All activities may be monitored and reported.
Last login: Wed Apr 17 11:39:22 2024 from 192.168.118.1
Welcome to 5.10.0-182.0.0.95.oe2203sp3.x86_64System information as of time: 2024年 04月 17日 星期三 11:48:15 CST
System load: 0.00
Processes: 195
Memory used: 10.2%
Swap used: 0%
Usage On: 12%
IP address: 192.168.118.128
Users online: 2
[root@Server-Web ~]# exit
注销
Connection to 192.168.118.128 closed.
[root@Server-NFS-DNS ~]#
三.环境搭建:
Server-Web: yum install nginx mariadb-server php* -y
Server-NFS-DNS:将wordpress上传到Server-NFS-DNS)端的/目录下
[root@Server-NFS-DNS ~]# cd /
[root@Server-NFS-DNS /]# ls
afs dev lib media proc sbin tmp wordpress-6.1-zh_CN.zip
bin etc lib64 mnt root srv usr
boot home lost+found opt run sys var
[root@Server-NFS-DNS /]# unzip wordpress-6.1-zh_CN.zip[root@Server-NFS-DNS /]# ls
afs dev lib media proc sbin tmp wordpress
bin etc lib64 mnt root srv usr wordpress-6.1-zh_CN.zip
boot home lost+found opt run sys var
[root@Server-NFS-DNS /]# cd wordpress
[root@Server-NFS-DNS wordpress]# ls
index.php wp-config-sample.php wp-mail.php
license.txt wp-content wp-settings.php
readme.html wp-cron.php wp-signup.php
wp-activate.php wp-includes wp-trackback.php
wp-admin wp-links-opml.php xmlrpc.php
wp-blog-header.php wp-load.php
wp-comments-post.php wp-login.php
四.将Server-NFS-DNS端的/wordpress 目录共享给 Server-Web
[root@Server-NFS-DNS wordpress]# yum install rpcbind nfs-utils -y
[root@Server-NFS-DNS wordpress]# cd ~
[root@Server-NFS-DNS ~]# vim /etc/exports
[root@Server-NFS-DNS ~]# chmod -Rf 777 /wordpress/wordpress 192.168.118.128(rw,sync,all_squash)
防火墙开启权限:
[root@Server-NFS-DNS ~]# firewall-cmd --permanent --zone public --add-service=mountd
success
[root@Server-NFS-DNS ~]# firewall-cmd --permanent --zone public --add-service=rpc-bind
success
[root@Server-NFS-DNS ~]# firewall-cmd --permanent --zone public --add-service=nfs
success
[root@Server-NFS-DNS ~]# firewall-cmd --reload
success
启动服务:
[root@Server-NFS-DNS ~]# systemctl start rpcbind
[root@Server-NFS-DNS ~]# systemctl start nfs-server
五.Server-web设置:
[root@Server-Web ~]#yum install rpcbind nfs-utils -y
[root@Server-Web ~]# showmount -e 192.168.118.131
Export list for 192.168.118.131:
192.168.118.128(rw,sync,all_squash) *
/wordpress *
[root@Server-Web ~]# mkdir /wp
[root@Server-Web ~]# mount -t nfs 192.168.118.131:/wordpress /wp
[root@Server-Web ~]# ls
anaconda-ks.cfg
[root@Server-Web ~]# cd /wp
[root@Server-Web wp]# ls
index.php wp-config-sample.php wp-mail.php
license.txt wp-content wp-settings.php
readme.html wp-cron.php wp-signup.php
wp-activate.php wp-includes wp-trackback.php
wp-admin wp-links-opml.php xmlrpc.php
wp-blog-header.php wp-load.php
wp-comments-post.php wp-login.php
六.Nginx设置:
[root@Server-Web ~]# firewall-cmd --permanent --zone public --add-service=http
success
[root@Server-Web ~]# firewall-cmd --reload
success
[root@Server-Web ~]# vim /etc/nginx/nginx.conf
七.修改wordpress配置文件
[root@Server-Web /]# cd wp
[root@Server-Web wp]# ls
index.php wp-config-sample.php wp-mail.php
license.txt wp-content wp-settings.php
readme.html wp-cron.php wp-signup.php
wp-activate.php wp-includes wp-trackback.php
wp-admin wp-links-opml.php xmlrpc.php
wp-blog-header.php wp-load.php
wp-comments-post.php wp-login.php
[root@Server-Web wp]# cp wp-config-sample.php wp-config.php
[root@Server-Web wp]# vim wp-config.phpdefine( 'DB_NAME', 'wordpress' );
/** Database username */
define( 'DB_USER', 'LYY' );/** Database password */
define( 'DB_PASSWORD', '123456' );
八.数据库设置
[root@Server-Web ~]# systemctl start mariadb
[root@Server-Web ~]# mysql
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 3
Server version: 10.5.22-MariaDB MariaDB ServerCopyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> create database wordpress;
Query OK, 1 row affected (0.001 sec)MariaDB [(none)]> create user 'LYY'@'localhost' identified by '123456';
Query OK, 0 rows affected (0.001 sec)MariaDB [(none)]> grant all on wordpress.* to 'LYY'@'localhost';
Query OK, 0 rows affected (0.001 sec)MariaDB [(none)]> exit
Bye
[root@Server-Web ~]# systemctl restart mariadb
[root@Server-Web ~]# systemctl restart nginx
九.windows设置

十.Server-NFS-DNS端配置DNS
[root@Server-NFS-DNS ~]# cd ~
[root@Server-NFS-DNS ~]# yum install bind -y[root@Server-NFS-DNS ~]# firewall-cmd --permanent --zone public --add-service=dns
success
[root@Server-NFS-DNS ~]# firewall-cmd --reload
success
[root@Server-NFS-DNS ~]# systemctl start named
[root@Server-NFS-DNS ~]# vim /etc/named.conf
[root@Server-NFS-DNS ~]# vim /etc/named.rfc1912.zones
zone "openlab.com" IN {
type master;
file "openlab.com.zone";
allow-update { none; };
};[root@Server-NFS-DNS ~]# cd /var/named/
[root@Server-NFS-DNS named]# cp -a named.localhost openlab.com.zone
[root@Server-NFS-DNS named]# vim openlab.com.zone
$TTL 1D
@ IN SOA openlab.com. admin.openlab.com. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS ns.openlab.com.
ns IN A 192.168.118.128
www IN A 192.168.118.128
bbs IN A 192.168.118.128[root@Server-NFS-DNS named]# systemctl restart named
十一.完成,输入域名访问
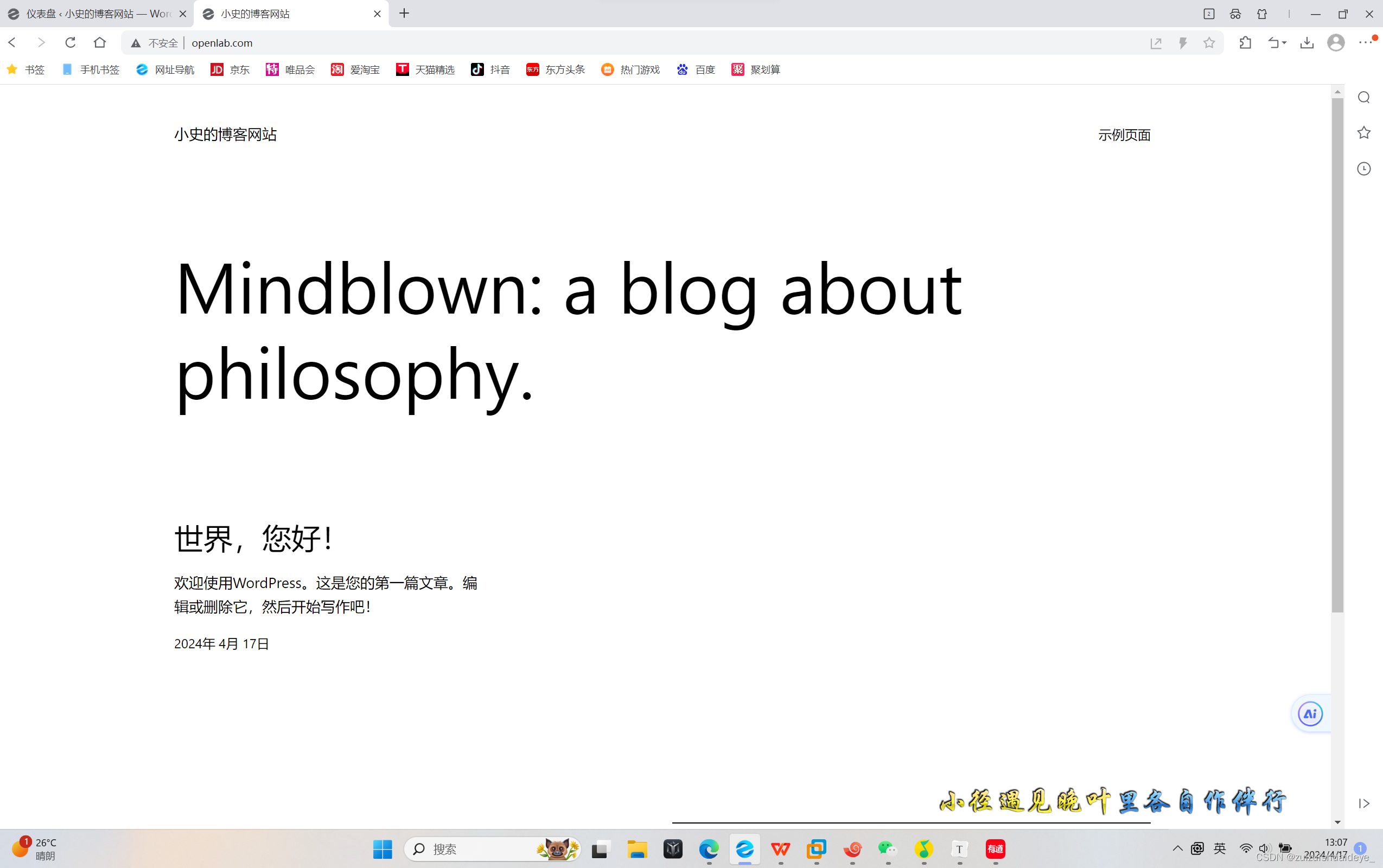
这篇关于分布式搭载博客网站的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!








