本文主要是介绍51进阶-信息搜集原理与实践2-20220615,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!

1/问答题
0.环境准备:
1)安装OWASP环境
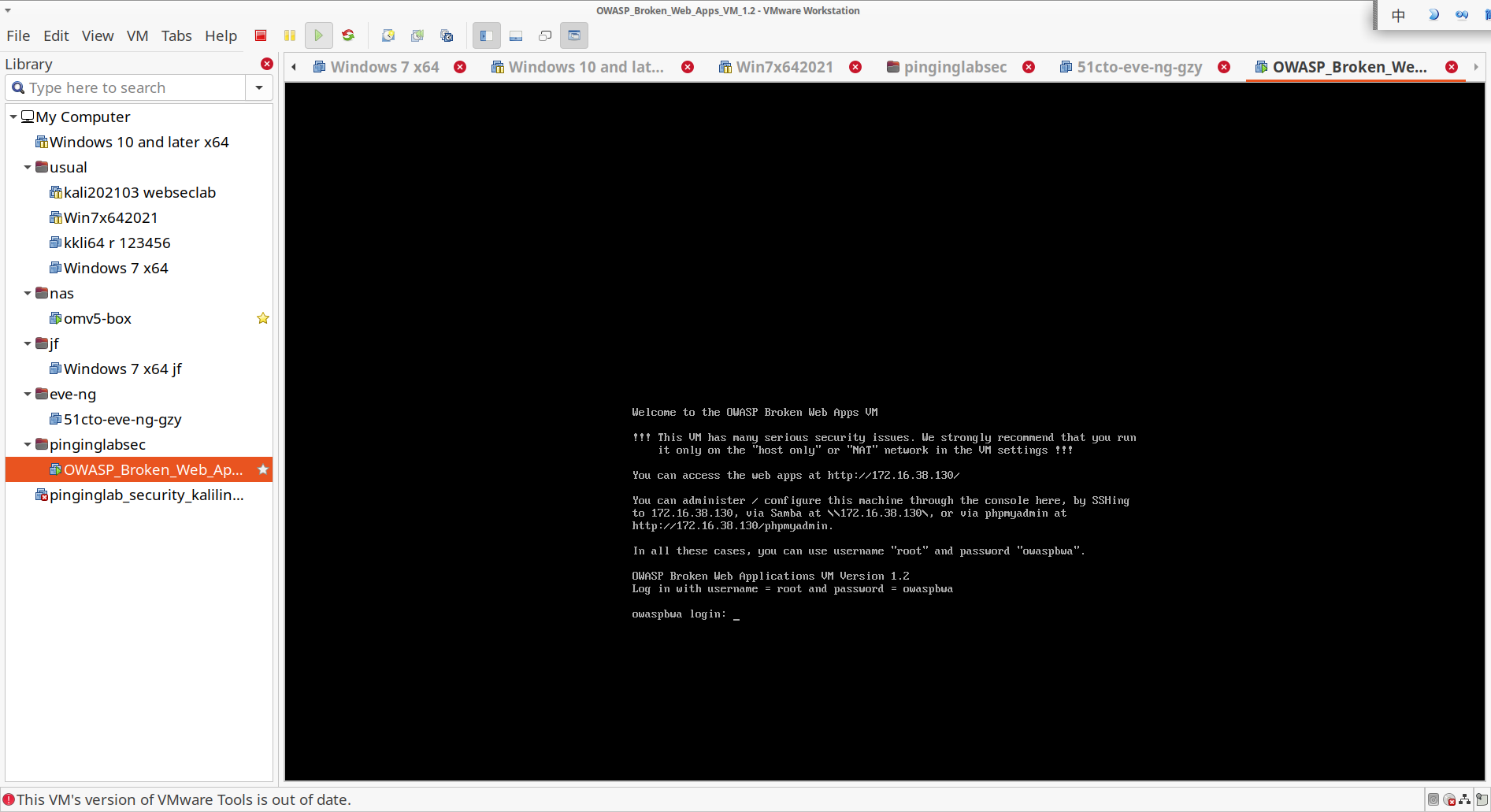
安装成功:
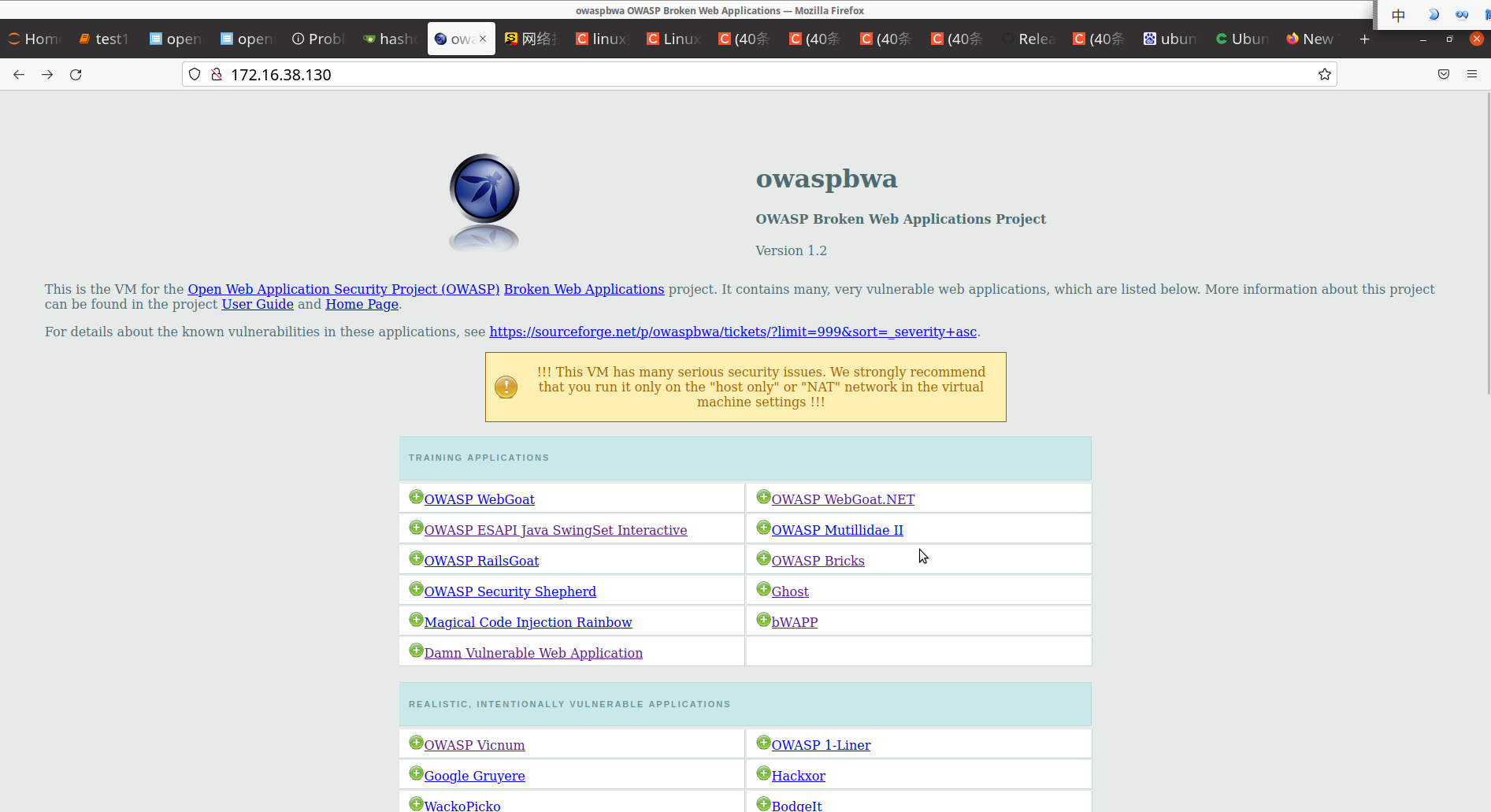
2)安装kali
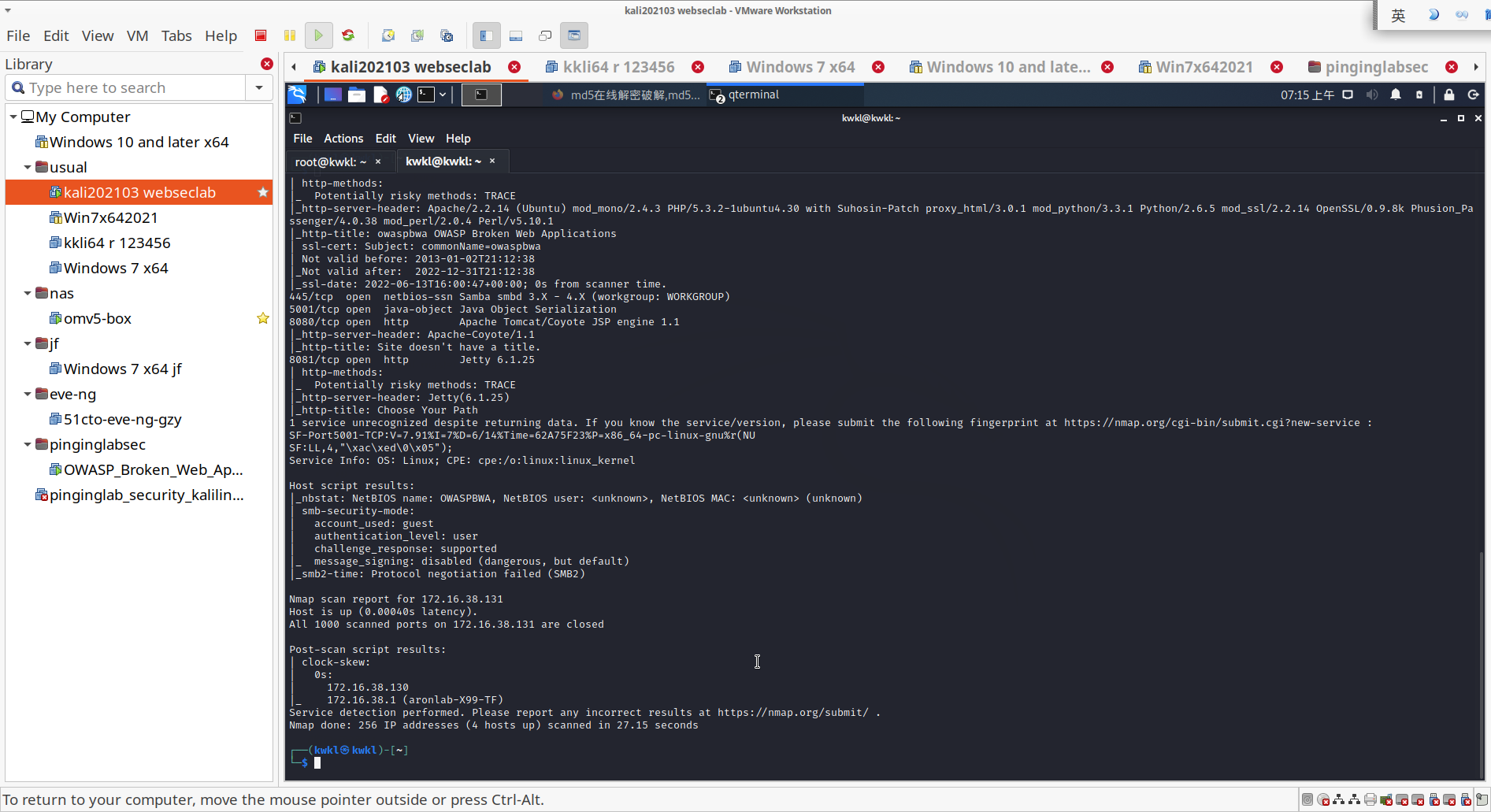
- 使用 nmap 扫描 owaspbwa 靶场
nmap -A 172.16.38.0/24
扫描C段,发现主机
``-A:详细扫描目标IP,加载所有脚本,尽可能地全面地探测信息
┌──(kwkl㉿kwkl)-[~]
└─$ nmap -A 172.16.38.0/24 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-14 00:00 HKT
Nmap scan report for aronlab-X99-TF (172.16.38.1)
Host is up (0.00066s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 40:7c:c9:d0:1e:e1:1b:92:93:10:aa:b8:39:a3:3c:96 (RSA)
| 256 4c:f4:55:04:10:08:0f:0e:9f:b1:56:26:81:14:32:b7 (ECDSA)
|_ 256 cd:0b:3c:c9:ff:b7:74:71:f5:69:5c:dd:a0:31:ee:c4 (ED25519)
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
902/tcp open ssl/vmware-auth VMware Authentication Daemon 1.10 (Uses VNC, SOAP)
3389/tcp open ms-wbt-server xrdp
5900/tcp open vnc RealVNC Enterprise 5.3 or later (protocol 5.0)
| vnc-info:
| Protocol version: 005.000
| Security types:
| Unknown security type (13)
| Unknown security type (133)
| RA2 (5)
| Unknown security type (129)
|_ Unknown security type (192)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelHost script results:
|_nbstat: NetBIOS name: ARONLAB-X99-TF, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-06-13T16:00:42
|_ start_date: N/ANmap scan report for 172.16.38.2
Host is up (0.0013s latency).
All 1000 scanned ports on 172.16.38.2 are closedNmap scan report for 172.16.38.130
Host is up (0.0033s latency).
Not shown: 991 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.3p1 Debian 3ubuntu4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 ea:83:1e:45:5a:a6:8c:43:1c:3c:e3:18:dd:fc:88:a5 (DSA)
|_ 2048 3a:94:d8:3f:e0:a2:7a:b8:c3:94:d7:5e:00:55:0c:a7 (RSA)
80/tcp open http Apache httpd 2.2.14 ((Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.30 with Suhosin-Patch proxy_html/3.0.1 mod_python/3.3.1 Python/2.6.5 mod_ssl/2.2.14 OpenSSL...)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.2.14 (Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.30 with Suhosin-Patch proxy_html/3.0.1 mod_python/3.3.1 Python/2.6.5 mod_ssl/2.2.14 OpenSSL/0.9.8k Phusion_Passenger/4.0.38 mod_perl/2.0.4 Perl/v5.10.1
|_http-title: owaspbwa OWASP Broken Web Applications
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Courier Imapd (released 2008)
|_imap-capabilities: THREAD=REFERENCES ACL IMAP4rev1 THREAD=ORDEREDSUBJECT completed SORT OK CAPABILITY ACL2=UNIONA0001 UIDPLUS IDLE QUOTA NAMESPACE CHILDREN
443/tcp open ssl/http Apache httpd 2.2.14 ((Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.30 with Suhosin-Patch proxy_html/3.0.1 mod_python/3.3.1 Python/2.6.5 mod_ssl/2.2.14 OpenSSL...)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.2.14 (Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.30 with Suhosin-Patch proxy_html/3.0.1 mod_python/3.3.1 Python/2.6.5 mod_ssl/2.2.14 OpenSSL/0.9.8k Phusion_Passenger/4.0.38 mod_perl/2.0.4 Perl/v5.10.1
|_http-title: owaspbwa OWASP Broken Web Applications
| ssl-cert: Subject: commonName=owaspbwa
| Not valid before: 2013-01-02T21:12:38
|_Not valid after: 2022-12-31T21:12:38
|_ssl-date: 2022-06-13T16:00:47+00:00; 0s from scanner time.
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
5001/tcp open java-object Java Object Serialization
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-server-header: Apache-Coyote/1.1
|_http-title: Site doesn't have a title.
8081/tcp open http Jetty 6.1.25
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Jetty(6.1.25)
|_http-title: Choose Your Path
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5001-TCP:V=7.91%I=7%D=6/14%Time=62A75F23%P=x86_64-pc-linux-gnu%r(NU
SF:LL,4,"\xac\xed\0\x05");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelHost script results:
|_nbstat: NetBIOS name: OWASPBWA, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)Nmap scan report for 172.16.38.131
Host is up (0.00040s latency).
All 1000 scanned ports on 172.16.38.131 are closedPost-scan script results:
| clock-skew:
| 0s:
| 172.16.38.130
|_ 172.16.38.1 (aronlab-X99-TF)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 256 IP addresses (4 hosts up) scanned in 27.15 seconds``─$ nmap -A 172.16.38.130
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-15 20:30 HKT
Nmap scan report for 172.16.38.130
Host is up (0.0022s latency).
Not shown: 991 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.3p1 Debian 3ubuntu4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 ea:83:1e:45:5a:a6:8c:43:1c:3c:e3:18:dd:fc:88:a5 (DSA)
|_ 2048 3a:94:d8:3f:e0:a2:7a:b8:c3:94:d7:5e:00:55:0c:a7 (RSA)
80/tcp open http Apache httpd 2.2.14 ((Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.30 with Suhosin-Patch proxy_html/3.0.1 mod_python/3.3.1 Python/2.6.5 mod_ssl/2.2.14 OpenSSL...)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.2.14 (Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.30 with Suhosin-Patch proxy_html/3.0.1 mod_python/3.3.1 Python/2.6.5 mod_ssl/2.2.14 OpenSSL/0.9.8k Phusion_Passenger/4.0.38 mod_perl/2.0.4 Perl/v5.10.1
|_http-title: owaspbwa OWASP Broken Web Applications
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Courier Imapd (released 2008)
|_imap-capabilities: CHILDREN QUOTA THREAD=ORDEREDSUBJECT IMAP4rev1 SORT UIDPLUS ACL THREAD=REFERENCES ACL2=UNIONA0001 OK CAPABILITY IDLE completed NAMESPACE
443/tcp open ssl/http Apache httpd 2.2.14 ((Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.30 with Suhosin-Patch proxy_html/3.0.1 mod_python/3.3.1 Python/2.6.5 mod_ssl/2.2.14 OpenSSL...)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.2.14 (Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.30 with Suhosin-Patch proxy_html/3.0.1 mod_python/3.3.1 Python/2.6.5 mod_ssl/2.2.14 OpenSSL/0.9.8k Phusion_Passenger/4.0.38 mod_perl/2.0.4 Perl/v5.10.1
|_http-title: owaspbwa OWASP Broken Web Applications
| ssl-cert: Subject: commonName=owaspbwa
| Not valid before: 2013-01-02T21:12:38
|_Not valid after: 2022-12-31T21:12:38
|_ssl-date: 2022-06-15T12:30:41+00:00; -3s from scanner time.
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
5001/tcp open java-object Java Object Serialization
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-server-header: Apache-Coyote/1.1
|_http-title: Site doesn't have a title.
8081/tcp open http Jetty 6.1.25
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Jetty(6.1.25)
|_http-title: Choose Your Path
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5001-TCP:V=7.91%I=7%D=6/15%Time=62A9D0E8%P=x86_64-pc-linux-gnu%r(NU
SF:LL,4,"\xac\xed\0\x05");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelHost script results:
|_clock-skew: mean: -2s, deviation: 0s, median: -3s
|_nbstat: NetBIOS name: OWASPBWA, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.44 seconds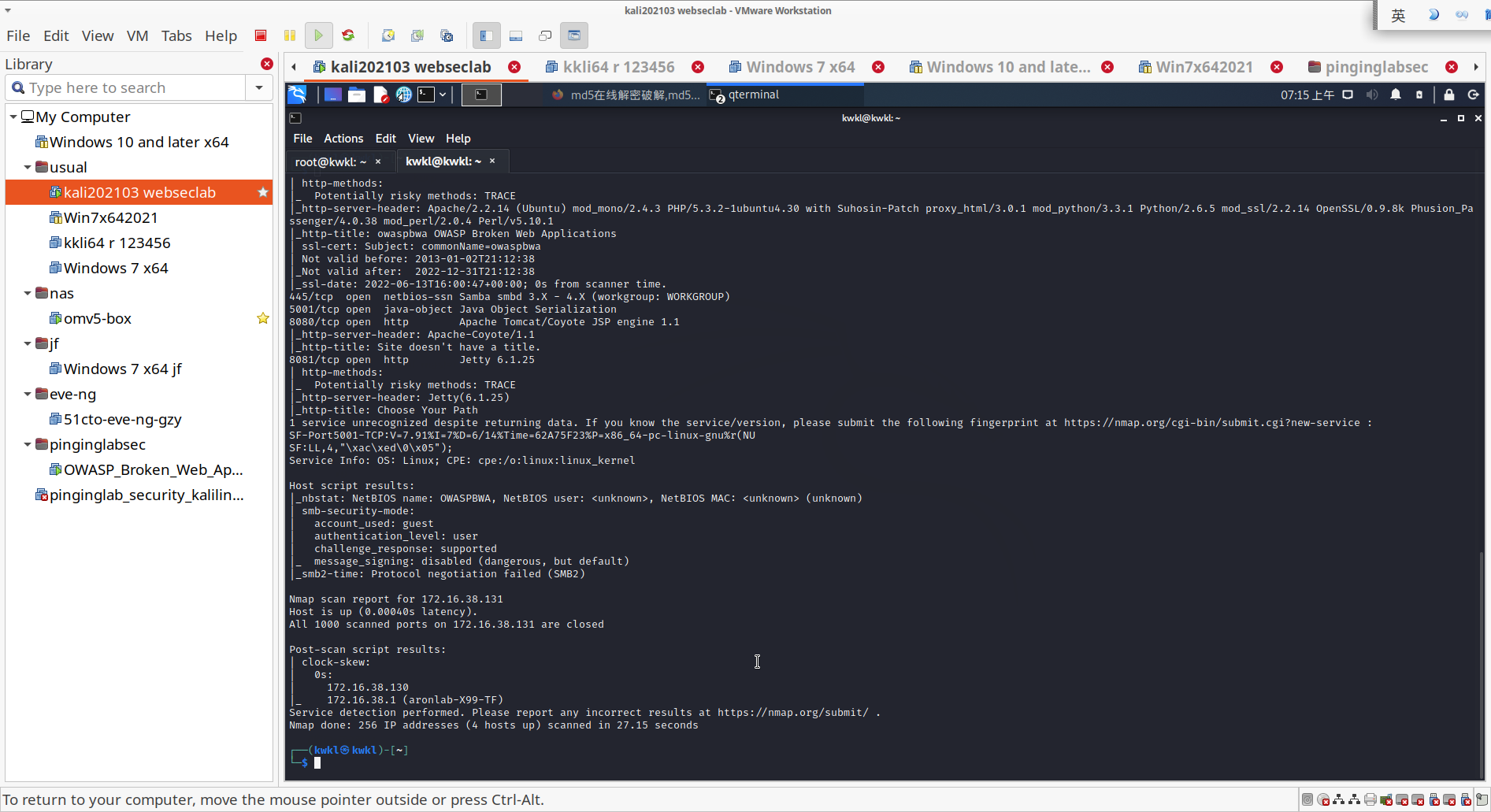
使用nmap -A 命令
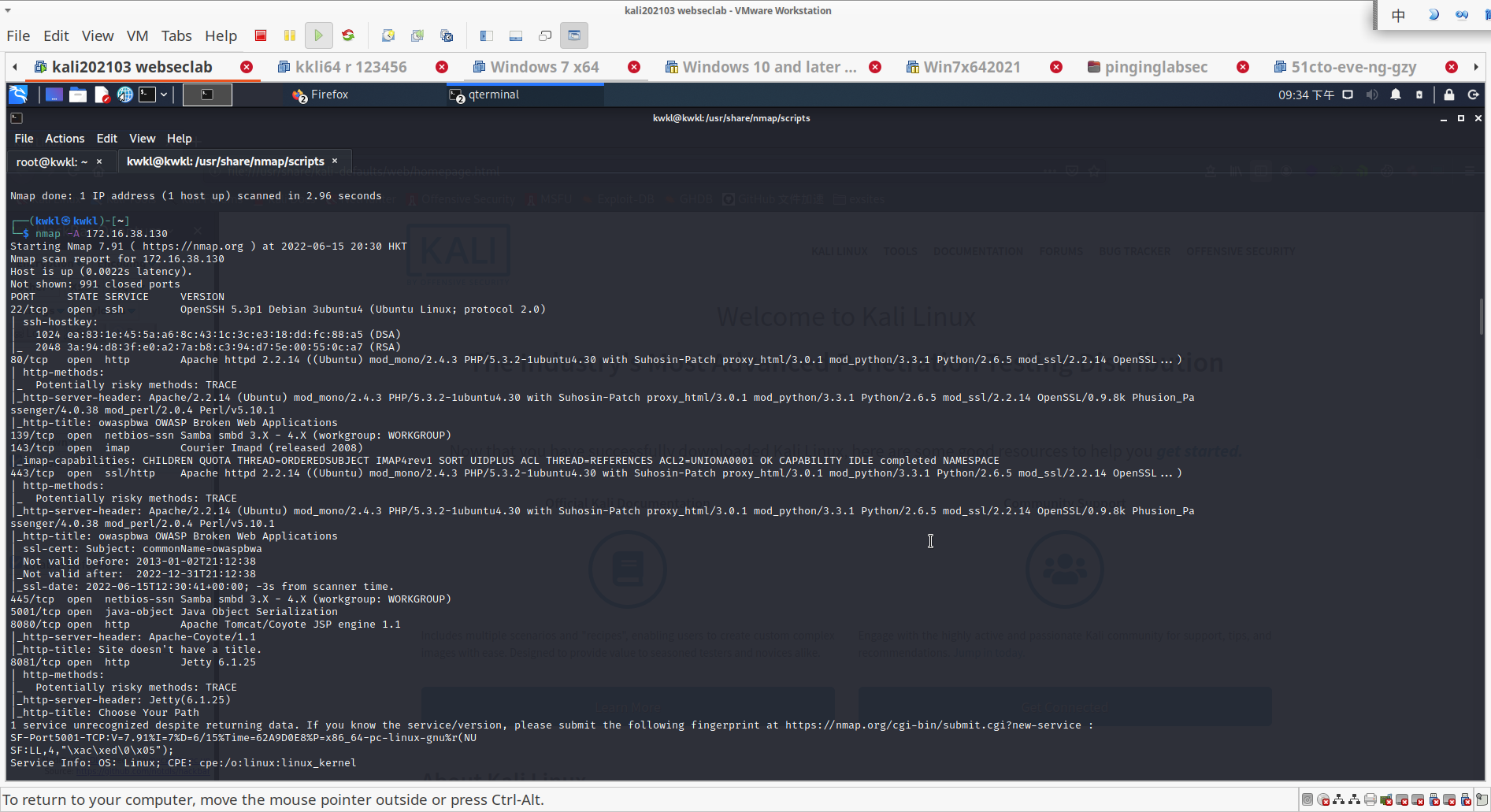
- 找出主机开放的端口
┌──(kwkl㉿kwkl)-[~]
└─$ nmap -p- 172.16.38.130
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-15 20:37 HKT
Nmap scan report for 172.16.38.130
Host is up (0.00068s latency).
Not shown: 65526 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
143/tcp open imap
443/tcp open https
445/tcp open microsoft-ds
5001/tcp open commplex-link
8080/tcp open http-proxy
8081/tcp open blackice-icecapNmap done: 1 IP address (1 host up) scanned in 3.84 seconds-p-:扫描全部端口
开放端口有:
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
143/tcp open imap
443/tcp open https
445/tcp open microsoft-ds
5001/tcp open commplex-link
8080/tcp open http-proxy
8081/tcp open blackice-icecap
找出开放大端口情况
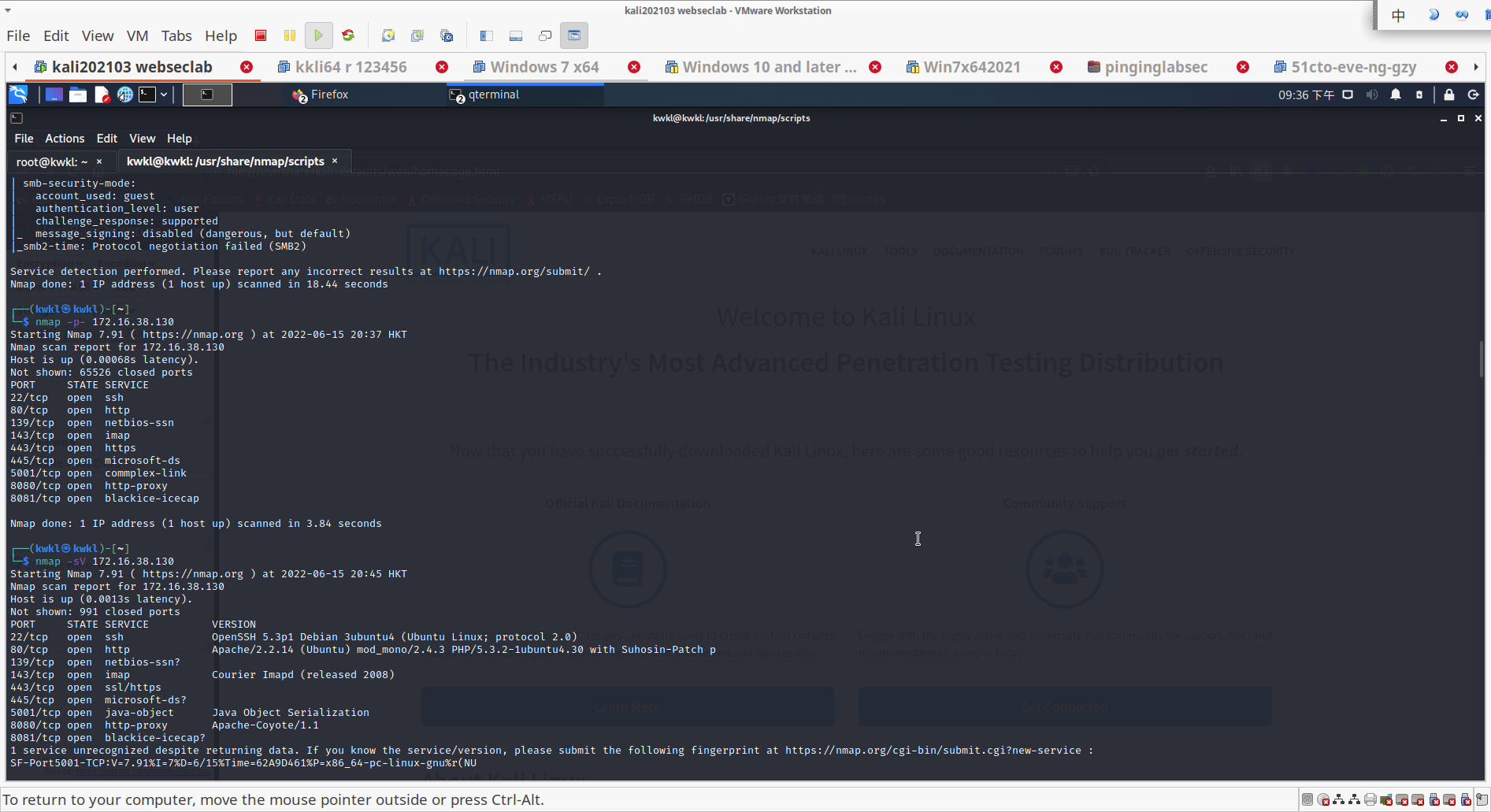
- 根据端口扫描特定服务(如 mysql 或 apache 等)
nmap -sV [host]
其中,-sV表示实施服务版本探测。
┌──(kwkl㉿kwkl)-[~]
└─$ nmap -p- -sV 172.16.38.130
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-15 20:46 HKT
Nmap scan report for 172.16.38.130
Host is up (0.0019s latency).
Not shown: 65526 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.3p1 Debian 3ubuntu4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.14 ((Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.30 with Suhosin-Patch proxy_html/3.0.1 mod_python/3.3.1 Python/2.6.5 mod_ssl/2.2.14 OpenSSL...)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Courier Imapd (released 2008)
443/tcp open ssl/http Apache httpd 2.2.14 ((Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.30 with Suhosin-Patch proxy_html/3.0.1 mod_python/3.3.1 Python/2.6.5 mod_ssl/2.2.14 OpenSSL...)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
5001/tcp open java-object Java Object Serialization
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
8081/tcp open http Jetty 6.1.25
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5001-TCP:V=7.91%I=7%D=6/15%Time=62A9D494%P=x86_64-pc-linux-gnu%r(NU
SF:LL,4,"\xac\xed\0\x05");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.39 seconds查看服务情况
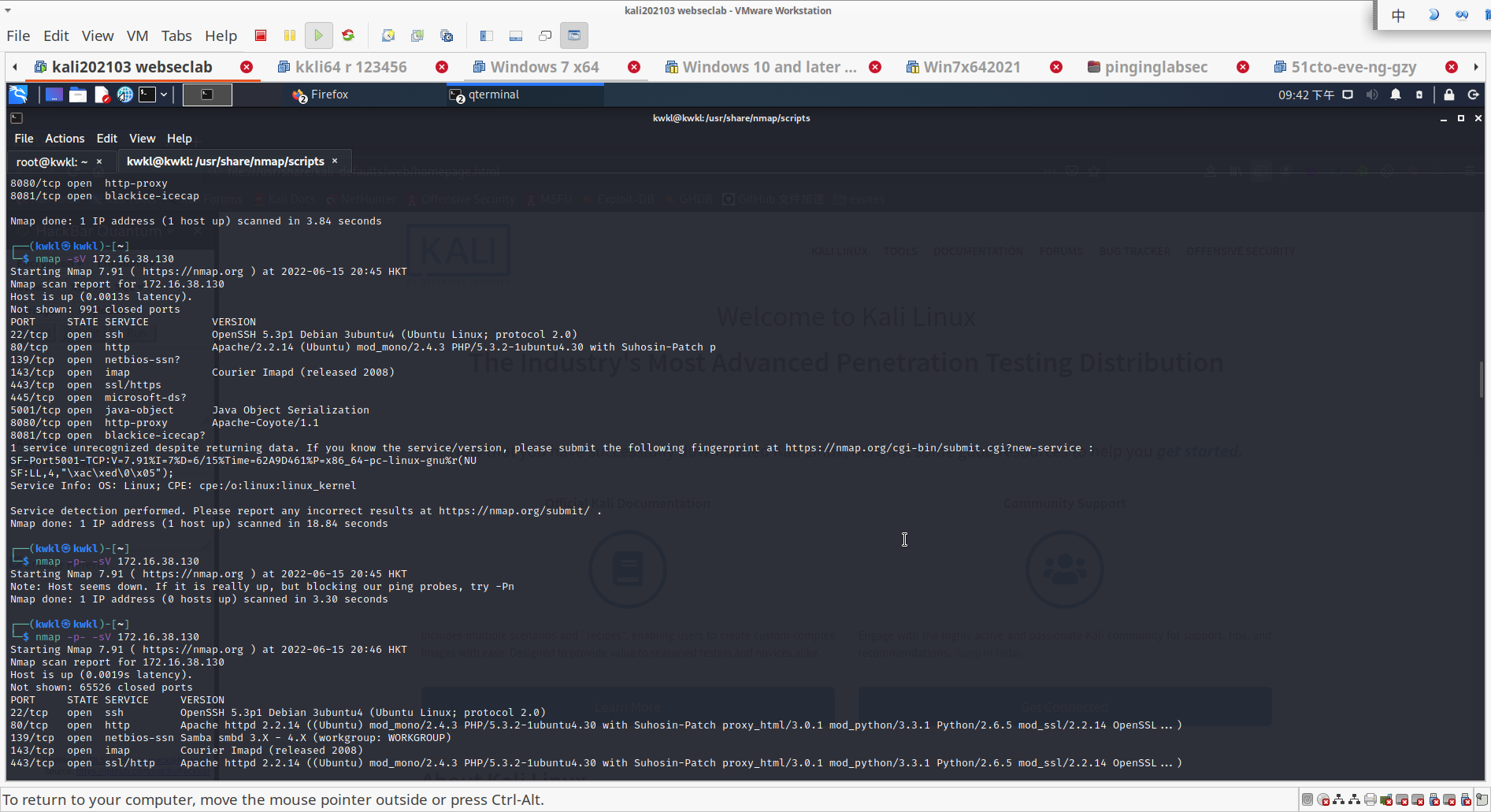
- 在 nmap 的 script 中找到与服务有关的任一脚本
寻找脚本
┌──(kwkl㉿kwkl)-[~]
└─$ ls /usr/share/nmap/scripts
acarsd-info.nse fcrdns.nse https-redirect.nse ms-sql-info.nse smb-os-discovery.nse
address-info.nse finger.nse http-stored-xss.nse ms-sql-ntlm-info.nse smb-print-text.nse
afp-brute.nse fingerprint-strings.nse http-svn-enum.nse ms-sql-query.nse smb-protocols.nse
afp-ls.nse firewalk.nse http-svn-info.nse ms-sql-tables.nse smb-psexec.nse
afp-path-vuln.nse firewall-bypass.nse http-title.nse ms-sql-xp-cmdshell.nse smb-security-mode.nse
afp-serverinfo.nse flume-master-info.nse http-tplink-dir-traversal.nse mtrace.nse smb-server-stats.nse
afp-showmount.nse fox-info.nse http-trace.nse murmur-version.nse smb-system-info.nse
ajp-auth.nse freelancer-info.nse http-traceroute.nse mysql-audit.nse smb-vuln-conficker.nse
ajp-brute.nse ftp-anon.nse http-trane-info.nse mysql-brute.nse smb-vuln-cve2009-3103.nse
ajp-headers.nse ftp-bounce.nse http-unsafe-output-escaping.nse mysql-databases.nse smb-vuln-cve-2017-7494.nse
ajp-methods.nse ftp-brute.nse http-useragent-tester.nse mysql-dump-hashes.nse smb-vuln-ms06-025.nse
ajp-request.nse ftp-libopie.nse http-userdir-enum.nse mysql-empty-password.nse smb-vuln-ms07-029.nse
allseeingeye-info.nse ftp-proftpd-backdoor.nse http-vhosts.nse mysql-enum.nse smb-vuln-ms08-067.nse
amqp-info.nse ftp-syst.nse http-virustotal.nse mysql-info.nse smb-vuln-ms10-054.nse
asn-query.nse ftp-vsftpd-backdoor.nse http-vlcstreamer-ls.nse mysql-query.nse smb-vuln-ms10-061.nse
auth-owners.nse ftp-vuln-cve2010-4221.nse http-vmware-path-vuln.nse mysql-users.nse smb-vuln-ms17-010.nse
auth-spoof.nse ganglia-info.nse http-vuln-cve2006-3392.nse mysql-variables.nse smb-vuln-regsvc-dos.nse
backorifice-brute.nse giop-info.nse http-vuln-cve2009-3960.nse mysql-vuln-cve2012-2122.nse smb-vuln-webexec.nse
backorifice-info.nse gkrellm-info.nse http-vuln-cve2010-0738.nse nat-pmp-info.nse smb-webexec-exploit.nse
bacnet-info.nse gopher-ls.nse http-vuln-cve2010-2861.nse nat-pmp-mapport.nse smtp-brute.nse
banner.nse gpsd-info.nse http-vuln-cve2011-3192.nse nbd-info.nse smtp-commands.nse
bitcoin-getaddr.nse hadoop-datanode-info.nse http-vuln-cve2011-3368.nse nbstat.nse smtp-enum-users.nse
bitcoin-info.nse hadoop-jobtracker-info.nse http-vuln-cve2012-1823.nse ncp-enum-users.nse smtp-ntlm-info.nse
bitcoinrpc-info.nse hadoop-namenode-info.nse http-vuln-cve2013-0156.nse ncp-serverinfo.nse smtp-open-relay.nse
bittorrent-discovery.nse hadoop-secondary-namenode-info.nse http-vuln-cve2013-6786.nse ndmp-fs-info.nse smtp-strangeport.nse
bjnp-discover.nse hadoop-tasktracker-info.nse http-vuln-cve2013-7091.nse ndmp-version.nse smtp-vuln-cve2010-4344.nse
broadcast-ataoe-discover.nse hbase-master-info.nse http-vuln-cve2014-2126.nse nessus-brute.nse smtp-vuln-cve2011-1720.nse
broadcast-avahi-dos.nse hbase-region-info.nse http-vuln-cve2014-2127.nse nessus-xmlrpc-brute.nse smtp-vuln-cve2011-1764.nse
broadcast-bjnp-discover.nse hddtemp-info.nse http-vuln-cve2014-2128.nse netbus-auth-bypass.nse sniffer-detect.nse
broadcast-db2-discover.nse hnap-info.nse http-vuln-cve2014-2129.nse netbus-brute.nse snmp-brute.nse
broadcast-dhcp6-discover.nse hostmap-bfk.nse http-vuln-cve2014-3704.nse netbus-info.nse snmp-hh3c-logins.nse
broadcast-dhcp-discover.nse hostmap-crtsh.nse http-vuln-cve2014-8877.nse netbus-version.nse snmp-info.nse
broadcast-dns-service-discovery.nse hostmap-robtex.nse http-vuln-cve2015-1427.nse nexpose-brute.nse snmp-interfaces.nse
broadcast-dropbox-listener.nse http-adobe-coldfusion-apsa1301.nse http-vuln-cve2015-1635.nse nfs-ls.nse snmp-ios-config.nse
broadcast-eigrp-discovery.nse http-affiliate-id.nse http-vuln-cve2017-1001000.nse nfs-showmount.nse snmp-netstat.nse
broadcast-hid-discoveryd.nse http-apache-negotiation.nse http-vuln-cve2017-5638.nse nfs-statfs.nse snmp-processes.nse
broadcast-igmp-discovery.nse http-apache-server-status.nse http-vuln-cve2017-5689.nse nje-node-brute.nse snmp-sysdescr.nse
broadcast-jenkins-discover.nse http-aspnet-debug.nse http-vuln-cve2017-8917.nse nje-pass-brute.nse snmp-win32-services.nse
broadcast-listener.nse http-auth-finder.nse http-vuln-misfortune-cookie.nse nntp-ntlm-info.nse snmp-win32-shares.nse
broadcast-ms-sql-discover.nse http-auth.nse http-vuln-wnr1000-creds.nse nping-brute.nse snmp-win32-software.nse
broadcast-netbios-master-browser.nse http-avaya-ipoffice-users.nse http-waf-detect.nse nrpe-enum.nse snmp-win32-users.nse
broadcast-networker-discover.nse http-awstatstotals-exec.nse http-waf-fingerprint.nse ntp-info.nse socks-auth-info.nse
broadcast-novell-locate.nse http-axis2-dir-traversal.nse http-webdav-scan.nse ntp-monlist.nse socks-brute.nse
broadcast-ospf2-discover.nse http-backup-finder.nse http-wordpress-brute.nse omp2-brute.nse socks-open-proxy.nse
broadcast-pc-anywhere.nse http-barracuda-dir-traversal.nse http-wordpress-enum.nse omp2-enum-targets.nse ssh2-enum-algos.nse
broadcast-pc-duo.nse http-bigip-cookie.nse http-wordpress-users.nse omron-info.nse ssh-auth-methods.nse
broadcast-pim-discovery.nse http-brute.nse http-xssed.nse openlookup-info.nse ssh-brute.nse
broadcast-ping.nse http-cakephp-version.nse iax2-brute.nse openvas-otp-brute.nse ssh-hostkey.nse
broadcast-pppoe-discover.nse http-chrono.nse iax2-version.nse openwebnet-discovery.nse ssh-publickey-acceptance.nse
broadcast-rip-discover.nse http-cisco-anyconnect.nse icap-info.nse oracle-brute.nse ssh-run.nse
broadcast-ripng-discover.nse http-coldfusion-subzero.nse iec-identify.nse oracle-brute-stealth.nse sshv1.nse
broadcast-sonicwall-discover.nse http-comments-displayer.nse ike-version.nse oracle-enum-users.nse ssl-ccs-injection.nse
broadcast-sybase-asa-discover.nse http-config-backup.nse imap-brute.nse oracle-sid-brute.nse ssl-cert-intaddr.nse
broadcast-tellstick-discover.nse http-cookie-flags.nse imap-capabilities.nse oracle-tns-version.nse ssl-cert.nse
broadcast-upnp-info.nse http-cors.nse imap-ntlm-info.nse ovs-agent-version.nse ssl-date.nse
broadcast-versant-locate.nse http-cross-domain-policy.nse impress-remote-discover.nse p2p-conficker.nse ssl-dh-params.nse
broadcast-wake-on-lan.nse http-csrf.nse informix-brute.nse path-mtu.nse ssl-enum-ciphers.nse
broadcast-wpad-discover.nse http-date.nse informix-query.nse pcanywhere-brute.nse ssl-heartbleed.nse
broadcast-wsdd-discover.nse http-default-accounts.nse informix-tables.nse pcworx-info.nse ssl-known-key.nse
broadcast-xdmcp-discover.nse http-devframework.nse ip-forwarding.nse pgsql-brute.nse ssl-poodle.nse
cassandra-brute.nse http-dlink-backdoor.nse ip-geolocation-geoplugin.nse pjl-ready-message.nse sslv2-drown.nse
cassandra-info.nse http-dombased-xss.nse ip-geolocation-ipinfodb.nse pop3-brute.nse sslv2.nse
cccam-version.nse http-domino-enum-passwords.nse ip-geolocation-map-bing.nse pop3-capabilities.nse sstp-discover.nse
cics-enum.nse http-drupal-enum.nse ip-geolocation-map-google.nse pop3-ntlm-info.nse stun-info.nse
cics-info.nse http-drupal-enum-users.nse ip-geolocation-map-kml.nse pptp-version.nse stun-version.nse
cics-user-brute.nse http-enum.nse ip-geolocation-maxmind.nse puppet-naivesigning.nse stuxnet-detect.nse
cics-user-enum.nse http-errors.nse ip-https-discover.nse qconn-exec.nse supermicro-ipmi-conf.nse
citrix-brute-xml.nse http-exif-spider.nse ipidseq.nse qscan.nse svn-brute.nse
citrix-enum-apps.nse http-favicon.nse ipmi-brute.nse quake1-info.nse targets-asn.nse
citrix-enum-apps-xml.nse http-feed.nse ipmi-cipher-zero.nse quake3-info.nse targets-ipv6-map4to6.nse
citrix-enum-servers.nse http-fetch.nse ipmi-version.nse quake3-master-getservers.nse targets-ipv6-multicast-echo.nse
citrix-enum-servers-xml.nse http-fileupload-exploiter.nse ipv6-multicast-mld-list.nse rdp-enum-encryption.nse targets-ipv6-multicast-invalid-dst.nse
clamav-exec.nse http-form-brute.nse ipv6-node-info.nse rdp-ntlm-info.nse targets-ipv6-multicast-mld.nse
clock-skew.nse http-form-fuzzer.nse ipv6-ra-flood.nse rdp-vuln-ms12-020.nse targets-ipv6-multicast-slaac.nse
coap-resources.nse http-frontpage-login.nse irc-botnet-channels.nse realvnc-auth-bypass.nse targets-ipv6-wordlist.nse
couchdb-databases.nse http-generator.nse irc-brute.nse redis-brute.nse targets-sniffer.nse
couchdb-stats.nse http-git.nse irc-info.nse redis-info.nse targets-traceroute.nse
creds-summary.nse http-gitweb-projects-enum.nse irc-sasl-brute.nse resolveall.nse targets-xml.nse
cups-info.nse http-google-malware.nse irc-unrealircd-backdoor.nse reverse-index.nse teamspeak2-version.nse
cups-queue-info.nse http-grep.nse iscsi-brute.nse rexec-brute.nse telnet-brute.nse
cvs-brute.nse http-headers.nse iscsi-info.nse rfc868-time.nse telnet-encryption.nse
cvs-brute-repository.nse http-hp-ilo-info.nse isns-info.nse riak-http-info.nse telnet-ntlm-info.nse
daap-get-library.nse http-huawei-hg5xx-vuln.nse jdwp-exec.nse rlogin-brute.nse tftp-enum.nse
daytime.nse http-icloud-findmyiphone.nse jdwp-info.nse rmi-dumpregistry.nse tls-alpn.nse
db2-das-info.nse http-icloud-sendmsg.nse jdwp-inject.nse rmi-vuln-classloader.nse tls-nextprotoneg.nse
deluge-rpc-brute.nse http-iis-short-name-brute.nse jdwp-version.nse rpcap-brute.nse tls-ticketbleed.nse
dhcp-discover.nse http-iis-webdav-vuln.nse knx-gateway-discover.nse rpcap-info.nse tn3270-screen.nse
dicom-brute.nse http-internal-ip-disclosure.nse knx-gateway-info.nse rpc-grind.nse tor-consensus-checker.nse
dicom-ping.nse http-joomla-brute.nse krb5-enum-users.nse rpcinfo.nse traceroute-geolocation.nse
dict-info.nse http-jsonp-detection.nse ldap-brute.nse rsa-vuln-roca.nse tso-brute.nse
distcc-cve2004-2687.nse http-litespeed-sourcecode-download.nse ldap-novell-getpass.nse rsync-brute.nse tso-enum.nse
dns-blacklist.nse http-ls.nse ldap-rootdse.nse rsync-list-modules.nse ubiquiti-discovery.nse
dns-brute.nse http-majordomo2-dir-traversal.nse ldap-search.nse rtsp-methods.nse unittest.nse
dns-cache-snoop.nse http-malware-host.nse lexmark-config.nse rtsp-url-brute.nse unusual-port.nse
dns-check-zone.nse http-mcmp.nse llmnr-resolve.nse rusers.nse upnp-info.nse
dns-client-subnet-scan.nse http-methods.nse lltd-discovery.nse s7-info.nse uptime-agent-info.nse
dns-fuzz.nse http-method-tamper.nse lu-enum.nse samba-vuln-cve-2012-1182.nse url-snarf.nse
dns-ip6-arpa-scan.nse http-mobileversion-checker.nse maxdb-info.nse script.db ventrilo-info.nse
dns-nsec3-enum.nse http-ntlm-info.nse mcafee-epo-agent.nse servicetags.nse versant-info.nse
dns-nsec-enum.nse http-open-proxy.nse membase-brute.nse shodan-api.nse vmauthd-brute.nse
dns-nsid.nse http-open-redirect.nse membase-http-info.nse sip-brute.nse vmware-version.nse
dns-random-srcport.nse http-passwd.nse memcached-info.nse sip-call-spoof.nse vnc-brute.nse
dns-random-txid.nse http-phpmyadmin-dir-traversal.nse metasploit-info.nse sip-enum-users.nse vnc-info.nse
dns-recursion.nse http-phpself-xss.nse metasploit-msgrpc-brute.nse sip-methods.nse vnc-title.nse
dns-service-discovery.nse http-php-version.nse metasploit-xmlrpc-brute.nse skypev2-version.nse voldemort-info.nse
dns-srv-enum.nse http-proxy-brute.nse mikrotik-routeros-brute.nse smb2-capabilities.nse vtam-enum.nse
dns-update.nse http-put.nse mmouse-brute.nse smb2-security-mode.nse vulners.nse
dns-zeustracker.nse http-qnap-nas-info.nse mmouse-exec.nse smb2-time.nse vuze-dht-info.nse
dns-zone-transfer.nse http-referer-checker.nse modbus-discover.nse smb2-vuln-uptime.nse wdb-version.nse
docker-version.nse http-rfi-spider.nse mongodb-brute.nse smb-brute.nse weblogic-t3-info.nse
domcon-brute.nse http-robots.txt.nse mongodb-databases.nse smb-double-pulsar-backdoor.nse whois-domain.nse
domcon-cmd.nse http-robtex-reverse-ip.nse mongodb-info.nse smb-enum-domains.nse whois-ip.nse
domino-enum-users.nse http-robtex-shared-ns.nse mqtt-subscribe.nse smb-enum-groups.nse wsdd-discover.nse
dpap-brute.nse http-sap-netweaver-leak.nse mrinfo.nse smb-enum-processes.nse x11-access.nse
drda-brute.nse http-security-headers.nse msrpc-enum.nse smb-enum-services.nse xdmcp-discover.nse
drda-info.nse http-server-header.nse ms-sql-brute.nse smb-enum-sessions.nse xmlrpc-methods.nse
duplicates.nse http-shellshock.nse ms-sql-config.nse smb-enum-shares.nse xmpp-brute.nse
eap-info.nse http-sitemap-generator.nse ms-sql-dac.nse smb-enum-users.nse xmpp-info.nse
enip-info.nse http-slowloris-check.nse ms-sql-dump-hashes.nse smb-flood.nse
epmd-info.nse http-slowloris.nse ms-sql-empty-password.nse smb-ls.nse
eppc-enum-processes.nse http-sql-injection.nse ms-sql-hasdbaccess.nse smb-mbenum.nse寻找apache相关的脚本┌──(kwkl㉿kwkl)-[~]
└─$ ls /usr/share/nmap/scripts | grep apache
http-apache-negotiation.nse
http-apache-server-status.nsesamba服务相关脚本
└─$ ls /usr/share/nmap/scripts | grep samba
samba-vuln-cve-2012-1182.nse┌──(kwkl㉿kwkl)-[/usr/share/nmap/scripts]
└─$ ls /usr/share/nmap/scripts | grep smb-vuln
smb-vuln-conficker.nse
smb-vuln-cve2009-3103.nse
smb-vuln-cve-2017-7494.nse
smb-vuln-ms06-025.nse
smb-vuln-ms07-029.nse
smb-vuln-ms08-067.nse
smb-vuln-ms10-054.nse
smb-vuln-ms10-061.nse
smb-vuln-ms17-010.nse
smb-vuln-regsvc-dos.nse
smb-vuln-webexec.nse查找http服务相关脚本
┌──(kwkl㉿kwkl)-[/usr/share/nmap/scripts]
└─$ ls /usr/share/nmap/scripts | grep http-vuln
http-vuln-cve2006-3392.nse
http-vuln-cve2009-3960.nse
http-vuln-cve2010-0738.nse
http-vuln-cve2010-2861.nse
http-vuln-cve2011-3192.nse
http-vuln-cve2011-3368.nse
http-vuln-cve2012-1823.nse
http-vuln-cve2013-0156.nse
http-vuln-cve2013-6786.nse
http-vuln-cve2013-7091.nse
http-vuln-cve2014-2126.nse
http-vuln-cve2014-2127.nse
http-vuln-cve2014-2128.nse
http-vuln-cve2014-2129.nse
http-vuln-cve2014-3704.nse
http-vuln-cve2014-8877.nse
http-vuln-cve2015-1427.nse
http-vuln-cve2015-1635.nse
http-vuln-cve2017-1001000.nse
http-vuln-cve2017-5638.nse
http-vuln-cve2017-5689.nse
http-vuln-cve2017-8917.nse
http-vuln-misfortune-cookie.nse
http-vuln-wnr1000-creds.nsemysql服务相关的脚本┌──(kwkl㉿kwkl)-[/usr/share/nmap/scripts]
└─$ ls /usr/share/nmap/scripts | grep mysql
mysql-audit.nse
mysql-brute.nse
mysql-databases.nse
mysql-dump-hashes.nse
mysql-empty-password.nse
mysql-enum.nse
mysql-info.nse
mysql-query.nse
mysql-users.nse
mysql-variables.nse
mysql-vuln-cve2012-2122.nse使用grep命令查询脚本
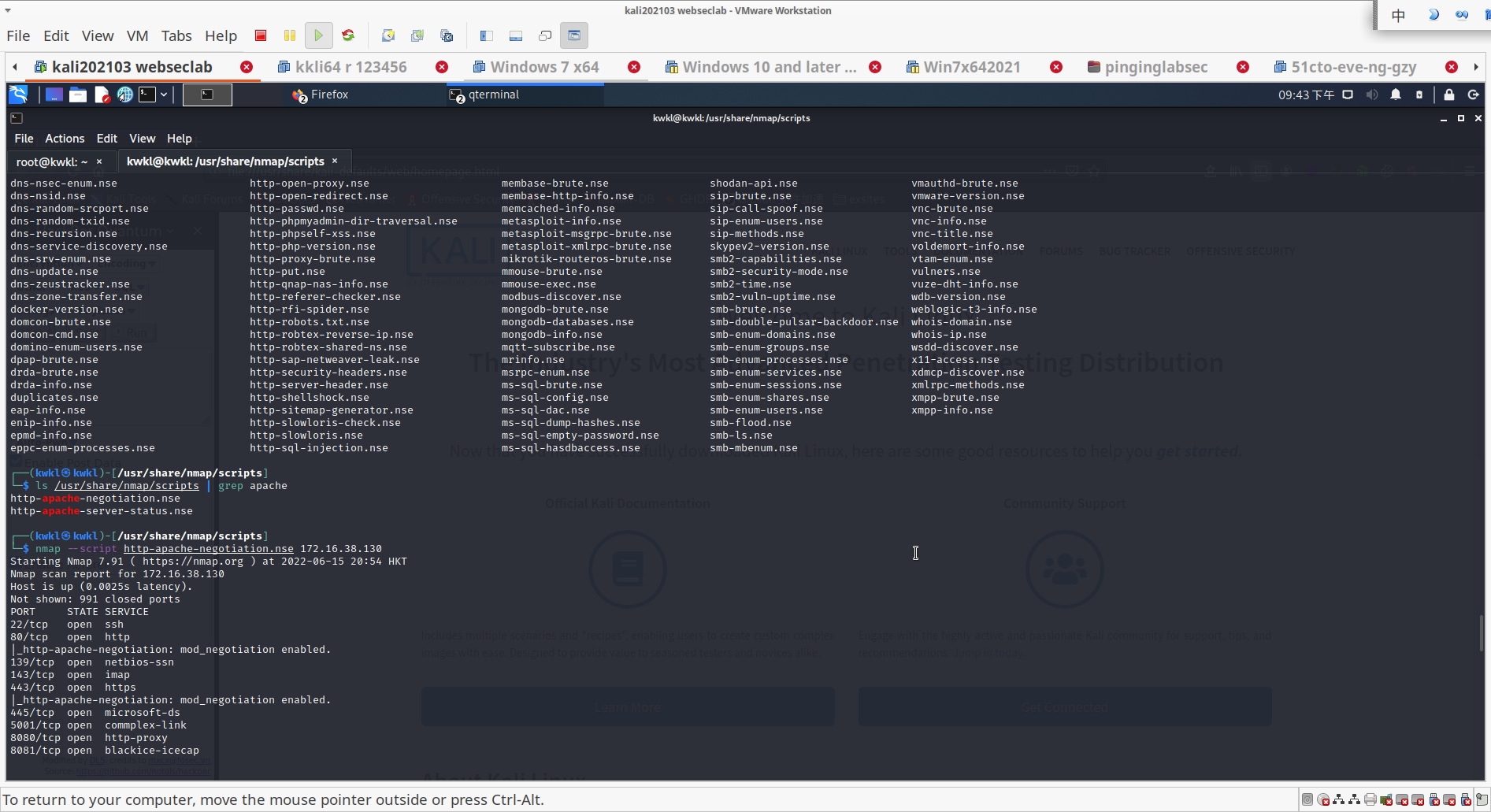
- 使用对应的脚本对指定服务进行扫描
利用apache相关脚本探测
┌──(kwkl㉿kwkl)-[/usr/share/nmap/scripts]
└─$ nmap --script http-apache-negotiation.nse 172.16.38.130
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-15 20:54 HKT
Nmap scan report for 172.16.38.130
Host is up (0.0025s latency).
Not shown: 991 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-apache-negotiation: mod_negotiation enabled.
139/tcp open netbios-ssn
143/tcp open imap
443/tcp open https
|_http-apache-negotiation: mod_negotiation enabled.
445/tcp open microsoft-ds
5001/tcp open commplex-link
8080/tcp open http-proxy
8081/tcp open blackice-icecapNmap done: 1 IP address (1 host up) scanned in 0.47 seconds┌──(kwkl㉿kwkl)-[/usr/share/nmap/scripts]
└─$ nmap --script http-apache-server-status.nse 172.16.38.130
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-15 20:54 HKT
Nmap scan report for 172.16.38.130
Host is up (0.0018s latency).
Not shown: 991 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
143/tcp open imap
443/tcp open https
445/tcp open microsoft-ds
5001/tcp open commplex-link
8080/tcp open http-proxy
8081/tcp open blackice-icecapNmap done: 1 IP address (1 host up) scanned in 5.72 seconds┌──(kwkl㉿kwkl)-[/usr/share/nmap/scripts]
└─$ samba脚本扫描失败
┌──(kwkl㉿kwkl)-[/usr/share/nmap/scripts]
└─$ nmap --script samba-vuln-cve-2012-1182.nse 172.16.38.130
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-15 20:59 HKT
Nmap scan report for 172.16.38.130
Host is up (0.0013s latency).
Not shown: 991 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
143/tcp open imap
443/tcp open https
445/tcp open microsoft-ds
5001/tcp open commplex-link
8080/tcp open http-proxy
8081/tcp open blackice-icecapHost script results:
|_samba-vuln-cve-2012-1182: Could not negotiate a connection:SMB: ERROR: Server returned less data than it was supposed to (one or more fields are missing); aborting [14]多个smb漏洞脚本扫描:┌──(kwkl㉿kwkl)-[/usr/share/nmap/scripts]
└─$ nmap --script smb-vuln-* 172.16.38.130
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-15 21:02 HKT
Failed to resolve "smb-vuln-cve2009-3103.nse".
Failed to resolve "smb-vuln-cve-2017-7494.nse".
Failed to resolve "smb-vuln-ms06-025.nse".
Failed to resolve "smb-vuln-ms07-029.nse".
Failed to resolve "smb-vuln-ms08-067.nse".
Failed to resolve "smb-vuln-ms10-054.nse".
Failed to resolve "smb-vuln-ms10-061.nse".
Failed to resolve "smb-vuln-ms17-010.nse".
Failed to resolve "smb-vuln-regsvc-dos.nse".
Failed to resolve "smb-vuln-webexec.nse".
Nmap scan report for 172.16.38.130
Host is up (0.0016s latency).
Not shown: 991 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
143/tcp open imap
443/tcp open https
445/tcp open microsoft-ds
5001/tcp open commplex-link
8080/tcp open http-proxy
8081/tcp open blackice-icecapNmap done: 1 IP address (1 host up) scanned in 112.66 seconds脚本扫描注入漏洞
┌──(kwkl㉿kwkl)-[~]
└─$ nmap --script /usr/share/nmap/scripts/http-sql-injection.nse 172.16.38.130
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-15 21:52 HKT
Nmap scan report for 172.16.38.130
Host is up (0.00061s latency).
Not shown: 991 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
143/tcp open imap
443/tcp open https
| http-sql-injection:
| Possible sqli for queries:
| https://172.16.38.130:443/ESAPI-Java-SwingSet-Interactive/main?function=About%27%20OR%20sqlspider
| https://172.16.38.130:443/ESAPI-Java-SwingSet-Interactive/main?function=ValidateUserInput%27%20OR%20sqlspider
| https://172.16.38.130:443/ESAPI-Java-SwingSet-Interactive/main?function=SessionManagement%27%20OR%20sqlspider
| https://172.16.38.130:443/ESAPI-Java-SwingSet-Interactive/main?function=Introduction%27%20OR%20sqlspider
| https://172.16.38.130:443/ESAPI-Java-SwingSet-Interactive/main?function=DataProtection%27%20OR%20sqlspider
| https://172.16.38.130:443/ESAPI-Java-SwingSet-Interactive/main?function=Logging%27%20OR%20sqlspider
| https://172.16.38.130:443/ESAPI-Java-SwingSet-Interactive/main?function=InitialSetup%27%20OR%20sqlspider
| https://172.16.38.130:443/ESAPI-Java-SwingSet-Interactive/main?function=Login%27%20OR%20sqlspider
| https://172.16.38.130:443/ESAPI-Java-SwingSet-Interactive/main?function=AccessControl%27%20OR%20sqlspider
| https://172.16.38.130:443/ESAPI-Java-SwingSet-Interactive/main?function=Encryption%27%20OR%20sqlspider
| https://172.16.38.130:443/ESAPI-Java-SwingSet-Interactive/main?function=Encoding%27%20OR%20sqlspider
| https://172.16.38.130:443/ESAPI-Java-SwingSet-Interactive/main?function=HttpSecurity%27%20OR%20sqlspider
| https://172.16.38.130:443/cyclone/?C=N%3bO%3dD%27%20OR%20sqlspider
| https://172.16.38.130:443/cyclone/?C=M%3bO%3dA%27%20OR%20sqlspider
| https://172.16.38.130:443/cyclone/?C=D%3bO%3dA%27%20OR%20sqlspider
|_ https://172.16.38.130:443/cyclone/?C=S%3bO%3dA%27%20OR%20sqlspider
445/tcp open microsoft-ds
5001/tcp open commplex-link
8080/tcp open http-proxy
8081/tcp open blackice-icecapNmap done: 1 IP address (1 host up) scanned in 24.90 seconds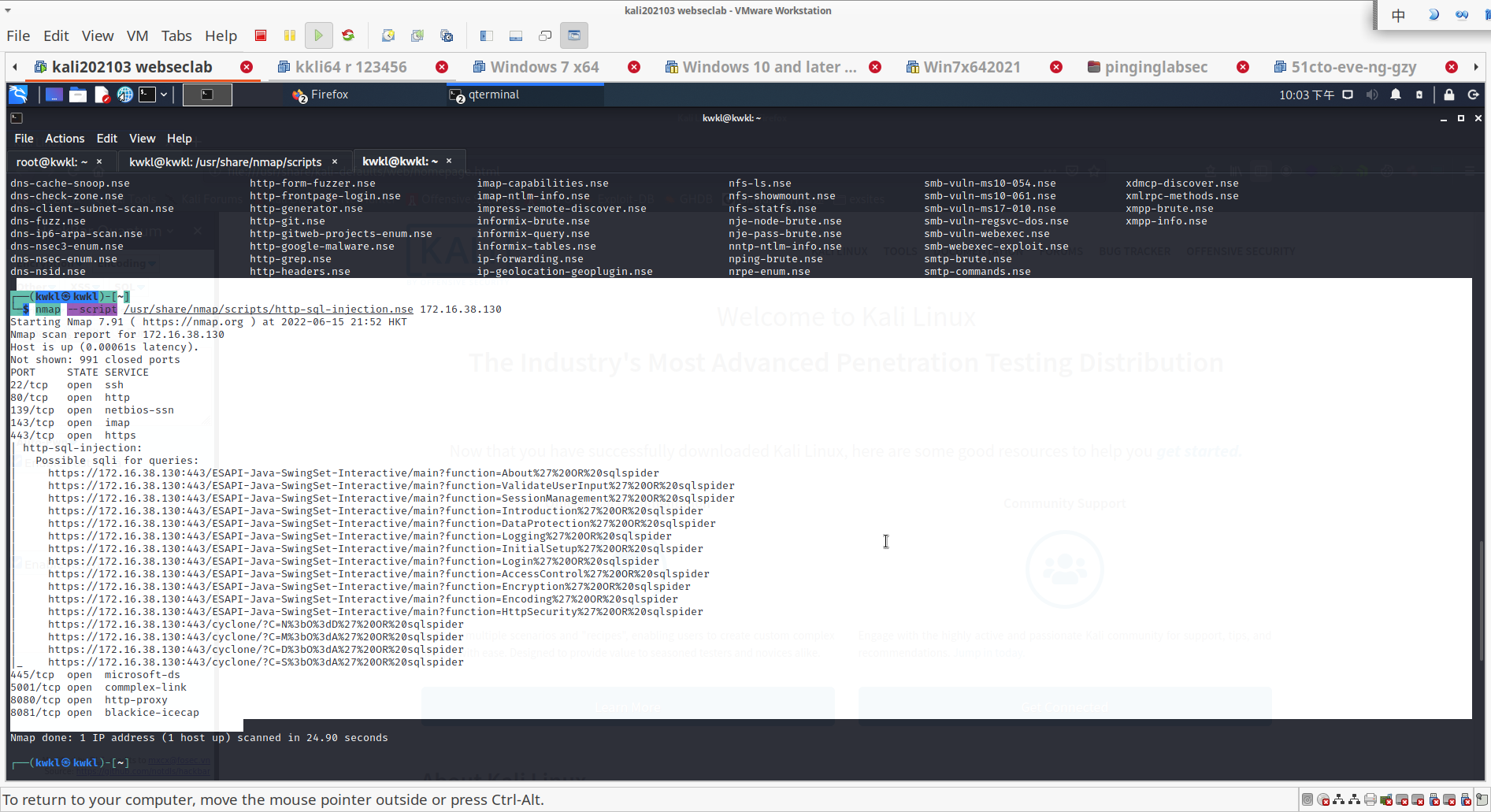
- 上述每一步都需要附上截图(必须包含每一天命令)进行说明
编写实验报告时,将整个作业过程中的涉及的步骤、效果、思路等整理为Word或PDF或PPT⽂档并上传,⽂档名称为"姓名-作业名称"。
这篇关于51进阶-信息搜集原理与实践2-20220615的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!






