本文主要是介绍公私钥加解密问题汇总,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
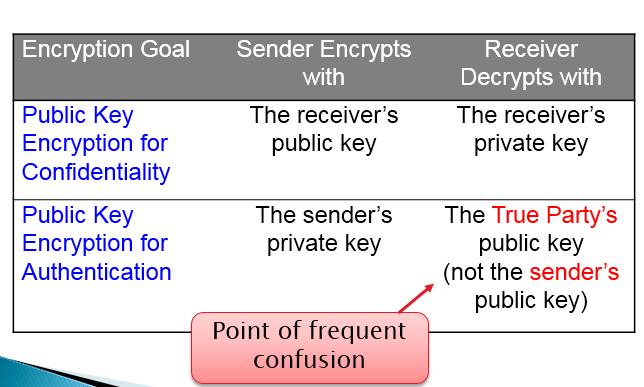
A is sending a message to B (using public key infrastructure). What kind of key is used for encryption (for the purpose of confidentiality)?
B’s public key.
加密用接收方公钥A is sending a message to B (using public key infrastructure). What kind of key is used for encryption (for the purpose of authentication)?
A’s private key.
验证用发送方私钥Which question (#1 or #2) is related to digital signature? Explain in detail.
#2, true party’s public key to authenticate.A is sending a message to B using a symmetric key encryption. Explain the mechanism including key sharing.
A will use B’s public to encrypt the symmetric key, B can use its own private key to decrypt it.4-1. Explain what digital envelope is in Question 4.
Digital envelope is the method to use symmetric key encryption to encrypt document but public key encryption to encrypt and send symmetric key, just like to put a key into an envelope.How do you verify digital signature? Especially what information do you need for verification? Discuss it in detail
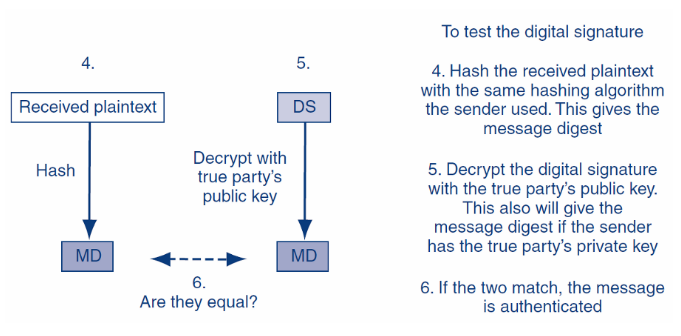
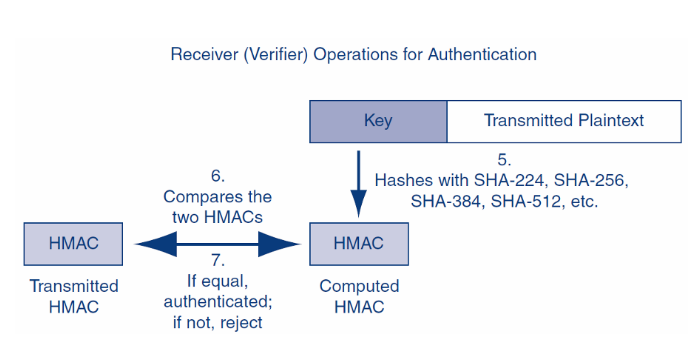
The receiver gets the massage and he/she will decrypt first and hash the plaintext with the same hashing algorithm the sender used; and then decrypt the DS with the true party’s public key. If the 2 match, the message is authenticated.
Third party?How can hashing be used to achieve integrity? Explain with an example.
Integrity means that the message cannot be changed or, if it is changed, that this change will be detected. The hashing is using a method to calculate and it will generate shorter length message which cannot be reversed, if the both sides can use the same hashing method generate the same result, that means the both sides achieve the integrity.Can you use hashing for authentication? Why or why not. Explain in detail.
Yes, the MS-CHAP Challenge-Response Authentication Protocol using hashing to authenticate.A is sending a message to B. A and B agree that digital signature(Q2), digital certificate(Q5), and digital envelope(Q4) need to be used. Describe the detailed mechanism to use those three notions in their communication.
整个传递过程是:
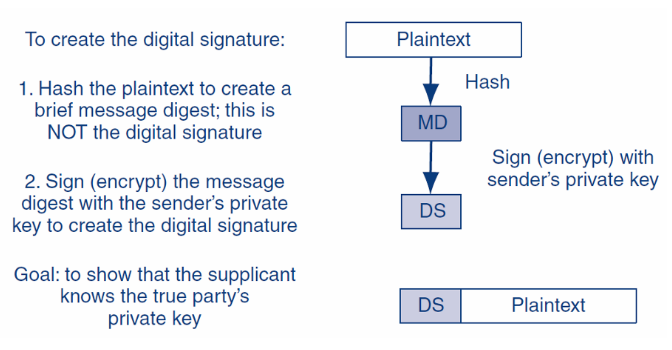
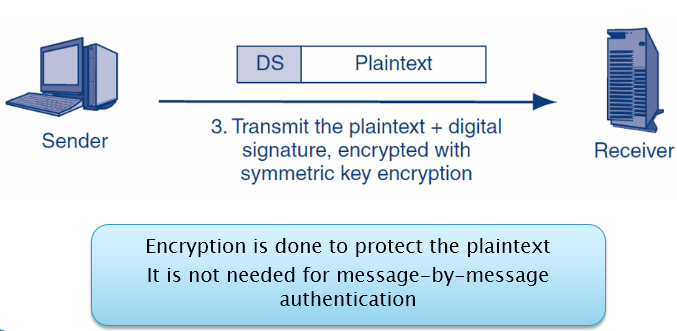
(1)发送方A先形成DS(MD+发送方私钥加密),将DS attach到 plaintext上,形成DS+plaintext,然后在用symmetric key加密;
(2)发送给接收方B;
(3)B接收到信息,先用symmetric key解密,然后再验证DS。即,先用true party的public key解密。其实这里的key来自于第三方的CA,而CA也相当于一套公私钥加解密机制,但是是早就install在你的OS里面了,这个部分就叫做数字证书。然后解密得到MD,再自己hash plaintext得到一个MD,比较得出完整性和验证发送者。
Message-by-Message Authentication?
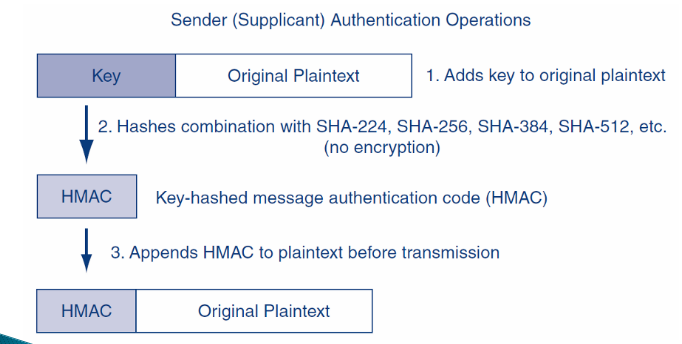
不必每一个message都验证,可以在上层控制,类似于流机制HMAC
symmetric key加密发送的时候,因为已经用了PKI机制,不用再加DS。
这篇关于公私钥加解密问题汇总的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!