本文主要是介绍【网络安全 | 指纹识别工具】WhatWeb使用详析,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
前言
WhatWeb 是一款用于识别 Web 应用程序和 Web 服务器的开源工具。它可以识别网站使用的编程语言、Web 框架、Web 服务器软件、Web 应用程序等信息,从而帮助安全测试人员快速了解目标网站的技术特征,发现可能存在的漏洞。
本文将对 WhatWeb 的使用方法进行讲解
文章目录
- 前言
- 正文
- 扫描网站指纹
- 实例
- 设置扫描强度
- 扫描内网网段
- 批量扫描
- 常用命令
- 编写插件
- 帮助
正文
Kali虚拟机自带whatweb工具,不需要安装、直接使用即可。
扫描网站指纹
- 在终端或命令行中输入 whatweb 命令,加上要扫描的网站 URL 或 IP 地址,例如:whatweb example.com
- WhatWeb 会自动识别目标网站的相关信息,并输出到终端或命令行中。
- 可以使用 -v 参数来显示所有信息,例如:whatweb -v example.com
实例
whatweb www.alibaba.com
回显如下:
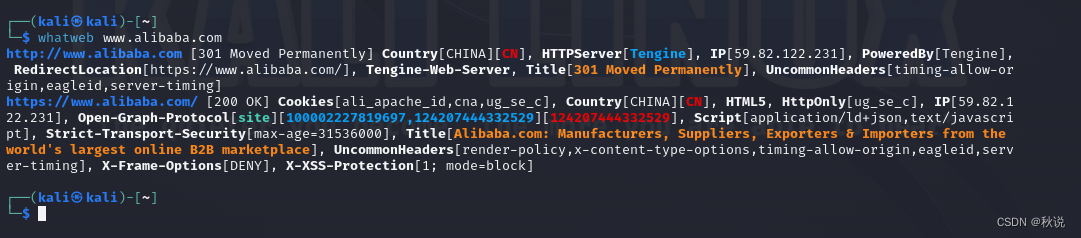
解释如下:
对于 http://www.alibaba.com:状态码(Status Code):301 Moved Permanently国家(Country):中国(CN)HTTP 服务器(HTTP Server):TengineIP 地址(IP):59.82.122.231由 Tengine 提供支持(Powered By Tengine)重定向地址(Redirect Location):https://www.alibaba.com/Tengine Web 服务器页面标题(Title):301 Moved Permanently不常见的头部信息(Uncommon Headers):timing-allow-origin、eagleid、server-timing对于 https://www.alibaba.com/:状态码(Status Code):200 OKCookies:ali_apache_id、cna、ug_se_c国家(Country):中国(CN)使用 HTML5 技术HttpOnly:ug_se_cIP 地址(IP):59.82.122.231Open Graph Protocol:site(100002227819697, 124207444332529)脚本类型:application/ld+json、text/javascript严格传输安全性(Strict Transport Security):max-age=31536000页面标题(Title):Alibaba.com: Manufacturers, Suppliers, Exporters & Importers from the world's largest online B2B marketplace不常见的头部信息(Uncommon Headers):render-policy、x-content-type-options、timing-allow-origin、eagleid、server-timingX-Frame-Options:DENYX-XSS-Protection:1; mode=block加上-v可以显示详细的输出信息:
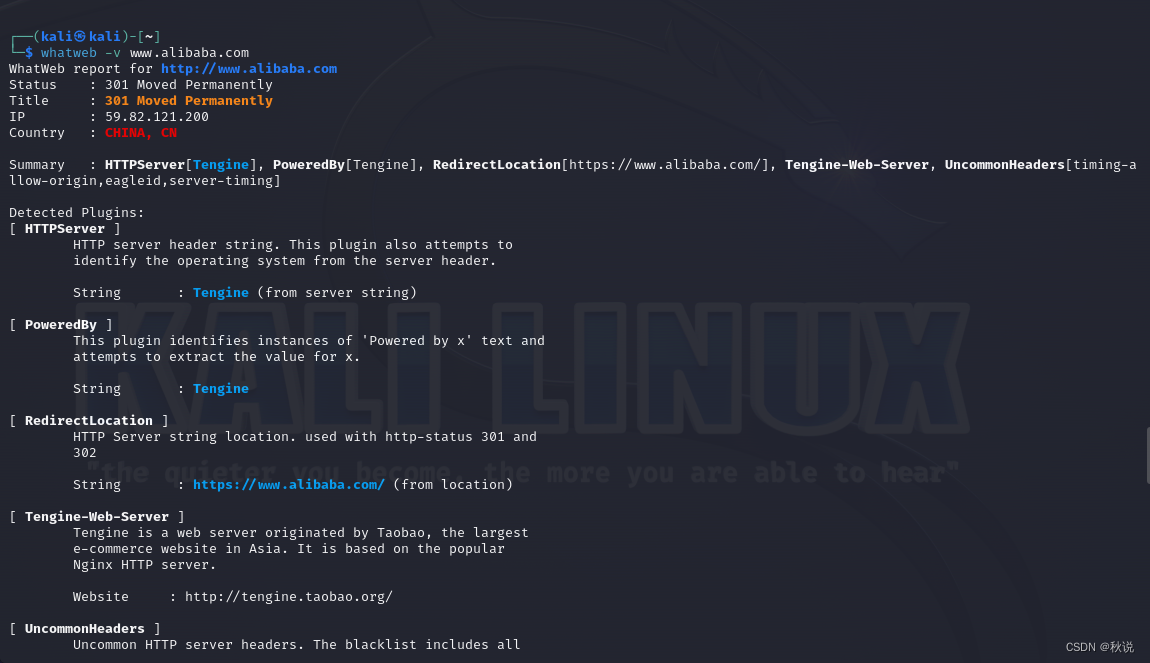
whatweb -v www.alibaba.com
设置扫描强度
加上-a可以指定扫描等级,WhatWeb有3种扫描级别,通过数字1、3、4选择
如:
whatweb www.alibaba.com -a 3
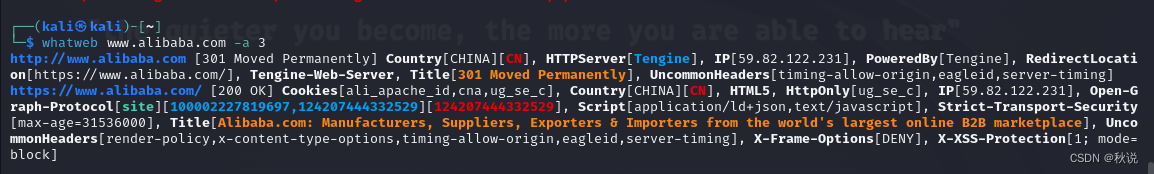
- 1表示发送1次http请求
- 3表示发送少量http请求
- 4表示发送大量http请求
扫描内网网段
命令行:
whatweb --no-errors -t 255 内网网段
批量扫描
扫描多个不同网站时,将要扫描网站的域名或IP保存到文件(如1.txt)中,再使用-i参数来连接该文件即可,如:
whatweb -i "root/1.txt"
常用命令
whatweb [URL]:扫描指定的 URL,输出识别结果。whatweb -v [URL]:以详细模式扫描指定的 URL,显示更多信息。whatweb [URL] -a "User-Agent":指定自定义的用户代理进行扫描。whatweb [URL] -t 10:设置超时时间为 10 秒。whatweb [URL] -x "/path/to/exclude":指定要排除的目录或文件。whatweb [URL] -p 80,443:指定要扫描的端口号,多个端口使用逗号分隔。whatweb -iL [file.txt]:从文件中读取多个 URL 进行扫描。whatweb --color=never:禁用彩色输出。
编写插件
whatweb对国内的网站识别并不友好,我们可以自己写插件,兼容更多国内的网站。
whatweb的官方模板:
Plugin.define "Plugin-Template" doauthor "Enter Your Name"version "0.1"description "Describe what the plugin identifies. Include the homepage of the software package"examples %w| include-some.net example-websites.com here.com |\# a comment block here is a good place to make notes for yourself and others \# There are four types of matches: regexp, text, ghdb \# Matches are enclosed in {} brackets and separated by commas matches [{:name=>"a brief description of the match, eg. powered by in footer",:certainty=>100, # 100 is certain, 75 is probably and 25 is maybe. if omitted, it defaults to 100. :regexp=>/This page was generated by http://www.genericcms.com\/en\/products\/generic-cms\/">Generic CMS<\/a>/ },{:name=>"title",:certainty=>75,:text=>"<title>Generic Homepage</title>" }]end
帮助
更多语法在帮助里可以找到,使用以下命令以获得帮助:
whatweb -h
WhatWeb - Next generation web scanner version 0.5.5.
Developed by Andrew Horton (urbanadventurer) and Brendan Coles (bcoles).
Homepage: https://www.morningstarsecurity.com/research/whatwebUsage: whatweb [options] <URLs>TARGET SELECTION:<TARGETs> Enter URLs, hostnames, IP addresses, filenames orIP ranges in CIDR, x.x.x-x, or x.x.x.x-x.x.x.xformat.--input-file=FILE, -i Read targets from a file. You can pipehostnames or URLs directly with -i /dev/stdin.TARGET MODIFICATION:--url-prefix Add a prefix to target URLs.--url-suffix Add a suffix to target URLs.--url-pattern Insert the targets into a URL.e.g. example.com/%insert%/robots.txtAGGRESSION:
The aggression level controls the trade-off between speed/stealth and
reliability.--aggression, -a=LEVEL Set the aggression level. Default: 1.1. Stealthy Makes one HTTP request per target and alsofollows redirects.3. Aggressive If a level 1 plugin is matched, additionalrequests will be made.4. Heavy Makes a lot of HTTP requests per target. URLsfrom all plugins are attempted.HTTP OPTIONS:--user-agent, -U=AGENT Identify as AGENT instead of WhatWeb/0.5.5.--header, -H Add an HTTP header. eg "Foo:Bar". Specifying adefault header will replace it. Specifying anempty value, e.g. "User-Agent:" will remove it.--follow-redirect=WHEN Control when to follow redirects. WHEN may be`never', `http-only', `meta-only', `same-site',or `always'. Default: always.--max-redirects=NUM Maximum number of redirects. Default: 10.AUTHENTICATION:--user, -u=<user:password> HTTP basic authentication.--cookie, -c=COOKIES Use cookies, e.g. 'name=value; name2=value2'.--cookie-jar=FILE Read cookies from a file.PROXY:--proxy <hostname[:port]> Set proxy hostname and port.Default: 8080.--proxy-user <username:password> Set proxy user and password.PLUGINS:--list-plugins, -l List all plugins.--info-plugins, -I=[SEARCH] List all plugins with detailed information.Optionally search with keywords in a commadelimited list.--search-plugins=STRING Search plugins for a keyword.--plugins, -p=LIST Select plugins. LIST is a comma delimited setof selected plugins. Default is all.Each element can be a directory, file or pluginname and can optionally have a modifier, +/-.Examples: +/tmp/moo.rb,+/tmp/foo.rbtitle,md5,+./plugins-disabled/./plugins-disabled,-md5-p + is a shortcut for -p +plugins-disabled.--grep, -g=STRING|REGEXP Search for STRING or a Regular Expression. Showsonly the results that match.Examples: --grep "hello"--grep "/he[l]*o/"--custom-plugin=DEFINITION Define a custom plugin named Custom-Plugin,Examples: ":text=>'powered by abc'"":version=>/powered[ ]?by ab[0-9]/"":ghdb=>'intitle:abc \"powered by abc\"'"":md5=>'8666257030b94d3bdb46e05945f60b42'""{:text=>'powered by abc'}"--dorks=PLUGIN List Google dorks for the selected plugin.OUTPUT:--verbose, -v Verbose output includes plugin descriptions.Use twice for debugging.--colour,--color=WHEN control whether colour is used. WHEN may be`never', `always', or `auto'.--quiet, -q Do not display brief logging to STDOUT.--no-errors Suppress error messages.LOGGING:--log-brief=FILE Log brief, one-line output.--log-verbose=FILE Log verbose output.--log-errors=FILE Log errors.--log-xml=FILE Log XML format.--log-json=FILE Log JSON format.--log-sql=FILE Log SQL INSERT statements.--log-sql-create=FILE Create SQL database tables.--log-json-verbose=FILE Log JSON Verbose format.--log-magictree=FILE Log MagicTree XML format.--log-object=FILE Log Ruby object inspection format.--log-mongo-database Name of the MongoDB database.--log-mongo-collection Name of the MongoDB collection.Default: whatweb.--log-mongo-host MongoDB hostname or IP address.Default: 0.0.0.0.--log-mongo-username MongoDB username. Default: nil.--log-mongo-password MongoDB password. Default: nil.--log-elastic-index Name of the index to store results. Default: whatweb--log-elastic-host Host:port of the elastic http interface. Default: 127.0.0.1:9200PERFORMANCE & STABILITY:--max-threads, -t Number of simultaneous threads. Default: 25.--open-timeout Time in seconds. Default: 15.--read-timeout Time in seconds. Default: 30.--wait=SECONDS Wait SECONDS between connections.This is useful when using a single thread.HELP & MISCELLANEOUS:--short-help Short usage help.--help, -h Complete usage help.--debug Raise errors in plugins.--version Display version information.EXAMPLE USAGE:
* Scan example.com../whatweb example.com* Scan reddit.com slashdot.org with verbose plugin descriptions../whatweb -v reddit.com slashdot.org* An aggressive scan of wired.com detects the exact version of WordPress../whatweb -a 3 www.wired.com* Scan the local network quickly and suppress errors.whatweb --no-errors 192.168.0.0/24* Scan the local network for https websites.whatweb --no-errors --url-prefix https:// 192.168.0.0/24* Scan for crossdomain policies in the Alexa Top 1000../whatweb -i plugin-development/alexa-top-100.txt \--url-suffix /crossdomain.xml -p crossdomain_xml
- TARGET SELECTION: 设置目标选择,可以输入URL、主机名、IP地址、文件名或CIDR格式的IP范围。
- TARGET MODIFICATION: 目标修改选项,可以添加URL前缀或后缀,也可以将目标插入到URL中的指定位置。
- AGGRESSION: 设置扫描侵入性级别,控制速度、隐蔽性和可靠性之间的平衡。
- HTTP OPTIONS: 设置HTTP选项,如自定义User-Agent、添加HTTP头、控制重定向行为等。
- AUTHENTICATION: 设置HTTP基本身份验证和cookie。
- PROXY: 设置代理服务器,包括主机名、端口和身份验证信息。
- PLUGINS: 插件相关选项,如列出插件、查看插件信息、搜索插件、选择插件等。
- OUTPUT: 设置输出选项,如详细与简要输出、是否使用颜色、日志记录等。
- LOGGING: 设置日志记录选项,包括日志文件格式和存储位置。
- PERFORMANCE & STABILITY: 设置性能和稳定性选项,如线程数、连接超时时间等。
- HELP & MISCELLANEOUS: 帮助和其他杂项选项,如显示帮助信息、调试模式、显示版本号等。
- EXAMPLE USAGE: 示例用法,演示了几个常见的命令用法和参数组合。
这篇关于【网络安全 | 指纹识别工具】WhatWeb使用详析的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!







