本文主要是介绍[Ubuntu 22.04] containerd配置HTTP方式拉取私仓Harbor,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
文章目录
- 1. 基础环境配置
- 2. Docker安装
- 3. 部署Harbor,HTTP访问
- 4. 部署ContainerD
- 5. 修改docker配置文件,向harbor中推入镜像
- 6. 配置containerd
- 6.1. 拉取镜像验证
- 6.2. 推送镜像验证
1. 基础环境配置
[Ubuntu 22.04] 安装K8S基础环境准备脚本
2. Docker安装
[Ubuntu 22.04] 安装docker,并设置镜像加速
3. 部署Harbor,HTTP访问
[Ubuntu 22.04] 安装Harbor#HTTP方式
浏览器中输入:http://192.168.11.20,即可访问刚才部署的harbor
4. 部署ContainerD
[Ubuntu 22.04] 安装containerd
5. 修改docker配置文件,向harbor中推入镜像
目标:向第三步部署的harbor仓库中推入镜像仓库
根据目前的环境,有两种方式可以向horbor中推入镜像。其一是通过docker向harbor中推入镜像仓库。其二是通过containerd向harbor中推入镜像
由于目前我们对于containerd并不熟悉,因此我们先直接通过docker向harbor中推入镜像,由于我们自己搭建的harbor是私有仓库,并且是HTTP的方式,因此我们需要配置docker的配置文件。
你可以重新找一台机器安装docker做实验,或者直接使用harbor那台机器也可以,这里我直接使用harbor那台机器上的docker工具,向harbor推送镜像。
配置修改如下,主要是增加了insecure-registries配置,如果你的配置文件中包含其它的配置,请不要直接执行,否则会覆盖你的配置。;另外,请一定要注意80端口,这个不能省略,否则docker会以https的方式访问harbor
tee /etc/docker/daemon.json << 'EOF'
{"registry-mirrors": ["http://hub-mirror.c.163.com","https://mirror.baidubce.com","https://docker.mirrors.ustc.edu.cn","https://registry.docker-cn.com","https://dockerproxy.com","https://ccr.ccs.tencentyun.com","https://registry.cn-hangzhou.aliyuncs.com"],"insecure-registries": ["192.168.11.20:80"]
}
EOFsystemctl restart docker.service 这里我随便推送harbor的一个镜像到我自己的harbor仓库当中,操作如下,第一步:重新打tag, 第二步:docker push。这里需要注意的是,再推送镜像之前,一定要在登录harbor,提前建立仓库目录,否则推送会被拒绝,另外,静态的Tag所指向的仓库端口必须要显式指定80端口,否则默认使用443端口
root@harbor-http:~/harbor#
root@harbor-http:~/harbor#
root@harbor-http:~/harbor# cat /etc/docker/daemon.json
{"registry-mirrors": ["http://hub-mirror.c.163.com","https://mirror.baidubce.com","https://docker.mirrors.ustc.edu.cn","https://registry.docker-cn.com","https://dockerproxy.com","https://ccr.ccs.tencentyun.com","https://registry.cn-hangzhou.aliyuncs.com"],"insecure-registries": ["192.168.11.20:80","192.168.11.30"]
}
root@harbor-http:~/harbor# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
goharbor/redis-photon v2.8.2 6f4498a430ca 7 weeks ago 121MB
goharbor/harbor-registryctl v2.8.2 fa61a236a6d6 7 weeks ago 142MB
goharbor/registry-photon v2.8.2 f80e71363231 7 weeks ago 79.3MB
goharbor/nginx-photon v2.8.2 3d009028f260 7 weeks ago 120MB
goharbor/harbor-log v2.8.2 2914d282d9bf 7 weeks ago 127MB
goharbor/harbor-jobservice v2.8.2 40118f1568a8 7 weeks ago 141MB
goharbor/harbor-core v2.8.2 0bbbd1f379fc 7 weeks ago 165MB
goharbor/harbor-portal v2.8.2 3e74e0758aa4 7 weeks ago 127MB
goharbor/harbor-db v2.8.2 5126635ae9f0 7 weeks ago 174MB
goharbor/prepare v2.8.2 eb3cf3cdd17a 7 weeks ago 163MB
hello-world latest 9c7a54a9a43c 2 months ago 13.3kB
root@harbor-http:~/harbor#
root@harbor-http:~/harbor# docker tag goharbor/harbor-core:v2.8.2 192.168.11.20:80/goharbor/harbor-core:v2.8.2
root@harbor-http:~/harbor#
root@harbor-http:~/harbor# docker login -u admin -p harbor666 192.168.11.20:80
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-storeLogin Succeeded
root@harbor-http:~/harbor#
root@harbor-http:~/harbor# docker push 192.168.11.20:80/goharbor/harbor-core:v2.8.2
The push refers to repository [192.168.11.20:80/goharbor/harbor-core]
c8ec2ddada08: Pushed
e1c4f1102d2f: Pushed
17583ba2a843: Pushed
0a049ad6bb06: Pushed
557ccce847e1: Pushed
9cb5dd968a55: Pushed
06d8a79a810a: Pushed
88edeb5b4944: Pushed
c00acf6f4f58: Pushed
21e7914e06fb: Pushed
v2.8.2: digest: sha256:654efa193924544a680f1cc7aaadb8d9fb4e1dcaa8c84a74c71b7fe861973838 size: 2411
root@harbor-http:~/harbor#
root@harbor-http:~/harbor# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
goharbor/redis-photon v2.8.2 6f4498a430ca 7 weeks ago 121MB
goharbor/harbor-registryctl v2.8.2 fa61a236a6d6 7 weeks ago 142MB
goharbor/registry-photon v2.8.2 f80e71363231 7 weeks ago 79.3MB
goharbor/nginx-photon v2.8.2 3d009028f260 7 weeks ago 120MB
goharbor/harbor-log v2.8.2 2914d282d9bf 7 weeks ago 127MB
goharbor/harbor-jobservice v2.8.2 40118f1568a8 7 weeks ago 141MB
192.168.11.20:80/goharbor/harbor-core v2.8.2 0bbbd1f379fc 7 weeks ago 165MB
goharbor/harbor-core v2.8.2 0bbbd1f379fc 7 weeks ago 165MB
goharbor/harbor-portal v2.8.2 3e74e0758aa4 7 weeks ago 127MB
goharbor/harbor-db v2.8.2 5126635ae9f0 7 weeks ago 174MB
goharbor/prepare v2.8.2 eb3cf3cdd17a 7 weeks ago 163MB
hello-world latest 9c7a54a9a43c 2 months ago 13.3kB
root@harbor-http:~/harbor#
6. 配置containerd
mkdir -p /etc/containerd/certs.d/192.168.11.20:80
tee /etc/containerd/certs.d/192.168.11.20:80/hosts.toml << 'EOF'
server = "http://192.168.11.20:80"[host."http://192.168.11.20:80"]capabilities = ["pull", "resolve", "push"]skip_verify = true
EOFsystemctl restart containerd.service6.1. 拉取镜像验证
执行:ctr image pull --plain-http=true -u admin:harbor666 192.168.11.20:80/goharbor/harbor-core:v2.8.2
root@containerd:~#
root@containerd:~# ctr image ls -q
docker.io/library/redis:alpine
root@containerd:~# cat /etc/containerd/certs.d/192.168.11.20\:80/hosts.toml
server = "http://192.168.11.20:80"[host."http://192.168.11.20:80"]capabilities = ["pull", "resolve", "push"]skip_verify = true
root@containerd:~#
root@containerd:~#
root@containerd:~# ctr image pull --plain-http=true -u admin:harbor666 192.168.11.20:80/goharbor/harbor-core:v2.8.2
192.168.11.20:80/goharbor/harbor-core:v2.8.2: resolved |++++++++++++++++++++++++++++++++++++++|
manifest-sha256:654efa193924544a680f1cc7aaadb8d9fb4e1dcaa8c84a74c71b7fe861973838: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:aea1be403dd1c4dce59794761f350e4706eb70771631535689e2b06a0a241001: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:548383ab94bf8b81b55cabf36298e0b14cca610a07a1ebd5bba013fa61ffab96: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:06212d50621c9654d97e7ec78e972b5017e139b11763375ee4c28bace1fcc087: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:cf14510ec51c323f283e583a5aabfa33337680e953b07d83162a6c5b5d72defc: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:b6c3d89688aed77dcbea624088f7613ac0923ca1f0398c42f0c79503a03baed6: done |++++++++++++++++++++++++++++++++++++++|
config-sha256:0bbbd1f379fc1f577c5db15c9deac4a218637e4af0196d97e6771f59d9815355: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:b3381433ebd4d04b664639ab510a6659fec0268dc222de8fb085da676f017cb4: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:b70a76c262e454573e9550cb64962b84a338d78d6f1db4ee9464cce0a8a47dcd: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:378fedafb8051764d80ec29260e7bf3101aabe84b72b23c5829deb2a445391a8: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:f9cd03857d3ab614d97d896de3496a66dffaf4cf5b2051cda730d028d6def94e: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:a3c670ddffbdf7be0c56baae8213258ee6cf339929c86b29905dd11808c80a34: done |++++++++++++++++++++++++++++++++++++++|
elapsed: 0.5 s total: 47.1 M (94.2 MiB/s)
unpacking linux/amd64 sha256:654efa193924544a680f1cc7aaadb8d9fb4e1dcaa8c84a74c71b7fe861973838...
done: 1.256989921s
root@containerd:~#
root@containerd:~#
root@containerd:~# ctr image ls -q
192.168.11.20:80/goharbor/harbor-core:v2.8.2
docker.io/library/redis:alpine
root@containerd:~#6.2. 推送镜像验证
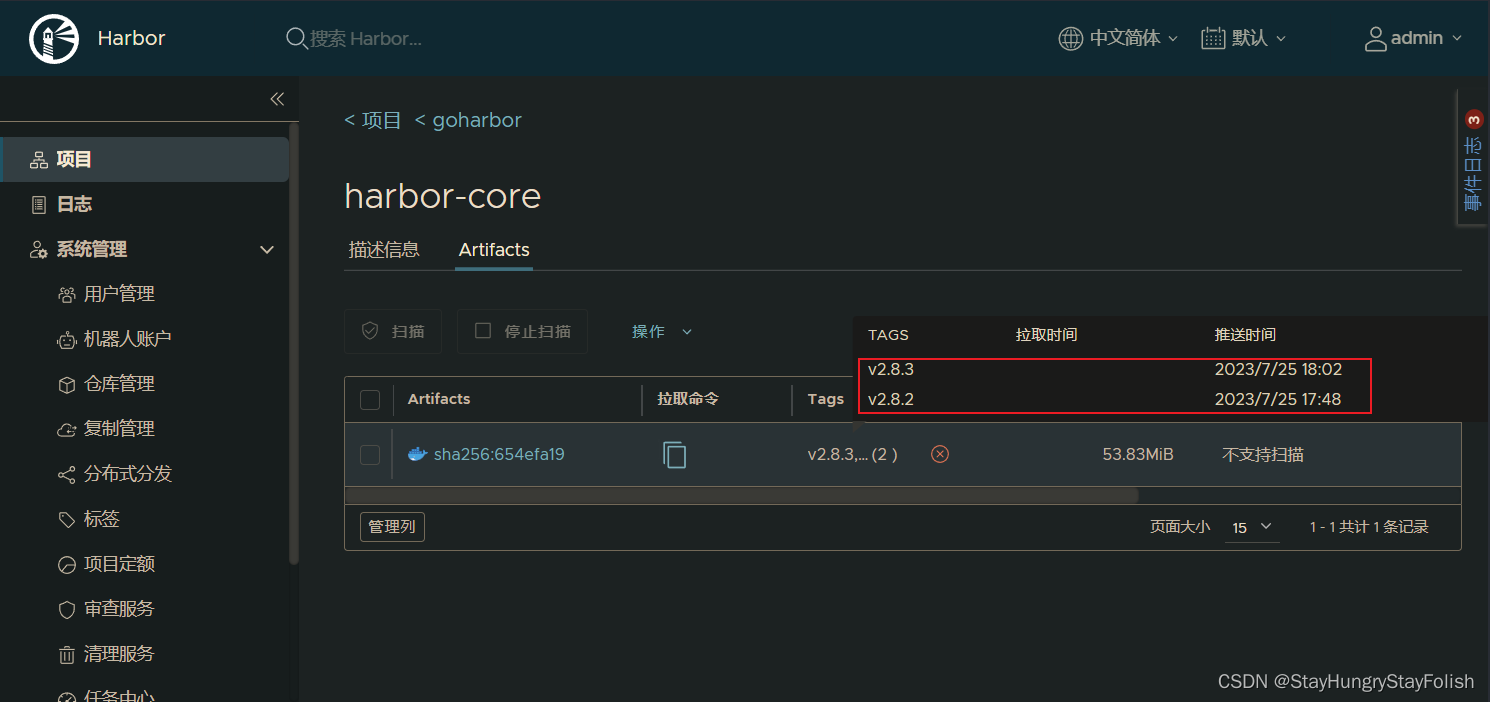
执行:ctr image push --plain-http=true -u admin:harbor666 192.168.11.20:80/goharbor/harbor-core:v2.8.3
root@containerd:~#
root@containerd:~# ctr image ls -q
192.168.11.20:80/goharbor/harbor-core:v2.8.2
docker.io/library/redis:alpine
root@containerd:~#
root@containerd:~# ctr image tag 192.168.11.20:80/goharbor/harbor-core:v2.8.2 192.168.11.20:80/goharbor/harbor-core:v2.8.3
192.168.11.20:80/goharbor/harbor-core:v2.8.3
root@containerd:~# ctr image ls -q
192.168.11.20:80/goharbor/harbor-core:v2.8.2
192.168.11.20:80/goharbor/harbor-core:v2.8.3
docker.io/library/redis:alpine
root@containerd:~#
root@containerd:~# ctr image push --plain-http=true -u admin:harbor666 192.168.11.20:80/goharbor/harbor-core:v2.8.3
manifest-sha256:654efa193924544a680f1cc7aaadb8d9fb4e1dcaa8c84a74c71b7fe861973838: done |++++++++++++++++++++++++++++++++++++++|
config-sha256:0bbbd1f379fc1f577c5db15c9deac4a218637e4af0196d97e6771f59d9815355: done |++++++++++++++++++++++++++++++++++++++|
elapsed: 0.2 s total: 7.7 Ki (38.4 KiB/s)
root@containerd:~#
root@containerd:~#
这篇关于[Ubuntu 22.04] containerd配置HTTP方式拉取私仓Harbor的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!







