本文主要是介绍SWAN测试用例af-alg/alg-camellia,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
Camellia作为一种块加密算法,支持块长度128、192或256位,其具有与AES同等级的安全强度。本测试用例使用到Camellia算法的两者密钥长度192和256。
以下启动af-alg/alg-camellia测试用例,注意在启动之前需要执行start-testing脚本开启测试环境。
$ cd strongswan-5.8.1/testing
$
$ sudo ./do-tests af-alg/alg-camelliaGuest kernel : 5.2.11
strongSwan : 5.8.1
Date : 20191025-0850-06[ ok ] 1 af-alg/alg-camellia: pre..test..postPassed : 1
Failed : 0The results are available in /srv/strongswan-testing/testresults/20191025-0850-06
or via the link http://192.168.0.150/testresults/20191025-0850-06Finished : 20191025-0850-11
以下为测试用例af-alg/alg-camellia的测试结果记录文件。
$ ls /srv/strongswan-testing/testresults/20191025-0850-06/af-alg/alg-camellia/
carol.auth.log carol.iptables-save carol.swanctl.pols moon.daemon.log moon.strongswan.conf moon.swanctl.pools
carol.daemon.log carol.strongswan.conf carol.swanctl.pools moon.ip.policy moon.swanctl.algs moon.swanctl.sas
carol.ip.policy carol.swanctl.algs carol.swanctl.sas moon.ip.route moon.swanctl.authorities moon.swanctl.stats
carol.ip.route carol.swanctl.authorities carol.swanctl.stats moon.ip.state moon.swanctl.certs moon.tcpdump.log
carol.ip.state carol.swanctl.certs console.log moon.ipsec.sql moon.swanctl.conf
carol.ipsec.sql carol.swanctl.conf index.html moon.iptables moon.swanctl.conns
carol.iptables carol.swanctl.conns moon.auth.log moon.iptables-save moon.swanctl.pols
由以上测试结果文件可知,此测试具体涉及到两个虚拟主机carol和moon。测试拓扑如下:

虚拟主机carol向VPN网关moon发起IPSec连接,IKE SA加密套件使用:camellia256-sha512-modp3072,IPSec SA加密套件使用camellia192-sha384。IPSec通道建立之后,在虚拟主机carol上ping网关moon之后的虚拟主机alice,以验证建立隧道的连通性。
测试配置文件
配置文件:strongswan-5.8.1/testing/tests/af-alg/alg-camellia/test.conf,内容如下。VIRTHOSTS变量定义了本测试用来需要使用的的虚拟主机列表。DIAGRAM指定了测试报告中使用的测试拓扑图,如上所示。变量IPSECHOSTS定义了测试中参与IPSec隧道建立的虚拟主机名称。SWANCTL为1表明使用命令行工具swanctl与主进程charon通信,而不是ipsec命令。
# All guest instances that are required for this testVIRTHOSTS="alice moon carol winnetou"# Corresponding block diagramDIAGRAM="a-m-c-w.png"# Guest instances on which tcpdump is to be startedTCPDUMPHOSTS="moon"# Guest instances on which IPsec is started Used for IPsec logging purposesIPSECHOSTS="moon carol"# charon controlled by swanctlSWANCTL=1
carol配置
连接配置文件:strongswan-5.8.1/testing/tests/af-alg/alg-camellia/hosts/carol/etc/swanctl/swanctl.conf,内容如下。虚拟主机carol的IP地址为192.168.0.100,而moon网关的IP地址为192.168.0.1。
另外,此连接home定义了本次测试使用的两个proposals。分别为IPSec使用的esp_proposals,其值为camellia192-sha384。以及IKE的proposal,值为camellia256-sha512-modp3072(三部分分别为加密算法,验证算法和Diffie-Hellman组)。
connections {home {local_addrs = 192.168.0.100remote_addrs = 192.168.0.1local {auth = pubkeycerts = carolCert.pemid = carol@strongswan.org}remote {auth = pubkeyid = moon.strongswan.org}children {home {remote_ts = 10.1.0.0/16updown = /usr/local/libexec/ipsec/_updown iptablesesp_proposals = camellia192-sha384}}version = 2proposals = camellia256-sha512-modp3072}}
StrongSwan配置文件:strongswan-5.8.1/testing/tests/af-alg/alg-camellia/hosts/carol/etc/strongswan.conf,内容如下,指定需要加载的模块。
1 # /etc/strongswan.conf - strongSwan configuration file2 3 swanctl {4 load = pem pkcs1 x509 revocation constraints pubkey openssl random5 }6 7 charon-systemd {8 load = random nonce pem pkcs1 af-alg gmp x509 revocation kernel-netlink curl socket-default updown vici9 }
其它配置文件(位于全局测试目录下),这些文件在测试准备阶段将拷贝到测试虚拟主机上,参见文件:strongswan-5.8.1/testing/scripts/load-testconfig。配置文件分成4个目录,其中etc目录下的文件主要是主机名文件hostname、以及ipsec和strongswan的配置文件。另外三个目录为ipsec.d,network和swanctl,其中ipsec.d和swanctl分别保存各自的证书文件,本测试用例中使用swanctl工具,参见文件:tests/af-alg/alg-camellia/test.conf,中的变量SWANCTL。
$ ls -R strongswan-5.8.1/testing/hosts/carol/ hosts/carol/etc/hostname
hosts/carol/etc/ipsec.conf
hosts/carol/etc/ipsec.secrets
hosts/carol/etc/strongswan.conf
hosts/carol/etc/ipsec.d/ipsec.sql
hosts/carol/etc/ipsec.d/cacerts/strongswanCert.pem
hosts/carol/etc/ipsec.d/certs/carolCert.pem
hosts/carol/etc/ipsec.d/private/carolKey.pem
hosts/carol/etc/network/interfaces
hosts/carol/etc/swanctl/rsa/carolKey.pem
hosts/carol/etc/swanctl/x509/carolCert.pem
hosts/carol/etc/swanctl/x509ca/strongswanCert.pem
network子目录下的文件interfaces,用于设置alice主机的网络接口eth0的IP地址信息。
auto loiface lo inet loopbackauto eth0iface eth0 inet staticaddress 192.168.0.100netmask 255.255.255.0broadcast 192.168.0.255gateway 192.168.0.254iface eth0 inet6 staticaddress fec0::10netmask 16
moon网关配置
配置文件:strongswan-5.8.1/testing/tests/af-alg/alg-camellia/hosts/moon/etc/swanctl/swanctl.conf,内容如下。注意网关moon的连接配置,两个proposals与carol的配置相同。以及定义了children连接名称为net。连接名称rw即Road Warrier为远程接入用户的连接配置。
作为网关,其事先并不知晓连接对端的IP地址信息,此处只有local_addrs的配置。
connections {rw {local_addrs = 192.168.0.1local {auth = pubkeycerts = moonCert.pemid = moon.strongswan.org}remote {auth = pubkey}children {net {local_ts = 10.1.0.0/16updown = /usr/local/libexec/ipsec/_updown iptablesesp_proposals = camellia192-sha384}}version = 2proposals = camellia256-sha512-modp3072}}
StrongSwan配置文件:strongswan-5.8.1/testing/tests/af-alg/alg-camellia/hosts/moon/etc/strongswan.conf,内容如下,指定要加载的模块。
# /etc/strongswan.conf - strongSwan configuration fileswanctl {load = pem pkcs1 x509 revocation constraints pubkey openssl random}charon-systemd {load = random nonce pem pkcs1 af-alg gmp x509 revocation kernel-netlink curl socket-default updown vici}
其它配置文件(位于全局测试目录下),这些文件在测试准备阶段将拷贝到测试虚拟主机上,参见文件:strongswan-5.8.1/testing/scripts/load-testconfig。配置文件分成4个目录,其中etc目录下的文件主要是主机名文件hostname、以及ipsec和strongswan的配置文件,还有rc.local文件。另外三个目录为ipsec.d,network和swanctl,其中ipsec.d和swanctl分别保存各自的证书文件,本测试用例中使用swanctl工具,参见文件:tests/af-alg/alg-camellia/test.conf,中的变量SWANCTL。
$ ls -R strongswan-5.8.1/testing/hosts/moon/ hosts/moon/etc/hostname
hosts/moon/etc/ipsec.conf
hosts/moon/etc/ipsec.secrets
hosts/moon/etc/rc.local
hosts/moon/etc/strongswan.conf
hosts/moon/etc/ipsec.d/ipsec.sql
hosts/moon/etc/ipsec.d/cacerts/strongswanCert.pem
hosts/moon/etc/ipsec.d/certs/moonCert.pem
hosts/moon/etc/ipsec.d/private/moonKey.pem
hosts/moon/etc/network/interfaces
hosts/moon/etc/swanctl/rsa/moonKey.pem
hosts/moon/etc/swanctl/x509/moonCert.pem
hosts/moon/etc/swanctl/x509ca/strongswanCert.pem
etc目录下的rc.local文件,其内容如下,关闭eth1接口的offload功能,文件中的解释为UDP的校验和offload功能,与libvirt和isc的dhcp服务程序不能一起工作。这个问题被发现在内核kernel 2.6.39-rc6 和 qemu-kvm 0.14的时候,现在已经被修复。
# Disable checksum offloading on eth1 because it does not currently work with# libvirt and isc-dhcp-server running on venus, see [1]# [1] - https://bugs.mageia.org/show_bug.cgi?id=1243ethtool --offload eth1 tx off >/dev/null 2>&1ethtool --offload eth1 rx off >/dev/null 2>&1exit 0
network子目录下的文件interfaces,用于设置moon主机的两个网络接口eth0和eth1的IP地址信息。
auto loiface lo inet loopbackauto eth0iface eth0 inet staticaddress 192.168.0.1netmask 255.255.255.0broadcast 192.168.0.255gateway 192.168.0.254iface eth0 inet6 staticaddress fec0::1netmask 16auto eth1iface eth1 inet staticaddress 10.1.0.1netmask 255.255.0.0broadcast 10.1.255.255iface eth1 inet6 staticaddress fec1::1netmask 16
准备阶段
配置文件:strongswan-5.8.1/testing/tests/af-alg/alg-camellia/pretest.dat,内容如下。在预测试pre-test阶段,备份moon和carol主机的iptables配置。启动strongswan。使用脚本expect-connection检测名称为net的连接(carol主机上为home)是否建立,超过5秒钟检测不到,打印失败信息。swanctl初始化一个名称为home的子连接。
通过之前的介绍已经在carol和moon虚拟主机的配置文件(etc/swanctl/swanctl.conf)中看到了home和net的配置信息。
1 moon::iptables-restore < /etc/iptables.rules2 carol::iptables-restore < /etc/iptables.rules3 moon::systemctl start strongswan4 carol::systemctl start strongswan5 moon::expect-connection net6 carol::expect-connection home7 carol::swanctl --initiate --child home 2> /dev/null
脚本expect-connection的内容如下。如果/etc/strongswan.conf文件中加载了stroke模块,或者DAEMON_NAME变量有值,将使用ipsec statusall命令查看连接信息;否则使用swanctl --list-conns查看。由以上介绍的文件strongswan.conf可知,并未加载stroke模块。使用swanctl查看连接信息,并在moon主机上检查是否存在名称为net的连接,在carol主机上检查是否存在home连接。默认的检测时长为5秒,可在命令行中指定此值。
secs=$2
[ ! $secs ] && secs=5cmd="swanctl --list-conns"
grep 'load.*stroke' /etc/strongswan.conf >/dev/null
if [ $? -eq 0 -o -n "$DAEMON_NAME" ]; thencmd="ipsec statusall"
filet steps=$secs*10
for i in `seq 1 $steps`
do$cmd 2>&1 | grep ^[[:space:]]*$1: >/dev/null[ $? -eq 0 ] && exit 0sleep 0.1
doneecho "Connection '$1' not available after $secs second(s)"
exit 1
测试阶段
配置文件:strongswan-5.8.1/testing/tests/af-alg/alg-camellia/evaltest.dat,内容如下。在第一行中,SSH登录到carol主机执行ping命令,并且期待alice返回的信息符合pattern:(128 bytes from PH_IP_ALICE: icmp_.eq=1)。其中PH_IP_ALICE为alice主机的IP地址。
1 carol::ping -c 1 -s 120 -p deadbeef PH_IP_ALICE::128 bytes from PH_IP_ALICE: icmp_.eq=1::YES
2 carol::swanctl --list-sas --raw 2> /dev/null::home.*version=2 state=ESTABLISHED local-host=192.168.0.100 local-port=4500 local- id=carol@strongswan.org remote-host=192.168.0.1 remote-port=4500 remote-id=moon.strongswan.org initiator=yes.*encr-alg=CAMELLIA_CBC encr-keysize=256 integ-alg=HMAC_SHA2_512_256 prf-alg=PRF_HMAC_SHA2_512 dh-group=MODP_3072.*child-sas.*home.*state=INSTALLED mode=TUNNEL protocol=ESP.*encr-alg=CAMELLIA_CBC encr-keysize=192 integ-alg=HMAC_SHA2_384_192.*local-ts=\[192.168.0.100/32] remote-ts=\[10.1.0.0/16]::YES
3 moon:: swanctl --list-sas --raw 2> /dev/null::rw.*version=2 state=ESTABLISHED local-host=192.168.0.1 local-port=4500 local-id=moon.strongswan.org remote-host=192.168.0.100 remote-port=4500 remote-id=carol@strongswan.org.*encr-alg=CAMELLIA_CBC encr-keysize=256 integ-alg=HMAC_SHA2_512_256 prf-alg=PRF_HMAC_SHA2_512 dh-group=MODP_3072.*child-sas.*net.*state=INSTALLED mode=TUNNEL protocol=ESP.*encr-alg=CAMELLIA_CBC encr-keysize=192 integ-alg=HMAC_SHA2_384_192.*local-ts=\[10.1.0.0/16] remote-ts=\[192.168.0.100/32]::YES
4 moon:: ip xfrm state::enc cbc(camellia)::YES
5 carol::ip xfrm state::enc cbc(camellia)::YES
6 moon::tcpdump::IP carol.strongswan.org > moon.strongswan.org: ESP.*length 208::YES
7 moon::tcpdump::IP moon.strongswan.org > carol.strongswan.org: ESP.*length 208::YES
第二行测试语句登录到carol主机中,使用命令swanctl --list-sas --raw显示安全关联SA的信息,在其中匹配随后的模式pattern字段,这个比较长。主要包括连接名称:home;状态:ESTABLISHED;本地地址:192.168.0.100:4500;ID信息;远端地址信息:192.168.0.1:4500。encr-alg字段为本测试用例中指定的IKE加密算法:CAMELLIA_CBC;字段encr-keysize指定了密钥长度为256,并且dh-group为MODP_3072,可见与以上的配置相符。
子连接的SA匹配信息有,协议protocol字段:ESP;加密算法encr-alg字段:CAMELLIA_CBC; 加密密钥长度encr-keysize为192;与以上的child连接配置相符。以下为carol虚拟主机执行swanctl --list-sas的显示信息,可见与测试文件evaltest.dat的第二行完全匹配。
home: #1, ESTABLISHED, IKEv2, 02cacf1c593096b2_i* 56be89492836bc46_rlocal 'carol@strongswan.org' @ 192.168.0.100[4500]remote 'moon.strongswan.org' @ 192.168.0.1[4500]CAMELLIA_CBC-256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_3072established 2s ago, rekeying in 13616shome: #1, reqid 1, INSTALLED, TUNNEL, ESP:CAMELLIA_CBC-192/HMAC_SHA2_384_192installed 2s ago, rekeying in 3487s, expires in 3958sin cc6d968b, 148 bytes, 1 packets, 2s agoout c4a8416e, 148 bytes, 1 packets, 2s agolocal 192.168.0.100/32remote 10.1.0.0/16
第三行测试语句为登录到moon网关,执行swanctl --list-sas --raw命令并检查输出结果,其内容与第二行类似。moon网关上执行swanctl --list-conns的结果如下显示。
rw: #1, ESTABLISHED, IKEv2, 02cacf1c593096b2_i 56be89492836bc46_r*local 'moon.strongswan.org' @ 192.168.0.1[4500]remote 'carol@strongswan.org' @ 192.168.0.100[4500]CAMELLIA_CBC-256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_3072established 1s ago, rekeying in 13763snet: #1, reqid 1, INSTALLED, TUNNEL, ESP:CAMELLIA_CBC-192/HMAC_SHA2_384_192installed 1s ago, rekeying in 3264s, expires in 3959sin c4a8416e, 148 bytes, 1 packets, 1s agoout cc6d968b, 148 bytes, 1 packets, 1s agolocal 10.1.0.0/16remote 192.168.0.100/32
第四和第五行测试语句分别登录到moon和carol上执行ip xfrm state命令,确认输出结果中的加密描述字符:enc cbc(camellia)。以下为carol主机上的执行结果:
src 192.168.0.100 dst 192.168.0.1proto esp spi 0xc4a8416e(3299361134) reqid 1(0x00000001) mode tunnelreplay-window 0 seq 0x00000000 flag af-unspec (0x00100000)auth-trunc hmac(sha384) 0x149e1b0de63af6d3eb86d022d34a77e4b42731dfb28bb105e7aaa0f9bddf525be2e44cde9ba07bb45a0e68cac43ac5db (384 bits) 192enc cbc(camellia) 0x7ad8b6af333b69c3d66b68886e3768ad1461c5a19f15a884 (192 bits)anti-replay context: seq 0x0, oseq 0x1, bitmap 0x00000000lifetime config:limit: soft (INF)(bytes), hard (INF)(bytes)limit: soft (INF)(packets), hard (INF)(packets)expire add: soft 3527(sec), hard 3960(sec)expire use: soft 0(sec), hard 0(sec)lifetime current:148(bytes), 1(packets)add 2019-10-25 08:50:13 use 2019-10-25 08:50:13stats:replay-window 0 replay 0 failed 0
src 192.168.0.1 dst 192.168.0.100proto esp spi 0xcc6d968b(3429734027) reqid 1(0x00000001) mode tunnelreplay-window 32 seq 0x00000000 flag af-unspec (0x00100000)auth-trunc hmac(sha384) 0xa2517ceb939c964f219aa469280c8f46fb4047162f19a169c82614e6517f8c77ab3cd2aa96c4f87ee942697f84e2bef6 (384 bits) 192enc cbc(camellia) 0x83d1fed89ac760fbff2371460a8c6041ffea649aedbf1bf1 (192 bits)anti-replay context: seq 0x1, oseq 0x0, bitmap 0x00000001lifetime config:limit: soft (INF)(bytes), hard (INF)(bytes)limit: soft (INF)(packets), hard (INF)(packets)expire add: soft 3489(sec), hard 3960(sec)expire use: soft 0(sec), hard 0(sec)lifetime current:148(bytes), 1(packets)add 2019-10-25 08:50:13 use 2019-10-25 08:50:13stats:replay-window 0 replay 0 failed 0
最后两行测试语句都是在moon网关上执行的,这里的tcpdump命令并不执行,而是检查在以上的测试过程后台tcpdump名称输出到文件/tmp/tcpdump.log中的日志信息,确认其中是否包含内容:(IP carol.strongswan.org > moon.strongswan.org: ESP.*length 208)。
14 08:50:11.910391 ARP, Request who-has winnetou.strongswan.org tell carol.strongswan.org, length 2815 08:50:11.953627 IP carol.strongswan.org > moon.strongswan.org: ESP(spi=0xc4a8416e,seq=0x1), length 20816 08:50:11.953686 IP carol.strongswan.org > alice.strongswan.org: ICMP echo request, id 3351, seq 1, length 12817 08:50:11.954295 IP moon.strongswan.org > carol.strongswan.org: ESP(spi=0xcc6d968b,seq=0x1), length 208
收尾阶段
配置文件:strongswan-5.8.1/testing/tests/af-alg/alg-camellia/posttest.dat,内容如下。其中第一行断开carol虚拟主机上名称为home的连接。第二行终止carol上的StrongSwan进程。第三行终止moon网关上的StrongSwan进程。最后两行恢复moon网关和carol主机上的iptables规则。
1 carol::swanctl --terminate --ike home2 carol::systemctl stop strongswan3 moon::systemctl stop strongswan4 moon::iptables-restore < /etc/iptables.flush5 carol::iptables-restore < /etc/iptables.flush
测试结果文件默认都保存在目录:/srv/strongswan-testing/testresults/20191025-0850-06/af-alg/alg-camellia下,其中文件console.log 记录了整个的测试过程。文件carol.daemon.log和moon.daemon.log文件记录了charon-systemd主进程的日志。完整的测试结果文件里边见本文开始部分。下图为IKEv2报文的交互报文。
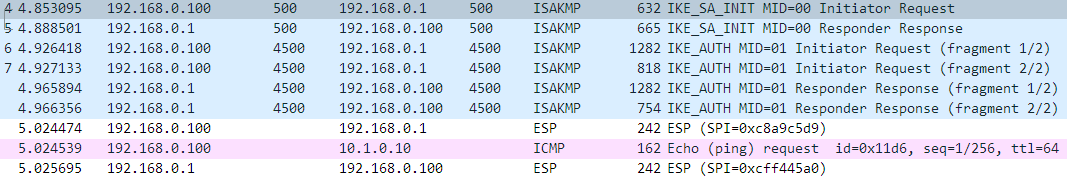
附件为tcpdump抓取到的报文,可由第二个IKE_SA_INIT回复报文中协商的proposal,再次确认使用的加密算法为:ENCR_CAMELLIA_CBC-256。之后的报文(IKE_AUTH等)为加密报文,不可查看。
ike-alg-camellia.pcap [https://download.csdn.net/download/sinat_20184565/11935258]
END
这篇关于SWAN测试用例af-alg/alg-camellia的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!