本文主要是介绍open***2.2.2吊销客户端证书,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
1、进入特定的目录,并执行吊销证书的命令
[root@open***-server easy-rsa]# cd /tools/open***/open***-2.2.2/easy-rsa/2.0/ [root@open***-server 2.0]# ls build-ca build-key-pkcs12 inherit-inter openssl-0.9.8.cnf sign-req build-dh build-key-server keys openssl-1.0.0.cnf vars build-inter build-req list-crl pkitool vars.20170506 build-key build-req-pass Makefile README whichopensslcnf build-key-pass clean-all openssl-0.9.6.cnf revoke-full [root@open***-server 2.0]# source vars NOTE: If you run ./clean-all, I will be doing a rm -rf on /tools/open***/open***-2.2.2/easy-rsa/2.0/keys、 [root@open***-server 2.0]# ./revoke-full test 说明:使用revoke-full 用户,吊销用户的证书 Using configuration from /tools/open***/open***-2.2.2/easy-rsa/2.0/openssl-1.0.0.cnf Revoking Certificate 02. Data Base Updated Using configuration from /tools/open***/open***-2.2.2/easy-rsa/2.0/openssl-1.0.0.cnf test.crt: C = CN, ST = ZJ, L = HangZhou, O = molewan, OU = molewan, CN = test, name = molewan, emailAddress = 314324506@qq.com error 8 at 0 depth lookup:CRL signature failure 140070029928264:error:0D0C50A1:asn1 encoding routines:ASN1_item_verify:unknown message digest algorithm:a_verify.c:217:
2、查看吊销证书的信息
[root@open***-server 2.0]# cat keys/crl.pem 说明:查看证书的相关信息 -----BEGIN X509 CRL----- MIIBcjCB3DANBgkqhkiG9w0BAQQFADCBljELMAkGA1UEBhMCQ04xCzAJBgNVBAgT AlpKMREwDwYDVQQHEwhIYW5nWmhvdTEQMA4GA1UEChMHbW9sZXdhbjEQMA4GA1UE CxMHbW9sZXdhbjEQMA4GA1UEAxMHbW9sZXdhbjEQMA4GA1UEKRMHbW9sZXdhbjEf MB0GCSqGSIb3DQEJARYQMzE0MzI0NTA2QHFxLmNvbRcNMTcwNTA5MDgwOTM4WhcN MTcwNjA4MDgwOTM4WjAUMBICAQIXDTE3MDUwOTA4MDkzOFowDQYJKoZIhvcNAQEE BQADgYEARaB98TxZIKeEf7JrELHmMQgpjImZVD1KHJ+POE7tuGstz0jzHy3c3Gso dB2pLPJg3HHrWf63AbvwgnHXUjlT4NxJE9OY2rSpidzTIkV5ib5kxjkdUYBxu8bL e2uRwt0Gb+s+VypEGIDxOtCVILe7qtAevaOJksPszkGPoyvLx54= -----END X509 CRL----- [root@open***-server 2.0]# cat keys/index.txt V270505134346Z01unknown/C=CN/ST=ZJ/L=HangZhou/O=molewan/OU=molewan/CN=server/name=molewan/emailAddress=314324506@qq.com R270505135734Z170509080938Z02unknown/C=CN/ST=ZJ/L=HangZhou/O=molewan/OU=molewan/CN=test/name=molewan/emailAddress=314324506@qq.com V270505140448Z03unknown/C=CN/ST=ZJ/L=HangZhou/O=molewan/OU=molewan/CN=ett/name=molewan/emailAddress=314324506@qq.com V270507032952Z04unknown/C=CN/ST=ZJ/L=HangZhou/O=molewan/OU=molewan/CN=wanlong/name=molewan/emailAddress=314324506@qq.com V270507034952Z05unknown/C=CN/ST=ZJ/L=HangZhou/O=molewan/OU=molewan/CN=qinwen/name=molewan/emailAddress=314324506@qq.com V270507064737Z06unknown/C=CN/ST=ZJ/L=HangZhou/O=molewan/OU=molewan/CN=xiaobao/name=molewan/emailAddress=314324506@qq.com 说明:以R开头的是被吊销过的
3、将吊销证书的文件拷贝到/etc/open***/keys的目录下
[root@open***-server 2.0]# cp keys/crl.pem /etc/open***/keys/ 说明:将生成的crl.pem吊销文件复制到/etc/open***/keys,并在server.conf中加如下的内容,当用户拨入时,open***就会读取吊销列表的客户端 [root@open***-server open***]# echo "crl-verify /etc/open***/keys/crl.pem">>/etc/open***/server.conf 第一次吊销证书的时候有效 [root@open***-server open***]# ll /etc/open***/keys/crl.pem -rw-r--r-- 1 root root 556 May 9 16:15 /etc/open***/keys/crl.pem
4、证书被吊销后,需要重启open***服务才能生效
[root@open***-server open***]# pkill open*** [root@open***-server open***]# ps -ef | grep *** root 3112 2391 0 16:18 pts/0 00:00:00 grep *** [root@open***-server open***]# /usr/local/sbin/open*** --config /etc/open***/server.conf & [1] 3115 [root@open***-server open***]# ps -ef | grep *** | grep -v grep root 3115 2391 0 16:19 pts/0 00:00:00 /usr/local/sbin/open*** --config /etc/open***/server.conf
5、查看被吊销的用户test拨号的效果
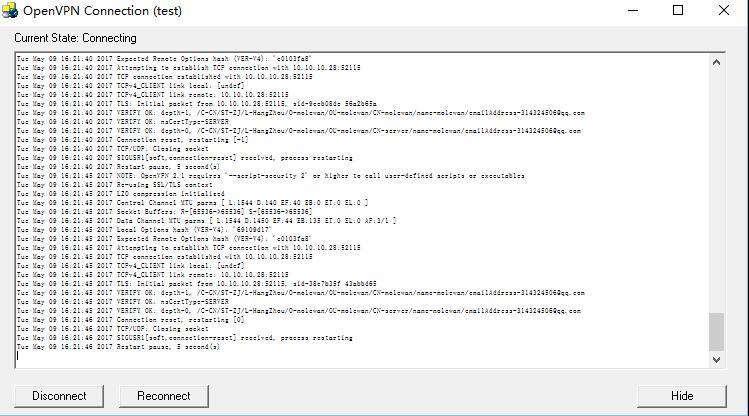 始终处于连接中,到此证书吊销已经成功
始终处于连接中,到此证书吊销已经成功
转载于:https://blog.51cto.com/molewan/1923759
这篇关于open***2.2.2吊销客户端证书的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!






