本文主要是介绍CSAPP 六个重要实验 lab1,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
CSAPP && lab1
--------------------------------------------------------------------实验要求--------------------------------------------------------------------
The Bit Puzzles
This section describes the puzzles that you will be solving in bits.c. More complete (and definitive, should there be any inconsistencies) documentation is found in the bits.c file itself.
Bit Manipulations
The table below describes a set of functions that manipulate and test sets of bits. The Rating column gives the difficulty rating (the number of points) for each puzzle and the Description column states the desired output for each puzzle along with the constraints. See the comments in bits.c for more details on the desired behavior of the functions. You may also refer to the test functions in tests.c. These are used as reference functions to express the correct behavior of your functions, although they don't satisfy the coding rules for your functions.
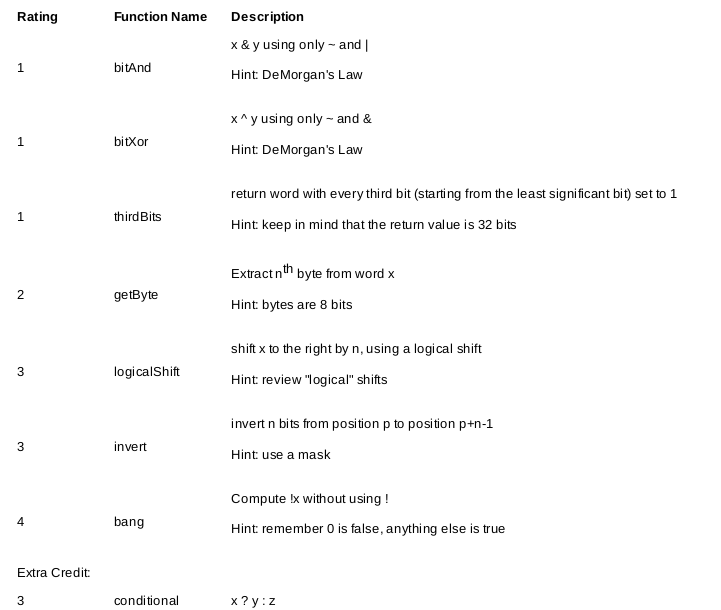
The following table describes a set of functions that make use of the two's complement representation of integers. Again, refer to the comments in bits.c and the reference versions in tests.c for more information.
-------------------------------------------------------------------以上为实验要求-------------------------------------------------------------
实验材料: bits.c
/* * CSE 351 HW1 (Data Lab )* * <Please put your name and userid here>* * bits.c - Source file with your solutions to the Lab.* This is the file you will hand in to your instructor.** WARNING: Do not include the <stdio.h> header; it confuses the dlc* compiler. You can still use printf for debugging without including* <stdio.h>, although you might get a compiler warning. In general,* it's not good practice to ignore compiler warnings, but in this* case it's OK. */#if 0
/** Instructions to Students:** STEP 1: Read the following instructions carefully.*/You will provide your solution to this homework by
editing the collection of functions in this source file.INTEGER CODING RULES:Replace the "return" statement in each function with oneor more lines of C code that implements the function. Your code must conform to the following style:int Funct(arg1, arg2, ...) {/* brief description of how your implementation works */int var1 = Expr1;...int varM = ExprM;varJ = ExprJ;...varN = ExprN;return ExprR;}Each "Expr" is an expression using ONLY the following:1. Integer constants 0 through 255 (0xFF), inclusive. You arenot allowed to use big constants such as 0xffffffff.2. Function arguments and local variables (no global variables).3. Unary integer operations ! ~4. Binary integer operations & ^ | + << >>Some of the problems restrict the set of allowed operators even further.Each "Expr" may consist of multiple operators. You are not restricted toone operator per line.You are expressly forbidden to:1. Use any control constructs such as if, do, while, for, switch, etc.2. Define or use any macros.3. Define any additional functions in this file.4. Call any functions.5. Use any other operations, such as &&, ||, -, or ?:6. Use any form of casting.7. Use any data type other than int. This implies that youcannot use arrays, structs, or unions.You may assume that your machine:1. Uses 2s complement, 32-bit representations of integers.2. Performs right shifts arithmetically.3. Has unpredictable behavior when shifting an integer by morethan the word size.EXAMPLES OF ACCEPTABLE CODING STYLE:/** pow2plus1 - returns 2^x + 1, where 0 <= x <= 31*/int pow2plus1(int x) {/* exploit ability of shifts to compute powers of 2 */return (1 << x) + 1;}/** pow2plus4 - returns 2^x + 4, where 0 <= x <= 31*/int pow2plus4(int x) {/* exploit ability of shifts to compute powers of 2 */int result = (1 << x);result += 4;return result;}FLOATING POINT CODING RULESFor the problems that require you to implent floating-point operations,
the coding rules are less strict. You are allowed to use looping and
conditional control. You are allowed to use both ints and unsigneds.
You can use arbitrary integer and unsigned constants.You are expressly forbidden to:1. Define or use any macros.2. Define any additional functions in this file.3. Call any functions.4. Use any form of casting.5. Use any data type other than int or unsigned. This means that youcannot use arrays, structs, or unions.6. Use any floating point data types, operations, or constants.NOTES:1. Use the dlc (data lab checker) compiler (described in the handout) to check the legality of your solutions.2. Each function has a maximum number of operators (! ~ & ^ | + << >>)that you are allowed to use for your implementation of the function. The max operator count is checked by dlc. Note that '=' is not counted; you may use as many of these as you want without penalty.3. Use the btest test harness to check your functions for correctness.4. Use the BDD checker to formally verify your functions5. The maximum number of ops for each function is given in theheader comment for each function. If there are any inconsistencies between the maximum ops in the writeup and in this file, considerthis file the authoritative source./** STEP 2: Modify the following functions according the coding rules.* * IMPORTANT. TO AVOID GRADING SURPRISES:* 1. Use the dlc compiler to check that your solutions conform* to the coding rules.* 2. Use the BDD checker to formally verify that your solutions produce * the correct answers.*/#endif
// Rating: 1
/* * bitAnd - x&y using only ~ and | * Example: bitAnd(6, 5) = 4* Legal ops: ~ |* Max ops: 8* Rating: 1*/
int bitAnd(int x, int y) {return 2;
}
/* * bitXor - x^y using only ~ and & * Example: bitXor(4, 5) = 1* Legal ops: ~ &* Max ops: 14* Rating: 1*/
int bitXor(int x, int y) {return 2;
}
/* * thirdBits - return word with every third bit (starting from the LSB) set to 1* Legal ops: ! ~ & ^ | + << >>* Max ops: 8* Rating: 1*/
int thirdBits(void) {return 2;
}
// Rating: 2
/* * fitsBits - return 1 if x can be represented as an * n-bit, two's complement integer.* 1 <= n <= 32* Examples: fitsBits(5,3) = 0, fitsBits(-4,3) = 1* Legal ops: ! ~ & ^ | + << >>* Max ops: 15* Rating: 2*/
int fitsBits(int x, int n) {return 2;
}
/* * sign - return 1 if positive, 0 if zero, and -1 if negative* Examples: sign(130) = 1* sign(-23) = -1* Legal ops: ! ~ & ^ | + << >>* Max ops: 10* Rating: 2*/
int sign(int x) {return 2;
}
/* * getByte - Extract byte n from word x* Bytes numbered from 0 (LSB) to 3 (MSB)* Examples: getByte(0x12345678,1) = 0x56* Legal ops: ! ~ & ^ | + << >>* Max ops: 6* Rating: 2*/
int getByte(int x, int n) {return 2;
}
// Rating: 3
/* * logicalShift - shift x to the right by n, using a logical shift* Can assume that 0 <= n <= 31* Examples: logicalShift(0x87654321,4) = 0x08765432* Legal ops: ~ & ^ | + << >>* Max ops: 20* Rating: 3 */
int logicalShift(int x, int n) {return 2;
}
/* * addOK - Determine if can compute x+y without overflow* Example: addOK(0x80000000,0x80000000) = 0,* addOK(0x80000000,0x70000000) = 1, * Legal ops: ! ~ & ^ | + << >>* Max ops: 20* Rating: 3*/
int addOK(int x, int y) {return 2;
}
/* invert - Return x with the n bits that begin at position p inverted * (i.e., turn 0 into 1 and vice versa) and the rest left * unchanged. Consider the indices of x to begin with the low-order* bit numbered as 0.* Example: invert(0x80000000, 0, 1) = 0x80000001,* invert(0x0000008e, 3, 3) = 0x000000b6,* Legal ops: ! ~ & ^ | + << >>* Max ops: 20* Rating: 3 */
int invert(int x, int p, int n) {return 2;
}
// Rating: 4
/* * bang - Compute !x without using !* Examples: bang(3) = 0, bang(0) = 1* Legal ops: ~ & ^ | + << >>* Max ops: 12* Rating: 4 */
int bang(int x) {return 2;
}
// Extra Credit: Rating: 3
/* * conditional - same as x ? y : z * Example: conditional(2,4,5) = 4* Legal ops: ! ~ & ^ | + << >>* Max ops: 16* Rating: 3*/
int conditional(int x, int y, int z) {return 2;
}
// Extra Credit: Rating: 4
/** isPower2 - returns 1 if x is a power of 2, and 0 otherwise* Examples: isPower2(5) = 0, isPower2(8) = 1, isPower2(0) = 0* Note that no negative number is a power of 2.* Legal ops: ! ~ & ^ | + << >>* Max ops: 20* Rating: 4*/
int isPower2(int x) {return 2;
}
对于这种神级bit operation还不能hold住,有些函数并未实现, 欢迎交流讨论 : D
我的解:(update 2015.10.10 原来的solution优点不规范,删了,以托管到github的为准)
https://github.com/jasonleaster/CSAPP/blob/master/lab1/bits.c
激吻 海耶兹 法国 布面油画 1859年 121×97cm 私人收藏
这幅画表现的是一对情侣在走廊间深吻的场景。画面构图简单,画家把人物安排在画面正中央,突显了主题。用笔细腻,女子身上的蓝色长裙光彩熠熠,蕾丝边的袖口优雅婉转。裙摆的褶皱在光线的照射下质感极强,女子的婀娜多姿被表现得淋漓尽致。男子暗红色的外袍和红色的裤子色彩对比和谐。暗黄的光线通过情侣投射在墙上,为画面铺上一层深情温馨的气息。 尽管这幅作品并非裸体绘画,但一直被评论家们认为是他的代表作之一。这幅作品在当时就引人注目,引起同时代人们的广泛尊重。作品所表现的内容是匿名人物,它并不需要什么深奥的文学解读便可以看得懂。该画最有味道的地方,也是画面构思最好的地方,是男子的左腿蹬在了一个台阶上,所有的感觉 都来源于这里。 正一艺术认为,这幅作品具有震撼的美感和强烈的现代意识。
这篇关于CSAPP 六个重要实验 lab1的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!










