本文主要是介绍加密软件加密与dat的关系_警察看到加密问题间谍软件制造商看到了机会,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
加密软件加密与dat的关系
By Patrick Howell O’Neill
帕特里克·豪威尔·奥尼尔
- The US Senate is set for a new hearing into encryption 美国参议院将开始新的加密听证会
- The big question: Is there new legislation mandating encryption back doors? 最大的问题:是否有新的法规要求加密后门?
- Meet the Israeli company selling a tool to push people off encrypted services 会见这家以色列公司,该公司出售一种工具来推动人们使用加密服务
Suppose you’re a cop who wants to eavesdrop on an encrypted phone call, the kind of call billions of people make all the time on WhatsApp. Old-fashioned wiretaps don’t work, since the technology underpinning encryption guarantees you’ll get nothing. You could try to hack a target’s phone and listen in — but that’s often a difficult and expensive proposition. Or you could legally demand that the company behind the service allow law enforcement a way to see the encrypted data, but that can mean a long and expensive legal battle.
小号 uppose你是谁想要窃听的加密电话呼叫警察,那种呼叫数十亿人使所有在WhatsApp的时间。 老式的窃听器不起作用,因为支持加密的技术保证您一无所获。 您可以尝试入侵目标的电话并收听-但通常这是一个困难而昂贵的提议。 或者,您可以从法律上要求服务背后的公司允许执法部门查看加密数据,但这可能意味着漫长而昂贵的法律斗争。
This long war between law enforcement and the technology industry will continue when the US Senate opens a hearing on data encryption Tuesday morning.
当美国参议院在星期二早上举行有关数据加密的听证会时,执法部门与技术行业之间的长期战争将继续。
The Senate Judiciary Committee, chaired by Republican Lindsey Graham, will hold the hearing, which will deal with technology that protects everything from WhatsApp communications to the data on your iPhone. Apple and Facebook privacy managers will be among those testifying next to one of the US government’s most vocal critics of encryption, Manhattan district attorney Cy Vance. The Trump administration has regularly criticized the use of cryptography, and in July Attorney General William Barr called for “lawful access” and encryption back doors that would allow officials to see encrypted private data.
由共和党人林赛·格雷厄姆(Lindsey Graham)主持的参议院司法委员会将举行听证会,该听证会涉及保护从WhatsApp通信到iPhone数据的一切技术。 苹果和Facebook隐私经理将是证人之一,紧随美国政府最强烈的加密批评家之一曼哈顿区检察官Cy Vance。 特朗普政府经常批评加密的使用,7月总检察长威廉·巴尔呼吁“合法访问”和加密后门,使官员可以查看加密的私人数据。
Opponents say these weaken internet security and privacy across the board, but there have been pushes from both parties in Congress to expand access to encrypted data. Several years ago the committee’s vice chair, Democrat Dianne Feinstein, promoted a controversial bill to mandate government access. That bill ended up going nowhere, but the biggest question leading into Tuesday’s hearing is whether a new bipartisan bill will emerge — and if so, whether it could have the backing of the White House.
反对者说,这些因素全面削弱了互联网的安全性和隐私性,但是国会两党都在努力扩大对加密数据的访问。 几年前,该委员会的副主席民主党人Dianne Feinstein提出了一项有争议的法案,要求政府准入 。 该法案最终无济于事,但导致周二听证会的最大问题是,是否会出现新的两党法案-如果是,它将获得白宫的支持。
But while this hearing is the latest chapter in the decades-long conflict between government and the technology industry, some companies are using different tactics to get access to encrypted data — and they’re selling it to law enforcement and intelligence agencies.
但是,尽管听证会是政府与技术行业之间长达数十年的冲突中的最新篇章,但一些公司正在使用不同的策略来访问加密数据,并将其出售给执法和情报机构。
不同的战术 (Different tactics)
Ten years ago, encryption — which deploys math to make data unreadable except by the intended recipient — was rare for ordinary users. Today, it protects the web browsing, text messages, and phone calls of billions of people around the world. That protection applies equally to democratically elected politicians and human rights activists but also to terrorists and spies, which has long driven governments to attempt to pierce encryption by both legal and technical means.
十年前,对于普通用户而言,很少使用加密(这种加密通过部署数学运算以使数据无法被预期的接收者读取)所罕见。 如今,它可以保护全球数十亿人的Web浏览,短信和电话。 这项保护同样适用于民主选举的政客和人权活动家,也适用于恐怖分子和间谍,长期以来,这驱使各国政府试图通过法律和技术手段破坏加密。
I recently met Ithai Kenan, vice president of an Israeli intelligence company called Picsix, at the Milipol security conference in Paris. Made up of Israeli intelligence veterans, Picsix is a decade-old company that specializes in data interception as a way of solving the encryption problem. (Its name is a nod to American football, and reflected in the company’s slogan: “The perfect interception.”)
我最近在巴黎举行的Milipol安全会议上会见了以色列情报公司Picsix的副总裁Ithai Kenan。 Picsix由以色列资深情报人员组成,是一家拥有十年历史的公司,专门从事数据拦截以解决加密问题。 (它的名字是对美式橄榄球的致敬,并在公司的口号中反映出来:“完美的拦截”。)

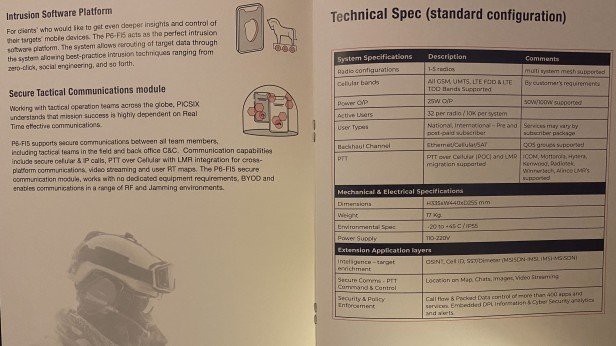
Kenan was selling the company’s newest product, a data interception and manipulation tool known as P6-FI5. The device works on GSM, 3G, and 4G cellular interception — meaning it can intercept and control both phone calls and data — and can be miniaturized to be carried inside backpacks or vehicles.
Kenan正在销售公司的最新产品,一种称为P6-FI5的数据拦截和操纵工具。 该设备可以在GSM,3G和4G蜂窝侦听上工作,这意味着它可以侦听和控制电话和数据,并且可以小型化以携带在背包或车辆中。
Picsix’s tool creates a fake cell tower that can fool a target’s phone into transmitting data to it. The device cannot read encrypted data, but instead tries a different tactic to get private information: making encrypted apps glitchy or even totally unusable. It’s a subtle but strong way to push a frustrated target away from a private app and toward a non-encrypted service that can easily be intercepted and eavesdropped on. The encryption itself is never broken — it is simply rendered useless.
Picsix的工具创建了一个伪造的手机发射塔,可以欺骗目标手机向其传输数据。 该设备无法读取加密的数据,而是尝试采取另一种策略来获取私人信息:使加密的应用程序出现故障甚至完全无法使用。 这是将受挫的目标从私有应用程序推向易于加密和窃听的非加密服务的微妙但有效的方法。 加密本身永不中断-只是变得毫无用处。
“We can manipulate data in a very selective manner,” Kenan said. “We can do it in a very selective way so it won’t seem like you’re being manipulated. We won’t just block WhatsApp entirely. Instead, we’ll let you make a WhatsApp call, and 10 seconds in, we’ll drop it. Maybe we’ll let you make another call, and in 20 seconds we’ll drop it. After your third failed call, trust me — you’ll make a regular call, and we will intercept it. It’s a smart and cost-effective way to go about interception.”
“我们可以以非常有选择性的方式操纵数据,”凯南说。 “我们可以以一种非常有选择性的方式来做到这一点,这样看来就好像您没有受到操纵。 我们不仅会完全阻止WhatsApp。 取而代之的是,我们让您拨打WhatsApp呼叫,然后在10秒钟之内放掉它。 也许我们会让您拨打另一个电话,然后在20秒内将其挂断。 在您的第三个呼叫失败后,请相信我-您将进行常规呼叫,我们将对其进行拦截。 这是进行拦截的明智且经济高效的方式。”
Traffic shaping to funnel data to more advantageous terrain is a tried and trusted intelligence tactic aimed at manipulating the target into a place where it’s easier to attack. This doesn’t accomplish the same goals as compromising a victim’s phone itself, but it can be equally effective and potentially even more persistent. A Trojan horse from a company like NSO Group might get you full access to the phone of a target for millions of dollars, but it relies on a vulnerability in the code running on the device: WhatsApp could release a security update tomorrow that renders the exploit useless and the money wasted.
流量整形以将数据集中到更有利的地形是一种经过实践检验且值得信赖的情报策略,旨在将目标操纵到更容易受到攻击的地方。 这并不能达到与牺牲受害者电话本身相同的目标,但是可以同样有效,甚至可能更持久。 来自NSO Group这样的公司的特洛伊木马程序可能会为您带来数百万美元的完全访问目标电话的权限,但它依赖于设备上运行的代码中的漏洞:WhatsApp明天可能会发布安全更新,以利用该漏洞没用,钱就浪费了。
Picsix argues that even though its tool won’t get access to the encrypted data, its usefulness won’t be wiped out by a single update either.
Picsix辩称,即使其工具无法访问加密数据,但一次更新也不会消除其实用性。
“That’s why we like data manipulation,” Kenan said.
“这就是为什么我们喜欢数据处理,” Kenan说。
The tactic also has the capacity to work across myriad devices, because it targets the data rather than the hardware. A Samsung Galaxy S10 and an iPhone 11 are two enormously different phones: every exploit has to be tailored to that specific target.
该策略还具有跨多种设备工作的能力,因为它针对的是数据而不是硬件。 三星Galaxy S10和iPhone 11是两种截然不同的手机:每种漏洞利用都必须针对特定目标量身定制。
“Because of how expensive Trojan horses are, there isn’t one manufacturer that does Trojan horses and actually supports all the different devices and manufacturers,” Kenan said. “You may have software for Android but not iOS. Let’s not even talk about all the funky devices you can find in China and India.”
“由于特洛伊木马的价格昂贵,因此没有一家制造商能够制造特洛伊木马并实际上支持所有不同的设备和制造商,”凯南说。 “您可能拥有适用于Android的软件,但没有适用于iOS的软件。 我们甚至不谈论在中国和印度都能找到的所有时髦设备。”
That said, Picsix’s technology can also reroute target data and inject malware onto a phone that uses its fake cell tower. From that moment, those multimillion-dollar Trojan horses can, potentially, be put to use.
也就是说,Picsix的技术还可以重新路由目标数据,并将恶意软件注入到使用其假基站的手机上。 从那时起,可以潜在地使用这些价值数百万美元的特洛伊木马。
更大的战斗 (The bigger battle)
Governments around the world have been using the tools built by companies like NSO Group and Picsix for years. There’s an entire highly capable and lucrative intelligence industry dedicated to the task.
多年来,世界各国政府一直在使用由NSO Group和Picsix等公司构建的工具。 整个功能强大且利润丰厚的情报行业都致力于这项任务。
But many top officials in Washington, DC, don’t want to have to rely on these tools to access data. Earlier this year during a security conference in New York City, Attorney General Barr called for back doors to encrypted data, and US Attorney Richard P. Donoghue pointed his finger at American tech giants.
但是华盛顿特区的许多高级官员不想依靠这些工具来访问数据。 今年早些时候,在纽约市的一次安全会议上 ,巴尔总检察长呼吁对加密数据进行后门,而美国总检察长理查德·多诺休(Richard P. Donoghue)则将矛头指向了美国科技巨头。
“These companies are marketing — they deny they’re marketing, but they are marketing — that they deny access to law enforcement,” Donoghue said. “They should be held accountable.”
Donoghue说:“这些公司在营销-他们否认自己在营销,但在营销-他们否认与执法部门接触。” “他们应该承担责任。”
For years, cryptographers have warned against encryption back doors as a solution that will undermine the security benefits of strong encryption. It’s not clear what will happen in the US Senate on Tuesday, but you can expect a back-and-forth debate that looks a lot like the so-called “crypto wars” of years past.
多年来,密码学家一直警告不要将加密后门作为一种解决方案,因为它会破坏强加密的安全性。 目前尚不清楚周二美国参议院将发生什么,但您可以期待一次来回辩论,看起来像是几年前的所谓“密码战争”。
Originally published on MIT Technology Review on December 10, 2019.
最初于2019年12月10日发表在《麻省理工学院技术评论》上。
翻译自: https://medium.com/mit-technology-review/cops-see-an-encryption-problem-spyware-makers-see-an-opportunity-50134737ac1c
加密软件加密与dat的关系
相关文章:
这篇关于加密软件加密与dat的关系_警察看到加密问题间谍软件制造商看到了机会的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!







