本文主要是介绍华为综合案例-普通WLAN全覆盖配置(2),希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
组网图
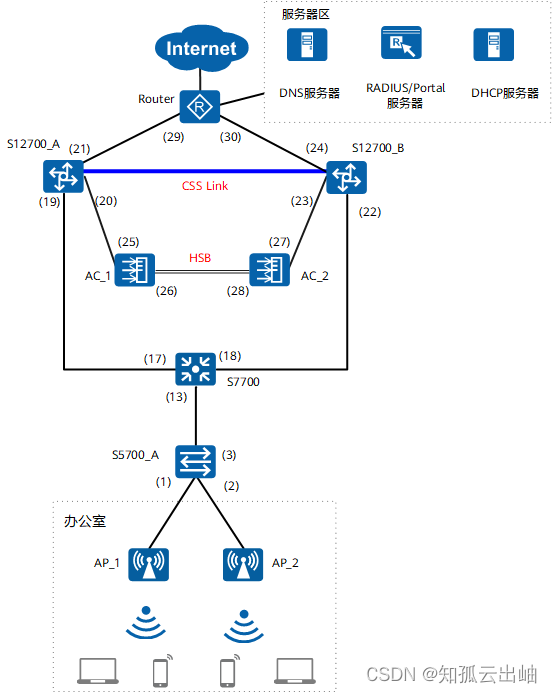
结果验证
在AC_1和AC_2上执行display ap all命令,检查当前AP的状态,显示以下信息表示AP上线成功。[AC_1] display ap all
Total AP information:
nor : normal [1]
ExtraInfo : Extra information
P : insufficient power supply
----------------------------------------------------------------------------------------------------
ID MAC Name Group IP Type State STA Uptime ExtraInfo
----------------------------------------------------------------------------------------------------
0 60de-4476-e360 AP_1 wlan_net 10.128.1.254 AP6050DN nor 0 10S -
----------------------------------------------------------------------------------------------------
Total: 1在AC_1和AC_2上执行display hsb-service 0命令,查看主备服务的建立情况,可以看到Service State字段的显示为Connected,说明主备服务通道已经成功建立。[AC_1] display hsb-service 0
Hot Standby Service Information:
----------------------------------------------------------Local IP Address : 10.1.1.253Peer IP Address : 10.1.1.254Source Port : 10241Destination Port : 10241Keep Alive Times : 5Keep Alive Interval : 3Service State : ConnectedService Batch Modules : Access-userShared-key : -
----------------------------------------------------------
[AC_2] display hsb-service 0
Hot Standby Service Information:
----------------------------------------------------------Local IP Address : 10.1.1.254Peer IP Address : 10.1.1.253Source Port : 10241Destination Port : 10241Keep Alive Times : 5Keep Alive Interval : 3Service State : ConnectedService Batch Modules : Access-userShared-key : -
----------------------------------------------------------在AC_1和AC_2上执行display hsb-group 0命令,查看HSB备份组的运行情况。[AC_1] display hsb-group 0
Hot Standby Group Information:
----------------------------------------------------------HSB-group ID : 0Vrrp Group ID : 1Vrrp Interface : Vlanif800Service Index : 0Group Vrrp Status : MasterGroup Status : ActiveGroup Backup Process : RealtimePeer Group Device Name : AC6805Peer Group Software Version : V200R010C00Group Backup Modules : Access-userAPDHCP
----------------------------------------------------------
[AC_2] display hsb-group 0
Hot Standby Group Information:
----------------------------------------------------------HSB-group ID : 0Vrrp Group ID : 1Vrrp Interface : Vlanif800Service Index : 0Group Vrrp Status : BackupGroup Status : InactiveGroup Backup Process : RealtimePeer Group Device Name : AC6805Peer Group Software Version : V200R010C00Group Backup Modules : Access-userAPDHCP
----------------------------------------------------------用户是否能够通过RADIUS模板的认证。(已在RADIUS服务器上配置了测试用户test@huawei.com,用户密码123456)。[AC_1] test-aaa test@huawei.com 123456 radius-template radius_huawei
Info: Account test succeed.- 完成配置后,用户可通过无线终端搜索到SSID为wlan_net的无线网络,用户关联到无线网络上后,无线终端能够被分配相应的IP地址。STA上打开浏览器访问Internet,自动跳转到Portal服务器提供的页面,在页面上输入正确的用户名(test@huawei.com)和密码(123456),认证通过后可以正常访问Internet。
- 用户使用手机可以正常使用漫游业务。
配置脚本
AC_1和AC_2的配置文件对比(加粗内容为AC_1和AC_2上的双机备份配置和无线配置同步配置,斜体内容为AC_1自动同步到AC_2的公有配置)AC_1AC_2#sysname AC_1
#
radius-server source ip-address 172.16.1.1
#
vrrp recover-delay 60
#
vlan batch 700 to 701 800 810 820
#
authentication-profile name wlan_net_dot1x_authdot1x-access-profile huaweiauthentication-scheme radius_huaweiaccounting-scheme radius_huaweiradius-server radius_huawei
authentication-profile name wlan_net_portal_authmac-access-profile macportal-access-profile wlan_netfree-rule-template default_free_ruleauthentication-scheme radius_huaweiaccounting-scheme radius_huaweiradius-server radius_huawei
#
web-auth-server source-ip 172.16.1.1
#
dhcp enable
#
dhcp snooping enable
#
vlan 700description wlan_netdhcp snooping enable
vlan 701description wlan_netdhcp snooping enable
vlan 800description AP-management-vlan
#
radius-server template radius_huaweiradius-server shared-key cipher %^%#b@)bNet)(Z)!N9T>p8kM(8w/N&3\>!KKg=DO<!R+%^%#radius-server authentication 172.16.1.254 1812 weight 80radius-server accounting 172.16.1.254 1813 weight 80radius-server timeout 1
radius-server authorization 172.16.1.254 shared-key cipher %^%#M"yY$,}"a8U12iTP4:u6nI-;9G/!eH`FJ:UePsB,%^%#
#
free-rule-template name default_free_rulefree-rule 1 destination ip 172.16.1.253 mask 255.255.255.255
#
url-template name huaweiurl http://172.16.1.254:8080/portalurl-parameter ssid ssid redirect-url url
#
web-auth-server huaweiserver-ip 172.16.1.254port 50200shared-key cipher %^%#6/j36uiW:M7dx'"L*2M*TN~P7t*K0(w9'=ER4bZ"%^%#url-template huawei
#
portal-access-profile name wlan_netweb-auth-server huawei direct
#
aaaauthentication-scheme radius_huaweiauthentication-mode radiusaccounting-scheme radius_huaweiaccounting-mode radiusaccounting realtime 15
#
interface Vlanif800ip address 10.128.1.2 255.255.255.0vrrp vrid 1 virtual-ip 10.128.1.1admin-vrrp vrid 1vrrp vrid 1 priority 120vrrp vrid 1 preempt-mode timer delay 1200dhcp select interfacedhcp server excluded-ip-address 10.128.1.1 10.128.1.3
#
interface Vlanif810ip address 10.1.1.253 255.255.255.252
#
interface Vlanif820ip address 172.16.1.2 255.255.255.0vrrp vrid 2 virtual-ip 172.16.1.1vrrp vrid 2 track admin-vrrp interface Vlanif800 vrid 1 unflowdown
#
interface GigabitEthernet0/0/23description Connect to AC_2_0/0/23port link-type trunkundo port trunk allow-pass vlan 1port trunk allow-pass vlan 800 810 820
#
interface GigabitEthernet0/0/24description Connect to S12700_A_1/1/0/20port link-type trunkundo port trunk allow-pass vlan 1port trunk allow-pass vlan 700 to 701 800 820
#
capwap source ip-address 10.128.1.1
#
hsb-service 0service-ip-port local-ip 10.1.1.253 peer-ip 10.1.1.254 local-data-port 10241 peer-data-port 10241
#
hsb-group 0track vrrp vrid 1 interface Vlanif800bind-service 0hsb enable
#
hsb-service-type access-user hsb-group 0
#
hsb-service-type dhcp hsb-group 0
#
hsb-service-type ap hsb-group 0
#
wlantraffic-profile name wlan_netuser-isolate l2security-profile name opensecurity opensecurity-profile name dot1xsecurity wpa2 dot1x aesssid-profile name wlan_net_portal_authssid wlan_net_portal_authssid-profile name wlan_net_dot1x_authssid wlan_net_dot1x_authdot11r enablevap-profile name wlan_net_portal_authservice-vlan vlan-id 700ssid-profile wlan_net_portal_authsecurity-profile opentraffic-profile wlan_netauthentication-profile wlan_net_portal_authip source check user-bind enablearp anti-attack check user-bind enablelearn-client-address dhcp-strictvap-profile name wlan_net_dot1x_authservice-vlan vlan-id 701ssid-profile wlan_net_dot1x_authsecurity-profile dot1xtraffic-profile wlan_netauthentication-profile wlan_net_dot1x_authip source check user-bind enablearp anti-attack check user-bind enablelearn-client-address dhcp-strictradio-2g-profile name 2Gradio-5g-profile name 5Gport-link-profile name defaultap-group name wlan_netradio 0radio-2g-profile 2Gvap-profile wlan_net_portal_auth wlan 1vap-profile wlan_net_dot1x_auth wlan 2radio 1radio-5g-profile 5Gvap-profile wlan_net_portal_auth wlan 1vap-profile wlan_net_dot1x_auth wlan 2radio 2vap-profile wlan_net_portal_auth wlan 1vap-profile wlan_net_dot1x_auth wlan 2ap-id 1 ap-mac 60de-4476-e360ap-name AP_1ap-group wlan_netmaster controllermaster-redundancy track-vrrp vrid 1 interface Vlanif800master-redundancy peer-ip ip-address 10.1.1.254 local-ip ip-address 10.1.1.253 psk %^%#HdgY%JtWL>H[k@Rs~<-)6,u4A&I1e5mO%jVwv~*N%^%#
#
dot1x-access-profile name huawei
#
mac-access-profile name mac
#
return
#sysname AC_2
#
radius-server source ip-address 172.16.1.1
#
vrrp recover-delay 60
#
vlan batch 700 to 701 800 810 820
#
authentication-profile name wlan_net_dot1x_authdot1x-access-profile huaweiauthentication-scheme radius_huaweiaccounting-scheme radius_huaweiradius-server radius_huawei
authentication-profile name wlan_net_portal_authmac-access-profile macportal-access-profile wlan_netfree-rule-template default_free_ruleauthentication-scheme radius_huaweiaccounting-scheme radius_huaweiradius-server radius_huawei
#
web-auth-server source-ip 172.16.1.1
#
dhcp enable
#
dhcp snooping enable
#
vlan 700description wlan_netdhcp snooping enable
vlan 701description wlan_netdhcp snooping enable
vlan 800description AP-management-vlan
#
radius-server template radius_huaweiradius-server shared-key cipher %^%#b@)bNet)(Z)!N9T>p8kM(8w/N&3\>!KKg=DO<!R+%^%#radius-server authentication 172.16.1.254 1812 weight 80radius-server accounting 172.16.1.254 1813 weight 80radius-server timeout 1
radius-server authorization 172.16.1.254 shared-key cipher %^%#M"yY$,}"a8U12iTP4:u6nI-;9G/!eH`FJ:UePsB,%^%#
#
free-rule-template name default_free_rulefree-rule 1 destination ip 172.16.1.253 mask 255.255.255.255
#
url-template name huaweiurl http://172.16.1.254:8080/portalurl-parameter ssid ssid redirect-url url
#
web-auth-server huaweiserver-ip 172.16.1.254port 50200shared-key cipher %^%#6/j36uiW:M7dx'"L*2M*TN~P7t*K0(w9'=ER4bZ"%^%#url-template huawei
#
portal-access-profile name wlan_netweb-auth-server huawei direct
#
aaaauthentication-scheme radius_huaweiauthentication-mode radiusaccounting-scheme radius_huaweiaccounting-mode radiusaccounting realtime 15
#
interface Vlanif800ip address 10.128.1.3 255.255.255.0vrrp vrid 1 virtual-ip 10.128.1.1admin-vrrp vrid 1dhcp select interfacedhcp server excluded-ip-address 10.128.1.1 10.128.1.3
#
interface Vlanif810ip address 10.1.1.254 255.255.255.252
#
interface Vlanif820ip address 172.16.1.3 255.255.255.0vrrp vrid 2 virtual-ip 172.16.1.1vrrp vrid 2 track admin-vrrp interface Vlanif800 vrid 1 unflowdown
#
interface GigabitEthernet0/0/23description Connect to AC_1_0/0/23port link-type trunkundo port trunk allow-pass vlan 1port trunk allow-pass vlan 800 810 820
#
interface GigabitEthernet0/0/24description Connect to S12700_B_2/1/0/23port link-type trunkundo port trunk allow-pass vlan 1port trunk allow-pass vlan 700 to 701 800 820
#
capwap source ip-address 10.128.1.1
#
hsb-service 0service-ip-port local-ip 10.1.1.254 peer-ip 10.1.1.253 local-data-port 10241 peer-data-port 10241
#
hsb-group 0track vrrp vrid 1 interface Vlanif800bind-service 0hsb enable
#
hsb-service-type access-user hsb-group 0
#
hsb-service-type dhcp hsb-group 0
#
hsb-service-type ap hsb-group 0
#
wlantraffic-profile name wlan_netuser-isolate l2security-profile name opensecurity opensecurity-profile name dot1xsecurity wpa2 dot1x aesssid-profile name wlan_net_portal_authssid wlan_net_portal_authssid-profile name wlan_net_dot1x_authssid wlan_net_dot1x_authdot11r enablevap-profile name wlan_net_portal_authservice-vlan vlan-id 700ssid-profile wlan_net_portal_authsecurity-profile opentraffic-profile wlan_netauthentication-profile wlan_net_portal_authip source check user-bind enablearp anti-attack check user-bind enablelearn-client-address dhcp-strictvap-profile name wlan_net_dot1x_authservice-vlan vlan-id 701ssid-profile wlan_net_dot1x_authsecurity-profile dot1xtraffic-profile wlan_netauthentication-profile wlan_net_dot1x_authip source check user-bind enablearp anti-attack check user-bind enablelearn-client-address dhcp-strictradio-2g-profile name 2Gradio-5g-profile name 5Gport-link-profile name defaultap-group name wlan_netradio 0radio-2g-profile 2Gvap-profile wlan_net_portal_auth wlan 1vap-profile wlan_net_dot1x_auth wlan 2radio 1radio-5g-profile 5Gvap-profile wlan_net_portal_auth wlan 1vap-profile wlan_net_dot1x_auth wlan 2radio 2vap-profile wlan_net_portal_auth wlan 1vap-profile wlan_net_dot1x_auth wlan 2ap-id 1 ap-mac 60de-4476-e360ap-name AP_1ap-group wlan_netmaster controllermaster-redundancy track-vrrp vrid 1 interface Vlanif800master-redundancy peer-ip ip-address 10.1.1.253 local-ip ip-address 10.1.1.254 psk %^%#>j6VS_;z=54_*oRNpd<<'_-8DRj,,Y!T~_,Z$4yI%^%#
#
dot1x-access-profile name huawei
#
mac-access-profile name mac
#
return
集群系统#
sysname CSS
#
vlan batch 730 800 820
#
interface Eth-Trunk1 description Connect to S7700_Eth-Trunk1port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 730 800
#
interface GigabitEthernet1/1/0/19eth-trunk 1
#
interface GigabitEthernet1/1/0/20description Connect to AC_1_0/0/24port link-type trunkundo port trunk allow-pass vlan 1port trunk allow-pass vlan 730 800 820
#
interface GigabitEthernet1/1/0/21description Connect to Router_0/0/29port link-type trunkundo port trunk allow-pass vlan 1port trunk allow-pass vlan 730 820
#
interface GigabitEthernet1/1/1/7mad detect mode direct
#
interface GigabitEthernet2/1/0/18description Connect to Router_0/0/30port link-type trunkundo port trunk allow-pass vlan 1port trunk allow-pass vlan 730 820
#
interface GigabitEthernet2/1/0/22eth-trunk 1
#
interface GigabitEthernet2/1/0/23description Connect to AC_2_0/0/24port link-type trunkundo port trunk allow-pass vlan 1port trunk allow-pass vlan 730 800 820
#
interface GigabitEthernet2/1/1/7mad detect mode direct
#
return
S7700#
sysname S7700
#
vlan batch 730 800
#
interface Eth-Trunk1description Connect to S12700_Eth-Trunk1 port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 730 800
#
interface Vlanif730ip address 10.173.1.1 255.255.252.0dhcp select relaydhcp relay server-ip 172.16.1.252
#
interface GigabitEthernet1/0/3description Connect to S5700_A_0/0/3port link-type trunkundo port trunk allow-pass vlan 1port trunk allow-pass vlan 730 800
#
interface GigabitEthernet1/0/17eth-trunk 1
#
interface GigabitEthernet2/0/18eth-trunk 1
#
return
S5700_A#
sysname S5700_A
#
vlan batch 730 800
#
traffic classifier huawei
if-match destination-mac 0100-5e00-0000 mac-address-mask ffff-ff00-0000
#
traffic behavior huawei
statistic enable
car cir 100
#
traffic policy huawei
classifier huawei behavior huawei
#
lldp enable
#
interface GigabitEthernet0/0/1description Connect to AP_1port link-type trunkport trunk pvid vlan 800 undo port trunk allow-pass vlan 1port trunk allow-pass vlan 730 800port-isolate enable group 1 stp edged-port enable traffic-policy huawei inboundtraffic-policy huawei outbound
#
interface GigabitEthernet0/0/2description Connect to AP_2port link-type trunkport trunk pvid vlan 800undo port trunk allow-pass vlan 1port trunk allow-pass vlan 730 800port-isolate enable group 1 stp edged-port enable traffic-policy huawei inboundtraffic-policy huawei outbound
#
interface GigabitEthernet0/0/3description Connect to S7700_1/0/3port link-type trunkundo port trunk allow-pass vlan 1port trunk allow-pass vlan 730 800
#
return
父主题: 综合案例-普通WLAN覆盖
版权所有 © 华为技术有限公司
< 上一节下一节 >场景化推荐配置
大广播域场景下的流量优化
在企业与园区场景中,通常采用单个大型子网的设计。单个大型子网简化了VLAN的配置、没有繁杂的漫游配置、故障定位简单。但是,单个大型子网使用大广播域,带来了大量报文复制发送、CPU使用率过高等问题。
通过将广播报文转单播处理、抑制未知单播、对AP多播报文进行限速等方法降低CPU处理量,以支撑大广播域场景。
# 打开mDNS单播应答功能。AC作为mDNS网关,对于mDNS服务请求报文,由AC进行服务单播代答。进而减少AC的复制流程。(缺省关闭,推荐开启)
<AC6805> system-view [AC6805] mdns unicast-reply enable
# 打开IGMP Snooping功能和丢弃VLAN内收到的未知组播流功能。当主机和上游三层设备之间传递的IGMP协议报文通过二层组播设备时,IGMP Snooping分析报文携带的信息,根据这些信息建立和维护二层组播转发表,从而指导组播数据在数据链路层按需转发。(缺省关闭,推荐开启)
<AC6805> system-view
[AC6805] wlan
[AC6805-wlan-view] traffic-profile name default
[AC6805-wlan-traffic-prof-default] igmp-snooping enable
[AC6805-wlan-traffic-prof-default] quit
[AC6805-wlan-view] quit
[AC6805] vlan 10
[AC6805-vlan10] multicast drop-unknown
# 打开ARP/ND/DHCP报文转单播处理功能。(缺省开启,推荐开启)<AC6805> system-view
[AC6805] wlan
[AC6805-wlan-view] traffic-profile name default
[AC6805-wlan-traffic-prof-default] traffic-optimize bcmc unicast-send arp nd dhcp
# 打开ARP/ND/DHCP抑制功能。当空口广播或组播协议报文转为单播报文失败时,丢弃这些报文。(缺省开启,推荐开启)<AC6805> system-view
[AC6805] wlan
[AC6805-wlan-view] traffic-profile name default
[AC6805-wlan-traffic-prof-default] traffic-optimize bcmc unicast-send mismatch-action drop
VR场景下的流量优化
AP对接VR设备场景下,由于丢包重传对用户体验影响较大,用户可将业务保障功能模式设置为可靠性优先,即在满足VR吞吐量要求下,通过空口适当降速,减小丢包、重传引起的抖动、延迟,提升用户体验。建议用户在VR游戏场景下,配置业务保障功能模式为可靠性优先,在VR视频场景下,建议配置为性能优先。# 配置业务保障功能模式为可靠性优先。(缺省为性能优先)<AC6805> system-view
[AC6805] wlan
[AC6805-wlan-view] ssid-profile name ssid1
[AC6805-wlan-ssid-prof-ssid1] service-guarantee reliability-first
开掘常见问题
AP上线失败
问题描述
AP上线失败。
可能原因
- 前期PoE交换机PoE参数配置错误
- AC和AP间的链路没打通
- 施工人员网线没做好
以上原因占据平时排查工作大部分时间。更多原因和解决处理方法请参考故障启示录中的AP上线失败。
处理过程
处理过程如下:
- 对照AP设备《产品描述》中指定的PoE供电协议标准,检查PoE供电设备是否满足。如果不符,则需要更换为满足要求的PoE供电设备。
对于华为PoE交换机,在系统视图下执行display poe power命令,根据回显信息中的USMPW(mW)值可以确定其供电协议标准:15400表示该交换机支持的PoE供电协议是IEEE 802.3af标准,30000表示该交换机支持的PoE供电协议是IEEE 802.3at标准。
- 检查AP与AC之间网络是否互通。如果不通,请检查对应配置是否正确。
-
尝试更换连接AP的物理线路。
这篇关于华为综合案例-普通WLAN全覆盖配置(2)的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!







