本文主要是介绍备考ICA----Istio实验10---为单个主机配置TLS Istio Ingress Gateway实验,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
备考ICA----Istio实验10—为单个主机配置 TLS Istio Ingress Gateway实验
1. 环境准备
部署httpbin
kubectl apply -f istio/samples/httpbin/httpbin.yaml
2. 证书生成
2.1 生成根证书
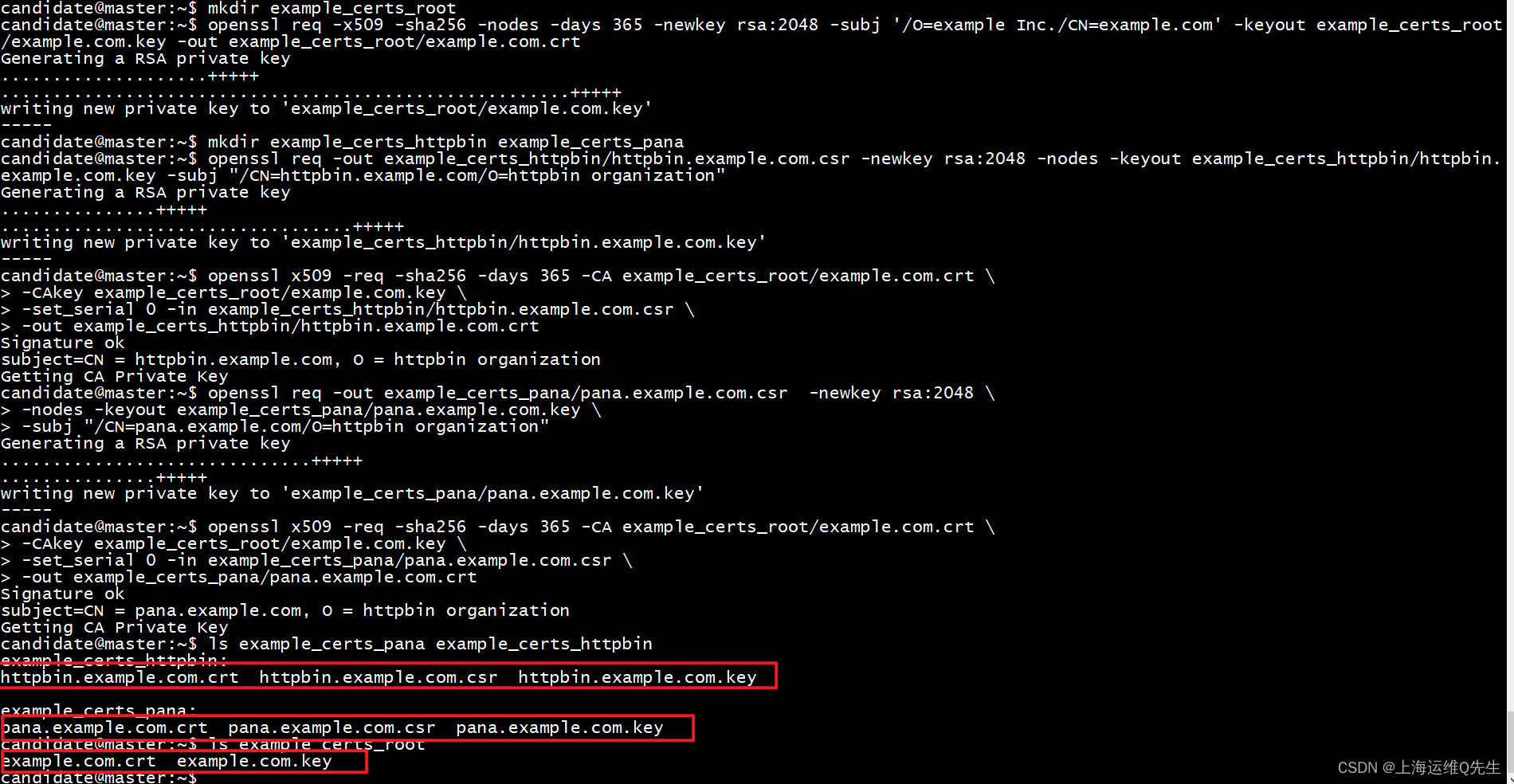
生成根证书keyfile和crt文件
mkdir example_certs_root
openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 \-subj '/O=example Inc./CN=example.com' \-keyout example_certs_root/example.com.key \-out example_certs_root/example.com.crt
2.2 生成httpbin.example.com证书
生成httpbin.example.com的keyfile和证书请求文件
mkdir example_certs_httpbin
openssl req -out example_certs_httpbin/httpbin.example.com.csr -newkey rsa:2048 \
-nodes -keyout example_certs_httpbin/httpbin.example.com.key \
-subj "/CN=httpbin.example.com/O=httpbin organization"
使用根证书签发httpbin.example.com的证书
这里我们为了后续实验只签发了1年
openssl x509 -req -sha256 -days 365 -CA example_certs_root/example.com.crt \
-CAkey example_certs_root/example.com.key \
-set_serial 0 -in example_certs_httpbin/httpbin.example.com.csr \
-out example_certs_httpbin/httpbin.example.com.crt
至此证书已经准备完毕
3. Istio配置
3.1 创建secret
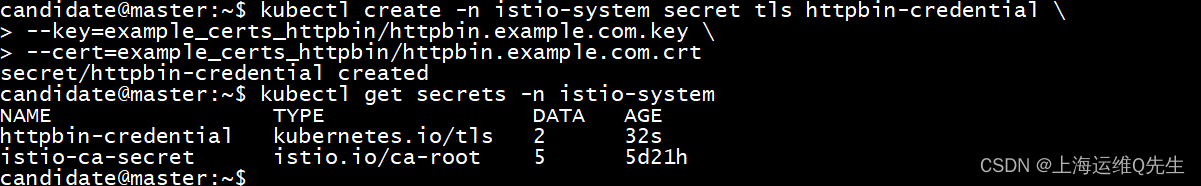
这个证书由于调用的是istio ingressgateway所以必须放在istio-system命名空间下.
kubectl create -n istio-system secret tls httpbin-credential \
--key=example_certs_httpbin/httpbin.example.com.key \
--cert=example_certs_httpbin/httpbin.example.com.crt
确认秘钥被正确创建
kubectl get secrets -n istio-system
3.2 为httpbin配置Gateway
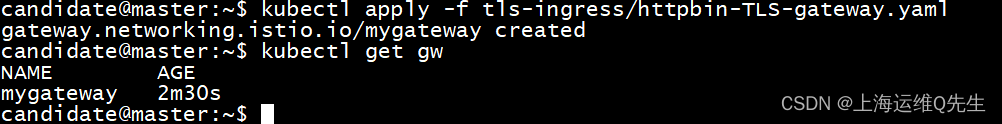
将证书应用给gw
tls-ingress/httpbin-TLS-gateway.yaml
apiVersion: networking.istio.io/v1beta1
kind: Gateway
metadata:name: mygateway
spec:selector:istio: ingressgateway # use istio default ingress gatewayservers:- port:number: 443name: httpsprotocol: HTTPStls:mode: SIMPLEcredentialName: httpbin-credential # must be the same as secrethosts:- httpbin.example.com
部署gw
kubectl apply -f tls-ingress/httpbin-TLS-gateway.yaml
3.3 为httpbin配置VS
tls-ingress/httpbin-TLS-VirtualService.yaml
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:name: httpbin
spec:hosts:- "httpbin.example.com"gateways:- mygatewayhttp:- match:- uri:prefix: /status- uri:prefix: /delayroute:- destination:port:number: 8000host: httpbin
部署
kubectl apply -f tls-ingress/httpbin-TLS-VirtualService.yaml
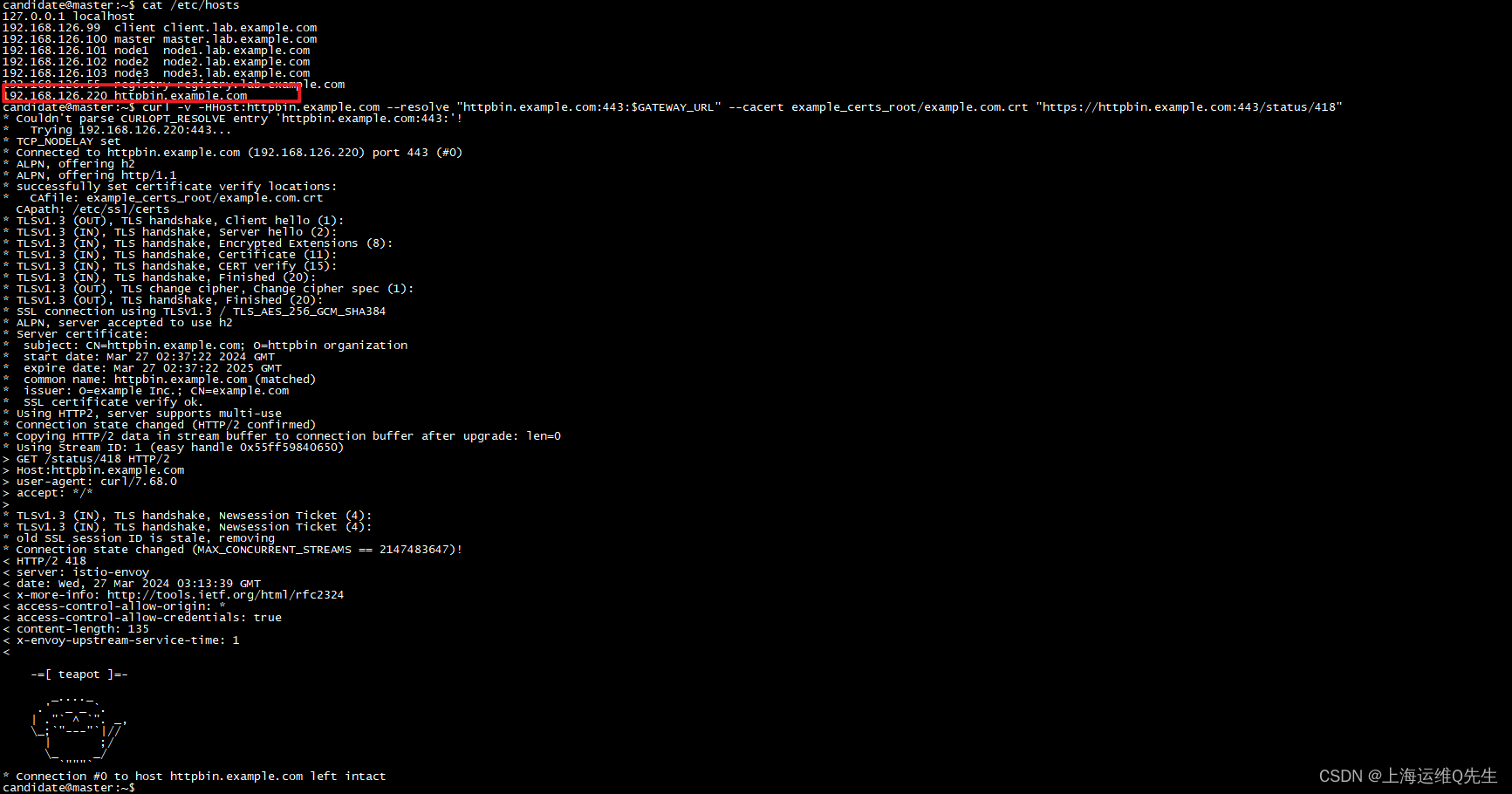
将istio-ingressgateway的ex-ip绑定到hosts后测试访问,服务访问正常,证书可以被正确加载
可以看到1年后我们的证书会到期.
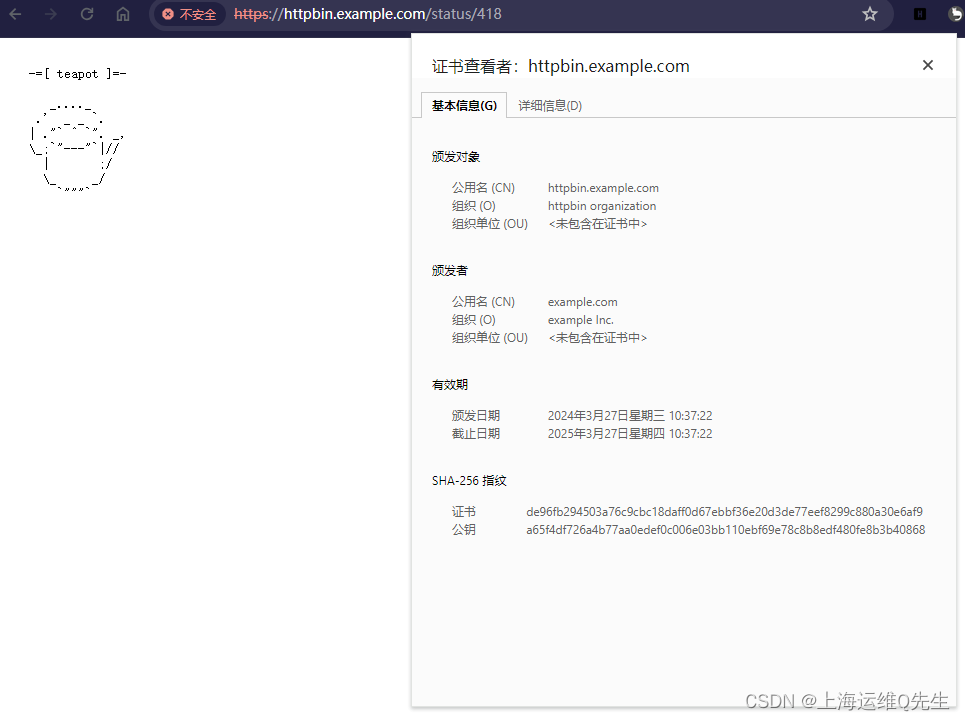
在本机上配置了hosts后测试也没有问题
3.4 轮转httpbin证书
当证书到期后我们需要更新证书,我们之前的证书是2025年到期.比如我们现在已经到期了,我们另外颁发1个10年的证书.
openssl req -out example_certs_httpbin/httpbin.example.com-2025.csr -newkey rsa:2048 \
-nodes -keyout example_certs_httpbin/httpbin.example.com-2025.key \
-subj "/CN=httpbin.example.com/O=httpbin organization"
使用根证书签发pana.example.com的证书,这里的-days 就是指定证书到期时间
openssl x509 -req -sha256 -days 3650 -CA example_certs_root/example.com.crt \
-CAkey example_certs_root/example.com.key \
-set_serial 0 -in example_certs_httpbin/httpbin.example.com-2025.csr \
-out example_certs_httpbin/httpbin.example.com-2025.crt
更新secret,更新秘钥后不需要去重启pod和gw等其他资源
kubectl delete secrets -n istio-system httpbin-credential
kubectl create -n istio-system secret tls httpbin-credential \
--key=example_certs_httpbin/httpbin.example.com-2025.key \
--cert=example_certs_httpbin/httpbin.example.com-2025.crt
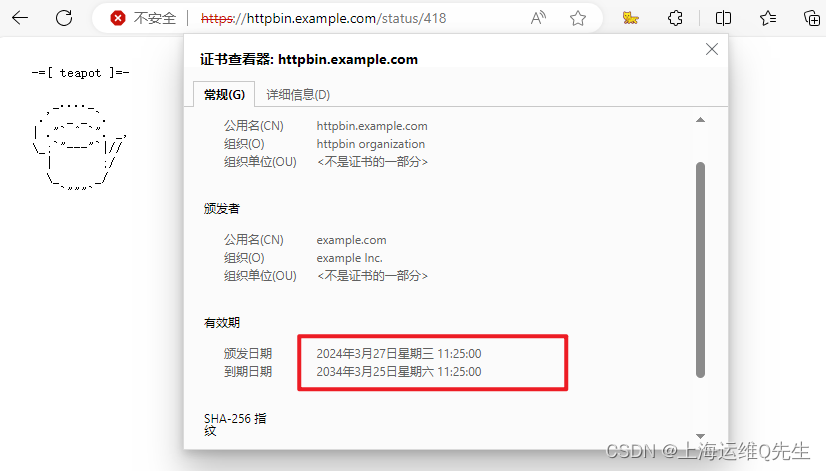
这里可以看到颁发日期已经是新的了,到期日期已经是10年后的日期
这篇关于备考ICA----Istio实验10---为单个主机配置TLS Istio Ingress Gateway实验的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!





